On Day 21 of Cybersecurity awareness month, strengthen your Microsoft365 security by giving precise access limitations to your guest users. Stay tuned for the upcoming blogs in our M365 Cybersecurity blog series.
Microsoft has positioned itself as a leading platform for both internal and external collaboration🤝. However, in today’s digital landscape, where internal threats are unpredictable, the risks posed by external users are undeniable!
To mitigate these risks, simply restricting guest user invitations might seem like a quick fix! But such an approach would invariably hinder the productivity and collaborative potential of the organization. The key lies in striking the right balance between enabling external collaboration and safeguarding security. So, to give the right level of access, you can configure guest user access restrictions in Microsoft Entra ID.
- This approach ensures that your organization can continue to collaborate with external users, all while maintaining a high level of security. Moreover, this approach doesn’t advocate avoiding guest users altogether! Instead, it acknowledges their significance in today’s collaborative business and lets us have stricter controls.
So, let’s dive into the blog to gain precise control over guest user access to resources through this security configuration.
Why to Configure Guest User Access Restrictions in Microsoft 365?
Consider the situation: Your company is hosting a vital project collaboration with an external partner. To ensure seamless teamwork, you invite external users to join your collaborative workspace. However, without the proper access controls in place, guests gain excessive privileges, inadvertently exposing your organization to security risks!
It boils down to one crucial factor – overprivileged access to these external guests. In simpler terms, they are given more privileges than they require, leading to the security breach!
However, the key lesson learned here is clear: with proper pre-configuration of how guest user can access, these malicious actors can be effectively handcuffed. And this is the major best practice you need to take into account when configuring the guest user profile.
Manage Guest User Access Permissions in MS Entra ID
From the above, we have learned the importance of configuring the guest user access settings. Now, let’s explore how to manage guest user access in Microsoft 365.
Managing what access guests have on your organization is a crucial task. So, Microsoft equips you with the power to decide the extent of access you’d like to grant external users. And this can be achieved using the “Guest user access restrictions” setting.
To configure Azure AD guest user permissions, navigate to,
Microsoft Entra admin center → Identity → User settings → Guest user access.
Note: This can also be configured via B2B external collaboration setting.
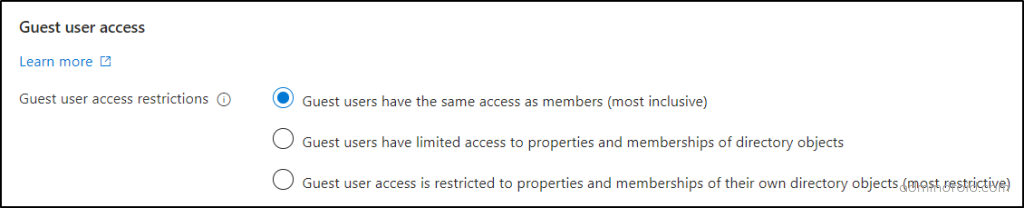
Here you will be given three options to control guest user access in Azure AD.
- Guest users have the same access as members (most inclusive)
- Guest users have limited access to properties and memberships of directory objects
- Guest user access is restricted to properties and memberships of their own directory objects (most restrictive)
But, before selecting any of these options for your organization, it’s essential to address three key points below.
- Determine which resources guest users need access to in order to perform their tasks.
- Consider whether they need to work with confidential or sensitive information in your Microsoft 365 environment.
- Evaluate whether any specific security policies are in place for guest users.
Once done with the above, you can configure appropriate access permissions for your guest users. This way, you can ensure that they have exactly what they need without compromising your organization’s security and data integrity.
Role Needed: You need global administrator privilege to give/set permissions to the guest users.
1. Guest Users Have the Same Access as Members
Giving guest users the same access as members is like giving them the keys to your kingdom! When granting member permissions, guest users gain extensive privileges ranging from accessing group properties to managing application credentials within Microsoft 365. Also, with this setting, guest users can invite other guests too!
These extensive permissions create a risk like,
- Data Leakage: Since full access permissions are granted, there’s a heightened risk of sensitive information leakage within Microsoft 365.
- Account Compromise: If a guest account with full privileges is compromised by an attacker, they are granted access to your Microsoft 365 resources.
- System Disruption: These guest users can modify data and potentially launch disruptive denial-of-service attacks, impacting the organization.
Let’s take a closer look at the permissions your guest users inherit when you opt for this configuration:
| Read Permission: 1. Read all the M365 group properties 2. Read all the group memberships of non-hidden/hidden groups 3. Read the properties of Azure AD apps and enterprise applications 4. Read all properties of devices 5. Read all Microsoft 365 domains 6. Read multi-tenant organization details 7. Read all administrative roles and memberships 8. Read all licensing subscriptions |
| Manage Permission: 1. Manage own mobile number 2. Manage own M365 profile photo 3. Manage group membership, ownership and all the properties. 4. Manage dynamic group membership settings in M365 5. Manage application properties and credentials 6. Manage owned application properties |
| Enumerate, Delete, Restore Permission: 1. Enumerate the list of all M365 users and contacts 2. Enumerate the list of all Microsoft 365 groups 3. Delete application password in Microsoft Entra ID 4. Delete owned groups in Microsoft 365 5. Restore owned Microsoft 365 groups 6. Restore owned M365 applications |
| Create Permission: 1. Create Microsoft 365 groups 2. Create security groups in Microsoft 365 3. Create application passwords for Microsoft 365 users 4. Register/Create new applications |
That’s a lot of permission, isn’t it? So, that’s why choosing this should be done at your own risk. From my point of view, enabling this configuration is a prudent choice when you’ve had a history of secure, long-term collaboration with breach-free partners.
However, it is recommended to provide restricted content access when collaborating with newer or less familiar external entities. This approach adds an extra layer of security and ensures that sensitive data remains safeguarded during collaborative efforts.
2. Default Guest User Access Permission in Microsoft Entra ID
This is the default permission for your guest users – guest users have limited access to properties and memberships of directory objects. With this setting, guest user access is restricted to access certain information related to users, groups, and apps. However, they are restricted from reading all directory properties, which is a privilege reserved for members.
- This balanced approach ensures that your guests can collaborate effectively without compromising the security and privacy of your organization.
Here are the permissions associated with this default guest setting in Azure AD. Guest users can,
- Read all the properties of the M365 users and contacts such as display name, sign-in name, email and more.
- Search users using their object ID or user principal name
- Change their own Microsoft 365 password
- Read properties of all the Microsoft 365 groups
- Read membership details of hidden M365 groups
- Read company display names and M365 domains
- Read properties of Azure AD apps and enterprise applications
- List Azure AD application permissions
However, it’s important to note that guest users will not have the ability to read or manage Microsoft 365 roles, policies, and subscriptions.
From my perspective, this approach holds more advantages than granting member permissions in Entra ID. Because providing full read and manage permissions for guest users can lead to misconfigurations in essential security settings. These misconfigurations may raise the risk of potential security issues.
3. Restrict Guest User Access Permission in Microsoft Entra ID
And coming to the last option, this is the most restricted access permission among the 3 that comes with double layered security!
Recommended One:
While you’re free to choose any of the access options based on your organization’s needs, our recommendation leans towards enabling this option – the most restrictive one.
We understand that merely advising you to configure the third option might not seem convincing on its own. That’s why we’re here to provide you with a detailed breakdown of the benefits associated with it.
Reduced Account Breaches: With limited permissions, guest users are restricted from performing only essential actions like changing their password or managing their mobile number. This controlled access also restricts their ability to read email names, user type properties of other users, effectively preventing potential account breaches.
Safeguarding M365 Critical Settings: Restricted access ensures that guest users cannot read or manage roles, subscriptions, Microsoft 365 policies, or devices. This controlled access minimizes the potential for misconfigurations of M365 security settings.
Microsoft 365 Privacy Protection: Guest users with restricted access cannot view the memberships of M365 groups they belong to or access other users’ profiles. This safeguards the privacy and confidentiality of user data.
So, now you’ve got the point! Restricted access permissions offer a meticulously controlled level of access for guest users. Configuring these permissions in Microsoft Entra ID is not just a suggestion but a robust security measure that enhances your organization’s protection.
However, there are some instances where external users may need additional permission. At that time, you can deploy least privilege access by configuring Privileged Identity Management (PIM) and granting Just-in-Time access in Microsoft 365. With PIM, admins can manage Microsoft Entra roles, Azure resource roles, or PIM for Groups based on organizational needs. Once their tasks are finished, you can revert to restricted access for guest users.
Best Practices for Secure External Collaboration in Microsoft 365
Configuring guest access restrictions is vital for secure B2B collaborations. To further enhance the security, consider implementing the following security measures:
Conditional Access Policies for External Users:
Conditional Access policies enable you to control user access to your M365 resources. In the past, we used the “all guest or external users” option to apply conditions to all guest/external users. But now, you can configure CA policy for specific external user types to provide precise access control over guest users.
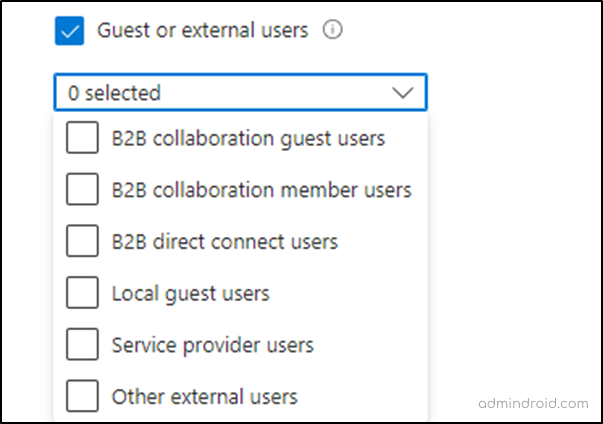
Access Packages for External Users:
Using access packages, onboard external users through an approval process in Entra ID to grant temporary and controlled access for a defined period. This one-time setup allows them to request necessary resources such as groups, teams, applications, SharePoint sites, and Microsoft Entra roles through an access package link upon approval. This approach streamlines collaboration while reducing security risks and administrative overhead.
Allow or Blocklist Policy in Azure Active Directory:
Besides fine-tuning permissions, it’s crucial to control who can be invited to your organization. Invitations to malicious domains can risk data leaks. Administrators can use allow or blocklist policy in MS Entra ID to automatically manage external user invitations. This helps in strengthening defenses against potential breaches and ensuring trusted collaboration.
Use Microsoft Teams Shared Channels:
You can create, and add external users to the Teams shared channels. This strategy allows you to precisely control the scope of their access, limiting it to only the essential files and content within those shared channels.
External Sharing Setting in Microsoft 365:
For secure B2B collaboration, efficiently configure external sharing settings such as limiting external sharing to specific security groups, limiting external sharing by domain, turn off anyone links in Microsoft 365. These measures collectively enhance your organization’s data protection strategy and promote secure collaboration with external entities.
Data Loss Prevention Policies:
Configuring data loss prevention (DLP) policies in Microsoft 365 is a crucial measure to prevent the leakage of sensitive information. This approach proves especially valuable for organizations with external users, as it helps maintain the security of confidential data and ensures it does not end up in the wrong hands.
Key Takeaway
In the end, “anything beyond the limit can end you up”! When it comes to Microsoft 365 security, it’s not only the security policies for external users that matter; it’s also the permissions you grant them. To strengthen your defense, scrutinize the access your guest users require, and tailor the access permissions accordingly. It’s the key to a secure and seamless B2B collaboration.
Security is not a product, but a process
-Bruce Schneier
We hope you now grasp the importance of configuring access permissions. Furthermore, feel free to reach out to us in the comment section for any assistance.






