Cyberattacks are becoming increasingly sophisticated, making it challenging for organizations to maintain robust security defenses in Microsoft 365. To effectively protect against these threats, a proactive approach is crucial. This is where the Configuration Analyzer in Microsoft Defender comes in. In this blog, we’ll explore the key features, benefits, and how to optimize and correct security policies with configuration analyzer effectively.
What is the Configuration Analyzer in Microsoft Defender?
The Configuration analyzer in Microsoft 365 is a centralized location to find and fix security policies. It helps identify areas where your policies may be weak or outdated compared to Microsoft’s Standard Protection and Strict Protection profile settings. If any of your settings fall short of these profiles, the analyzer will highlight them, enabling you to take corrective action and bolster your defenses.
Configuration Analyzer for Security Policies
The configuration analyzer covers a broad spectrum of preset security policies, including:
1. Exchange Online Protection (EOP) Policies – These policies apply to Microsoft 365 organizations with Exchange Online mailboxes and standalone EOP organizations without Exchange Online mailboxes.
- Anti-spam policies
- Anti-malware policies
- EOP anti-phishing policies
2. Microsoft Defender for Office 365 Policies – These policies are applicable to organizations using Microsoft 365 E5 or those with Defender for Office 365 add-on subscriptions.
- Anti-phishing policies (spoof settings, impersonation settings, advanced phishing thresholds)
- Safe Links in Microsoft Defender
- Safe Attachment policies in Microsoft 365
Additional Microsoft 365 Configurations Monitored by the Configuration Analyzer
Beyond protection policies in EOP and Microsoft Defender for Office 365, the configuration analyzer also checks for critical non-policy configurations, including:
- DomainKeys Identified Mail (DKIM)
- Outlook external sender identification
Where to Find Configuration Analyzer in Microsoft Defender?
To have full control in the Microsoft Defender portal, you need roles such as ‘Organization Management’ or ‘Security Administrator’. To access configuration analyzer in Microsoft 365 Defender, do the following.
- Sign in to the Microsoft Defender portal.
- Navigate to Email & collaboration –> Policies & rules –-> Threat policies.
- Click on Configuration analyzer under ‘Templated policies’.
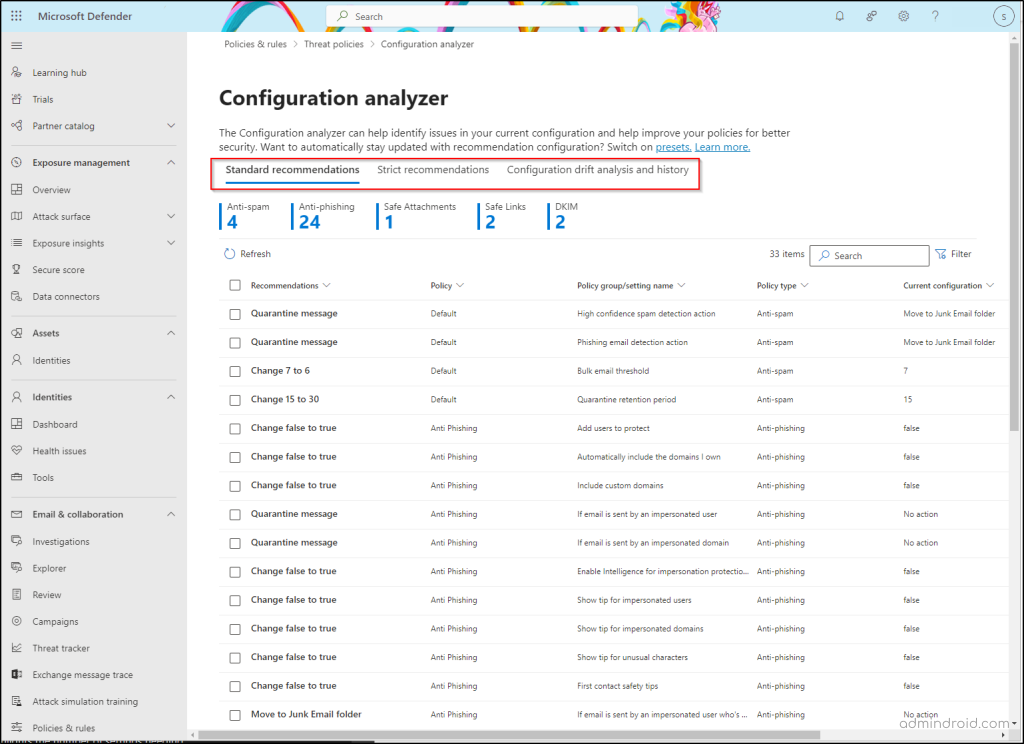
Configuration Analyzer in Microsoft Defender Overview
In this section, we’ll explore the key features and tabs in the Configuration Analyzer. You’ll learn how it helps you compare your security policies against recommended standards and track any changes over time to ensure compliance.
Key Tabs in Configuration Analyzer
The configuration analyzer features three main tabs:
- Standard Recommendations: This tab compares your existing security policies against the standard recommendations. It suggests configuration changes that align with industry best practices to enhance your overall security posture.
- Strict Recommendations: This tab offers a higher comparison of your existing security policies to strict recommendations. These suggestions are aimed at organizations with higher security needs, such as those handling sensitive data or operating in highly regulated industries.
- Configuration Drift Analysis and History: This tab helps track and analyze configuration changes over time, allowing you to identify any deviations from the established security baselines. It is crucial for maintaining consistent security configurations and ensuring compliance.
A Closer Look at Standard Recommendations and Strict Recommendations Tabs
By default, the configuration analyzer opens on the Standard recommendations tab, but you can switch to the Strict recommendations tab anytime. Both tabs look and function the same.
Summary of Security Settings Analyzed in Configuration Analyzer
The top section of each tab highlights how many settings in your security policies need adjustments to align with either the Standard or Strict protection levels. These policies include:
- Anti-spam
- Anti-phishing
- Anti-malware
- Safe Attachments (if you have Microsoft Defender for Office 365)
- Safe Links (if you have Microsoft Defender for Office 365)
- DKIM
- Built-in Protection (if you have Microsoft Defender for Office 365)
- Outlook
If a policy type doesn’t appear, it means all settings in that category already meet the recommended protection levels.
Detailed Settings Table in Configuration Analyzer
The main part of the tab is a table listing the settings that need to be updated. Here’s a breakdown of the table columns:
- Recommendations: The ideal setting for either Standard or Strict protection.
- Policy: The specific policy that includes the setting.
- Policy group/setting Name: The setting that requires attention.
- Policy Type: The type of policy, like Anti-spam or Anti-phishing.
- Current Configuration: The setting’s current value.
- Last Modified: When the setting was last changed.
- Status: The progress status, usually starting as ‘Not started’.
Viewing Details for a Recommended Policy Setting in Configuration Analyzer
To view more information about a recommended policy setting, go to either Standard Protection or Strict Protection tab. Click on any policy to learn about the details of it.
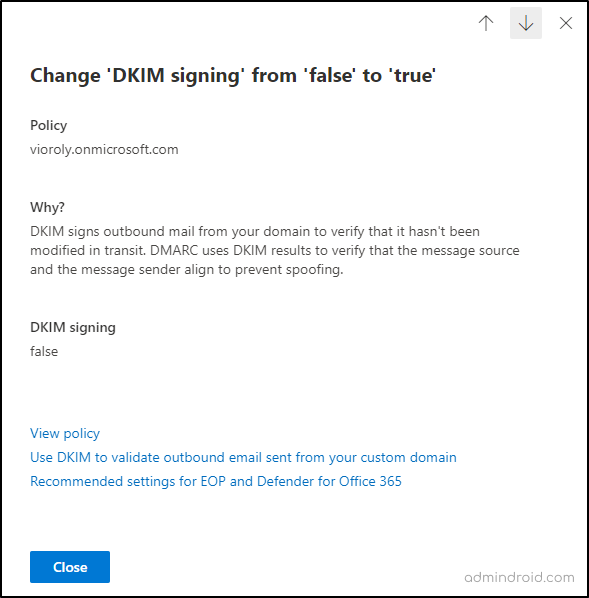
The following is the information in the details flyout:
- Policy: Displays the name of the policy impacted by the recommendation.
- Why?: Explains why the recommended setting is suggested.
- Recommended Setting: Shows the specific setting that needs adjustment and the recommended value.
- View Policy: A link that takes you directly to the policy details in the Microsoft Defender portal, where you can manually update the setting.
- Learn More: Provides a link to the recommended settings for EOP and Microsoft Defender for Office 365 security.
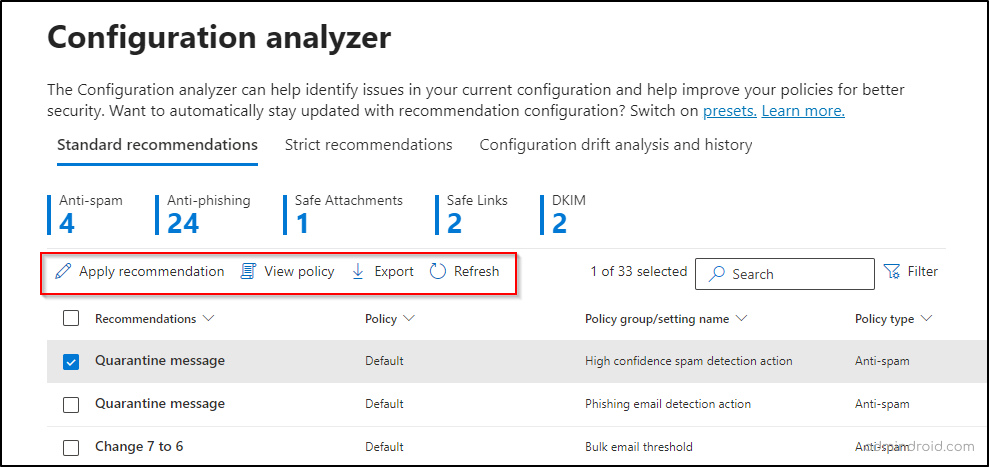
How to Take Action on a Recommended Policy Setting?
To apply recommendations in the configuration analyzer, click on the checkbox next to any policy setting in the Standard recommendations or Strict recommendations tab.
The following actions will appear:
1. Apply Recommendation: This option updated the setting to the recommended value. If multiple steps are required, this option will be grayed out.
When you click ‘Apply recommendation’, a confirmation dialog will appear. You can choose not to see this dialog again in the future. After confirming,
- The setting is updated to the recommended value.
- The recommendation remains selected, but only the Refresh option is available.
- The status of the recommendation changes to ‘Complete’.
2. View Policy: This link takes you directly to the policy details in the Microsoft Defender portal, where you can manually update the setting.
3. Export: You can export the selected recommendation to a .csv file by clicking ‘Export’.
After updating a setting, either automatically or manually, click Refresh to update the list. The row for the updated recommendation will disappear, and the number of recommendations will decrease.
Configuration Drift Analysis and History Tab
This tab lets you track changes to your security policies and see how they compare to Standard or Strict settings. Here’s what you can view:
- Last Modified: When the change was made.
- Modified By: Who made the change.
- Setting Name: The name of the setting.
- Policy: The affected policy.
- Type: The category like Anti-spam, Anti-phishing, etc.
- Configuration Change: Shows the old and new values of the setting.
- Configuration Drift: Indicates if the security increased or decreased compared to Standard or Strict settings.
Note: Unified Auditing must be enabled for drift analysis.
Apart from configuration analyzer in Defender portal, Microsoft experts developed a PowerShell tool named “Office 365 Advanced Threat Protection Recommended Configuration Analyzer (ORCA)” to check anti-malware and anti-spam settings. But note that ORCA’s suggestions may differ from official Microsoft recommendations.
I hope this blog provided valuable insights into the Configuration Analyzer feature in Microsoft Defender. Want to ensure your security settings stay aligned with best practices? You can easily enable preset security policies (Standard and Strict) in Microsoft 365 to keep your configurations optimized and up-to-date. Feel free to reach us through the comment section for any queries!