On Day 3 of Cybersecurity awareness month, learn the top Microsoft Entra ID secure score recommendations to improve your organization’s security. Stay tuned for the upcoming blogs in our M365 Cybersecurity blog series.
There’s no silver bullet with cybersecurity; a layered defense is the only viable option
-James Scott
As the quote goes, admins need to configure various security settings to have a layered defense to safeguard the Microsoft 365 environment. One such vital metric every organization should implement is the Microsoft secure score recommendations. Organizations having Entra ID P1 and P2 licenses can implement these top 5 Microsoft Entra ID secure score recommendations based on Conditional Access policy required to enhance the security framework.
Let’s dive deeper into the top Entra recommendations and how to create CA policies for each of them using your Entra premium licenses.
Top Microsoft Entra ID Secure Score Recommendations
Below are the top Microsoft Entra ID secure score recommendations especially for the organizations having Entra ID P1 and P2 licenses.
- Enable Microsoft Entra ID identity protection sign-in risk policies
- Enable Microsoft Entra ID identity protection user risk policies
- Enable conditional access policies to block legacy authentication
- Ensure sign-in frequency is enabled, and browser sessions are not persistent for administrative users
- Protect your tenant with insider risk condition in conditional access policy
1. Enable Sign-in Risk Policies in Microsoft Entra Identity Protection
Configuring sign-in risk policies in Microsoft Entra ID ensures that any suspicious sign-ins or risky sign-ins should satisfy the multi-factor authentication challenge. Enabling the sign-in risk policies helps to prevent password cracking, account breaches, etc.
How to Configure Sign-in Risk Policy in Microsoft Entra ID?
Admins can create a sign-in risk-based Conditional Access policy to ensure that no suspicious sign-ins are allowed to access Microsoft 365 services or resources to prevent account compromise, data loss, etc.
2. Enable User Risk Policies in Microsoft Entra Identity Protection
Configuring user risk policies helps to detect that a user account has been compromised. You can configure a user risk CA policy to automatically respond to a specific user risk level, such as blocking access to the resources or requiring a password change, etc.
How to Configure User Risk Policy in Microsoft Entra ID?
Admins can create a user risk-based Conditional Access Policy to prevent users with several levels of risk from signing into Microsoft 365. Based on the severity, the users will be either blocked or required to satisfy multi-factor authentication to access M365 services.
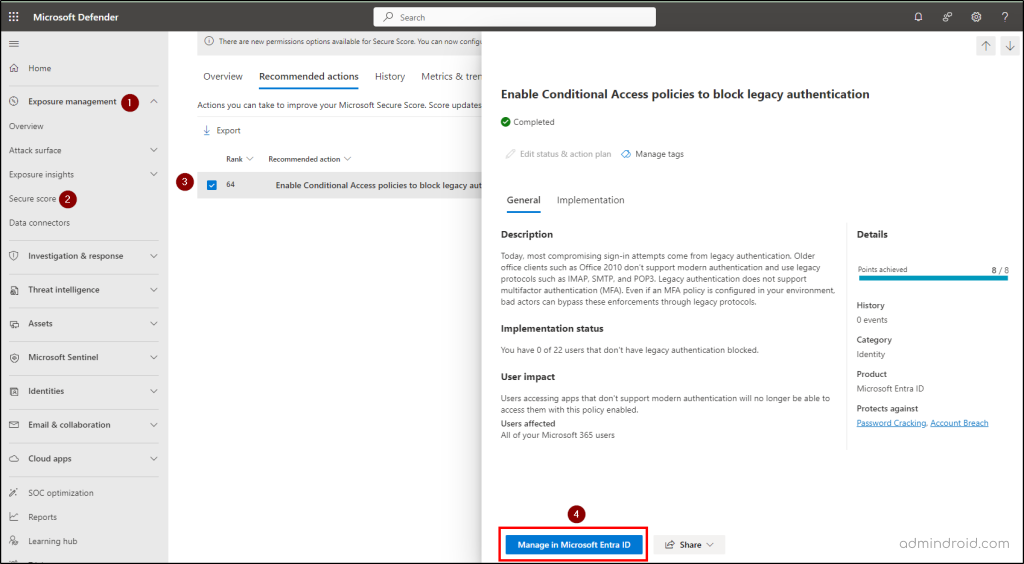
3. Enable Conditional Access Policies to Block Legacy Authentication
Legacy authentication leads to the most compromising sign-in attempts in today’s world. Also, Microsoft deprecated basic authentication protocols to mitigate risks among organizations. Older Office clients don’t support modern authentication and use legacy protocols such as IMAP, SMTP, and POP3. Even if MFA is configured in your environment, bad actors can bypass the MFA enforcement using legacy protocols.
- Navigate to the secure score recommendations page in Microsoft Defender.
- Search and locate the ‘Enable conditional access policies to block legacy authentication’ recommendation.
- Click on ‘Manage in Microsoft Entra ID’, and you will be navigated to the Conditional Access page in the Microsoft Entra admin center.
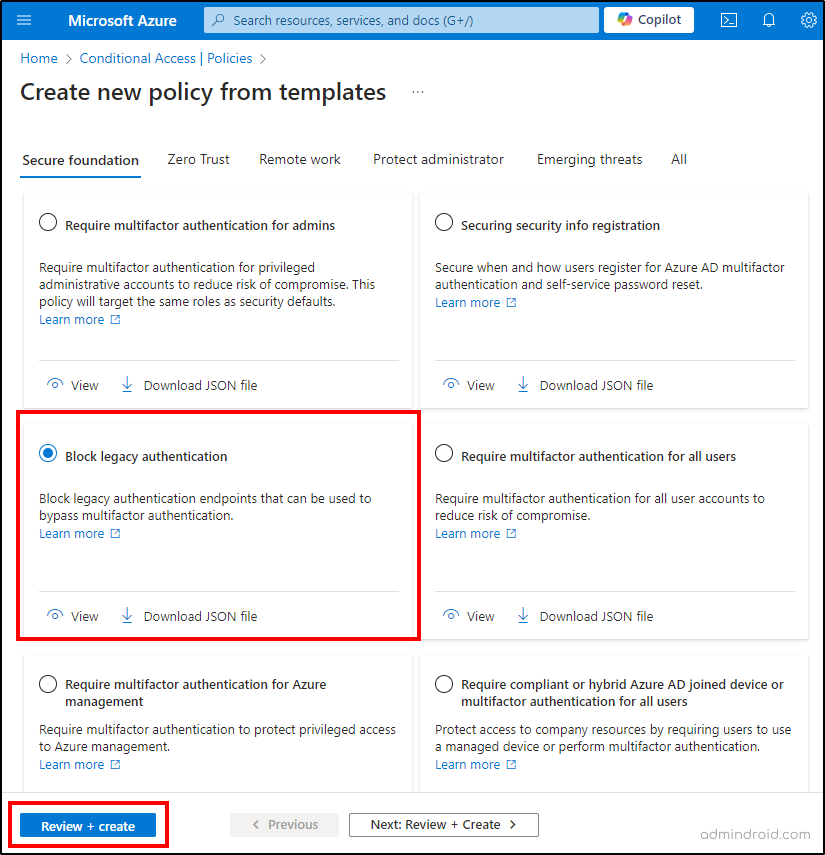
- Click on ‘New policy from template’ and select ‘Block legacy authentication’ template.
- Choose ‘Review + create’ to review the settings and create a CA policy to block legacy authentication protocols.
This recommendation helps to prevent password cracking, account breaches, etc.
4. Ensure Sign-in Frequency is Enabled, and Browser Sessions are Not Persistent for Administrative Users
Browser sessions that are kept alive for an indefinite period led to drive-by attacks in web browsers. Forcing the MFA timeout helps to ensure that sessions aren’t alive for longer periods. Ensuring that browser sessions are not persistent prevents the creation and saving of session cookies.
Follow the steps below to implement this Entra ID recommendation.
- Navigate to the Microsoft Entra admin center.
- Click on Protection –> Conditional Access.
- Click on New policy.
- Select ‘Users and groups’. Under ‘Include’, choose ‘Select users and groups’ and then select Directory roles.
- The below directory roles should be included for MFA at a minimum.
- Application administrator
- Authentication administrator
- Billing administrator
- Cloud application administrator
- Conditional Access administrator
- Exchange administrator
- Global administrator
- Global reader
- Helpdesk administrator
- Password administrator
- Privileged authentication administrator
- Privileged role administrator
- Security administrator
- SharePoint administrator
- User administrator
- Go to Target resources -> Cloud apps –> Include –> select All cloud apps (don’t exclude any apps).
- Under Access controls –> Grant –> select Grant access –> check Require multi-factor authentication.
- Under Session, select Sign-in frequency and set it to at most 4 hours (for E3 tenants). E5 tenants with Privileged Identity Management (PIM) can be set to a maximum of 24 hours.
- Check the Persistent browser session checkbox and then select ‘Never persistent’ in the drop-down menu.
- Select On and click Create to enable the policy.
This recommendation also helps to avoid account breaches, data exfiltration attacks, etc.
5. Configure Insider Risk Protection in Conditional Access Policy
Configuring insider risk protection helps to protect critical resources from users based on their insider risk levels. It involves adaptive protection implementation to identify user behavior patterns and respond to them accordingly to protect your organization’s sensitive assets.
Enabling insider risk protection in conditional access policy blocks user access to resources or allow access with certain restrictions based on their levels like elevate, moderate, or minor. By implementing this recommendation, you will be safeguarded from insider threats in your organization.
I hope this blog provides you with the top Microsoft Entra recommendations and the implementation steps for the organizations having Entra P1 and P2 licenses. These top recommendations help to maximize the secure score and improve overall Microsoft 365 security.