Investigating suspicious activity in Microsoft 365 has always been a challenging task. While Microsoft Purview centralizes audit data, logs generated by each workload vary in structure, format, and identifiers. This makes it hard for analysts to connect events and trace an attacker’s actions. Linkable identifiers in Microsoft Entra solve this by assigning a consistent session-based ID across all logs, allowing analysts to correlate activities end-to-end. This unified approach makes it easier to trace attacker movement, detect anomalies, and respond to identity threats effectively. Let’s dive deeper into how they work and why they’re essential to track and investigate identity activities in Microsoft 365.
What Are Linkable Identifiers in Microsoft Entra ID?
Imagine an attacker successfully signs in to a compromised user account. They move between Outlook, SharePoint, and Teams, downloading files, sending emails, and creating new sharing links. Traditionally, SOC analysts had to manually correlate Microsoft 365 audit logs with user accounts and IP addresses to track malicious sessions. This approach was time-consuming and error-prone, especially when attackers moved laterally across services.
This is where linkable identifiers come in! Linkable identifiers in Entra ID are unique values that help security analysts trace user activity across Microsoft 365 services.
Microsoft Entra provides two types of linkable identifiers to strengthen identity threat detection and response:
- Session ID-based Identifiers (SID)
- Unique Token Identifiers (UTI)
Session ID-based Identifier (SID)
When a user signs in to Microsoft Entra, a unique session ID (SID) is created. This SID works like a name tag for that sign in session. Every access token (AT), refresh token (RT), and session cookie from that session carries the same SID. This lets you trace all actions like opening emails, downloading files, or using Teams back to one session.
Unique Token Identifier (UTI)
Alongside the SID, each token also has its own Unique Token Identifier (UTI), which works like a serial number for that specific token. While the SID groups activity within one session, the UTI helps trace the actions of a single token. This becomes especially useful if a token is stolen or reused by an attacker. With the UTI, analysts can pinpoint exactly what that token accessed, when it was used, and from where. It also allows the team to revoke just the compromised token without ending the entire session.
Both the SID and UTI are recorded in Microsoft Entra sign in logs and Microsoft 365 service audit logs like Exchange, SharePoint, and Teams. This gives analysts a simple way to see all activity and investigate suspicious behavior.
This end‑to‑end visibility strengthens identity threat detection and response with linkable identifiers.
Where Can You Find Linkable Identifiers in Microsoft 365?
To support advanced investigations, Microsoft provides log availability for linkable identifiers across multiple logging sources, including:
- Microsoft Entra sign-in logs
- Microsoft Exchange Online audit logs
- Microsoft Graph activity logs
- Microsoft SharePoint Online audit logs
- Microsoft Teams audit logs
This table shows the mapping between linkable identifier claims and various Microsoft 365 audit log attributes.
| Claim | Format | Description | Entra Sign‑in Logs | Exchange Online Audit Logs | Microsoft Graph Activity Logs | SharePoint Online Audit Logs | Teams Audit Logs |
| Oid | String (GUID) | Unique ID of the user or service principal. | User ID | TokenObjectId | UserId | UserObjectId | UserKey |
| tid | String (GUID) | ID of the tenant the user signed into. | Resource Tenant ID | TokenTenantId | TenantId | OrganizationId | OrganizationId |
| sid | String (GUID) | ID for the entire sign‑in session. | Session ID | SessionID / AADSessionId | SessionId | AADSessionId | AADSessionId |
| deviceid | String (GUID) | Device ID (only for registered/domain‑joined). | Device ID | DeviceId | DeviceId | DeviceId | DeviceId |
| uti | String | Unique per‑token identifier (case‑sensitive) | Unique Token Identifier | UniqueTokenId (within App Access Context) | SignInActivityId | UniqueTokenId (within App Access Context) | UniqueTokenId (within App Access Context) |
| iat | Integer (Unix timestamp) | Time when the token was issued. | Date | IssuedAtTime (within App Access Context) | TokenIssuedAt | IssuedAtTime (within App Access Context) | IssuedAtTime (within App Access Context) |
Once you know where to locate these identifiers, analyzing each workload becomes much easier.
How to Investigate Identity Activities Using Linkable Token Identifiers?
Follow these steps to trace suspicious sessions and uncover hidden risks using specific Session ID (SID) or Unique Token Identifier (UTI) in Microsoft 365.
- Find Session ID in Microsoft Entra sign-in logs
- Trace Session ID-based activities across Microsoft 365
- Confirm to identity threat and respond
1. Find Session ID in Entra ID Sign-in Logs
tart with Microsoft Entra sign-in logs to pinpoint where the suspicious session originated.
Every sign-in log in Entra includes linkable identifiers like SID and UTI, which are essential for tracing user activity across Microsoft 365. If you’re wondering how to locate Session ID in Entra logs, it is available in the log entry details and can be used to correlate all related activities.
- Sign in to the Microsoft Entra admin center with at least a Reports Reader role.
- Go to Microsoft Entra ID –> Monitoring & health –> Sign-in logs.
- Filter by time range or a specific user to locate relevant log entries.
- Upon selecting a log entry:
- The Basic Info tab provides the User ID, Resource Tenant ID, Session ID, Unique Token Identifier, and Date.
- For registered or domain-joined devices, the Device ID can be found in the Devices tab.
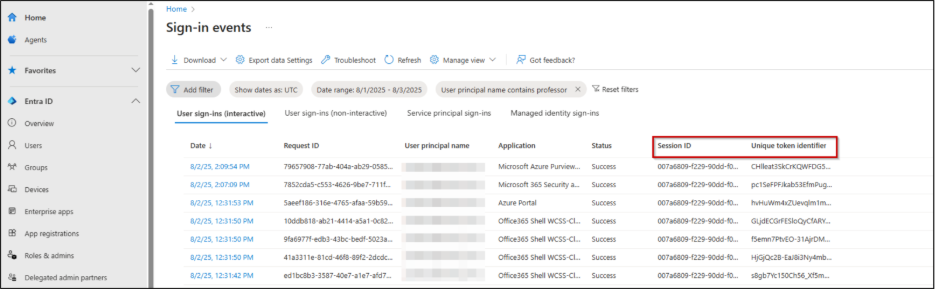
These identifiers are key to correlating activities across Microsoft 365 services. Not all applications send Session IDs with their audit events, which can limit activity correlation across Microsoft 365.
Tip: Besides reviewing Entra ID sign‑in logs directly, you can create a custom Workbook in Microsoft Entra to visualize all activities tied to a specific Session ID (SID).
2. Export Session ID-based Activities Across Microsoft 365
Once you have the Session ID and Unique Token Identifier from the Entra sign-in logs, you can use them to connect the dots across Microsoft 365 audit logs. The goal is to see exactly what the compromised user did after the suspicious sign-in.
Microsoft 365 audit logs provide detailed records of user activity but searching them effectively can be difficult due to inconsistencies in how different services store session identifiers.
To simplify this process, we developed a PowerShell script to efficiently export user activity logs linked to a specific SID.
Correlating User Activities Across Microsoft 365 Using PowerShell
The script helps security teams rebuild the user’s activity timeline by collecting session ID-based audit logs in a consistent and easy-to-analyze format. It reduces manual effort and accelerates investigations by turning raw audit data into an actionable report.
Script Highlights:
- Retrieves all activities performed during a specific session. By default, it can access up to 180 days of data. You can customize the date range using the StartDate and EndDate parameters.
- Generates a well-organized, user-friendly CSV report for immediate use.
- Supports execution via Certificate-Based Authentication (CBA).
Script Execution Methods:
After downloading the script, execute it using any of the methods listed below.
Method 1: Execute the script with MFA or non-MFA account.
|
1 |
./UserSessionAuditReport.ps1 |
This format prompts you to enter a Session ID and UPN at runtime and retrieves user activity logs for that session over the default 180-day period.
To specify a custom date range, execute the below:
|
1 |
./UserSessionAuditReport.ps1 -SessionID <SessionID> -UserID <upn> -StartDate <startdate> -EndDate <enddate> |
Make sure to replace the placeholders with your actual values. This helps you focus on the exact window of suspicious activity.
Method 2: Run the script using certificate-based authentication.
To use the CBA, you must register the app in Entra ID which helps you to connect Exchange Online using certificate.
|
1 |
./UserSessionAuditReport.ps1 -Organization <Domain> -ClientId <AppId> -CertificateThumbprint <CertThumbPrint> |
Depending on the requirements, you can use either CA certificates or create self-signed certificates.
Sample Output
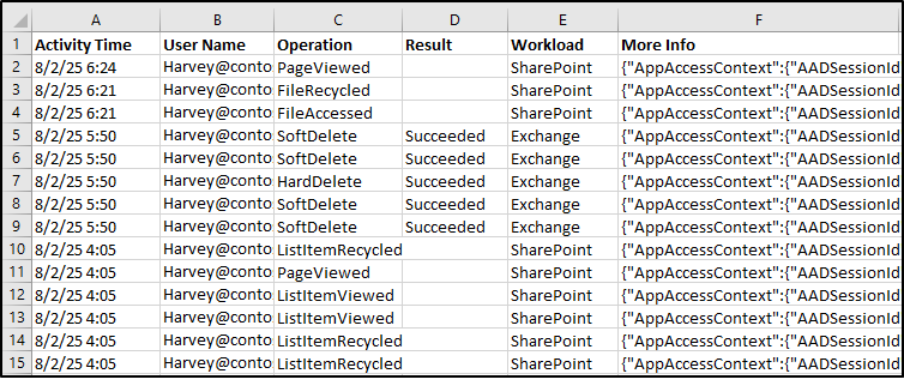
The script exports sessionID-based audit logs with the following attributes:
- Activity Time
- User Name
- Operation
- Result
- Workload
- Detailed Audit Info
3. Confirm to Identity Threat and Respond
If the timeline confirms malicious activity or data exfiltration:
- Revoke the active session in Microsoft Entra to invalidate all tokens.
- Reset the user’s credentials and enable MFA to secure the account.
- Continue monitoring for any suspicious follow‑up activity.
By analyzing and exporting logs, security teams can secure compromised accounts with a clear trail of events that supports rapid investigation and remediation.
With linkable identifiers in Microsoft Entra ID, organizations can achieve end‑to‑end visibility and make investigations faster and more reliable. I hope this blog helped you understand how to use SIDs and UTIs for better identity threat detection.
If anything is unclear or you need help, feel free to ask in the comments.