With cyber threats advancing at an unprecedented rate, safeguarding user accounts has been more critical. Imagine a world where each login is protected by an added security layer, significantly lowering the chances of a breach. Multi-Factor Authentication (MFA) is driving this shift, offering a remarkable 99.9% effectiveness in preventing attacks.
To enhance security and safeguard user accounts, in May 2024, Microsoft mandated MFA for all users. In the recent announcement, Microsoft outlined that the first phase of this rollout will begin October 15, 2024, requiring MFA to access the Microsoft Entra admin center, Azure portal, and Intune admin center.
In this blog, we’ll explain the implications of this change and guide you through the process of setting up MFA for these admin portals.
What are the Applications That Have a Mandatory MFA Requirement?
Here’s a list of applications affected by the MFA requirement across two phases.
Phase 1: Starting on or after October 15, 2024
- Azure portal
- Microsoft Entra admin center
- Microsoft Intune admin center
Phase 2: Early 2025
- Nov 11, 2024 UPDATE: Microsoft 365 admin center (Starting February 3rd, 2025)
- Azure command-line interface (Azure CLI)
- Azure PowerShell
- Azure mobile app
- Infrastructure as Code (IaC) tools
The following comparison highlights the impact of the MFA mandate on different user accounts.
| Accounts | MFA Required? | Impact |
| Users performing CRUD operations in the above listed applications | Yes ✅ | MFA required once enforcement begins. |
| Users accessing Azure services (not listed apps) | No ❌ | Authentication is controlled by the app owner. |
| Workload identities (Managed, Service Principals) | No ❌ | Not impacted by MFA enforcement. |
| User identities for automation | Yes ✅ | Not recommended, should migrate to workload identities. |
| Break glass accounts/Emergency access accounts | Yes ✅ | Once MFA enforcement is enabled, Microsoft recommends configuring FIDO2 security keys as a best practice for break glass accounts. |
Tip: To further enhance security, configure session timeouts for the Entra portal to terminate sessions when they are idle for some time.
How to Implement Strong MFA Methods for MS Entra Admin Center Sign-ins?
To prepare for upcoming changes and protect admin access, you can configure Conditional Access policies that enforce MFA for all users accessing admin portals. For enhanced security and compliance, you can implement strong authentication methods, such as phishing-resistant MFA, starting in report-only mode to gauge their impact before full implementation.
Create Conditional Access Policies to Enforce Mandatory MFA for Accessing Entra Admin Center
You can set up Conditional Access policies to control access to Microsoft administrative portals by enforcing Multi-Factor Authentication (MFA). Below, we’ll explore how to enforce MFA for all users accessing admin portals to enhance security.
License Requirements:
Entra ID P1/P2 license is required to configure Conditional Access policies.
Steps to Enable MFA for Your Tenant:
- Sign in to the Microsoft Entra admin center at least as a Conditional Access administrator.
- Navigate to: Identity → Protection → Conditional Access → Create New Policy.
- Name the policy.
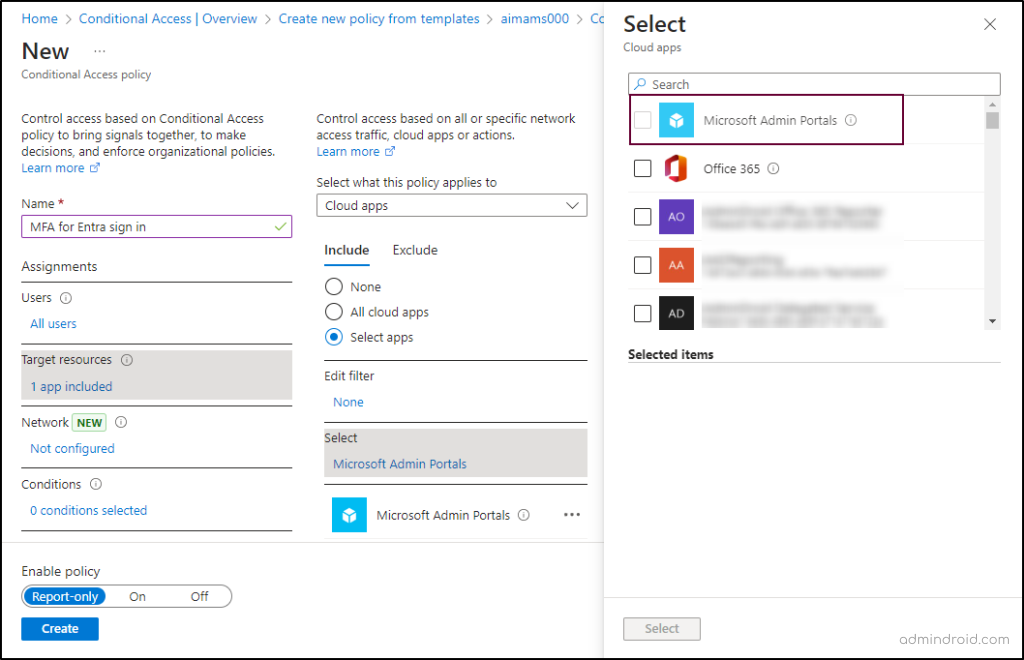
- In the Assignments section, choose the ‘All users’ option.
- In the Target resources section, choose ‘Select apps’ -> search and select ‘Microsoft Admin Portals’. Since MFA cannot be configured for individual admin portals like Microsoft Entra, Intune, or Azure alone, you need to apply policies to all Microsoft admin portals.
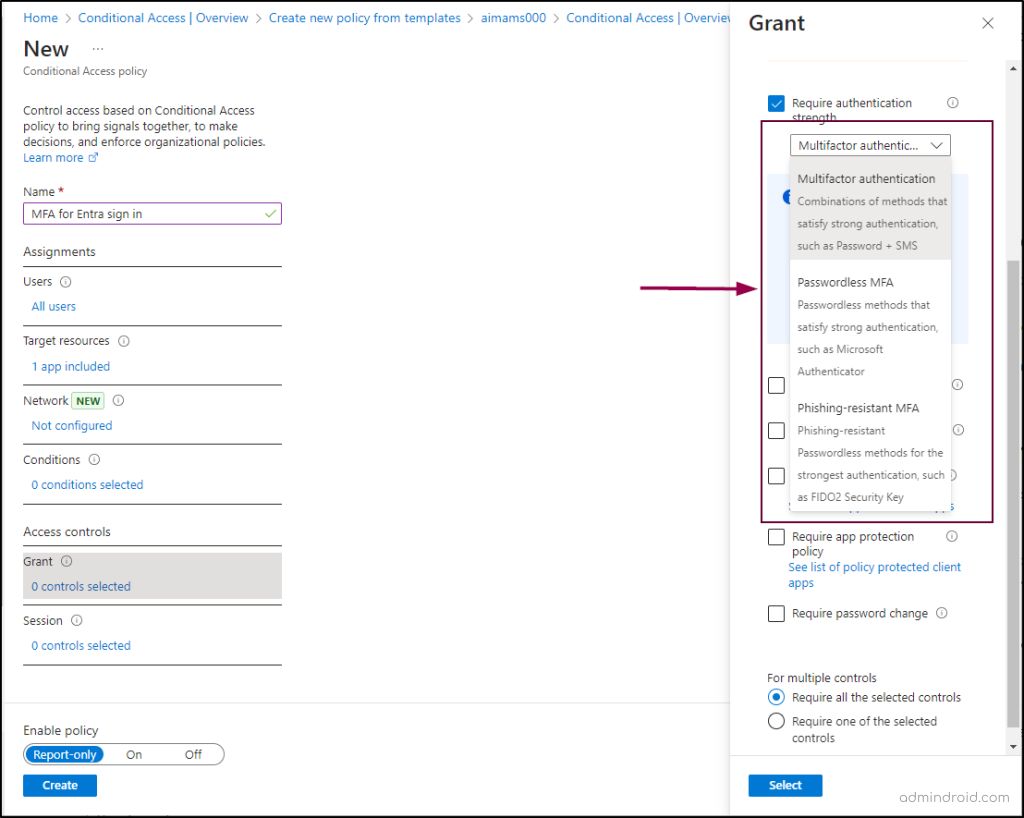
- Under Access controls, select Grant and then choose Grant access. Here, you can opt to create either weak or strong authentication methods. Microsoft recommends using strong, phishing-resistant MFA for better security.
- Select Require authentication strength and choose from the available authentication methods based on your requirements. Click ‘Select’.
- Then, click Create to apply the settings.
By implementing these steps, you can ensure that all users are required to use MFA, enhancing the security of your administrative access. Additionally, this implementation will increase your Microsoft Secure Score, as it is one of the highest-scoring configurations in the Secure Score recommendations.
External MFA solutions can also fulfill MFA requirements, which are currently available in public preview with support for external authentication methods.
Note: If MFA isn’t set up by the enforcement date, users must register for MFA before they can access the Azure portal, Microsoft Entra admin center, and Intune admin center on their next sign-in.
We hope this blog helps you effectively plan for setting up mandatory MFA for all users. Thanks for reading! However, keep in mind the risks of MFA fatigue attacks and learn how to mitigate them to enhance Microsoft 365 security. If you have any questions, feel free to reach out through the comments section.