Email accounts are one of the most frequently targeted entry points for cybercriminals, and a single compromise can lead to severe consequences. In fact, 91% of cyberattacks start with email, and attackers are always looking for ways to exploit human error or weak security to gain access to Microsoft 365 mailboxes. 😶
Once an attacker gains access to a user’s email account through phishing, stolen credentials or hijacking an active session, it becomes a powerful tool to spread more attacks. They can send phishing emails to other internal users, impersonate employees, manipulate conversations, and even steal sensitive data, all while going unnoticed.
That’s why securing a compromised email account is more important than ever. Just one compromised account can lead to a wide range of threats across your organization. In this blog, let’s explore the impact, how to detect, and respond to a compromised email account.
The Impact of a Compromised Microsoft 365 Email Account
Imagine a scenario where your finance lead’s email account is compromised. The attacker uses that account to send a convincing message to another team member, urging immediate payment to a fake vendor. Since the message appears to come from a legitimate company email address, it raises no red flags. By the time anyone realizes what’s happened, the payment is made, and the money is gone. 😨
The consequences of a compromised Microsoft 365 email account can be severe:
- 💸Financial loss: Organizations can lose anywhere from thousands to millions of dollars in fraudulent payments.
- 🔐Data exposure: Sensitive data, such as intellectual property or legal documents, can be leaked or stolen.
- 🎭Identity theft: Steal other users’ personal identity information (PII) and impersonate them to gain deeper access both inside and outside the organization.
These types of incidents are often linked to Business Email Compromise (BEC) attacks, which accounted for 73% of all reported cyber incidents in 2024. And BEC is just one of the many methods attackers use to exploit an organization once they’ve gained access to a single compromised mailbox.
Now that we understand the risks, let’s go step by step through the process of identifying and responding to a compromised email account in Microsoft 365.
How to Find a Compromised Mailbox in Microsoft 365
If you’re wondering whether a Microsoft 365 email account has been compromised, here are some red flags to look for. If you notice one or more of the following, the account may be at risk:
- Investigate risky sign-ins to identify unusual activity, such as logins from unfamiliar devices, suspicious geographic locations, or unknown IP addresses.
- With the introduction of linkable identifiers, admins can trace session ID–based audit logs to correlate incidents across Microsoft 365 and verify potential malicious activity.
- Multiple failed login attempts, which could indicate password spray attacks or brute force attacks.
- Emails that are missing or deleted without the user’s knowledge.
- Inbox rules that were added or changed without permission, especially the new mailbox rules that forward emails to external addresses or move them to hidden folders.
- New external email forwarding rules have been set up to automatically forward emails to external addresses.
- Frequent password changes or repeated account lockouts that the user didn’t cause.
- Unexpected changes to security settings, like recovery phone numbers or backup email addresses.
- Suspicious messages found in the Sent or Deleted Items folders.
- Changes to the user’s profile details, such as their name or phone number, in the Global Address List.
- Suspicious email signatures added or changed to impersonate someone else, such as a manager or executive.
- The user account is suddenly blocked from sending emails because Microsoft’s security measures detected suspicious or spam-like activity.
Noticing any of these warning signs? It’s a strong indicator that the Microsoft 365 mailbox may be compromised.
Secure a Compromised Mail Enabled Account in Microsoft 365
If you believe an attacker has gained access to a user’s Microsoft 365 account, it’s critical to take immediate action to block their access and prevent further damage. Follow these steps to secure a hacked Microsoft 365 email account:
- Disable the compromised Microsoft 365 account
- Revoke all active user sessions in Microsoft 365
- Notify the affected user and others
- Reset the user’s Microsoft 365 password
- Enforce Multi-Factor Authentication
- Remove any suspicious MFA-registered devices
- Review and revoke user consents to applications
- Find the M365 admin roles assigned to the user
- Check mailbox permissions and email forwarding
- Run a full antivirus scan on the user device
- Track compromised user account activities
1. Disable the Compromised Microsoft 365 Email Account
The moment you suspect an account has been compromised, disable it right away without any delay. This simple step instantly blocks the attacker from causing more harm and gives you room to investigate without interference. It’s your first line of defense, and acting fast can make the difference between a minor incident and a full-blown breach.
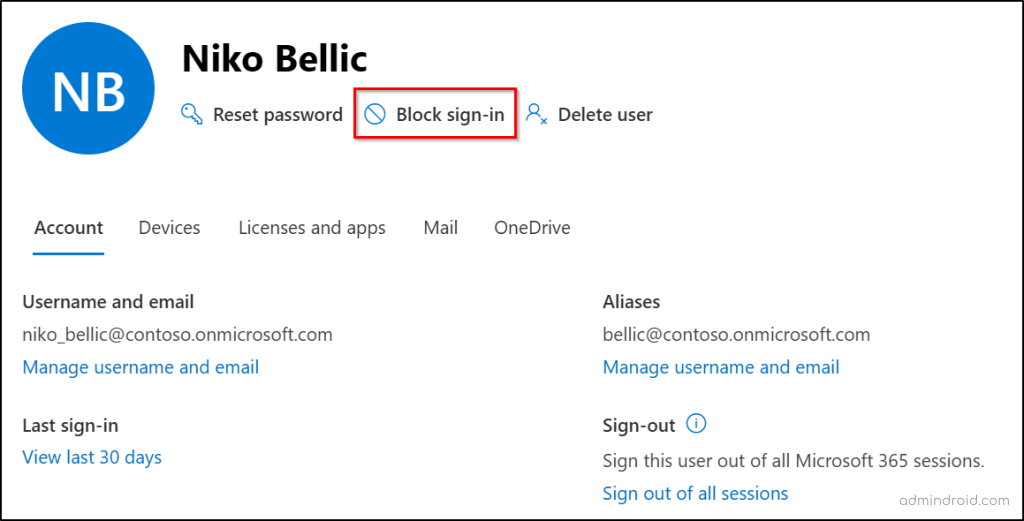
Follow these steps to disable a Microsoft 365 user account:
- Sign in to the Microsoft 365 admin center.
- Go to Users → Active users and select the affected user.
- In the user details pane, click Block sign-in to disable the account.
2. Revoke All Active Sessions of the Affected User in Microsoft 365
Disabling the user account in Microsoft 365 is essential, but they don’t end active sessions that may still be running on other devices or apps. If an attacker is already logged in, they might continue accessing data or performing unauthorized actions, even after you’ve taken other security steps.
That’s why it’s critical to revoke all active sessions immediately. This ensures the attacker is completely signed out and forced to reauthenticate, which they’ll fail if you’ve already secured the account.
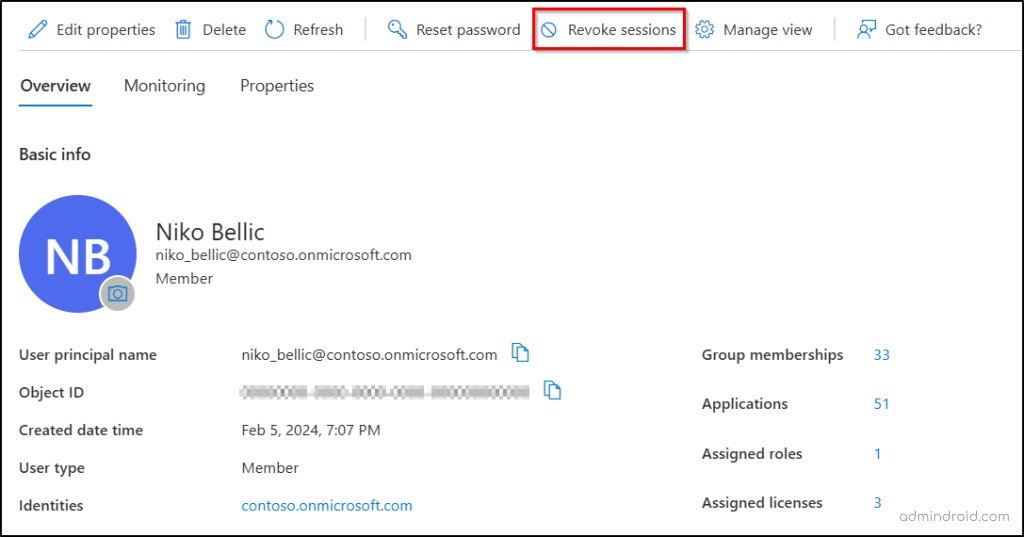
Follow the steps below to revoke all sessions of the user in Microsoft 365:
- Sign in to the Microsoft Entra admin center.
- Go to Users → All users, then select the compromised user account.
- On the user’s overview page, click Revoke sessions in the toolbar.
- Click Yes on the confirmation prompt to complete the action.
3. Notify the Affected User and Others
Business Email Compromise (BEC) often succeeds because no one realizes the account has been hacked. That’s why clear communication is critical. As soon as you confirm or suspect a compromise, inform the affected user immediately and alert your organization. Let others know not to respond to any emails from the compromised account without your explicit approval. Quick, transparent communication can stop the attacker in their tracks and prevent further damage.
4. Reset the Users’ Password in Microsoft 365
Resetting the password is a critical step in securing a compromised email account. Even if you disable the account temporarily, an attacker may still try to log in once it’s re-enabled, especially if the password hasn’t been changed. That’s why resetting it is essential.
More importantly, resetting the password helps stop the chain of compromise, since attackers often use one hacked Microsoft 365 account to gain access to others.
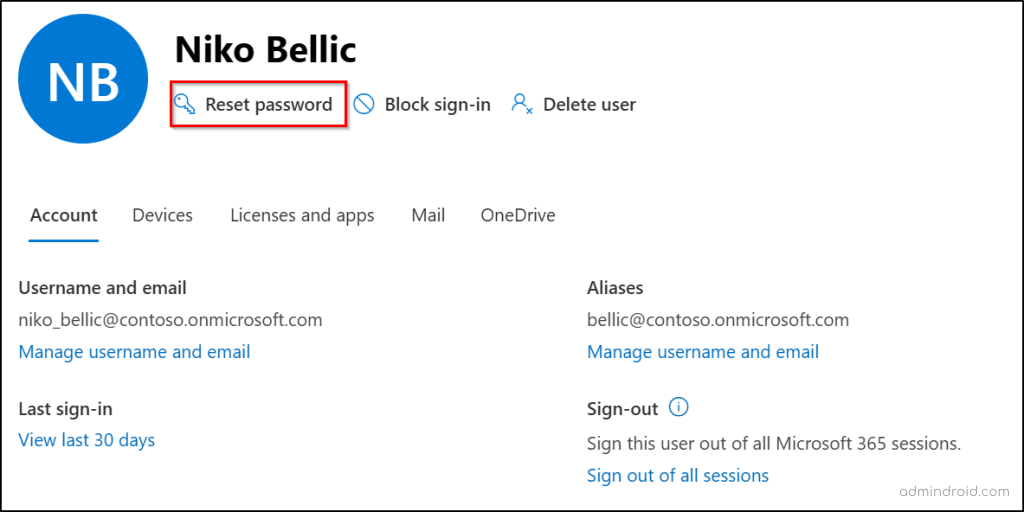
Follow these steps to reset a user’s password in Microsoft 365:
- Go to the Active users page in the Microsoft 365 admin center.
- Select the affected user and click Reset password.
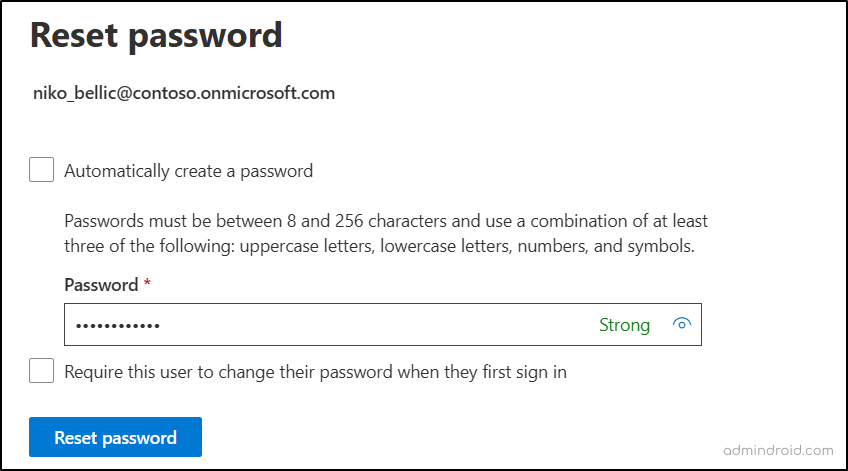
- If you want Microsoft to generate a password, check the Automatically create a password box.
- To create a custom password manually, enter it in the Password field.
- You can also check “Require this user to change their password when they first sign in“, based on your requirements.
- Click Reset password to update the user’s password.
When resetting a compromised user’s password, make sure it’s strong, unique, and secure:
- Avoid reusing old passwords or setting weak ones, as these are easily guessed and commonly targeted by attackers.
- Strengthen Microsoft 365 password policy to enforce strong password complexity settings and prevent the use of known weak or breached passwords.
- Ban custom passwords in Microsoft 365 to prevent users from using guessable passwords related to the company name, location, or common phrases.
- And most importantly, never send passwords over email, because the attacker could have access to the mailbox.
5. Enforce Multi-Factor Authentication for Compromised Email Account
The impact of enforcing Multi-Factor Authentication (MFA) for the compromised user account is a stronger defense against account compromise. You can configure MFA for the affected users in multiple ways, such as using security defaults, per-user settings, or Conditional Access policies. It adds a second layer of protection to help secure user accounts from phishing, brute-force attacks, and other threats.
Even if an attacker gets hold of the updated user credentials, MFA can still block their access by requiring an additional verification step. That’s why it’s crucial to enforce the user to complete MFA registration in Microsoft 365 environment.
6. Remove Suspicious MFA Registered Devices in Entra ID
If a user’s account is compromised, there’s a risk that the attacker may have registered their own device for MFA, giving them a way to bypass future login protections. Simply enabling MFA isn’t enough if the attacker is already on the trusted device list.
To fully secure the account, you must review and remove any unauthorized or suspicious MFA methods tied to the compromised user. This ensures only legitimate users can verify their identity and regain access.
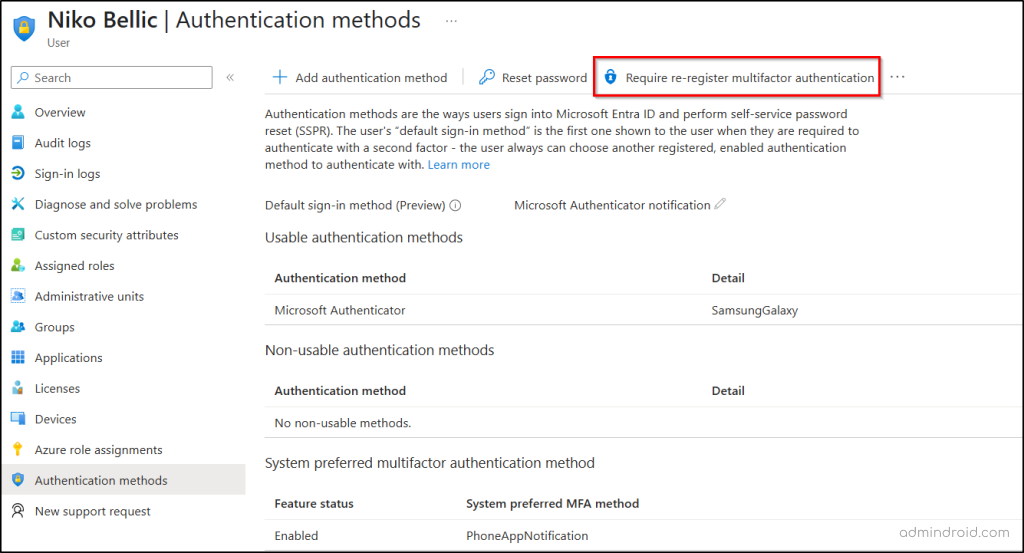
Follow these steps to remove suspicious MFA-registered devices from Entra ID:
- Go to the All users page in the Microsoft Entra admin center.
- Select the compromised user account, then navigate to Authentication methods.
- Review the list for any unknown or suspicious devices registered for authentication.
- If needed, click Require re-register multifactor authentication to force the user to set up MFA again on their next sign-in.
7. Review and Revoke Affected User Consent to Application
When an attacker gains access to a Microsoft 365 account, the damage isn’t always limited to email. In many cases, they silently authorize malicious apps to access the user’s data, even after you’ve changed the password or reset MFA. These applications can operate in the background, reading emails, accessing files, or exfiltrating data without being noticed.
That’s why it’s critical to review and manage user consent to applications. Revoking unnecessary or suspicious consents cuts off another potential access point that attackers might still control.
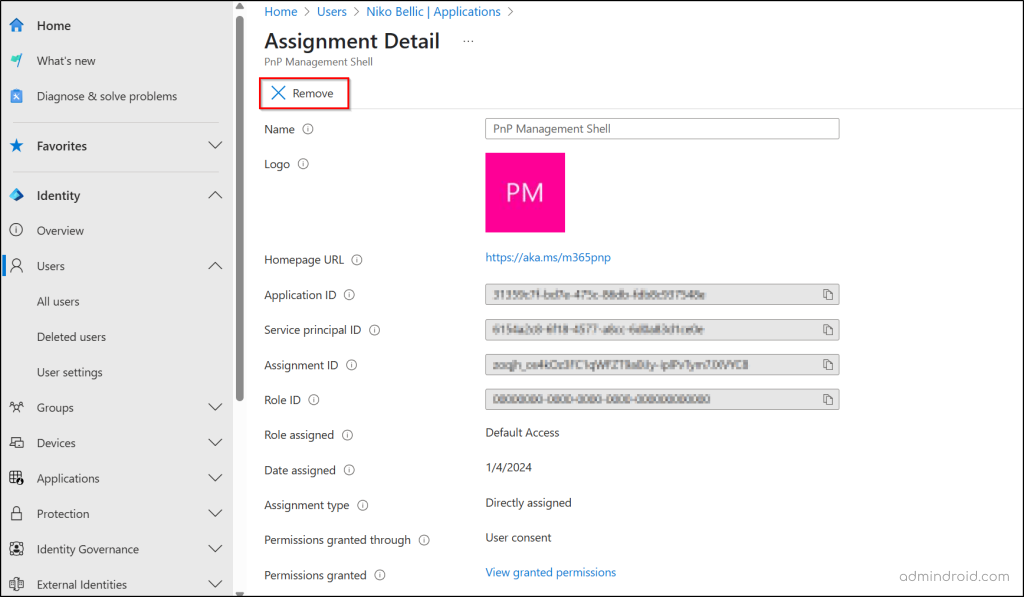
Revoke application permissions granted to a user by following the steps below:
- Go to the All users page in the Entra admin center.
- Click on the affected user, then select Applications.
- Find and click on any suspicious application assignments.
- Click Remove to revoke the user’s consent to the application.
8. Find and Remove Microsoft 365 Admin Roles Assigned to the User
A compromised account with admin privileges is a high-risk situation. Attackers can use those permissions to change configurations, access sensitive data, or even create new backdoor accounts. That’s why it’s critical to immediately check if the affected user has any Microsoft 365 admin roles assigned.
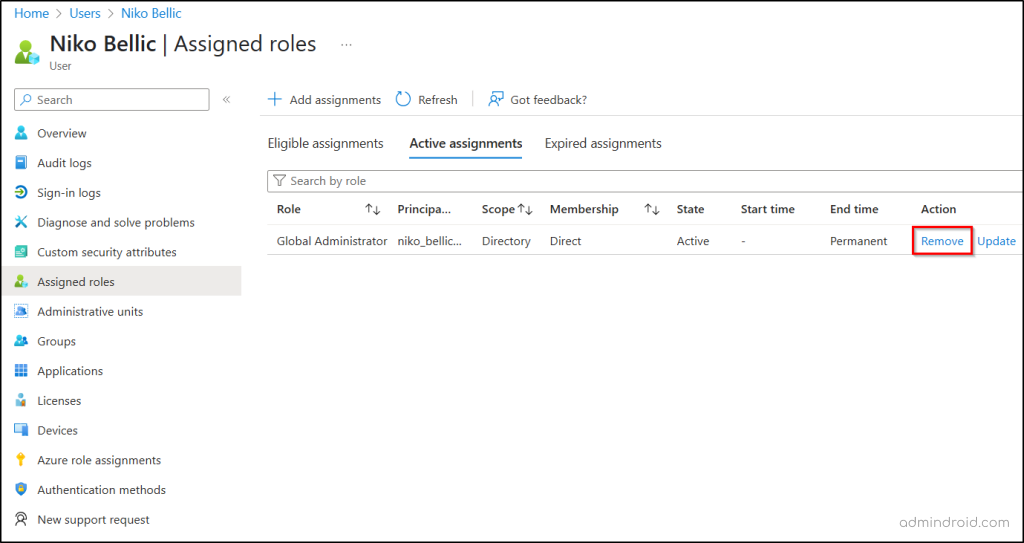
Follow these steps to find and remove any unnecessary admin roles from the compromised user:
- Go to All users in the Entra admin center.
- Select the compromised user from the list.
- Go to the Assigned roles tab to view all admin roles assigned to the user.
- Review the list and identify any roles that should not be assigned.
- Under the Action column, click Remove to revoke the role assignment.
9. Check Exchange Online Mailbox Permissions and Email Forwarding
Attackers often modify mailbox settings to maintain access or monitor communications even after the initial compromise. They may set up email forwarding rules to silently send copies of messages to external addresses. In some cases, they assign mailbox permissions like Read, Send As, or Send on Behalf to other suspicious addresses, allowing them to spy on the user’s emails. These hidden changes can go unnoticed and lead to further data leaks or misuse.
Therefore, make sure to check for any suspicious forwarding rules and delegated permissions on the compromised mailbox.
Use the steps below to check and clean up any suspicious forwarding rules or mailbox delegate permissions.
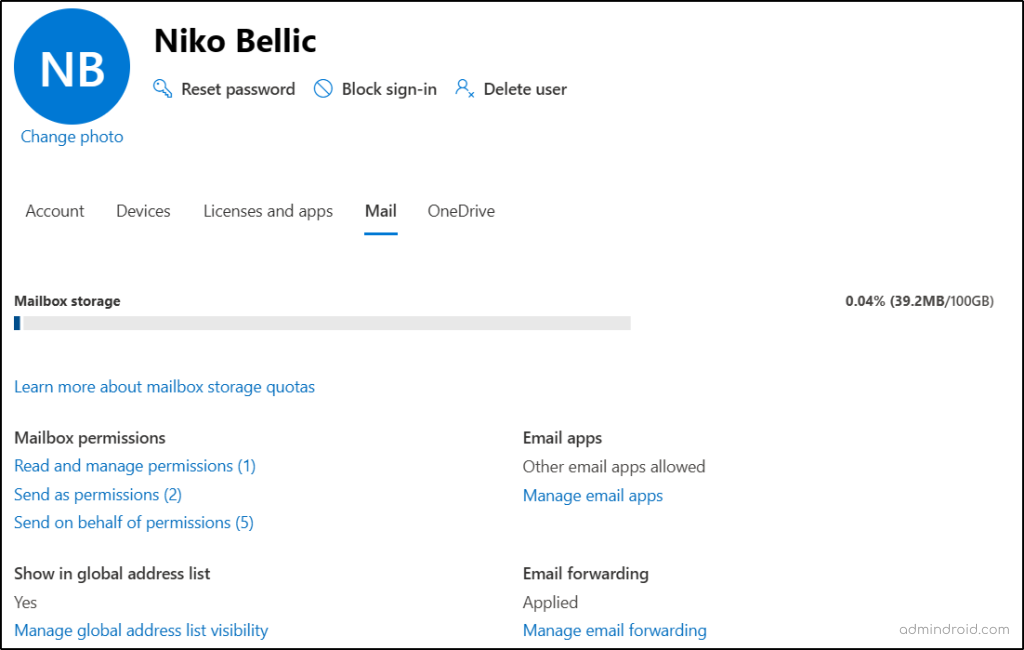
- Navigate to the Active users page in the Microsoft 365 admin center.
- Select the affected user and go to the Mail tab.
- If the text “Applied” is visible under Email forwarding, it means emails are being forwarded.
- Click Manage email forwarding to see the forwarding address. If it looks suspicious, uncheck Forward all emails sent to this mailbox and click Save changes.
- Next, check Mailbox permissions, including Read and manage permissions, Send as permissions, and Send on behalf permissions.
- If any unknown or suspicious users are listed, click on the user and select Remove permissions to revoke their access.
10. Run a Full Antivirus Scan on the Affected User’s Devices
After securing the compromised Microsoft 365 account, it’s essential to ensure that the device used by the affected user is clean and safe. Attackers often install malware like trojans, spyware, rootkits, keyloggers, or even worms to maintain access or steal more data.
Running a full antivirus scan helps detect and remove these hidden threats. Use a trusted antivirus or endpoint protection solution like Microsoft Defender to perform a deep scan of the affected machine. If you find malware, clean the device or replace it according to your organization’s incident response procedures. This step prevents reinfection and protects other accounts and systems from compromise.
11. Analyze the Microsoft 365 Unified Audit Logs to Trace Compromised Email Account Actions
Securing a compromised Microsoft 365 account is only part of the response. To fully understand the scope of the incident, it’s essential to track the unified audit log and investigate the actions taken using the account during the compromise.
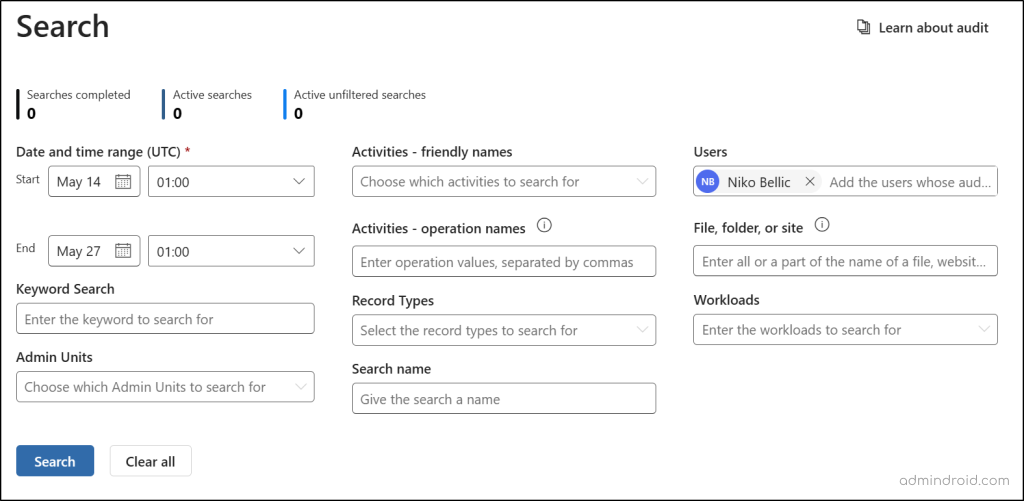
Microsoft purview audit logs allow you to trace user activities and identify any unauthorized or suspicious behavior. Filter the logs by selecting a date range that begins just before the unusual activity was detected. This helps pinpoint actions such as email forwarding, login attempts, permission changes, or data access that may indicate malicious use.
Automate Compromised Account Remediation in Microsoft 365 Using PowerShell
Dealing with compromised accounts is never pleasant, but it’s something every admin faces. When an account is flagged as compromised, time is critical. Every minute of delay increases the risk of data exposure or misuse.
However, performing a solid set of recommended remediation manually across each affected user can be tedious, inconsistent, and error-prone. That’s why we built a PowerShell script to automate the entire remediation workflow, saving you time and reducing the room for error.
Download Script: AutomateCompromisedAccountRemediation.ps1
This script is designed to handle the key steps Microsoft recommends when responding to a compromised user account. It wraps eight best practices into a single guided process, allowing you to act quickly and confidently.
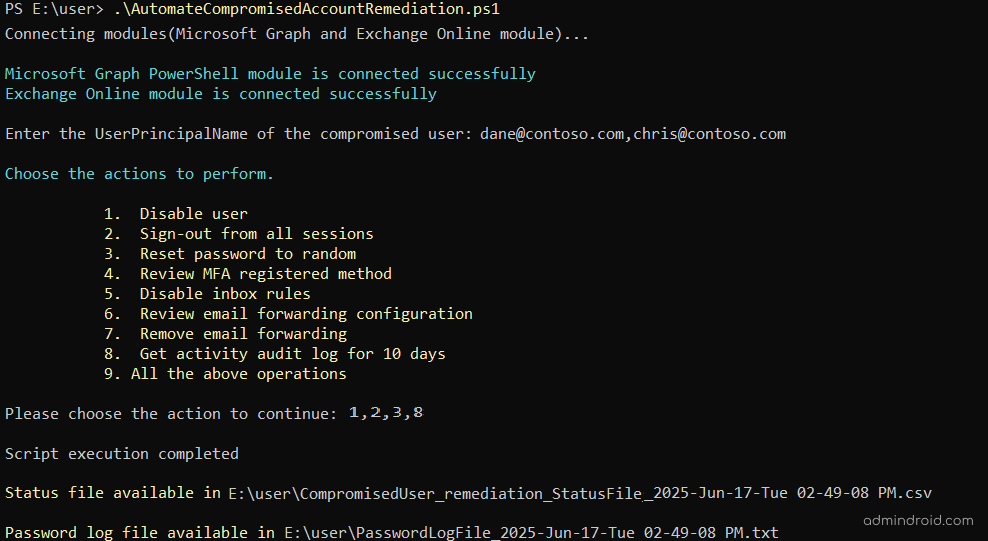
Upon execution of the above script, you’ll be prompted to enter the User Principal Names(s) (UPN) of the compromised Microsoft 365 account. Then, the script will prompt you to select the remediation steps you want to run.
Each selected action is executed in sequence, and the following log files are generated based on the inputs and execution scenarios to help you effectively follow up on the actions taken:
- Password Log File – List the newly created passwords of the users.
- Invalid User Log File – Flags any UPNs not found in your tenant.
- Error Log File – Captures any execution errors with details and error codes.
- Status File – Lists the last 10 days of activity for the compromised user account.
Wrapping Up
While these steps help you regain control over a compromised Microsoft 365 email account, it’s always better to be proactive. Preventing an account from being compromised in the first place is far more effective than recovering from one.
We hope this blog helped you identify and secure compromised mail-enabled accounts in your organization. If you have any questions or feedback, feel free to share them in the comments below. We’re here to help!






