On Day 7 of Cybersecurity awareness month, learn to conceal your organization by implementing strong authentication methods. Stay tuned for more blogs in Office 365 Cybersecurity blog series.

Do you think setting up complex passwords will help you? Nah! Password complexity alone is not sufficient to make passwords secure. Thus, configuring MFA with a strong authentication method is the only way to secure your Microsoft 365 accounts. So, we are back to the grind of discovering new hidden MFA security configurations and implementing stronger authentication!
Microsoft released grant control and authentication strengths in Conditional Access policies.
Multiple-case implementation in CA policies is now possible! Specifically, disabling weaker MFA authentication methods like SMS and categorizing MFA authentication methods based on the user category.
Confused about what I am saying? Don’t worry, though! Without further ado, let’s get deeper into how to implement authentication strength in your organization.
The Conditional Access Authentication Strength – Setting:
The ‘Authentication Strength’ control in Conditional Access lets you decide exactly which MFA methods users can use to sign in. This gives admins more precision and granular control over authentication security.
Instead of simply requiring MFA, this feature allows you to define the strength of authentication that users must meet. You can choose from predefined levels like Multifactor, Passwordless MFA, or Phishing-resistant MFA, or even create your own authentication strength that fits your organization’s security needs.
You can configure this through the “Require authentication strength” option in Conditional Access. Here’s how to do it:
- Go to the Microsoft Entra admin center.
- Navigate to Entra ID section → Conditional Access → Edit an existing policy (or Create a new one).
- Under the Grant section, select the “Require Authentication Strength” option to enforce your chosen MFA level.
In short, Conditional Access Authentication Strength helps you move from “just having MFA” to enforcing the right kind of MFA, tailored for your environment’s risk level and compliance goals.
Note: Conditional Access and Authentication Strength require either a Microsoft Entra ID P1 or Microsoft 365 Business Premium license.
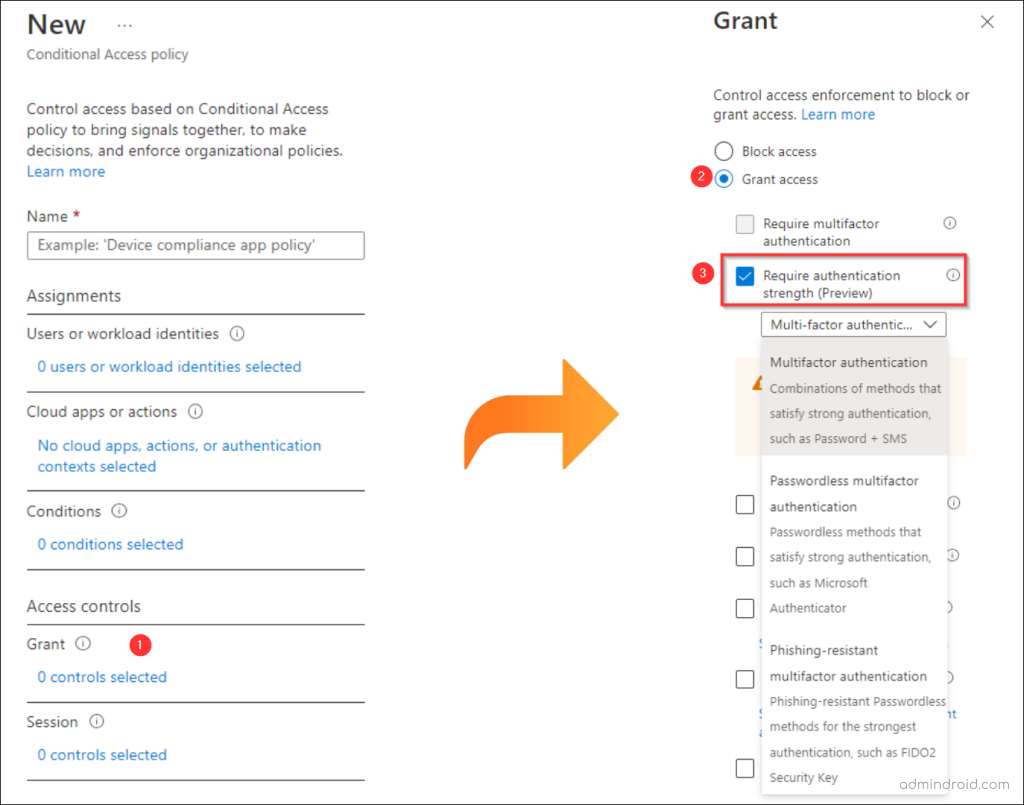
How Authentication Strength Helps You Enforce Stronger MFA Methods
For every lock, there is someone out there trying to pick it or break in.
– David Bernstein
🚨Don’t let your MFAs get broken! While playing out with this new grant control, I noticed some of its use cases.
One of them is disabling weaker MFA methods, like SMS.
While there are several ways to disable SMS authentication, there is no clearer way to exclude SMS as an MFA factor for specific groups. And now the solution is here!
With the “Require authentication strength” option, admins can define and enforce custom authentication levels for users. This gives them the flexibility to block weaker MFA methods, like SMS, and ensure only stronger authentication options are used across the organization.
Secondly, require different authentication methods for different circumstances.
For example, responsibilities in your organization may range from basic-level workers (contingent staff) to design teams, development teams, highly privileged accounts, etc. Although requiring the same level of authentication for all users is relatively straightforward, it’s not always necessary!
For instance, it might not be essential to deploy FIDO2 security keys for contingent staff.
So, the only issue is that implementing different MFA techniques for different users might take a long time. Previously, Conditional Access policies merely required “multi-factor authentication.” Therefore, the MFA method cannot be differentiated.
With authentication strengths, you can categorize the users in different circumstances and enforce different MFA requirements, whether that’s SMS-based MFA, passwordless options, FIDO2 security keys, or even a combination of multiple methods.
Different Types of Authentication Strengths in Conditional Access
Apparently, Microsoft is planning to remove the “Require multi-factor authentication” checkbox and replace it with “Require authentication strength.”
Following a thorough analysis of all authentication methods, Microsoft has categorized different authentication strengths under the grant control. They are,
(Basic) ‘Multifactor Authentication’ Strength:
Combination of methods that satisfy medium assurance authentication strength, such as password + SMS.
When a Conditional Access policy uses this grant control, the selected users or groups must authenticate with any method that qualifies under the “multifactor authentication strength” category.
In simple terms:
They must use at least one MFA method from the allowed list, but not necessarily a strong one. This is the problem: the list includes both strong and weak MFA methods!
So, if you enable this thinking, it will force users to use FIDO2 or other high-assurance methods; it won’t! Users can still fall back to less secure methods, which defeats the purpose of enforcing strong MFA eventually! Enabling this control does not force users to use stronger methods.
Below are the authentication methods supported under the ‘multifactor authentication strength’ control:
- Microsoft Authenticator (Phone Sign-in)
- Password + SMS/Voice/Microsoft Authenticator (Push)/Software OATH/Hardware OATH
- Windows Hello For Business / Platform Credential
- Passkeys (FIDO2)
- Certificate-based Authentication (Multifactor)
- Federated Multifactor
- Federated Single factor + SMS/Voice/Microsoft Authenticator (Push)/Software OATH/Hardware OATH token
⚠️Did you notice!? Microsoft has brought the MFA push notification system under a minimum security level. This is due to the increase in different MFA fatigue attacks and push-based exploitation. Relying on push-only MFA is no longer safe — it’s time to move users toward more secure methods like passwordless or phishing-resistant MFA.
‘Passwordless Authentication’ Strength:
Passwordless methods that satisfy high assurance authentication strength, such as Microsoft Authenticator, FIDO2 Security Keys.
The “Passwordless MFA authentication strength” is considered the second most secure MFA option. Doubting it? You can get insights on the benefits of passwordless authentication and why it should be implemented with this Microsoft article.
Now, when it comes to Conditional Access, this grant option only applies to users who have enabled passwordless authentication. Here are the methods supported under the Passwordless MFA authentication strength control:
- Windows Hello For Business / Platform Credential
- Passkeys (FIDO2)
- Certificate-based Authentication (Multifactor)
- Microsoft Authenticator (Phone Sign-in)
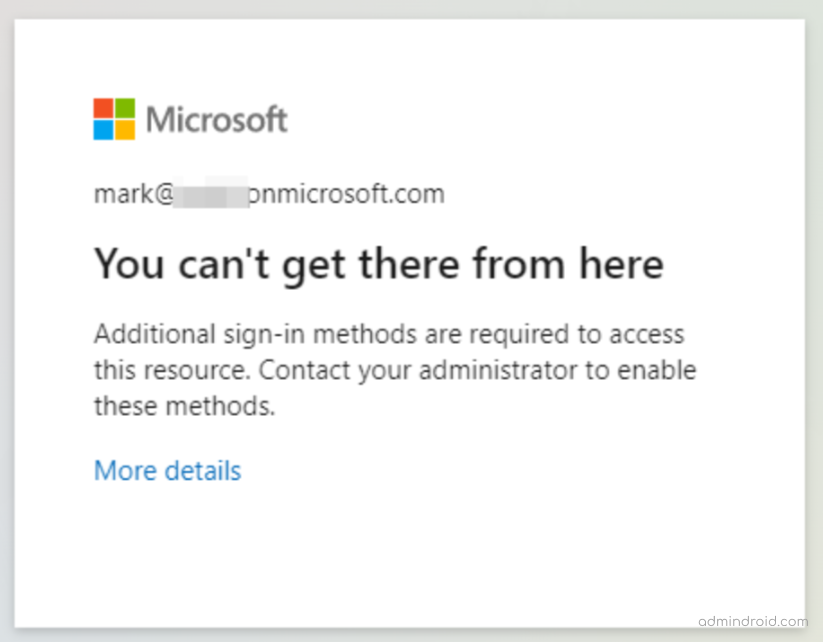
This level helps block weaker MFA methods like SMS or voice calls. If users try to sign in with anything outside the above list while this authentication strength is active in a policy, they’ll see the message:
You can’t get there from here...
Additional sign-in methods are required to access this resource.
So, make sure to enable passwordless authentication for the user before applying the policy.
How to Enable Passwordless Authentication in Entra
To enable passwordless authentication for any user, follow these steps:
- Go to the Microsoft Entra admin center → Authentication methods → Policies.
- Select any passwordless option you want to enable: Microsoft Authenticator or Passkey (FIDO2).
- Add the required users or groups and choose the authentication type (passwordless or any).
- Click Save.
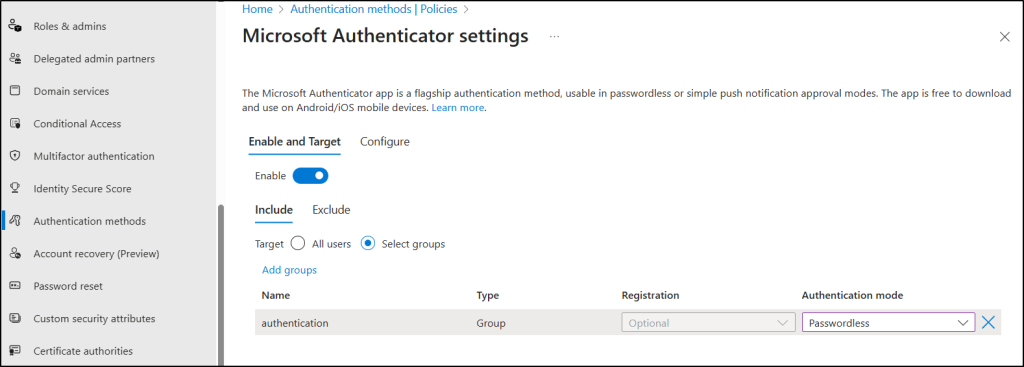
Once enabled, the selected users or groups will be prompted to set up passwordless sign-in the next time they log in.
Note: You can only enable one work or school account in the Microsoft Authenticator app. If you attempt to add another work/school account, you will receive the following message:
Your organization does not allow you to add your account to Microsoft Authenticator.
‘Phishing–resistant MFA’ Strength:
Phishing-resistant MFA methods such as FIDO2 Security Keys or Windows Hello for Business.
It’s finally time for the most secure form of MFA: the FIDO2 Security key, passkeys, and CBA. That’s exactly what it sounds like! Even the most sophisticated phishing attacks cannot compromise this phishing-resistant MFA. Research by Barracuda Networks says that around 667% of phishing attacks arose during the pandemic. Woah! That’s an alarming count, isn’t it? So, phishing-resistant MFA was discovered to counter such suspicious attacks.
What are security keys?
It is a hardware token that goes beyond traditional MFA techniques. This delivers a more seamless authentication experience because users no longer need to memorize passwords, wait for OTPs, and input them into the website. Rather, the app accesses the user’s private key on their device, and the user authenticates themselves using a fingerprint or other biometric feature.
Also, you can utilize Microsoft 365 passkeys, another phishing-resistant method with FIDO2 credentials. It is stored directly on the user’s device to provide more convenient logins. This method prevents password spray attacks and harmful phishing attacks effectively.
This type of authentication method can be used for highly privileged admin and executive accounts. No data can be theft with this kind of phishing-resistant MFA.
How to Require Phishing-resistant Multifactor Authentication?
As part of Microsoft’s push toward stronger identity protection, phishing-resistant MFA ensures users can only authenticate using hardware-bound credentials or cryptographic keys, eliminating the risks tied to codes or approvals that can be intercepted or spoofed. Here’s how to enforce phishing-resistant MFA through Conditional Access policy.
- Go to the Microsoft Entra admin center → Entra ID → Conditional Access → Create new policy.
- Configure the required fields, such as Name, Assignments, Target resources, Network, and Conditions, based on your policy requirements.
- In the Grant section, select Require Authentication Strength.
- From the available options, choose Phishing-resistant MFA.
Once this is enabled, only the following methods will satisfy the authentication requirement:
- Windows Hello for Business / Platform Credential
- Passkeys (FIDO2 Security Keys)
- Certificate-based Authentication (Multifactor)
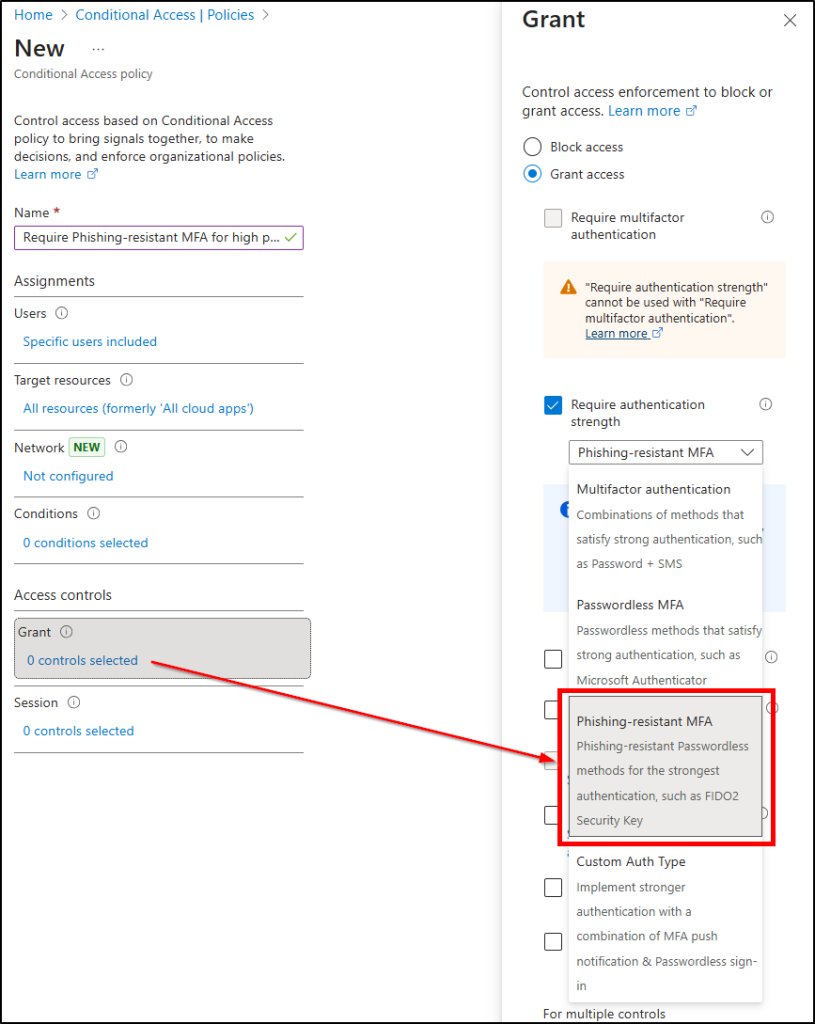
5. After configuring the settings, click Select to confirm your choices, then set Enable policy to Report-only for testing.
6. Finally, choose Create to save and activate your Conditional Access policy.
When this strength is applied, users won’t be able to sign in using weaker MFA methods like SMS, voice calls, or even Microsoft Authenticator number matching! Any attempt using those methods will fail the policy, and access will be blocked!
This enforcement ensures that sign-ins rely only on phishing-resistant MFA, offering the highest level of identity assurance and resistance to phishing attacks, a key step in adopting a Zero Trust security model.
‘Custom Auth Type’ Strength:
Strengthen the authentication step by customizing multiple MFA methods into one based on your requirements.
The cherry on top of all methods is the absolute flexibility to create our own CUSTOM AUTHENTICATION STRENGTH in Microsoft Entra.
Instead of relying solely on Microsoft’s predefined MFA levels, you can now design a strength that fits your organization’s exact security model. Custom authentication strengths let you combine multiple MFA methods into a single, tailored policy that meets specific compliance or risk-based requirements.
This means deciding which authentication methods are allowed and how they can be combined, giving you full control over identity assurance! This gives admins granular control over MFA enforcement and helps align with organizational security or compliance needs.
For example,
- You could mandate FIDO2 + Certificate-based authentication for privileged roles or high-risk apps, while allowing Microsoft Authenticator for standard users.
- You could require users to authenticate with FIDO2 + certificate-based authentication, or block weaker methods like SMS while keeping Microsoft Authenticator as an option.
This approach not only strengthens sign-in security but also helps you tailor MFA enforcement across different user groups and scenarios, achieving the right balance between usability and protection.
How to Create a Custom Authentication Strength in Entra ID
Here’s how to create your own custom authentication strength:
- Go to the Microsoft Entra admin center → Entra ID → Authentication Methods.
- Under the Manage section, select Authentication strengths.
- Click + New authentication strength
- Provide a name and description for easy identification. Then, select the specific MFA combinations you want to allow (for example, Passkeys, Microsoft Authenticator, or CBA).
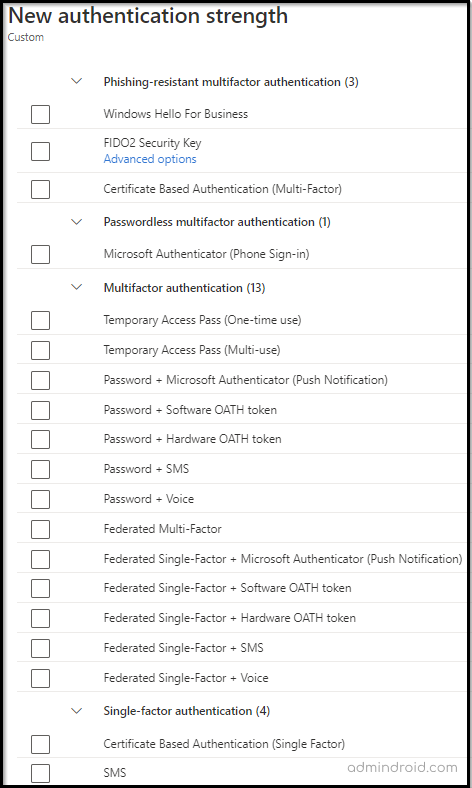
5. Review your configuration and click Create to save it.
Once created, you can link this custom authentication strength to any Conditional Access policy. This ensures users meet your exact MFA requirements, rather than relying solely on Microsoft’s preset options! This flexibility allows you to balance usability and security while phasing out weaker sign-in methods across your tenant.
Is Microsoft Entra ID P1 License the Only Solution to Strengthen Security?
Not at all! You can still secure your Microsoft 365 accounts and prevent MFA bypass attacks even with a Microsoft Entra ID Free license. Yes, you heard it right!
Researchers say that most users use MFA push notification authentication. But the question is, is it really safe to use the MFA push notification system? Yes, 100 percent! But only if you enable the below-recommended setting along with push notification. If not, you will be put in serious danger! Moreover, most of us failed to notice and configure this hidden setting in Microsoft Entra.
Wondering how to set it up? Navigate to the path given below to turn on number matching and additional context in Microsoft Authenticator. Without these, attackers can exploit MFA fatigue to trick users into approving malicious requests.
Go to Microsoft Entra admin center → Entra ID → Authentication methods → Policies → Microsoft Authenticator → Configure tab.
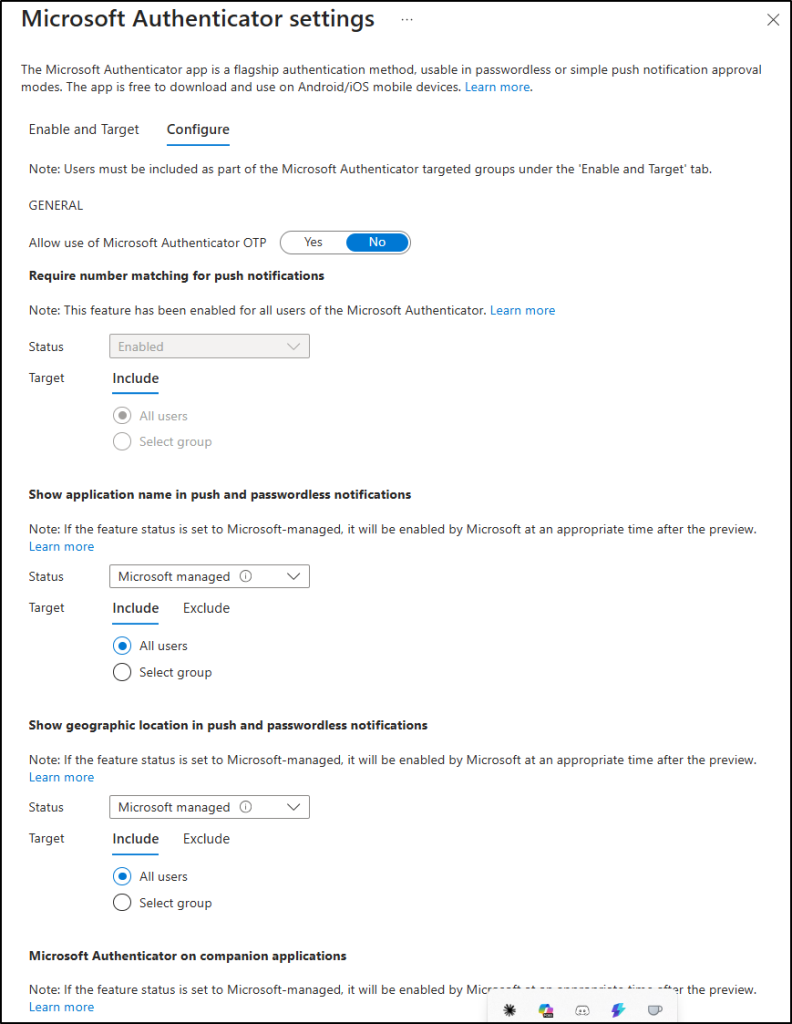
Follow the steps here to enable MFA number matching and additional contexts to experience attack-free multi-factor authentication: https://blog.admindroid.com/how-to-safeguard-from-security-flaws-found-in-mfa-push-notification-method/
The bottom line is that passwordless authentication is very useful for organizations needing strong protection without exceeding their budget. And for those aiming for the highest protection, moving toward phishing-resistant MFA is the best next step.
So, consider removing phone-based MFA and transitioning your users to more secure methods. To further enhance your security, fine-tune your phishing protection with Microsoft Secure Score recommendations.