On Day 13 of Cybersecurity Awareness Month, we’re excited to share 5 Defender for Cloud Apps recommended actions that can boost your Microsoft Secure Score by around 10 points! Stay tuned for the upcoming blogs in our M365 Cybersecurity blog series.
| 😱What if…the following situation happens? Imagine a scenario where a finance analyst decides to use a popular, free budgeting tool for tracking quarterly expenses. It might seem convenient, but your IT dept hasn’t approved it for security compliance. Little did they know this tool stores all sensitive data like vendor contracts and employee salary details in its own insecure cloud, which might not meet your organization’s security standards! If it gets compromised, your company’s sensitive financial data could be exposed, leading to huge financial losses and reputational damage! |
The thing is: We all love the convenience of cloud apps, but not everyone sticks to the IT-approved apps or checks their security! Employees often grab whatever seems useful, even if it’s not secure. This can be risky, as unapproved apps can expose confidential data and more.
To prevent such incidents and regain control over cloud app usage, Microsoft has ‘Defender for Cloud Apps (MDCA), a robust Cloud Access Security Broker (CASB) solution. Securing with Cloud App Security is essential, but it gets even better when you act on Secure Score recommendations given for MDCA.
And that’s exactly what we’re here to explain in this blog.
What is Microsoft Defender for Cloud Apps?
Defender for Cloud Apps (DCA) is part of the Microsoft Defender suite, that lets you identify users using cloud applications, control how they’re used and protect your company data. Connecting Microsoft 365 to Defender for Cloud Apps, lets you stream all events to DCA and monitor user activity.
Benefits of Microsoft Defender for Cloud Apps:
- Defender for Cloud Apps integrates smoothly with Microsoft 365 and over 25,000 other cloud applications, giving you visibility and control across different cloud environments.
- Detects Shadow IT and provides real-time session monitoring using advanced techniques like anomaly detection, behavioral analytics, and machine learning.
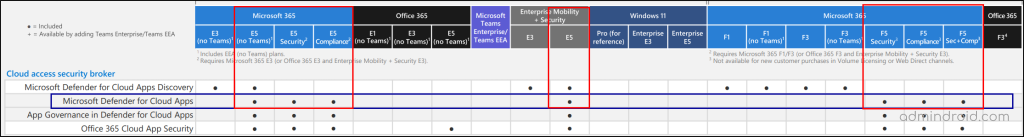
Defender for Cloud Apps is part of the Microsoft 365 E5 tier, but it’s also bundled with other licenses – check the image for details. But I must say that organizations heavily reliant on cloud applications, MDCA is a valuable investment!
Microsoft Secure Score Recommendations in Defender for Cloud Apps
Now that we’ve covered what Defender for Cloud Apps is, let’s dive into the major part: Microsoft Secure Score! This is a security analytics tool from Microsoft that assesses your organization’s overall security posture. It calculates a percentage score based on your configurations and settings and suggests ways to improve security.
In this section, we’ll focus specifically on the Secure Score recommendations that protect your cloud apps. You can also secure third-party apps with secure score recommendations that can be applied to all third-party apps within Microsoft 365.
NOTE: You’ll need to connect Microsoft 365 to Defender for Cloud Apps to access these new recommendations.
Here are the recommendations given by Secure Score for Microsoft Defender for Cloud Apps.
- Ensure Microsoft Defender for Cloud Apps is enabled
- Create an OAuth app policy to notify you about new OAuth applications
- Create an app discovery policy to identify new and trending cloud apps in your org
- Create a custom activity policy to get alerts about suspicious usage patterns
- Deploy a log collector to discover shadow IT activity
Now, let’s walk through how to set these up one by one to better monitor your cloud app activity and boost your Secure Score.
1. Ensure Microsoft Defender for Cloud Apps is Enabled
First, ensure you are a Security Admin in Microsoft 365 so that you can set up & manage Defender for Cloud Apps.
READ ME! To monitor and protect each user, you must have a Defender for Cloud Apps license for everyone you want to secure.
Once licenses are sorted, check that Cloud Apps in Defender is enabled. Then, connect your apps in the app connector settings and then start monitoring user activity across all your cloud apps.
Now that Defender for Cloud Apps is up, the next secure score recommendations list step revolves around a different context! All the recommended actions suggest deploying Defender for Cloud Apps alerts to notify admins about user activities. For this, there are six different Defender for Cloud App policy types available:
- Activity policy
- File policy
- App discovery policy
- Access policy
- Session policy
- OAuth app policy
Based on Secure Score recommendations, we’ll go over how to create and control cloud apps with these policies.
2. Create an OAuth App Policy to Notify About New OAuth Applications
Since OAuth apps request access to sensitive data or act on behalf of users, it’s crucial to ensure you’re aware of these new OAuth app connections.
For this, creating an OAuth app policy can help you manage app permissions and get notified when a new OAuth app is authorized. This lets you investigate the app’s permissions and who authorized it.
How to Create Alerts When New OAuth Applications Are Added?
While Microsoft Defender for Cloud Apps comes with several default policy templates (we can explore that on another day), there isn’t one specifically for OAuth app alerts. So, let’s create one.
- Login to the Microsoft Defender portal and open the ‘Cloud Apps’ dropdown.
- Under the ‘Policies’ dropdown, select ‘Policy Management’.
- Click ‘Create Policy’ and choose ‘OAuth app policy’.
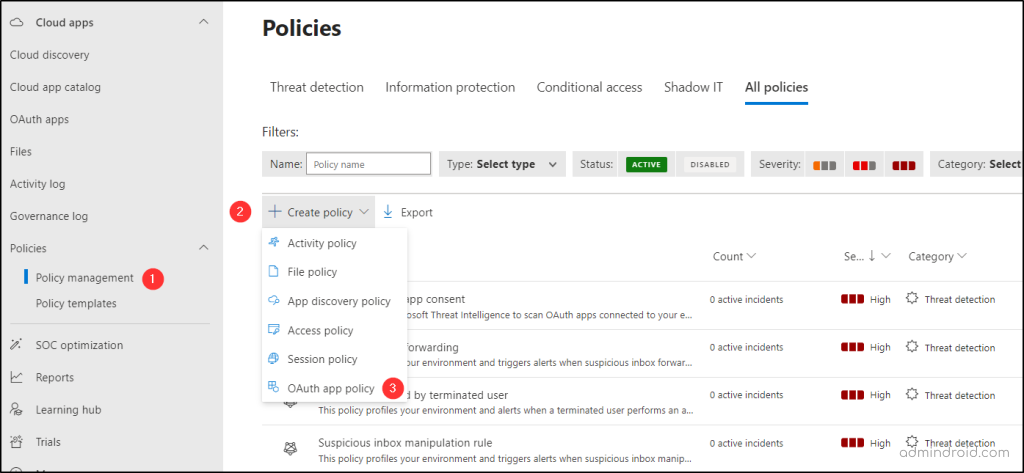
Note: By default, it will apply to all the connected apps in the ‘App Connector’ setting page. You can customize this as you wish on the policies page.
- Name the policy, set the severity level, and add a description.
- Since there’s no built-in alert for new app additions, here’s a quick workaround. Head to the “Create filters for the policy” section, choose the ‘Permissions’ filter, and select all the sensitive permissions you want to track. This way, you’ll catch any new apps that ask for high-level permissions.
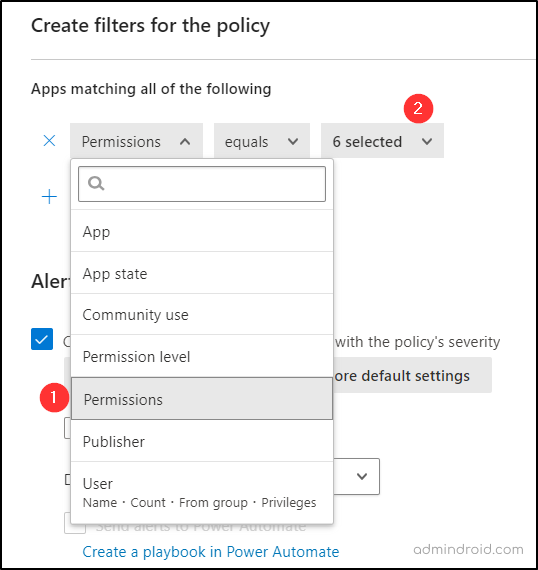
6. In the ‘Alerts’ section, check the option to create an alert for each matching event. Opt to receive email alerts for easy monitoring.
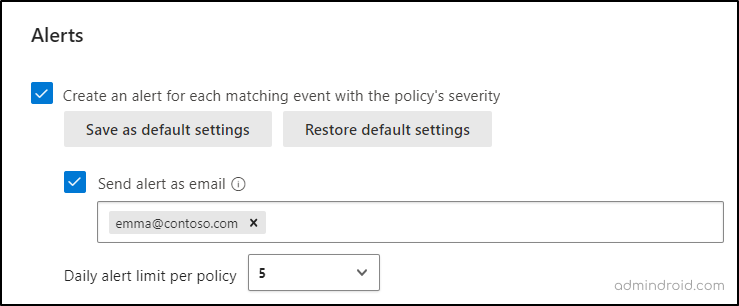
- Set the daily alert limit and save the policy.
This policy alerts you when new apps request sensitive data and boosts your security and Secure Score by 4 points. That’s what I said first, a double win! 😉
3: Create an App Discovery Policy to Identify New & Trending Cloud Apps in Your Org
App discovery policies in Defender for Cloud Apps are your best friends when it comes to spotting new or unusual app usage based on traffic logs. Microsoft recommends enabling a cloud app discovery policy to catch any suspicious activity within your organization’s apps.
The good news? You don’t have to start from scratch. 😌Microsoft provides some handy default cloud app policy templates that you can deploy right away!
How to Configure Alerts for Popular Cloud Applications in MS Defender?
- Log in to the Microsoft Defender for Cloud Apps portal.
- From the ‘Policies’ dropdown, select ‘Policy Templates.’
- Now, toggle the ‘Advanced Filter’ on the right side.
- Set the filter to: Type equals ‘App discovery policy’.
- You’ll see four built-in templates related to identifying popular apps:
- New popular app – Alerts you when new apps are used by over 500 users.
- New high-volume app – Alerts you when new apps have daily traffic exceeding 500 MB.
- New high upload volume app – Alerts you for new apps with significant daily upload traffic.
- New risky app – Alerts you when new apps score less than 6 and have over 50 users and 50 MB of daily traffic.
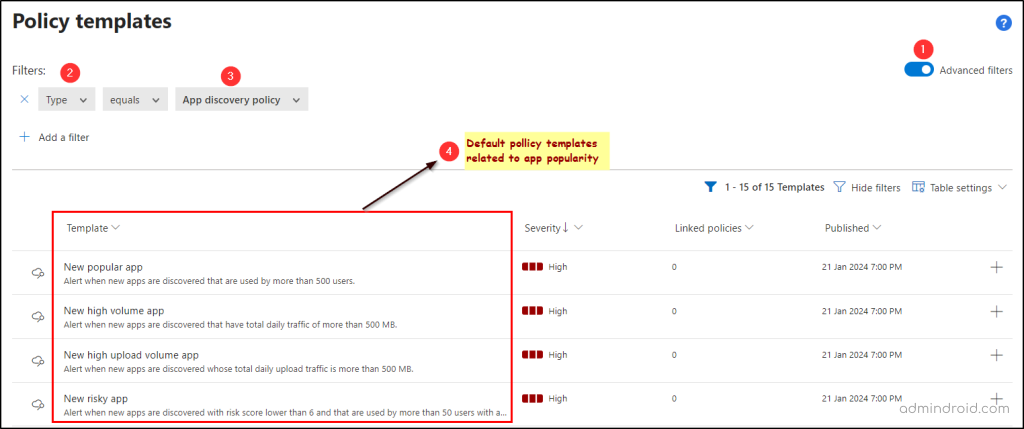
- Preview all the above policies, edit as per your wish and click ‘Create’. This can get you 3 points in your Secure Score.
That’s it. You’ll have your finger on the pulse of user activity, even when they think they’re flying under the radar!
4. Create a Custom Activity Policy to Get Alerts About Suspicious Usage Patterns
Defender for Cloud Apps activity policy lets you keep an eye on specific user actions and catch any unexpected spikes in activity. Admins can effectively make use of the cloud app activity policies to investigate anomaly detection alerts and identify different security threat scenarios.
Just like app discovery policies, you’ll find several activity policy templates in the Defender for Cloud Apps section. Each one focuses on a particular activity, helping you pinpoint areas of concern.
- Log in to the Microsoft Defender portal and open the ‘Cloud Apps’ dropdown.
- Next, select ‘Policy Templates’ from the ‘Policies’ dropdown.
- Now, toggle the ‘Advanced Filter’ on the right side.
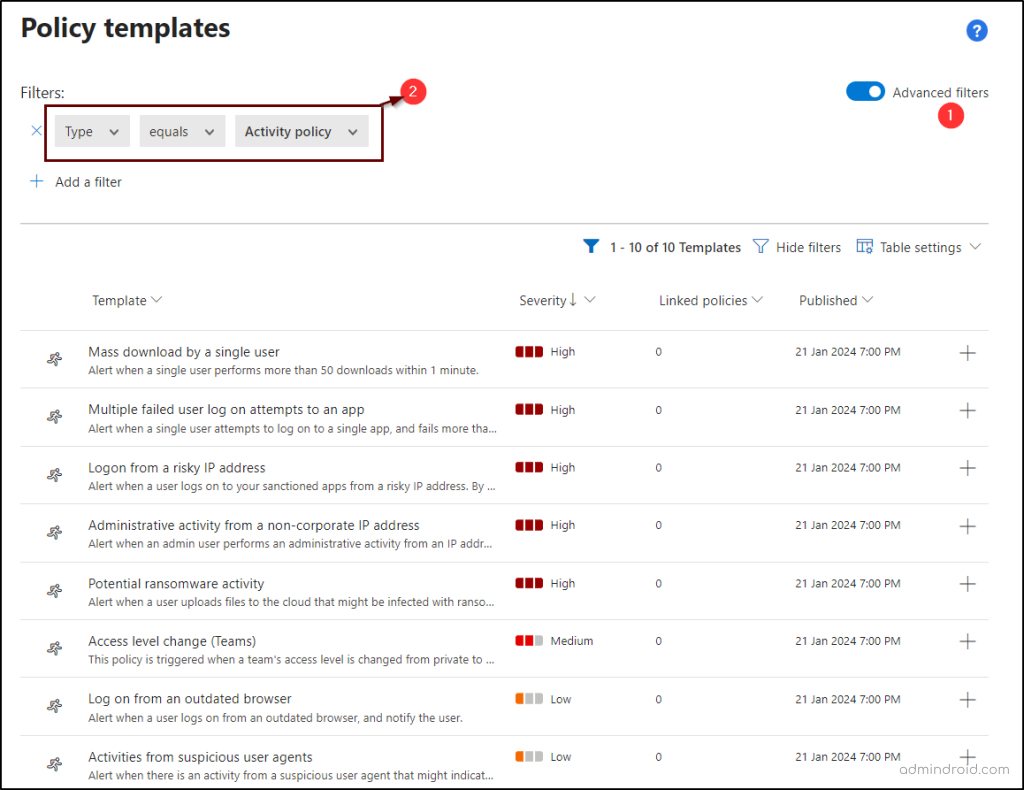
- Set the filter to: Type equals ‘Activity policy’.
- You will find the 7 built-in policy templates for this case.
- Mass download by a single user – Alerts when one user downloads more than 50 files in a minute.
- Multiple failed login attempts – Notifies you if a user fails to log in to an app more than 10 times within 5 minutes.
- Logon from a risky IP – This policy alerts you when a user logs into sanctioned apps from a risky IP address. By default, the Risky IP category includes addresses tagged as Anonymous proxy, TOR, or Botnet. You can add more IPs in the IP address ranges settings page.
- Administrative activity from a non-corporate IP – Alerts when an admin logs in from an IP not on your corporate list.
- Potential ransomware activity – Notifies you if a user uploads files that could be infected with ransomware.
- Log on from an outdated browser – Alerts when a user accesses the app from an outdated browser and notifies them.
- Activities from suspicious user agents – Sends an alert if an activity is detected from a suspicious user agent that may indicate an attack tool is being used.
Pick your preferred policy, deploy it, and you’re good to go to increase your Secure Score by 2 points!
5. Deploy a Log Collector to Discover Shadow IT Activity
A Log Collector is the best way to find shadow IT activities. 🤔Why, you ask? It offers automated, continuous monitoring of all network traffic without being limited to specific endpoints or a lot of hardware.
The Log Collector runs on your network and collects logs using Syslog or FTP. It processes, compresses, and sends the logs to the Defender for Cloud Apps portal.
- To start, log into the Defender for Cloud Apps portal and click on ‘Cloud Discovery.’
- Select the ‘Configure Automatic log upload’ page.
- In the Data Sources tab, click Add Data Source to create a source for your appliance.
- Then, in the Log Collector tab, click Add Log Collector to set up a new one.
- Follow the instructions provided to deploy Docker and the log collector container.
And that’s a wrap on the Defender Cloud Apps Secure Score recommendations! 🎉Now, the ball is in your court, analyze & implement based on your preferences.
Plus, in honor of Cybersecurity Awareness Month, we’re giving you the gift of knowledge. 🎁
- First on the list: A collection of essential Microsoft 365 security settings that’s often missed by admins.
- Another is a collection of powerful advanced security configurations for Microsoft 365.
Consider these gifts as our way of helping you protect your organization. Feel free to reach out if you have any queries!