Day 3 of the Microsoft Entra Practitioner Series transitioned from building the foundational setup for unified identity and network access to a real hands-on deployment experience through the Microsoft Entra Suite Workshop.
In case you missed the earlier sessions, here’s a quick recap:
- Day 1: Unify Identity and Network Access for Zero Trust Security
- Day 2: Unified Identity and Network Foundation for Entra Suite
On Day 3, all the speakers focused on the Microsoft Entra Suite Workshop, presenting an actionable, step-by-step strategy to streamline every feature within the suite. The session moved beyond foundational concepts and guided participants through practical deployment scenarios, helping them translate Zero Trust principles into implementation.
The workshop primarily covered:
- Establishing a baseline and getting started
- Securely onboarding your workforce
- Modernize VPN and protect legacy apps
- Secure access to all internet resources
Without further delay, let’s dive into why each stage matters and how you can get started to build a unified, secure, and modern identity environment with Microsoft Entra Suite.
Breaking the Myth: Premium Security Tools ≠ Guaranteed Protection
Merill Fernando highlighted a common misconception among practitioners: that deploying premium security tools guarantees better protection. In reality, the Secure Employee Access in the Age of AI report shows that 94% of organizations experienced an identity or network access incident in the past year, demonstrating that increased complexity often amplifies risk.
That’s why the Microsoft Entra Suite Workshop matters — it focuses on simplifying and integrating security solutions to build true resilience. It also breaks down the silos between identity and network security, unifying them to close critical protection gaps.

Then, Ramero Calderon highlighted that the workshop provides a roadmap for using Entra features in the right order, based on best practices, to achieve next-level security while simplifying your environment. This structured approach reflects the workshop’s core motto: to simplify, integrate, and implement security solutions in a way that strengthens overall resilience.
How to Use the Microsoft Entra Suite Workshop
Martin Coetzer walked through what the workshop is and how to use it effectively. The Microsoft Entra suite workshop is essentially a spreadsheet of clear, practical steps designed to help organizations address identity and access challenges, tailored for decision-makers and stakeholders.
Before diving into the workshop, it is crucial to bring the right people together and ensure everyone understands each feature in the suite. This is where the Microsoft Entra Workshop Delivery Guide comes in. It explains who should use the workshop, the key objectives, and how to plan and structure it for maximum impact.
In the Microsoft Entra Workshop, there are five stages, and each corresponds to a separate sheet with recommendations presented in compact swim lanes for easy navigation and implementation. It is important to review each recommendation carefully, one by one.
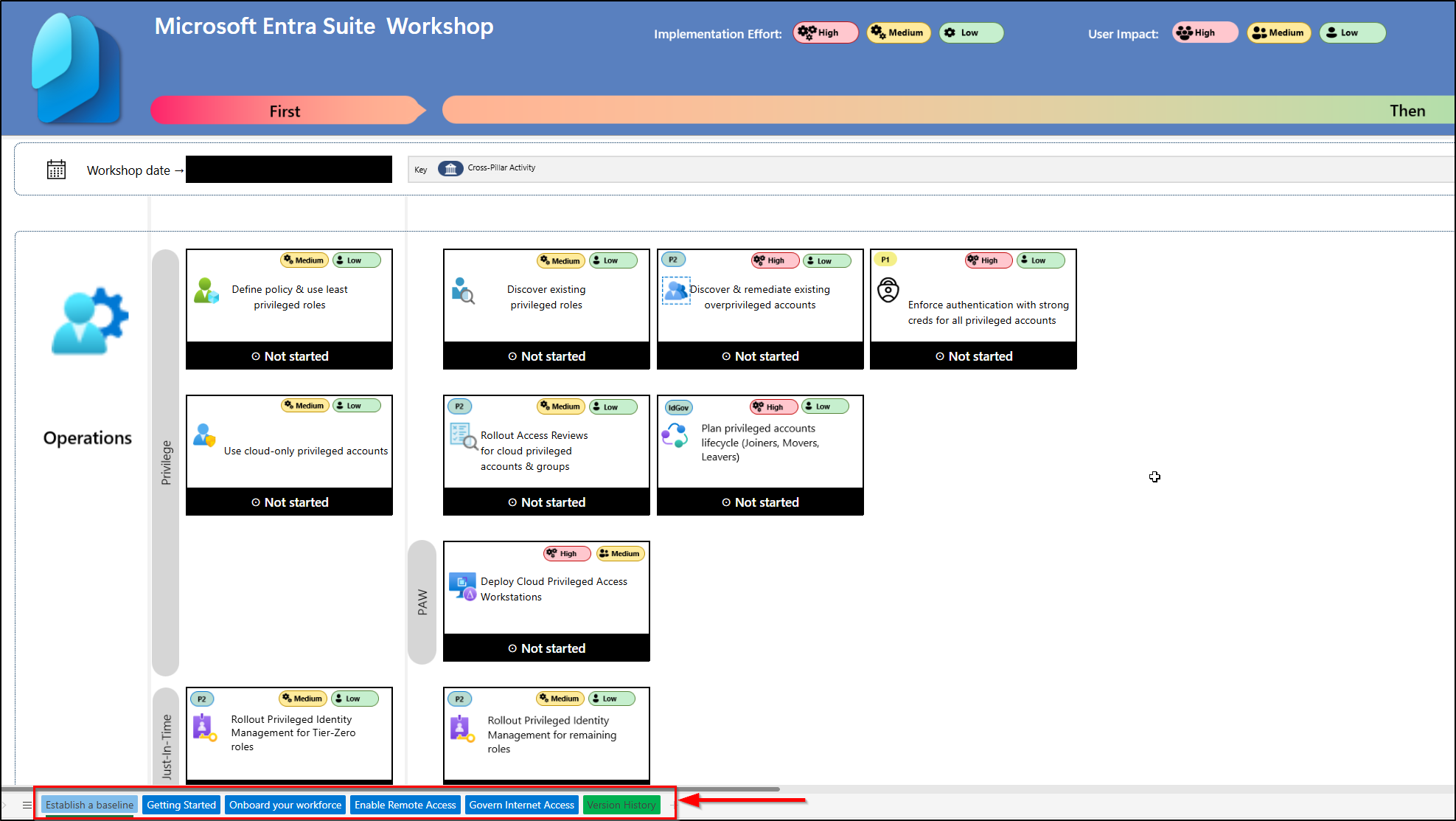
Clicking on a suggestion redirects you to a more detailed document, which may include references and related links for further information on that specific recommendation. For example, if you click the “Define policy & use least privileged roles” recommendation, you will be navigated to the corresponding Microsoft guide.
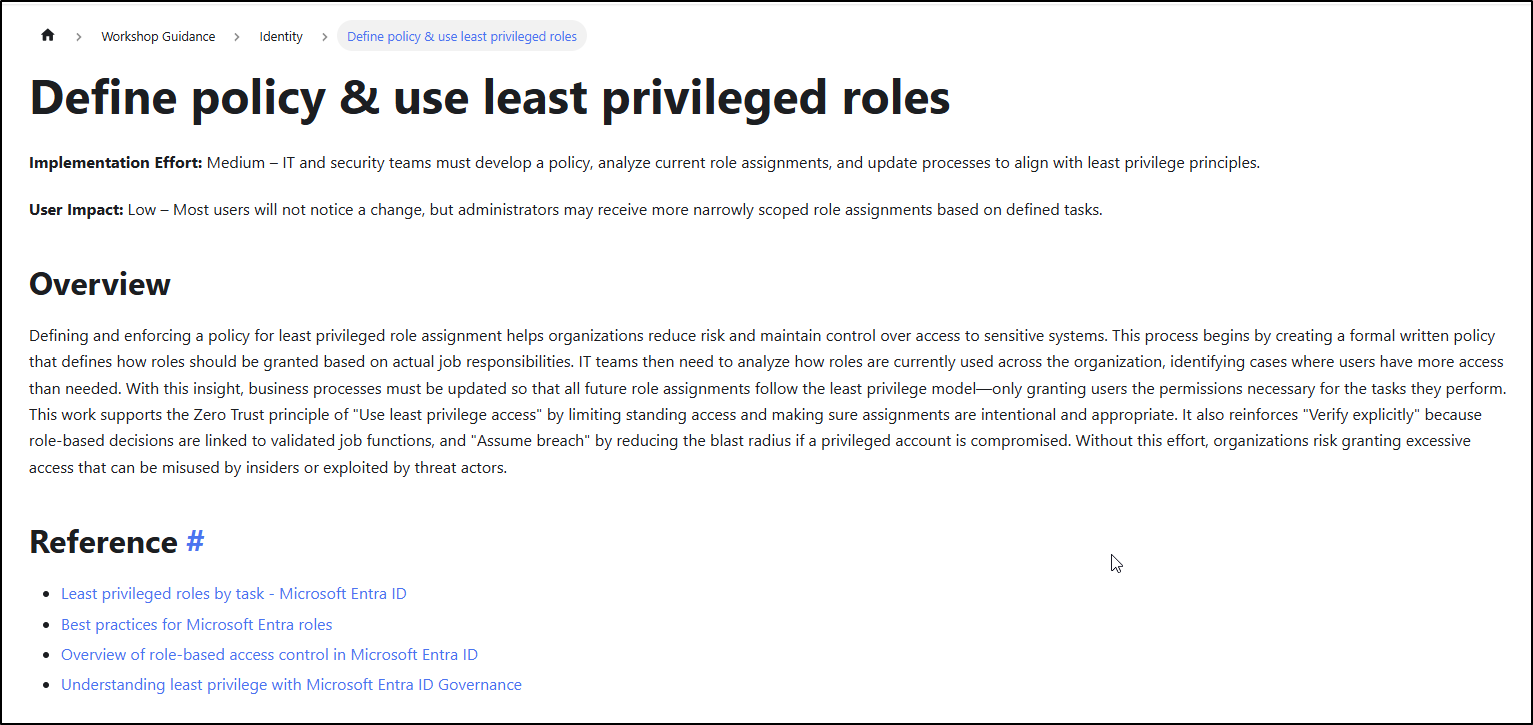
Once you understand it, you can use the state dropdown to mark its progress, such as planning, completed, and so on. Each recommendation also shows implementation effort and user impact. Implementation effort reflects the administrative work required, while user impact indicates how it might affect productivity.
These details are critical for informed decision-making and help prioritize actions effectively. Additionally, you can create multiple copies of the sheet for use with different customers and add notes to each suggestion.
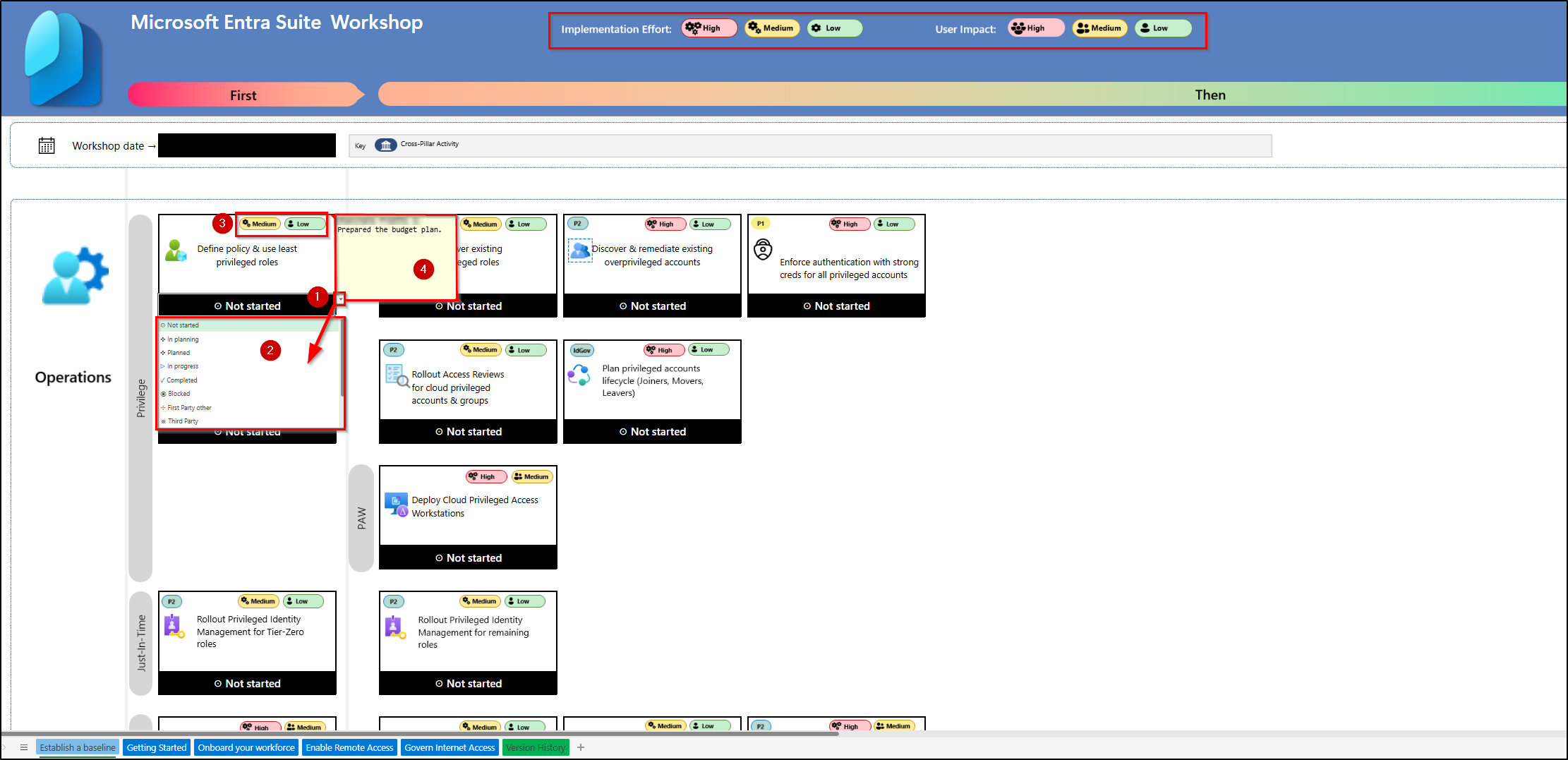
The Five Sections of the Microsoft Entra Suite Workshop
The Microsoft Entra Suite Workshop is organized into five sheets:
- Establish a Baseline
- Getting Started
- Onboard Your Workforce
- Enable Remote Access
- Govern Internet Access
Out of the five stages, the first two, ‘Establish a Baseline’ and ‘Getting Started’, cover the basics and were mostly addressed in Day 2 of the Microsoft Entra Practitioner sessions. These stages are essential for establishing the correct foundation before deploying the features in the suite and should be completed before moving on to the last three stages of the workshop.
1. Establish a Baseline
At this stage, you can find all the baseline recommendations related to privileges, just-in-time access, and SecOps. For example, the recommendation of Define policy and use least privileged roles aligns well with a Zero Trust posture, where unnecessary access is avoided and users are granted only what they need. Completing these steps builds confidence in your security foundation. Another important recommendation is to roll out Privileged Identity Management (PIM) for Tier-zero roles. However, many stakeholders set it up and forget it, so combining this with regular access reviews is crucial to monitor user activity and ensure your environment stays secure.
Many customers and practitioners set up security recommendations such as PIM and least privileged roles and then move on, but ongoing review is critical. Monitoring user behavior ensures that policies are being followed and that the organization remains protected from potential threats.
2. Getting Started
In this stage, Microsoft Entra provides recommendations related to application access, users and groups, and basic identity governance. For example, the first recommendation is to design a Conditional Access posture, which includes steps such as deploying Conditional Access with authentication strength controls for guest accounts, network and legacy app access, and SharePoint Online sites.
Along with this, make sure to review each recommendation, as they lay the groundwork for the more advanced steps. With that foundation in place, let’s now focus on the more advanced and critical stages of the workshop to roll out Microsoft Entra suite.
3. Onboard Your Workforce
The Onboard Your Workforce stage consists of four blocks of tasks arranged in swim lanes, with dependencies flowing from left to right. Each block focuses on a critical area to ensure secure and efficient workforce onboarding.
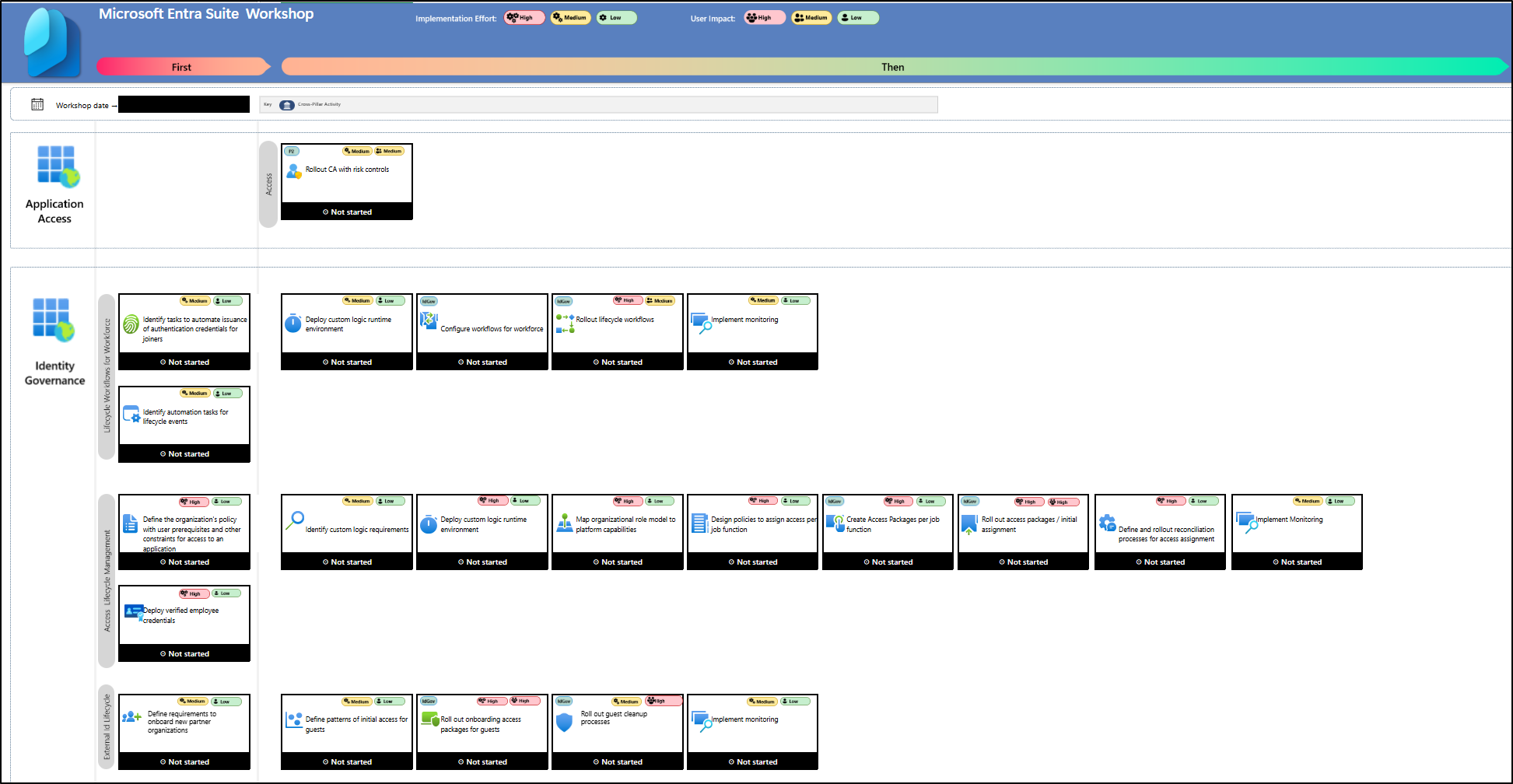
a. Application Access
Ramero Calderon emphasized that the first block focuses on Application Access, which includes the task of rolling out Conditional Access (CA) with risk controls such as sign-in risks and user risks. Deploying risk-based Conditional Access enables dynamic access decisions and significantly strengthens the organization’s security posture.
b. Identity Governance
- Lifecycle Workflows for Workforce
This block focuses on managing the joiner, mover, and leaver lifecycle within the organization. He illustrated this with a scenario where an HR data source feeds user information into Entra, enabling automation for issuing authentication credentials to new joiners. He stressed the importance of identifying the technical prerequisites for these automation tasks.
Once identified, you need to configure lifecycle workflows for workforce management, and the linked document provides techniques to implement them. You can also add Logic Apps, an extended capability that works with workflows to automate complex tasks and improve efficiency. A monitoring strategy should also be in place to track automation outcomes—for example, setting up alert systems to detect when a task fails.
- Access Lifecycle Management
Managing the lifecycle of user access ensures that employees have the right permissions based on their job function while preventing unnecessary access. This involves creating access packages in entitlement management tailored to each role and granting access accordingly. The workshop outlines step-by-step tasks to create these access packages, requiring user authentication and enabling organizations to follow their regulatory or risk management policies.
Ramero Calderon highlighted one key task: “Define and roll out reconciliation process for access provisioning.” This involves regularly validating that provisioned users are active, correctly scoped, and have accurate attributes. Administrators can monitor provisioning logs in the Microsoft Entra admin center to detect anomalies such as skipped users, attribute mismatches, and other inconsistencies, ensuring secure and compliant access management.
- External User Lifecycle
The External Identity Lifecycle closely mirrors internal workforce onboarding and can often be managed in parallel. It involves defining requirements for new partner organizations, identifying initial guest access patterns, and aligning them with access packages to provide appropriate permissions. Subsequent tasks include cleaning up inactive guests and monitoring guest access to maintain security.
4. Enable Remote Access
Once users have been onboarded and granted access, the next focus is application access for their day-to-day work. Microsoft Entra serves as a gateway to application access, addressing the challenges of organizations that use both cloud and on-premises applications. Traditionally, this was managed through VPNs, which provided broad access to all applications. The Entra Suite introduces capabilities to modernize VPNs and enable secure remote access, minimizing unnecessary access and aligning with Zero Trust principles.
Thomas Detzner walked us through the Enable Remote Access stage, beginning with a key principle: stop buying or building applications that depend on Active Directory. Before the Entra Suite, organizations had to modernize applications manually, especially web-based ones. For on-premises applications such as those hosted on SAP servers, they often relied on third-party partner solutions to enable remote access. With Global Secure Access in the Entra Suite, there is now a built-in capability to overcome these limitations.
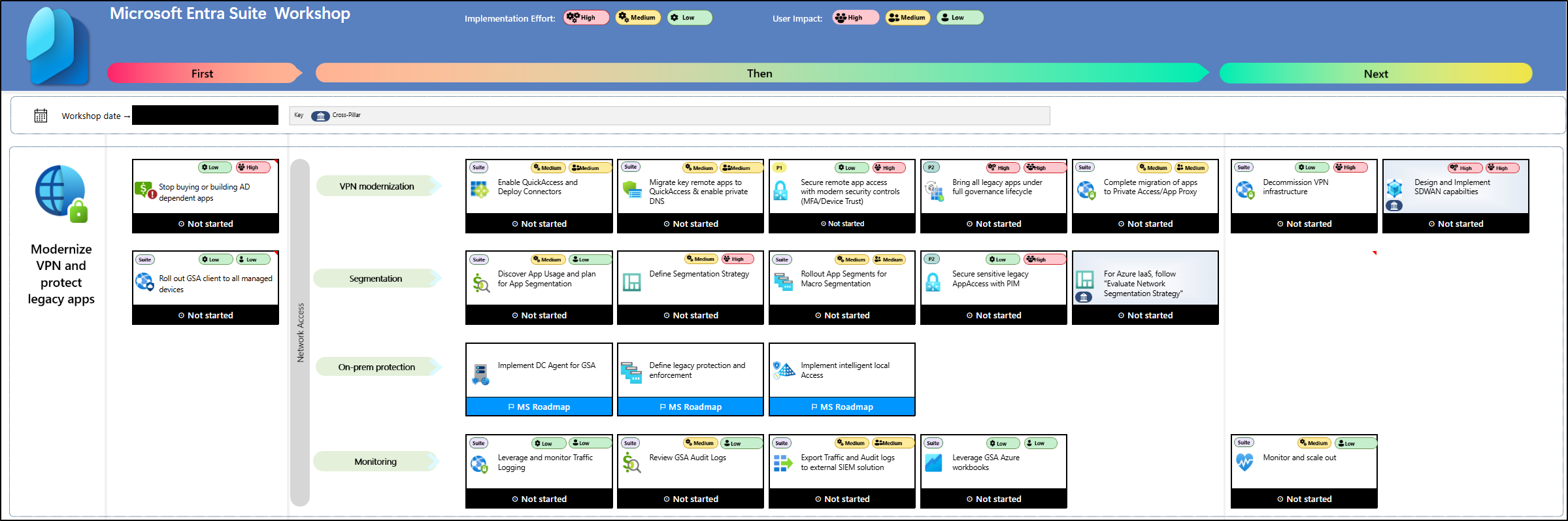
a. VPN modernization
To begin modernizing VPN, enable Quick Access in Microsoft Entra Global Secure Access, which serves as an easy first step in transforming traditional VPNs into Entra Private Access. You can then deploy connectors to establish secure connections with your on-premises environment.
Next, migrate or integrate remote applications to Quick Access and enable private DNS to allow internal name resolution for remote clients. In line with the Zero Trust model, extend modern security controls such as MFA, Conditional Access, and device trust to these remote applications. These apps or app segments are stored as enterprise applications within your tenant, making them easier to manage.
Once integrated, bring all legacy applications under a full governance lifecycle, enabling access packages and access reviews without requiring changes within the apps themselves. The following steps involve completing migration of applications to Private Access or App Proxy and decommissioning traditional VPN structures. Finally, design and implement SD-WAN capabilities to strengthen performance and secure connectivity.
b. Segmentation
Segmentation starts with understanding application usage by identifying which applications your users actually access. As Merill Fernando noted, many organizations lack visibility into app usage, and in some cases, users are granted organization-wide access, such as permissions to all servers, which increases vulnerability. Many customers also struggle with outdated VPN profiles and their management.
Thomas Detzner said that to address this, you should start by turning on discovery to identify application usage within your organization. While discovery runs, begin defining your segmentation strategy, deciding how granular you want it to be and grouping applications accordingly. Once segmented, you can secure access to sensitive legacy applications using Privileged Identity Management (PIM) controls. Additional guidance on handling Azure IaaS and evaluating your network segmentation strategy is provided in the workshop sheet.
c. On-prem protection
A few new capabilities are on the roadmap, currently in private preview, to enhance performance and security. These include a DC agent for GSA, richer controls for domain controllers, legacy app protection, and intelligent local access to route traffic efficiently while maintaining secure on-premises application access.
d. Monitoring
The final swim lane focuses on monitoring, covering traffic logging, GSA audit logs, exporting data to SIEM solutions, and using customizable Workbooks to tailor monitoring to organizational needs. Monitoring plays a critical role in enforcing a Zero Trust approach, and native Sentinel integration is available for seamless security analytics and threat detection. Additionally, for a deeper dive into implementing a Zero Trust approach, there is a dedicated Zero Trust workshop that you can check out.
5. Govern Internet Access
Merill Fernando raised an important question: how can organizations protect users from malicious cloud applications and unsafe websites? How does the Entra Suite help address these challenges?
Thomas Detzner explained that this is where Entra Internet Access comes in, providing a clear roadmap for securing web traffic and cloud applications.
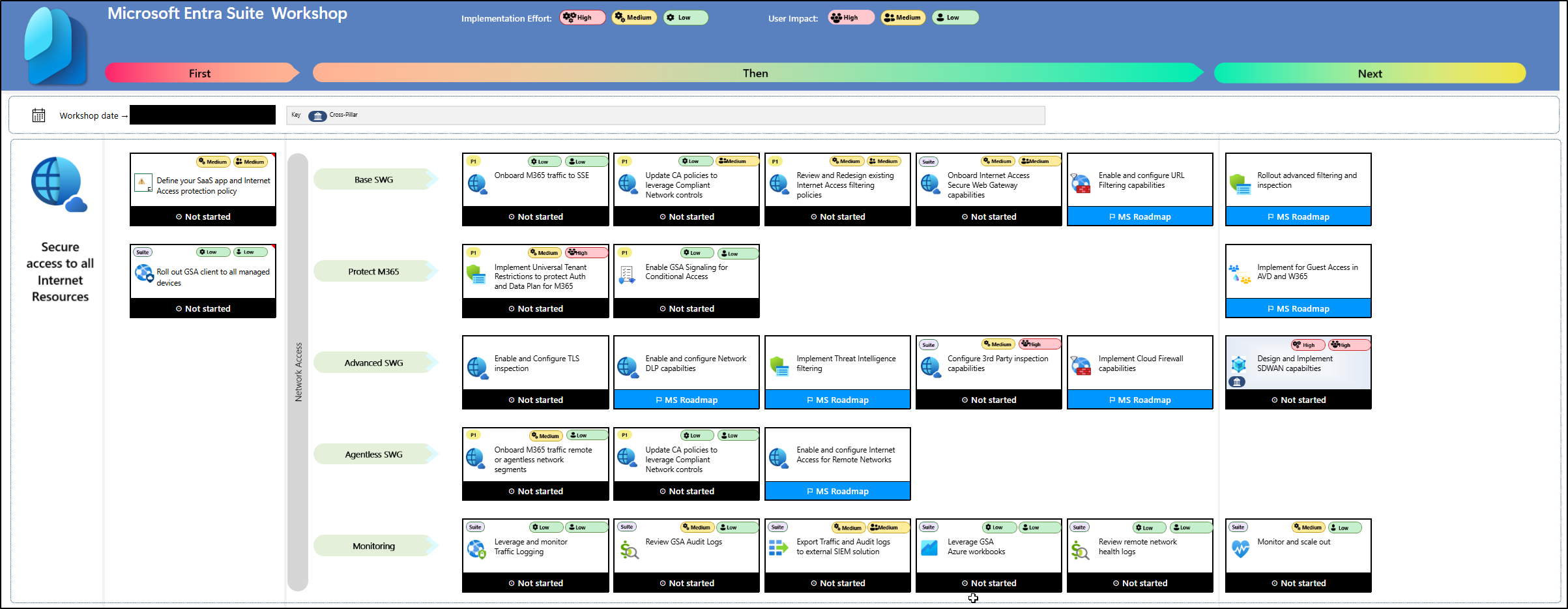
a. Base Secure Web Gateway (Base SWG)
The Base SWG stage consists of multiple steps in the workshop swim lane. Thomas emphasized that the first step is onboarding Microsoft 365 traffic using Microsoft Entra Internet Access. He also highlighted the recommendation to use Conditional Access policies in combination with Global Secure Access to prevent malicious access to Microsoft apps, third-party SaaS applications, and private line-of-business (LoB) apps. Exploring each recommendation in the swim lane is key to properly implementing the Base SWG.
b. Protect Microsoft 365
After deploying Base SWG, the next step is to protect Microsoft 365 using new capabilities such as Universal Tenant Restrictions. This feature safeguards both the authentication plane and data plane when accessing Microsoft 365 services. Previously, many organizations relied on proxy servers and complex configurations; with Universal Tenant Restrictions, admins no longer need to manage these proxies, and it also helps prevent data exfiltration for any app integrated with Microsoft Entra ID.
c. Advanced Secure Web Gateway
In this stage, he stressed enabling TLS inspection to apply deep and granular security controls, including advanced threat detection, content filtering, and compliance monitoring, even for encrypted sessions. This approach also helps prevent users from accidentally uploading sensitive data into AI tools. Additional capabilities such as network DLP, threat intelligence filtering, and cloud firewall are also on the roadmap under Advanced SWG and are currently in private preview.
d. Agentless SWG
Agentless SWG is useful when you cannot deploy an agent or the GSA client to certain users, such as B2B guests or partner users who need access to your applications. It allows you to protect and filter their access without requiring installation on their devices. This capability supports Microsoft 365 traffic, compliant network controls, and general internet access, ensuring secure access for external or unmanaged users.
e. Monitoring
As with all other stages, a horizontal monitoring swim lane is included here. It encompasses traffic logging, GSA audit logs, exporting data to external SIEM solutions, and customizable Workbooks to meet organizational needs. Additionally, remote network health logs are captured under the implementation of the Agentless SWG scenario, providing visibility into network performance and security.
That’s it! We hope this recap helps you understand how the Microsoft Entra Suite Workshop can elevate your unified identity and network access, strengthening your Zero Trust security posture. Finally, the Entra Suite also dispels the myth that identity and network are separate, by bringing them together and closing several critical gaps. Happy reading!