On Day 27 of Cybersecurity awareness month, learn to monitor and secure your emailing process by keeping track of the Microsoft 365 mailflow reports. Stay tuned for more blogs in the Cybersecurity blog series.
As we all know, users are prone to spam and malware attacks, with which the organization’s data is bound to be breached and this leads to data loss and corruption. To protect the Exchange Online mailboxes from such attacks, a cloud-based filtering service, called Exchange Online Protection (EOP) is used. Besides EOP, Microsoft has also facilitated Office 365 administrators with plenty of mailflow status reports which are available in the Microsoft 365 Defender Portal and Exchange Admin Center.
Security is always excessive until it’s not enough
–Robbie Sinclair
As the quote goes, it is mandatory to keep track of the mailflow status to enhance your organization’s security. Hence, monitoring these reports will help protect your Microsoft 365 organizations from spam, malware, phishing, spoofing, and more such email threats.
Must-Track Reports Recommended for Ensuring a Secure Mail Flow
Some of the reports that I would recommend keeping an eye on, for ensuring a secure mail flow are as follows:
To view the above reports,
- Navigate to the Microsoft 365 Defender Portal.
- Select ‘Reports’ from the left pane of the portal.
- Choose ‘Email & collaboration reports’ to access the mentioned reports.
Permissions Required for Accessing these Reports in the Defender Portal
To view these mail flow and collaboration reports, you need to be assigned with any one of the following roles:
- Global Reader
- Security Administrator
- Security Reader
- Organization Management
Also, note that the Microsoft 365 Defender portal comes with most of the M365 subscriptions by default. You can check out the ‘Prerequisites for Microsoft 365 Defender‘ document to know the licensing requirements that provide you with access to the defender portal at no additional cost.
Mailflow Status Summary Report
With the ‘Mailflow status summary’ report, you can get the organization’s bird’s eye representation of all the inbound and outbound emails. The report includes statistics on spam and malware detections, whether an email is spotted as ‘Good mail’, and if an email is allowed or blocked on edge i.e., the emails that are rejected at the edge itself, before being examined and allowed by EOP or Defender for Office 365.
Additionally, the report represents the email statistics in three different views as follows:
- Type (such as Good mail, Malware, Phishing email, Spam, Edge protection, and Rule messages)
- Direction (Inbound, Outbound)
- Mailflow (based on how the emails are blocked, like Rule block, Malware block, Spam block, Detonation block, Impersonation block, etc.)
For instance, you shall use this report to view trends of spam-detected emails. You can filter out the report for any specified date range, say for the last 15 days, and take required actions.
Threat Protection Status Report
This report shows information about the email threats with details such as the malicious content along with the malicious email identified and blocked by EOP and Defender for Office 365.
The graphical representation in this report contains the spam, malware, and phishing email statistics depicted based on various detection mechanisms. The detection technologies include machine learning analysis, policies configured in the organization like anti-phishing, safe links, safe attachments, spoofing with external domains, intra-org spoofing, and so on.
For instance, if a malware is detected in an email, you can get to know what malicious content was found in the email; be it the files or URLs that might have been blocked by any of your configured safe links, safe attachments, or other anti-malware/anti-phishing policies. With the help of this report information, you can decide if the organization’s policies require amendments and take the necessary steps.
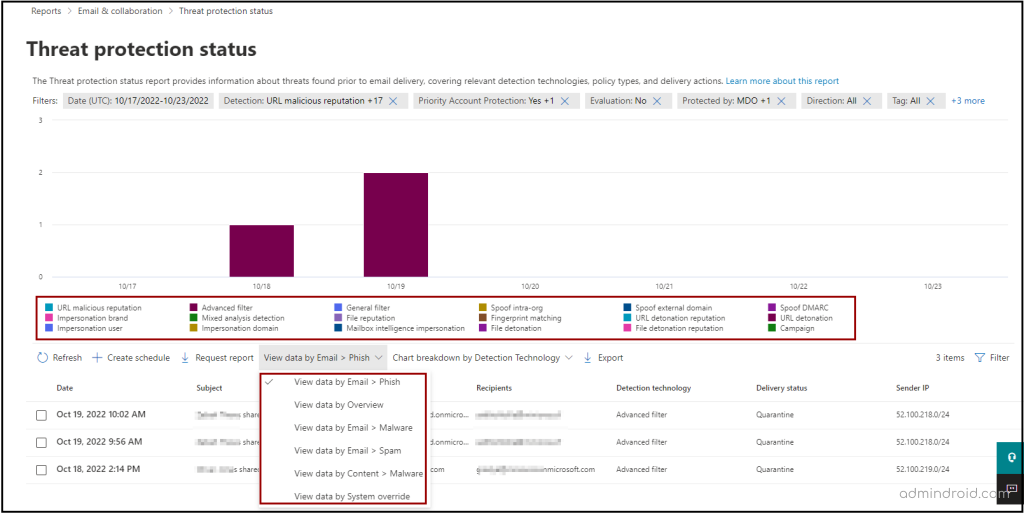
The chart shows data for the last 7 days by default. You can filter this report to view trends and details for any specified time interval from 30 – 90 or custom date ranges.
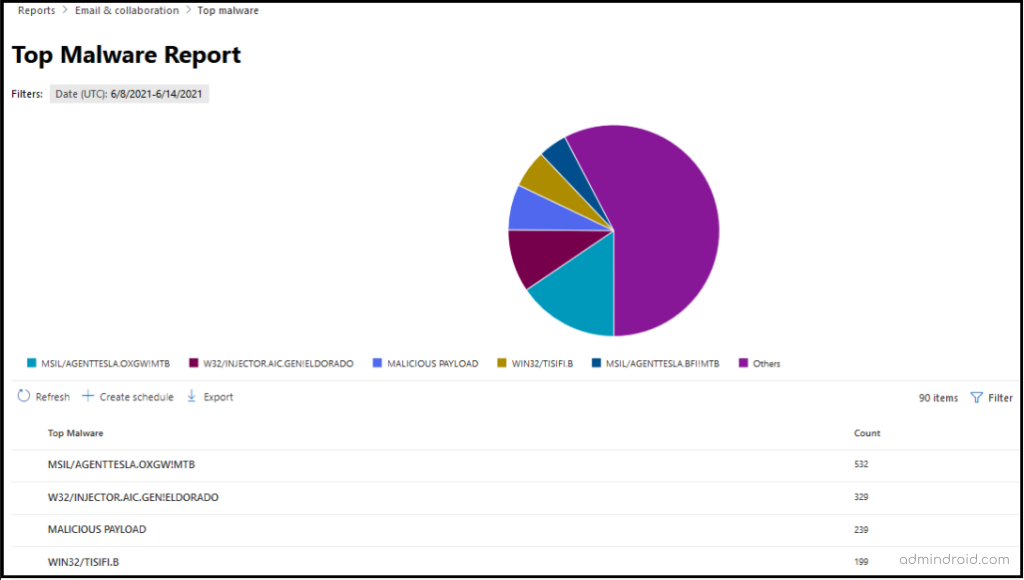
Top Malware Report
The top malware report brings forth the malware that has hit your organization the most, along with the number of email messages that are detected to be having that malware. These malwares are detected by the anti-malware protection in EOP.
By keeping track of this report, admins can be aware of the malware that’s consistently being encountered and take appropriate actions for blocking it to safeguard the organization.
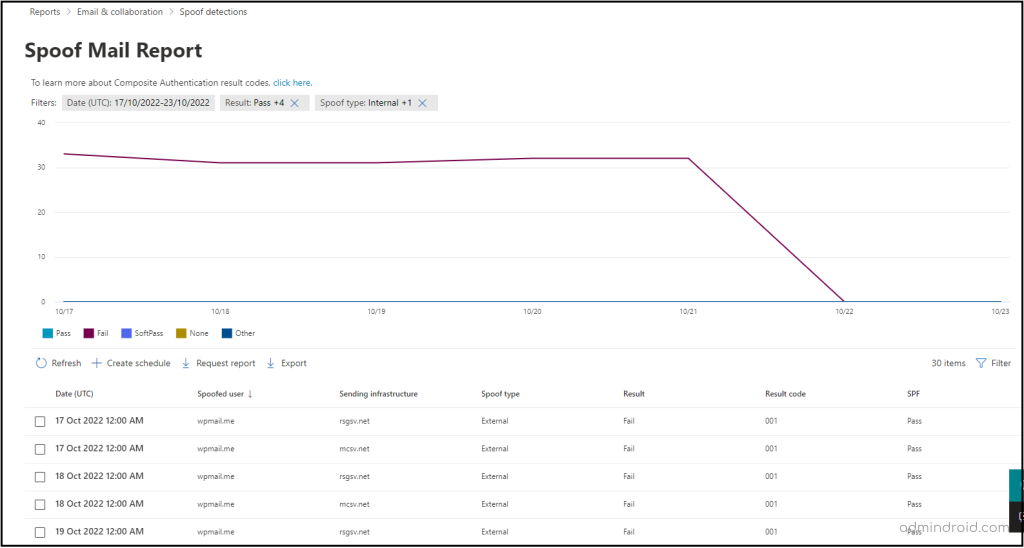
Spoof Detections Report
Sending emails with a forged sender address leads to potential risks. To have a watch on such incoming emails, the spoof detection report will be helpful. This report shows details about the spoofed emails with information such as the spoofed domain, the sending infrastructure, whether it’s internal or external, the number of emails from a spoofed domain, and the results of SPF/DKIM/DMARC checks.
For instance, a user in your organization receives an email from a domain, say ‘contoso.com’; but the email was sent actually sent from an outlook.com address. So, the sending infrastructure here would be outlook.com, and the spoofed user domain would be ‘contoso.com’.
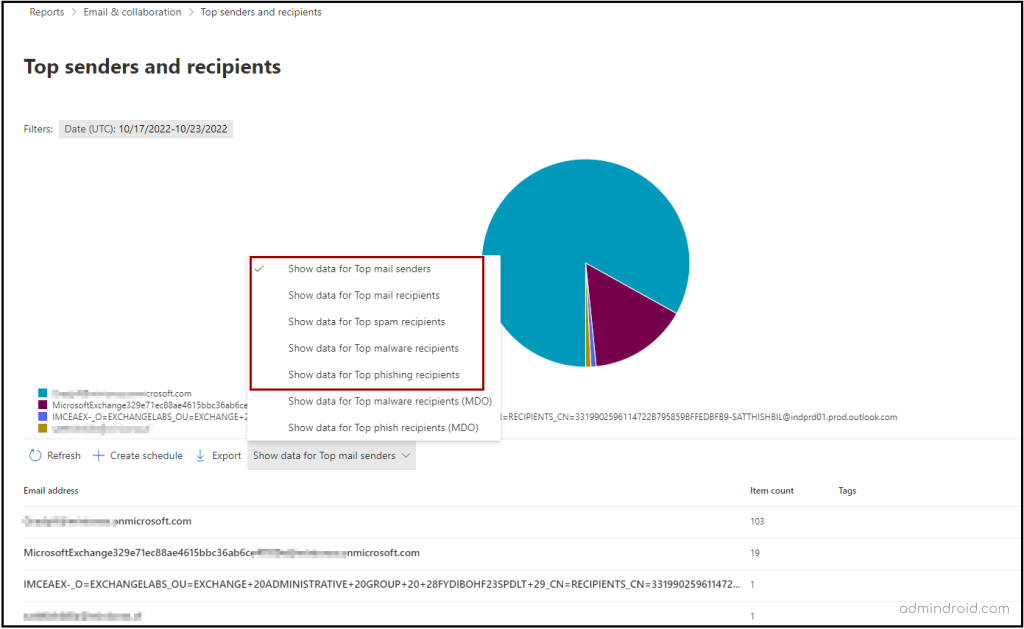
Top Senders and Recipients Report
This report will let you know the top mail senders and recipients in your organization. The report exposes data for the top mail senders and recipients, top spam recipients, top malware recipients, and top phish recipients as individual pie-chart representations along with the sender/recipient, and the message count.
By default, the report shows data for the last week; however, data is available for the last 90 days. You can filter the report and view your desired data for any specified time interval.
In addition to the aforementioned reports, there are more reports to track auto-forwarded messages, transport rule matches, compromised users, URL threat protection, and unusual email flow in both the M365 Defender portal and Exchange Admin Center. I recommend you to check out those reports as well.
By monitoring all these reports consistently, you can take action to configure necessary anti-spam, anti-malware, transport rules, and more such policies to enhance the security of the users and the organization.
Streamline Mail Flow Monitoring with AdminDroid
Relying solely on the native auditing system for mail flow status insights can leave admins with inadequate information. While it provides a glimpse into a few statistics, these limited attributes fall short of what is truly necessary for mail flow monitoring. There are more things admins need to know, like what operation was performed, by whom, activity time, etc.
But fear not, for there is a solution that surpasses limited attributes and elevates the email auditing experience to unprecedented heights. AdminDroid email analytics lets admins monitor mail flow status summary, threat protection status, mailbox traffic reports, and much more. 💥
Let’s explore the different reports offered by AdminDroid email analytics and see how they can help admins monitor mail flow in their organization!
Mail Flow Reports:
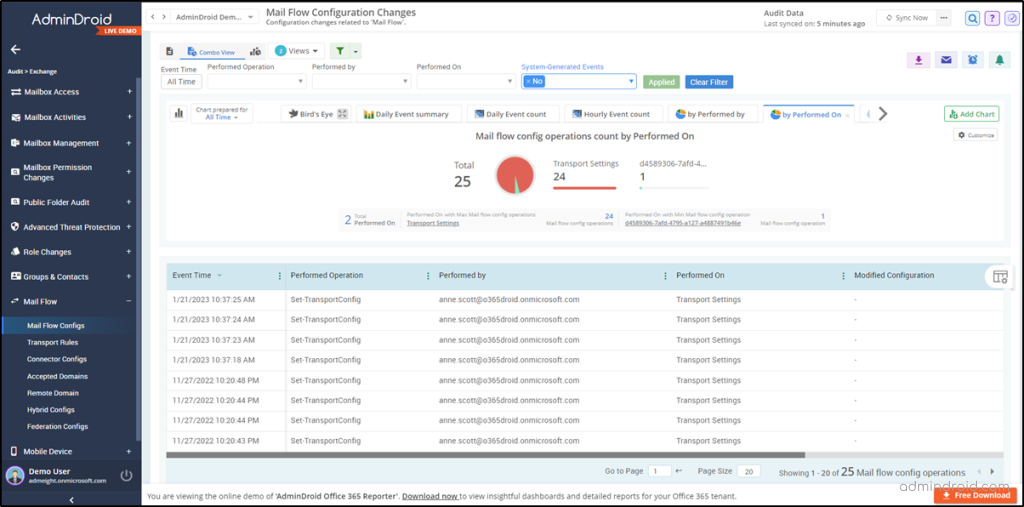
- Mail flow configuration changes
- Mail flow status report
- Transport rule changes
Suspicious Email Activity Reports:
- Incoming external spam/phish/malware mails
- Outgoing external spam/phish/malware mails
- Internal spam/spoof/malware mails
- Internal phish mails
- External spoof mails
Threat Protection by Malware Detection Reports:
- Malware engine-based detections
- Detonation/Reputation/Campaign malware detections
- File/URL based malware detections
Top Email Statistics:
- Top spoofs/malwares
- Top mail senders/ receivers
- Top spam senders/ receivers
- Top phish senders/ receivers
- Top malware senders/ receivers
Efficient Email Monitoring Solution –AdminDroid
Insightful stats and deep analysis of email activities give admins a crystal-clear visualization of the organization’s mail flow, making it easier to stay on top of everything. 🔍📈 With the AdminDroid email activity monitoring tool, admins will receive instant alerts on suspicious emails, unusual mail flow, malicious mail detections, and more. It ensures that admins act quickly to keep the organization safe and secure. And with delegate access, email admins are allowed to access only the email dashboard and email-related reports, maintaining a robust security posture.
But AdminDroid isn’t just limited to email protection reports – it offers 1800+ reports with in-depth details, 30+ dashing dashboards with compelling insights, and numerous features to effectively manage all Microsoft 365 services. 📊 But that’s not all! AdminDroid goes above and beyond with advanced features like delegation, advanced scheduling, and advanced filtering, making Microsoft 365 management a breeze!
I hope this blog has provided you with an overview of the email security reports that you can take a look at, and securely handle the emails in your organization.






