There’s something about October; it makes you pause, reflect, and rethink things. Maybe that’s why people say the “October Theory” is real! 🤔
For us, every October has its own story, and this time, it was about closing the gap between what looks secure and what actually is!
And this pushed us to go beyond what we had covered. So, we went broader exploring Active Directory foundations, hybrid setups, AI-driven security concerns, cloud risks, and more.
For 31 days, we shared a mix of myths, realities, and hands-on security insights across all IT environments. And even broke the illusion that “secure by default” is always secure. 💯
Some posts were eye-openers;
Some were reminders;
And a few made us realize how much security has evolved! 📈
Now, with October behind us, it feels right to look back at everything we’ve explored over these 31 days, the insights, the challenges, and the little lessons.
Myth vs Reality: The Spark That Became a Campaign!
It all started as a random spark during a brainstorming session for Cybersecurity Awareness Month.
We thought, why not make it a 31-day reality check for admins? What if we turn those everyday IT misconceptions into a month-long myth-busting challenge?
And that’s how the Myth vs. Reality idea was born! ⭐We didn’t want it to be just another catchy campaign. Our goal was to simplify the complex security concepts that feel relatable and help admins see the ‘why’ behind the ‘what’.
Because not every security risk hides in advanced exploits. Sometimes, it’s right there in plain sight, buried in default settings, ignored alerts, or the classic “we’ve always done it this way.”
So, each day, we picked a myth that admins have quietly believed or overlooked:
- AI data can’t be controlled
- Our users are too smart to fall for phishing.
- Trusted office IPs are always safe.
- DLP scans the document completely without leaving any words
And we flipped them, not just to prove them wrong, but to show what’s really happening behind the scenes! We had a dedicated Myth vs. Reality webpage where each myth could be flipped to reveal the truth and its fix underneath, step-by-step. (to make awareness both interactive and insightful 😜). You can flip through all 31 myths we’ve busted so far right here 👇
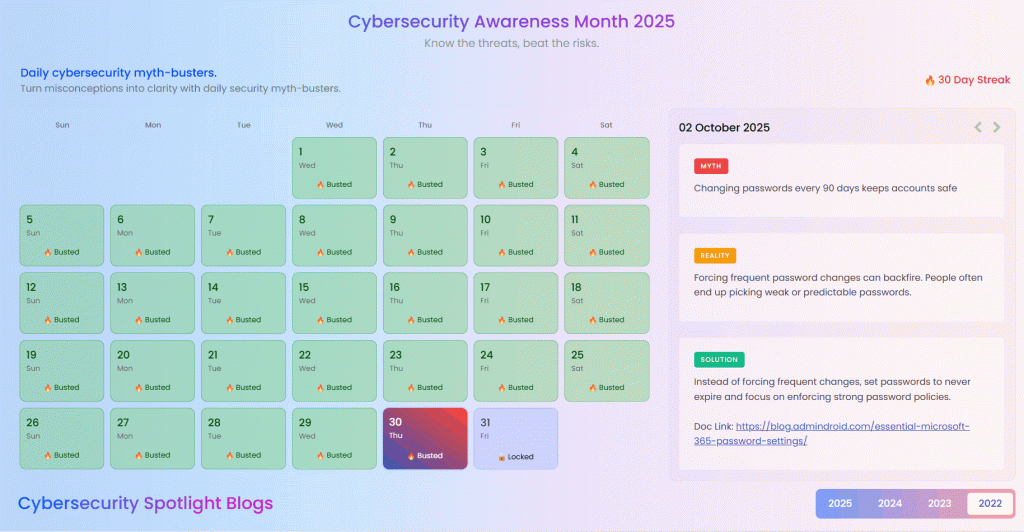
And if there’s one thing this series proved, it’s that even the smallest assumptions can create the biggest security gaps.
31 Days. 6 Themes. 1 Goal — Stronger Security
Here’s how our 31 days shaped up, across six security mindsets:
- Don’t Assume Safe – Challenge the defaults you trust too much.
- Strengthen Your Identity Core – Protect who connects, and how.
- Govern the Rise of AI Apps – Secure what didn’t exist yesterday.
- The Admin Security Playbook – The essentials every admin lives by.
- Know Before You Grant – Every permission is a responsibility.
- Protect What Matters – Safeguard what leaves your environment.
Don’t Assume Safe
We started with the most common trap, comfort. 😅The false sense of security that comes from “it’s always been like this.” Many Microsoft 365 security missteps (and even general security configurations) don’t come from hackers, but come from admins trusting defaults, skipping access reviews, or assuming that if it worked yesterday, it’s safe today.
This section unpacks those silent risks: the ones hidden behind settings that look harmless. From trusted office IPs to local admin accounts, default VPN setups, and remote access options. They don’t throw alerts or trigger warnings, but they quietly widen your attack surface over time.
1. Setting your office IP as “trusted” in Conditional Access might sound safe, but it’s easier to exploit than you think! 👉Read: Why is Office IP as a Trusted Location in Conditional Access Risky?
2. By default, any authenticated user in Active Directory can add up to ten computers to the domain. 👉Read: Prevent Users from Adding Computers to the Domain Using Group Policy
3. Local admin accounts might seem harmless, but that small convenience can snowball into a full network compromise. 👉Read: Best Practices to Secure Local Admin Accounts
4. VPNs have been around forever, and many admins still trust them as an old, reliable tool. But that’s the illusion; familiar doesn’t mean secure. 👉Read: Are VPN Really Safe and Secure?
5. Remote PowerShell access isn’t always risky by itself; the problem starts when more users get added to the Remote Management group without realizing what that means! 👉Read: Restrict Remote PowerShell Access to Non-Admins.
6. Sometimes, staying “secure” needs a bit of deception. Regular monitoring in Active Directory can miss what attackers cleverly hide, so why not trick them instead? 😉 👉Read: How to Set Up Honey Accounts in Active Directory
7. If external sharing is allowed on a SharePoint site, any site member can share content externally! ⏩A small slip here can turn into a serious data leak. A better fix? 👉Read: Allow only specific security groups to share externally in a SharePoint Site
Strengthen Your Identity Core
Everything starts and often fails with identity! If you don’t control who connects and how, no policy or firewall can save you.
Every weak credential, unmanaged service account, or outdated password policy is the cracks that quietly weaken your entire security posture. So, we brought all those identity-first measures together in one place to help you strengthen your IT environments. ✅
This section dives into tightening your identity hygiene, from Active Directory hardening to securing hybrid environments. Because at the end of the day, if your identity layer isn’t strong, nothing else really stands secure.
8. Traditional default password policies configured through GPO treat everyone the same, but not every AD account carries the same risk! A better way? 👉 Read: Set Up Fine-Grained Password Policies in Active Directory
9. Many admins still use regular Active Directory user accounts for scheduled tasks, automation, and skip password rotation, but that’s a risky shortcut! So, the best way? 👉Read: Use Managed Service Accounts (MSAs) in Active Directory.
10. Resetting the KRBTGT account password might not sound exciting, but it’s key to keeping your identity layer secure. But how to? 👉Read: How to Reset KRBTGT Account Password in Active Directory
11. Managing identities across cloud and on-prem environments makes hybrid domains more exposed to password-based attacks. How to close the gap? 👉Read: Go passwordless with Microsoft Entra Kerberos.
12. Hybrid identity setups bridge on-prem and cloud, but that bridge is exactly what attackers target! 👉Read: Steps to Protect Against Hybrid Identity Attacks.
Govern the Rise of AI Apps
🤖AI brought new possibilities and new problems, too! So, we stepped in to tackle what didn’t even exist a year ago: generative AI tools, Copilot, and sensitive data flowing into AI systems.
Blocking AI isn’t the answer; controlling how it’s used safely is! 💯In this section, we explored every angle of AI governance in Microsoft 365, from blocking unauthorized AI apps to applying granular controls for approved ones and even granting just-in-time access when productivity demands it.
All the angles, every scenario, covered! ✅ From blocking, controlling, and time-bound access to monitoring AI interactions, every step is detailed to help admins. The good thing is that you don’t need any 3rd party tool to implement these restrictions. It’s all built right in Microsoft Entra Suite and Microsoft Purview.
13. Blocking every AI tool isn’t the answer; block only the AI apps that you don’t want your Microsoft 365 users to use! 👉Read: Block GenAI Using Web Content Filtering in Microsoft 365
14. You don’t always need to block; just add the right security checks! 👉 Read: Enforce Stronger Security Controls for Generative AI Apps.
15. Despite all the Microsoft 365 security layers, data can still leak when users upload it to ChatGPT. ⚠️Stop it before it spreads! 👉 Read: Prevent Users from Uploading Sensitive Data to ChatGPT
16. Sometimes users genuinely need AI apps to get their work done — and blocking them entirely in your Microsoft 365 environment only slows productivity. The smarter alternative? 👉 Read: Grant Just-In-Time Access to GenAI Apps Using Access Packages
17. AI apps don’t just stop with users — the real risk starts where they’re accessed: devices. 📱 Keep them in check! 👉 Read: Block Risky AI Apps Across Microsoft 365 Managed Devices
18. Just securing AI apps’ usage isn’t enough; the real win is continuously monitoring Microsoft 365 Copilot usage and other GenAI activities. 👉 Read: Monitor AI-to-user and user-to-AI interactions across Microsoft 365
The Admin Security Playbook
No matter how strong your tools are, security awareness and governance always come down to the people behind them — the admins. 👑This section is for the everyday defenders, the ones who patch, monitor, and enforce.
We bring together everything admins need to strengthen IT environments, from Active Directory hardening and admin hygiene to comprehensive defense strategies across every setup.
At the end of the day, best practices aren’t just policies; they’re the habits that define how secure your organization truly is.
19. If your AD environment falls, everything follows. Secure it right with these essential hardening practices every admin should apply. 👉 Read: Best Practices for Active Directory Security
20. Automation saves time, until exposed credentials turn it into a security risk! Learn the safest ways. 👉 Read: Best Methods to Securely Store Passwords for Automated PowerShell Scripts
21. Remote access makes life easier and breaches easier, too! Lock down your RDP sessions with these proven admin best practices. 👉 Read: 11 Best Practices to Secure Remote Desktop Access.
22. Build a consistent hybrid identity plan, see which AD and Microsoft 365 features to use (and which to avoid) for a simpler, safer identity posture. 👉 Read: Compare Security Features of Active Directory and Microsoft 365.
23. When your org runs across cloud and on-prem, one compromised admin account can trigger a chain reaction, data gets wiped, servers hijacked, trust shattered! These ten practices can stop that. 👉 Read: Best Practices to Secure Admin Accounts in Hybrid Environments
Know Before You Grant
Access doesn’t always mean trust, but we often treat it that way! This section is about slowing down before hitting the button – “Grant Permission.” Every app, user, and automation script in Microsoft 365 carries privileges that can spiral out of control fast.
That’s why we dove into the essentials of Microsoft 365 permission governance: blocking unsafe secrets, delegating only what’s necessary, tracking who has access to what, and more.
24. Client secrets might look like a quick fix for app connections, but once leaked, they turn into invisible backdoors to your M365 tenant! 👉 Read: Block the Creation of Client Secrets in Microsoft Entra Applications
25. Not all Entra app permissions behave the same; some act on behalf of users; others run with full system power! Know the difference. 👉 Read: Difference B/W Delegated and App-Only Access in Entra Applications
26. You can’t secure what you can’t see, and that includes Entra app permissions, too! Get clear visibility into app consents. 👉Read: PowerShell Script to Export Entra Enterprise App Permissions Report
27. Least privilege isn’t just a principle; it’s a practice. Delegate only what’s truly needed in Active Directory & keep admin rights tight. 👉 Read: Delegation Wizard for Active Directory Least Privilege.
Protect What Matters
Data doesn’t just live inside your tenant anymore; it moves, syncs, and finds its way across clouds, apps, and even AI models. So instead of just locking it down, we decided to focus on visibility, which means knowing what data you have, where it goes, and who’s touching it.
Data protection is at the core of Microsoft 365 security and compliance. And that’s why here we focus on strengthening admin visibility through DLP, DSPM, and AI-aware monitoring. This helps to detect sensitive data misuse, insider risks, and AI-driven exposure.
Because protecting what’s sensitive starts with knowing what’s leaving your environment and why.
28. The biggest risks are often the quiet ones: internal codes, employee records, and client IDs. Build custom SITs in Microsoft Purview and stop them. 👉 Read: Create Custom Sensitive Information Types for DLP
29. See every corner of your data, what’s protected, what’s exposed, and what’s slipping away. 👉 Read: How DSPM in Microsoft Purview Helps Protect Sensitive Data.
30. AI sees everything you feed it, but do you see what it keeps? 👉 Read: How DSPM for AI helps monitor and protect data shared through AI and Copilot.
31. Personal data protection isn’t just compliance; it’s the trust your people & customers place in you. Keep that trust unbroken. 👉 Read: Best Practices for Protecting Employee Personal Data
Let’s Continue to Strengthen IT Environments, Every Day!
With this, we close our Cybersecurity Awareness Month series for 2025.
Over the past 31 days, we’ve explored real-world admin challenges, from managing access permissions to strengthening data protection across cloud, hybrid, and AI-powered environments. Each topic came down to one thing: building habits that make security part of what you do, not just what you know! 🤝
But cybersecurity doesn’t end with October; it evolves every single day. 💯As attackers get smarter, so should we. Keep tightening controls, questioning permissions, and staying curious about what’s changing around you. Because security isn’t something you finish, it’s something you maintain. ⚙️
Thanks for following along and being part of this journey.
Here’s to staying secure, every day! 🥂






