On Day 5 of Cybersecurity awareness month, learn to conceal your organization by blocking user consent to suspicious applications. Stay tuned for more blogs in Office 365 Cybersecurity blog series.
Have you ever heard about the illicit grant consent attack in Microsoft 365? It’s a consent phishing attack where a malicious attacker creates an Entra-registered application asking for basic permission such as reading email address or extensive permissions like accessing OneDrive. Users in Office 365 who are unaware of this cruel strategy fall into this trap, that leads to compromise and theft of valuable organizational data.
Sadly, MFA and other basic security methods will no longer protect the organization against these types of attacks, leaving them vulnerable to severe security risks.
We have an illusion of security; we don’t have security!
– Issac Yeffet.
It is evident that email phishing is targeting many Microsoft 365 organizations every year. However, some enterprises are falling prey to an emerging scam, consent phishing attack.
Do you know that O365 Admins are the ones who allow data leakages?
As we all know, Microsoft usually provides numerous hidden security configurations that help to safeguard enterprise data. Despite this, some critical default settings aren’t configured as expected according to the admins’ security preferences.
As a result, attackers can cleverly enter your organization by bypassing MFA and other basic security configurations in your Office 365. Hence, admins should keep an eye on default settings and check whether those settings restrict users’ access to O365 data.
Risks of Installing an OAuth 2.0 Supported Third-Party Application
Third-party applications can highly scale our workflow and time management to a greater extent. When an O365 user adds an external application that supports OpenID connect or OAuth 2.0 frameworks, it may ask for consent to read, write permissions, document access, email address, etc.
However, some suspicious applications will use that privilege and ask for access to all your sensitive data via the prompt below. Unknowingly, a poor user hits ‘Accept’ and agrees to all permission requests, allowing the vicious app to steal sensitive information that provides more opportunities for an attacker to access it.
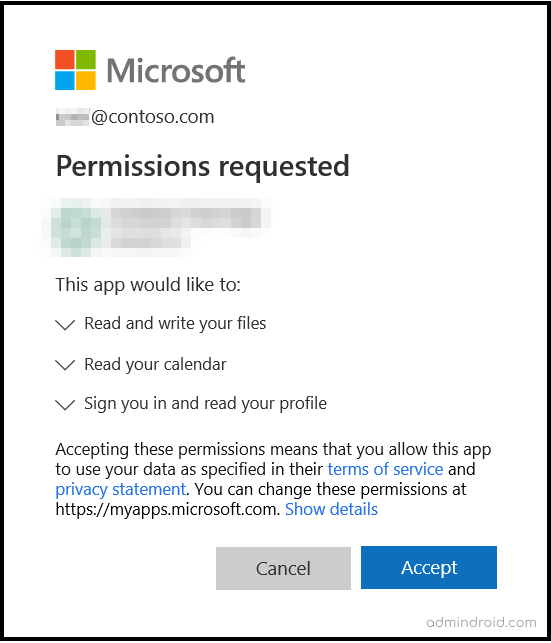
Configure How Users Consent to Applications
By default, Microsoft has ‘Allowed users consent for apps’ they want to access. An admin needs to block or control this setting to prevent severe security damage and enhance application security. Admin can manage the user consent to apps using the following methods.
- Block user consent to all apps.
- Allow users consent for apps from Microsoft verified publishers only.
- Enable admin consent workflow for consent requests.
- Create custom app consent policies via MS Graph.
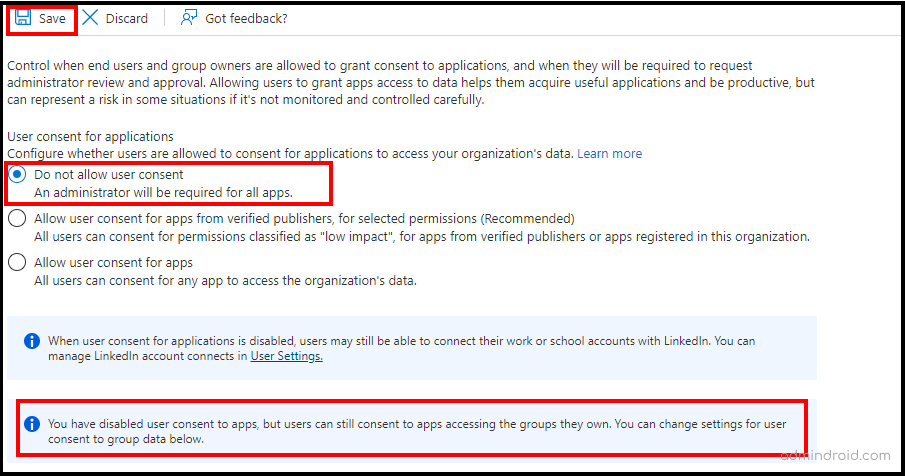
Method-1: Block User Consent for Apps in Microsoft 365
You must be the global administrator or privileged administrator to manage the user consent for third-party applications. Please follow the instructions below to block user consent settings.
- Sign in to Microsoft Entra Admin Center.
- Navigate to the following path: Applications –> Enterprise applications –> Consent and permissions –> User consent settings.
- Then, select the ‘Do not allow user consent’ setting to block the users from using all the applications they want to access.
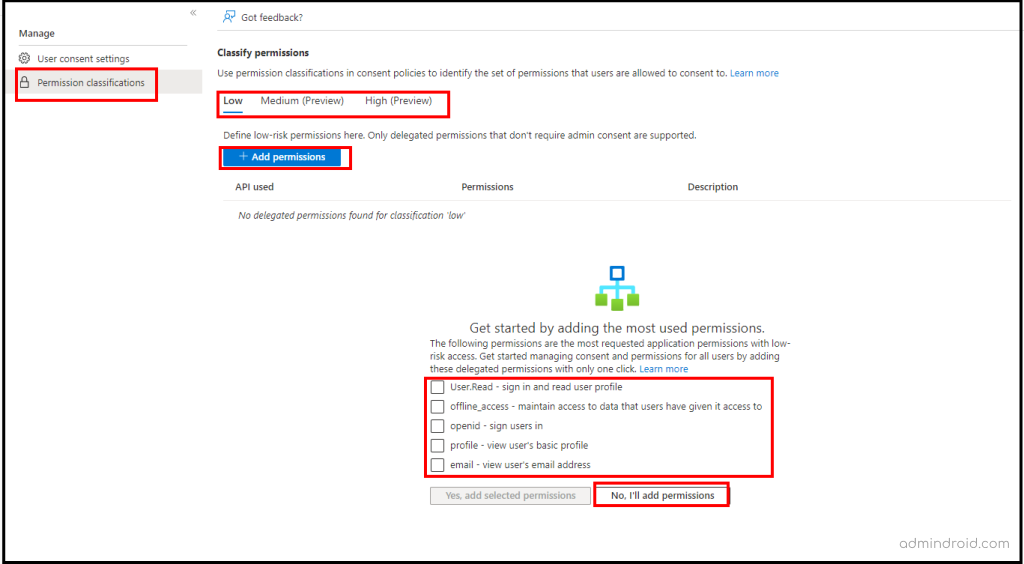
Method-2: Grant Permissions to Microsoft Certified Third-Party Applications
As a precaution against severe security risks from suspicious third-party applications, Microsoft provides a setting that only allows Microsoft-certified apps from verified publishers. If you opt for the ‘Allow user consent for apps from verified publishers for selected permissions’ option, you can set custom permissions and block users from consenting to an application from a non-verified publisher.
Currently, admins can define a set of delegated permissions under the ‘Low Impact‘ level, whereas ‘Medium’ and ‘High’ levels are in preview mode.
Method-3: Enable the Admin Consent Workflow to Approve App Consent Requests
Once the user consent for apps is blocked, a user will have no right to provide consent to an app they try to access. Therefore, admins can enable ‘Admin Consent Workflow’ settings to securely grant access to the applications.
Also, admins can set a reviewer to check and approve those admin consent requests to prevent any security damages. So, follow the below steps to enable the ‘Admin Consent Workflow’ settings.
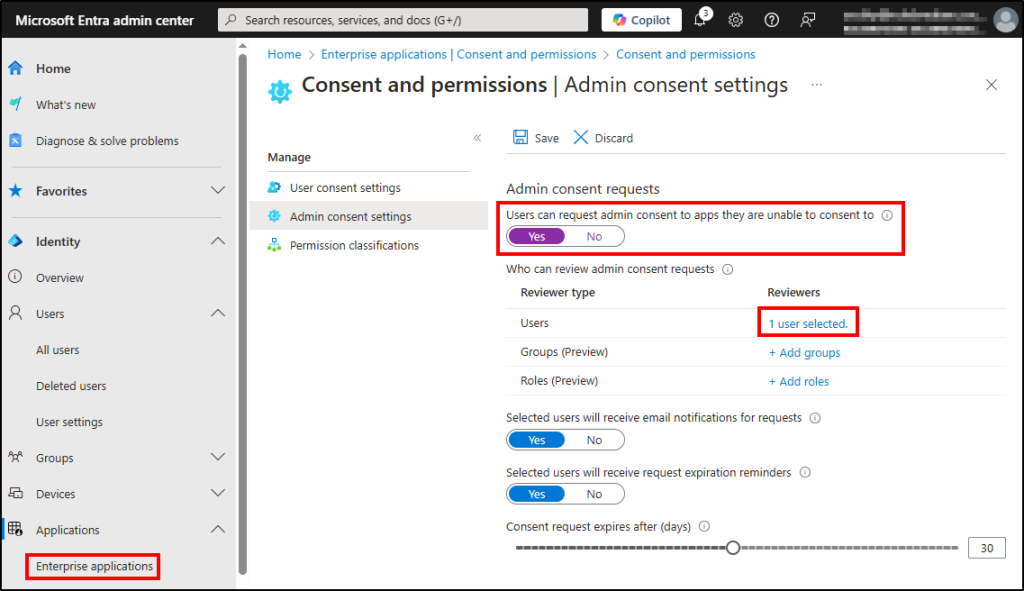
- Sign in to Microsoft Entra Admin Center.
- Navigate to Enterprise applications –> Consent and permissions –> Admin consent settings.
- Turn the ‘User can request admin consent to apps they are unable to consent to’ toggle to ‘Yes’.
- Select the reviewer (i.e., users, groups, or roles) based on your requirements.
- Click Save.
Once the admin consent workflow has been created, users can only request admin approval for an application.
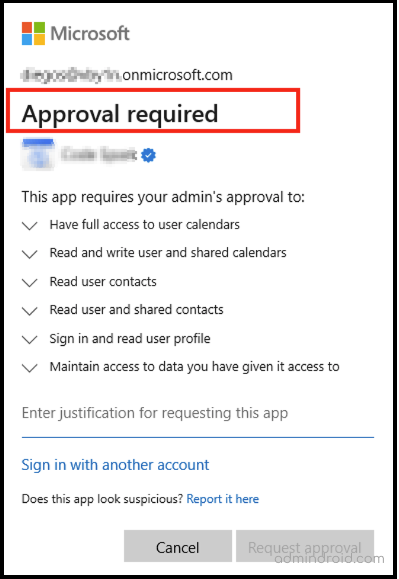
Method-4: Create Office 365 Custom App Consent Policies
Admins can also create custom app consent policies via Microsoft Graph PowerShell to approve app consent requests. They can set several conditions they want to include and/or exclude, permission type, client application ids to match with, and more granularly in their consent policies.
Data security will be compromised easily through consent phishing attacks, no matter if you enable multi-factor authentication or other authentication methods. Therefore, it’s crucial to review user consents granted to apps and remove any unnecessary ones to prevent attackers from accessing your organization’s data.
Unfortunately, this is not just a doorstep to obtaining detailed statistics on users’ permitted applications. Yes, native reporting or PowerShell doesn’t provide an efficient way to get all the desired application reports. You can get the stats only after it sucks your entire time.
But no more waste of time! AdminDroid provides a more detailed and granular view of the applications that users have granted consent to access their Microsoft 365 data. Let’s explore the range of reports it offers.
Keep Your Microsoft 365 Secure with AdminDroid’s Application Monitoring!
The ‘Consent to Applications’ report offers a transparent and comprehensive overview of user-consented applications, including the application name, the users who have granted permissions, consented time, and more.
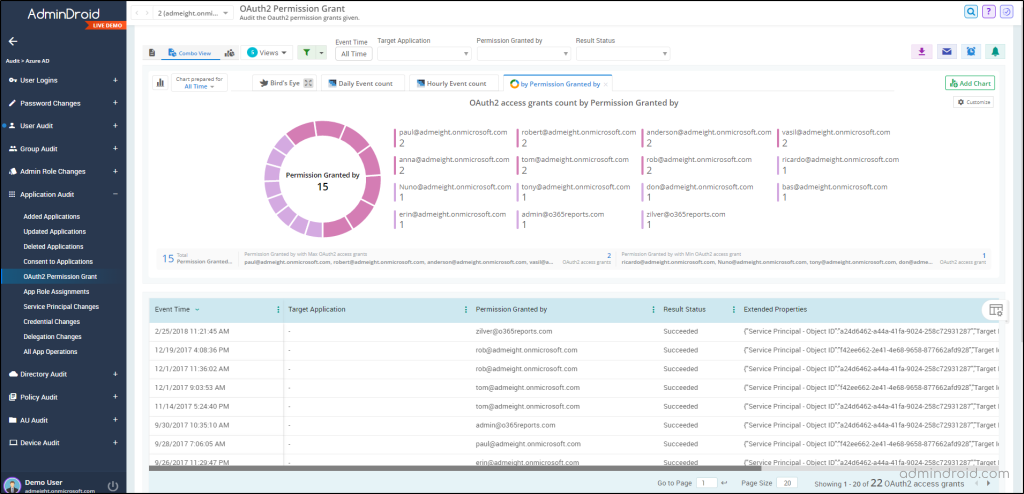
Secondly, the ‘OAuth Permission Granted Applications’ report allows you to identify all the OAuth applications to which the users have granted permissions in your M365 tenant. It includes the details such as the application name, the user who granted the permissions, consent time, and the result status.
With these reports, AdminDroid free Azure AD auditing tool helps you thoroughly understand the Microsoft 365 landscape within your organization. It further deepens your insights into the Azure AD applications used within Microsoft 365 through the below additional reports.
- Added Applications
- Updated Applications
- Deleted Applications
- App Role Assignments
- Service Principal Changes and more.
AdminDroid provides all these 120+ Azure AD reports through a single, easy-to-navigate interface to simplify extracting deep organizational insights. Additionally, with its 30+ visually appealing dashboards, you can explore every aspect of your organization’s Microsoft 365 activities.
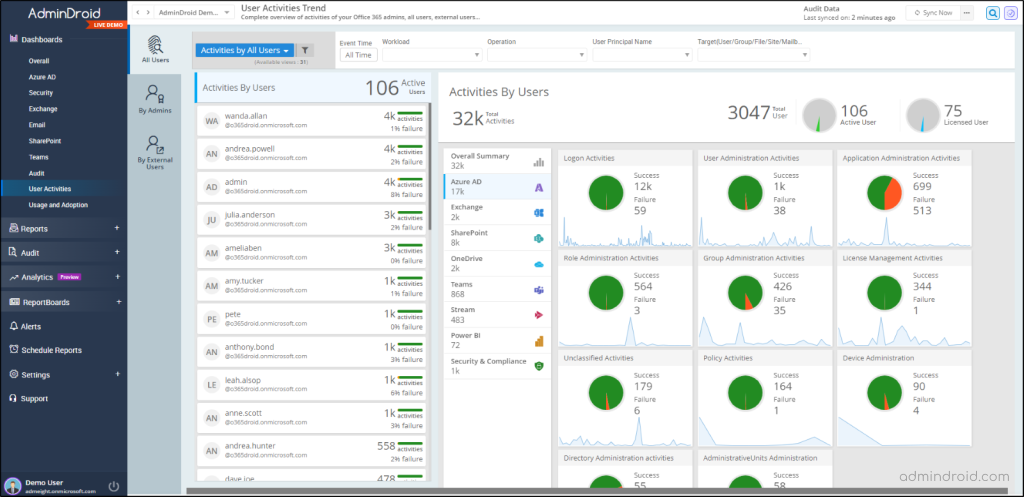
So, why do you stick to the traditional, time-consuming methods when AdminDroid can simplify your Azure AD management?
“AdminDroid – a one-stop solution for auditing and reporting on Azure AD, saving your valuable time and improving your organization’s security”.
I hope this blog will help you find a simple and very secure way to stay away from the malicious phishing apps and attacks that are rapidly emerging these days!






