🤔Are you a regular reader of our blogs? If so, you may have come across a lot of content related to MFA & Conditional Access policies. Why did we bring on most like this? Well, the reason is that MFA is one easy step toward getting into the absolute security zone. And as a cherry on top of this, MFA & CA policies come under the Business suite itself!
Here are some MFA and Conditional Access policy blogs that you might find helpful.
- Configuring and Managing MFA in Office 365
- When to use what – Security defaults VS Conditional Access policies
- Safeguard Office 365 Users from MFA Fatigue Attacks
- Use Phishing-Resistant MFA to Implement Stronger MFA Authentication
- How to Safeguard from Security Flaws Found in MFA Push Notification Method?
- Inbuilt Reports on Azure MFA Registration and Reset Events
- External User Types for CA Policies in Azure AD
- 5 Must Know Device-based Conditional Access Policies in Microsoft 365
- An Admin’s Complete Guide to Monitor Conditional Access Policy Changes
And, now adding to the list, Microsoft announced about Conditional Access policy templates in Entra back in November 2021. Yet why does this CA policy template remain in the news for so long? Let’s dig out the answer here!
In this blog, we shall look into the widely spoken CA policy templates and how to deploy them to empower security among enterprises.
What are Conditional Access Policy Templates?
Configuring Conditional Access policies is always challenging, since we need to consider every individual case; otherwise, the work environment may be adversely affected. So, to make it easier to apply CA policies, Microsoft introduced Conditional Access policy templates.
Conditional Access policy templates are pre-defined set of conditions and controls that provides a convenient method to implement new policies scoped with Microsoft recommendations.
Overall, the CA policy templates are based on Microsoft standards, which takes the organization one step closer to the Zero Trust paradigm.
As Microsoft stated, it comes with 14 Conditional Access policy templates that can be filtered by six different scenarios.
- Secure foundation
- Zero Trust
- Remote work
- Protect administrators
- Emerging threats
- All
Purpose of Conditional Access Policy Templates:
With its many benefits, it helps to ensure that only authorized users can access sensitive resources within organizations. Some of them are:
- Rather than creating new policies defining controls and access from scratch, you can quickly pick a template and apply Conditional Access policies.
- IT security administration departments can streamline the process of managing CA policies in their organizations.
- Increased ability to work more on monitoring the Conditional Access policy changes.
- As the templates are Microsoft-suggested, we can be sure that the pre-defined policy templates are the best in terms of effectiveness and efficiency. In the end, organizations can be assured that their policies are up-to-date and reflect best practices for securing corporate assets.
- These templates come with advanced and finely granulated controls, thus helping organizations to meet the absolute compliance requirements.
Isn’t that quite a lot? Absolutely, yes! 💯 Therefore, there is no reason to say NO to using Conditional Access policy templates in organizations.
Now that we know what CA templates are, let’s look at how to apply security policy templates.
How to Use the Conditional Access Templates in Entra?
- Head over to the Entra Admin Center, navigate to Entra ID → Conditional Access.
- Click Create new policy from templates at the top.
- You’ll see multiple template categories (with predefined policies under each). Templates may appear in more than one category. There are around 18 templates currently, and they will continue to grow.
- Secure Foundation– Baseline identity protection policies enforcing strong authentication and core security controls across users.
- Zero Trust– Policies that enforce device compliance, risk evaluation, and least-privilege access before granting access.
- Remote Work – Controls designed to secure access from external networks and unmanaged environments.
- Protect Administrator – Applies stricter authentication and access controls specifically to privileged admin accounts to reduce the blast radius of a compromise.
- Emerging threats – Adaptive protections targeting new attack patterns, risky sign-ins, and evolving identity threats.
- AI Agents – Policies that govern and secure access by AI-driven applications and service identities.
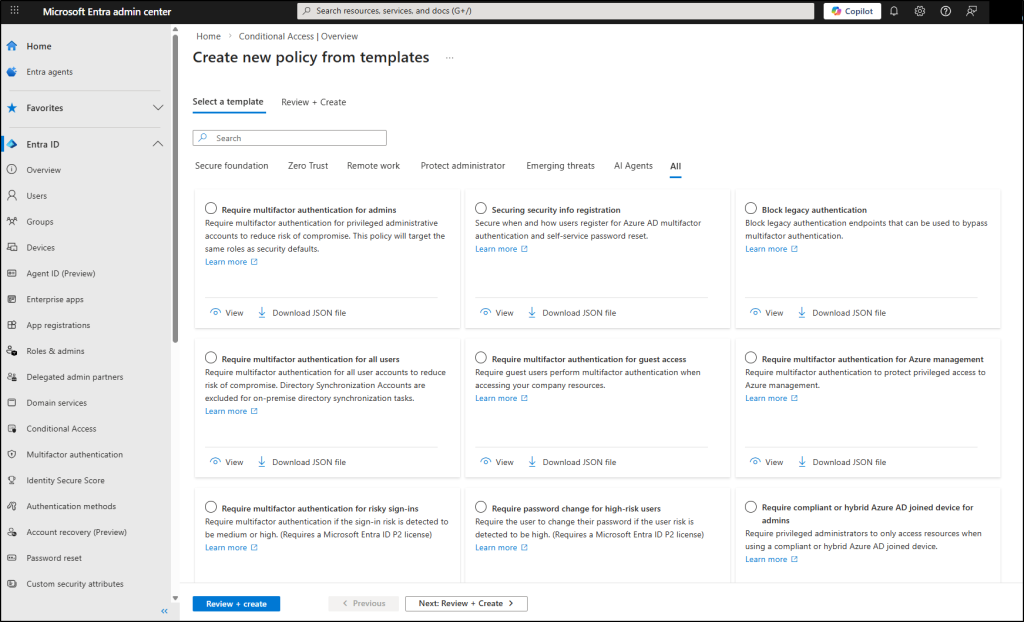
Note: You can also export the JSON definition of any policy for further customization or backup purposes.
4. Select a template, review the preconfigured settings, adjust if needed, and click Review + Create. The policy will be created with a unique identifier for tracking and management.
That’s it, done in a jiffy! 🚀 But, certain things you might have to know while creating a Conditional Access policy using default templates. They are as follows:
Points to Remember:
- When creating CA policies, all users (except the policy creator) are automatically included and cannot be customized.
- By default, the current user (policy creator) will be excluded from the CA policy. Nevertheless, once a Conditional Access policy is created, you can include/exclude specific accounts or customize the policy using the ‘Edit’ option.
- To prevent disruptions, each policy is created in Report-Only mode by default.
All About ‘Conditional Access Policy Templates’
Having learned how to implement Conditional Access policies, let’s now go deeper and learn what Conditional Access policy templates are added to the list.
| S.No | Conditional Access Policies | Description |
| 1. | Require multifactor authentication for admins. | Enforces MFA for users assigned privileged administrative roles. This reduces the risk of account takeover for high-impact identities that can modify tenant-wide settings. |
| 2. | Securing security info registration. | This feature is only available to users who have enabled combined registration. Controls where and how users can register or update their MFA methods and security information. ➜ Prevents attackers with stolen credentials from hijacking accounts by enrolling their own authentication methods. |
| 3. | Block legacy authentication. | Microsoft has started to deprecate basic authentication protocols to mitigate risks among organizations. This will eventually block authentication attempts using legacy protocols such as IMAP, POP, SMTP AUTH, and older Office clients. ➜This template is also one of the top 5 Entra ID secure score recommendations to improve your security. |
| 4. | Require multifactor authentication for all users. | Applies MFA requirements across all users accessing targeted resources. ➜Provides a strong baseline security posture against password-based attacks. |
| 5. | Require multifactor authentication for guest access. | Guests can’t be avoided, but we can ensure they are accessing corporate networks in accordance with stricter protocols. This template forces external guest users to complete MFA before accessing resources. ➜Helps secure collaboration scenarios involving third-party identities. |
| 6. | Require multifactor authentication for Azure management. | Enforces MFA specifically when users access Azure management interfaces like the Azure portal, CLI, or PowerShell. ➜This can help to protect critical infrastructure from unauthorized changes even if credentials are compromised. |
| 7. | Require multifactor authentication for risky sign-ins. | (Requires an Azure AD Premium P2 License) If the sign-in risk is detected to be medium or high, MFA is required. ➜Eventually, this helps to secure Microsoft 365 from risky sign-ins. |
| 8. | Require password change for high-risk users. | (Requires an Azure AD Premium P2 License) If any user is flagged as high risk, this policy will force them to reset their password before regaining access. |
| 9. | Require a compliant or hybrid Azure AD-joined device for admins. | Ensures administrators can access resources only from compliant or hybrid joined devices. ➜Adds device-level assurance for privileged accounts. |
| 10. | Block access for unknown or unsupported device platforms. | Users will be blocked from accessing business resources if they sign in with either an unknown or unsupported device. |
| 11. | No persistent browser sessions. | This prevents access when an unmanaged device remains signed in to the browser after one hour. |
| 12. | Require a compliant or hybrid Azure AD-joined device or multifactor authentication for all users. | Protect access to company resources by requiring users to use a managed device or perform multifactor authentication. (macOS or Windows only) |
| 13. | Use application-enforced restrictions for unmanaged devices. | Block or limit access to SharePoint, OneDrive and Exchange content from unmanaged devices. ➜Protects corporate data without fully blocking access for users on personal devices. |
| 14. | Require MDM-enrolled and compliant device to access cloud apps (Preview) | Allows access only from devices enrolled in MDM and marked as compliant. ➜Ensures managed and secure devices are used to access corporate resources. |
| 15. | Require multi-factor authentication for Microsoft admin portals | Enforces MFA when accessing Microsoft admin portals such as Microsoft 365 Admin Center, Intune, and Defender portals. ➜Adds an extra layer of protection for portals where configuration changes can have a tenant-wide impact. |
| 16. | Block access to Office 365 apps for users with insider risk | Restricts access to O365 applications for users flagged by Microsoft Purview Insider Risk Management. ➜Helps contain potential data exfiltration or malicious activity from within the organization before it escalates. |
| 17. | Require phishing-resistant multi-factor authentication for admins | Goes beyond standard MFA by requiring admins to use phishing-resistant methods like FIDO2 security keys or Windows Hello for Business. ➜Protects against modern phishing and adversary-in-the-middle attacks that can bypass traditional MFA. |
| 18. | Block High-Risk Agent Identities from Accessing Resources | Prevents AI agents and workload identities flagged as high risk from accessing organizational resources. ➜As AI-driven automation grows, this policy ensures compromised or rogue agent identities can’t move laterally through your environment. |
The built-in Conditional Access template library will continue to evolve as new threats emerge and identity security evolves! So expect more templates to be added to these categories over time, which makes it even easier to adopt a strong security posture right out of the box.
Start with the Secure Foundation templates if you’re new to this, and work your way up; your identity perimeter will be better for it.
Secure your sensitive resources with ease!






