On Day 16 of Cybersecurity Awareness Month, learn how to monitor your organization’s activities using Microsoft 365 unified audit log. Stay tuned for more blogs in the Cybersecurity blog series.
A small ignorance from our side can cause a big security impact on our organization. Yes, you get what I say, we must track the Microsoft 365 user activities happening in our organization to prevent security flaws. Especially with the phasing out of Classic Search in Microsoft Purview, adapting to new changes becomes crucial. It requires us to utilize the Audit New Search feature in the Microsoft Purview portal to monitor user activities with greater precision and filtration.
Microsoft 365 audit logs are an added layer of surveillance that provides deeper insight into activities happening in the Microsoft 365 organization. It provides details about all the activities, with who performed them and when. Collectively speaking, audit logs in Microsoft 365 help us to pinpoint the cause of the issue. Basically, the unified audit log in Microsoft Purview is not enabled by default. Admins must enable it manually to record Microsoft 365 activities.
“A Regular Check can protect you from data leaks”.
–Benjamin Addams
How to Enable Unified Audit Log in Microsoft 365?
The audit logs in Microsoft 365 organization can be enabled using two methods:
Enable Unified Audit Log from Microsoft Purview Portal
Follow the steps described here to enable Microsoft Purview audit logs for access:
- Go to the Microsoft Purview compliance portal.
- Under the Solutions category, select Audit.
- If auditing is not turned on for your organization, a banner prompting ‘Start recording user and admin activity’ will be displayed in the New Search tab.
- Click on the banner to enable the audit logs.
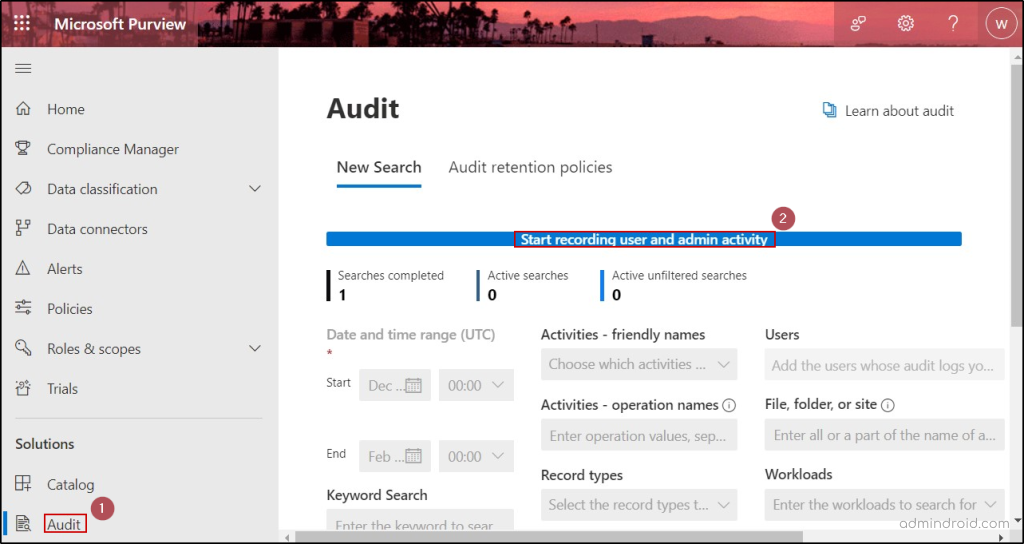
Note: Enabling audit logging allows admins to access the logs using the audit search in Office 365. Once enabled, Microsoft 365 starts to log all activities from that point forward. Events and actions that occurred beyond that point aren’t recorded in the audit log. To specifically track object deletions in Entra ID, admins have to use Entra audit logs or MS Graph API.
Enable Unified Audit Log Using PowerShell Cmdlets
First, make sure to connect to the Exchange PowerShell module. Since the cmdlets we are going to use belong to the EXO module, ensuring the connection is necessary.
To make sure the audit log search is turned on or off, you can use the “Get-AdminAuditLogConfig” as demonstrated here:
|
1 |
Get-AdminAuditLogConfig | Format-List UnifiedAuditLogIngestionEnabled |
The above execution will return either True or False based on the current status of the audit log.
To enable the audit log, run the following cmdlet.
|
1 |
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true |
If you want to disable the unified audit log in Microsoft 365 (not recommended), execute the following cmdlet.
|
1 |
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $false |
Note: Generally, it takes 60 minutes for the changes you have made to be reflected.
Audit New Search in Microsoft Purview with Improved Search Filters
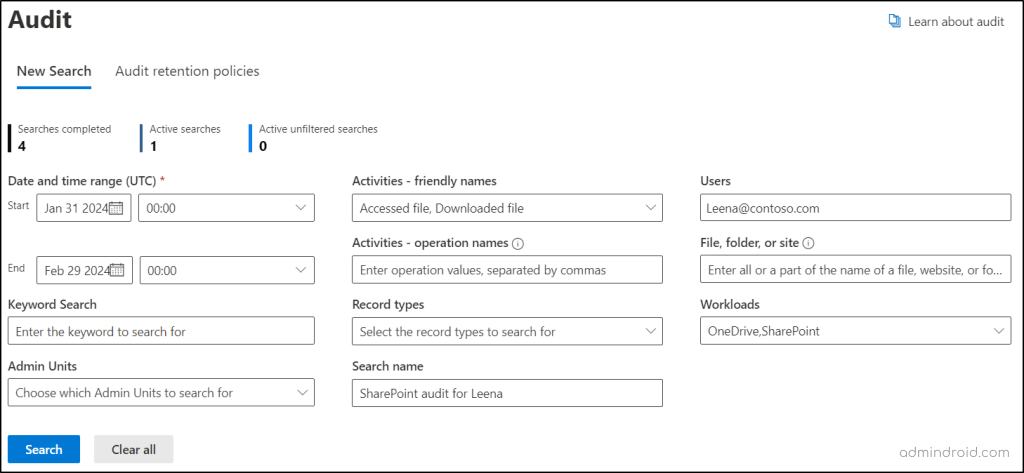
When you navigate to the audit – New Search window in Microsoft Purview, you can narrow down your search using the following filters. In contrast to the previous Classic Search, which lacked many search categories, this New Search offers an improved audit log experience with advanced and flexible search criteria.
Date and time range (UTC): The maximum retention period for Microsoft Purview Audit (Standard) logs is 180 days. If the specified date and time range exceed this limit, an error stating “Search duration is too long. Please select a date range less than 6 months” will be displayed.
Activities – friendly names: This drop-down allows you to choose activities based on various workloads to audit file downloads, audit email deletions, monitor SPO site creations, and more.
Users: You can mention specific users in this text box to track user activities in Microsoft 365.
Activities – operation names: Here, use the list of operation names to monitor activities like groups created in Microsoft 365, members removed from Microsoft groups, etc. An operation name is a technical identifier assigned to each specific operation or activity, while a friendly name is a user-friendly label assigned to an activity or operation.
File, folder, or site: Here, you can enter the name or URL of the files, sites, or folders to get only the related Microsoft 365 audit logs. The wildcard character (*) is also supported here.
Keyword Search: This criterion can be used to search for activities related to a keyword or phrase.
- For example, entering the keyword “Delete” will list deletions that have taken place in users, folders, groups, sites, etc. To search keywords with special characters, you can use asterisks (*).
Record types: Choose the specific Microsoft 365 record types (refers to a classification or category assigned to organize and manage data).
- For instance, if you’re targeting searches related to sensitivity labels in Microsoft Purview Information Protection (MIP), choose record types like MIPLabel, MipAutoLabelExchangeItem, and MipAutoLabelSharePointItem.
Admin Units: In this drop-down, you can select administrative units in Entra ID to narrow the scope of your audit search.
Search name: Here, provide a name for the audit search that is going to be performed.
With AI workloads becoming integral to business operations, monitoring AI interactions is as crucial as tracking traditional Microsoft 365 activities. DPSM for AI acts like an audit log for AI-related activities. Through the Activity Explorer, it lets admins see the type of activity, user, date and time, app accessed, and any sensitive information involved.
How to Access Audit Logs in Microsoft 365 Compliance Center?
To access or search for audit logs through the New Search audit from the Microsoft Purview compliance portal, follow the steps described here:
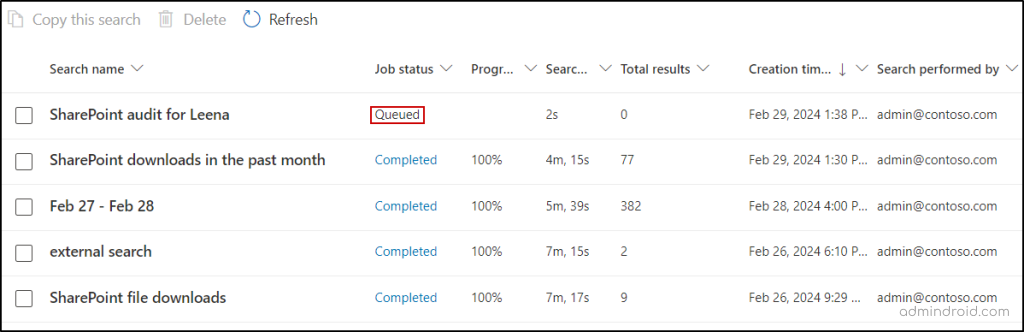
- Select the Date and time range (UTC). Then, select other search criteria, if you wish to filter the search.
- Make sure to specify the name for the search in the Search name text box and click the Search button.
- The search will be queued and will be completed within some time based on the search query. After completion, the Job status will change to Completed. After that, you can click on a particular search to access the audit reports.
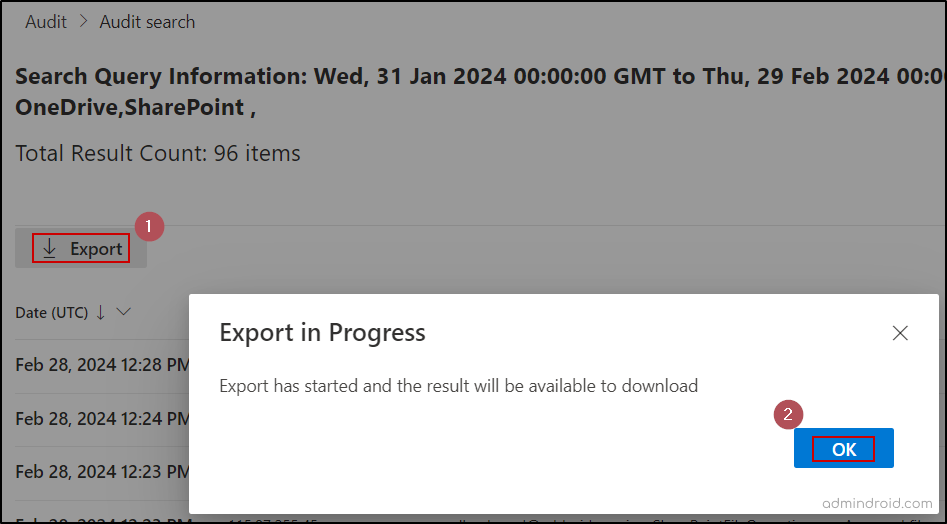
- If you wish to download Microsoft 365 audit logs as a CSV file, you can use the Export button and select OK.
A Quick Checklist to Effectively Monitor Microsoft 365 User Activities
Audit logs list all the activities performed in the Microsoft 365 environment. There are lots of activities happening in the organization, but not all the activity affects the organization’s security! To improve security, you can check workload-specific activities. Here’s a checklist that covers important activities that require Microsoft 365 admins frequently. Make sure to audit the Microsoft 365 user activities below and have a safe environment.
Get SharePoint Audit Reports:
We use SharePoint to store, share, and access all the organizational details from any device. It is, therefore, important to safeguard the data it contains and keep tabs on SharePoint permission changes and user access frequently. Check the mentioned SharePoint Online audit logs to make your site data leakproof.
- User or group added to SharePoint site: The users added to SharePoint groups must be supervised by the admin to prevent data leaks.
- Audit SharePoint site permission changes: The sharing setting defines how and with whom your organization’s data is shared. Monitor SharePoint permission level changes and ensure no critical SharePoint sharing setting changes go unnoticed.
- SharePoint file access logs: To find unauthorized and anonymous file activities, it is essential to monitor file access in SharePoint Online auditing.
- Audit external file sharing: Admins need to monitor what files are shared with external users to avoid any accidental sharing. To prevent data leakage, admins can utilize SharePoint audit logs to generate reports on audit external file sharing.
Get Microsoft Teams Activity Logs:
Microsoft Teams is the communicative hub for easily sharing information both internally and externally. Therefore, monitoring audit logs for events in Microsoft Teams is essential to maintain productivity and enhanced security. Check the below-mentioned audit reports to track Microsoft Teams activity.
- Audit Microsoft Teams membership changes: Microsoft 365 users within teams and channels have access to the data and files shared within those channels. Any unauthorized person added to the team can potentially lead to data leaks. Hence, Microsoft Teams membership changes should be monitored.
- Files shared with external users: Track external sharing in Microsoft Teams audit logs to make sure none of the sensitive data is shared unintentionally.
- Sent invitation for shared channel: Shared channels possess the capability to extend invitations to external users. Therefore, it is essential to examine the shared channel creations and the invitations sent from them to detect any instances of anonymous user additions.
- Audit MS Teams meeting activities: Monitoring chats and meeting activities in Team audit logs assist in internal investigations when needed. This also facilitates more effective responses to security events and ensures compliance with regulations.
Get Exchange Online Audit Reports:
Obtaining Exchange Online audit reports is crucial for maintaining a secure and compliant email environment. These mailbox audit logs provide valuable insights into Microsoft 365 email statistics by users, guest user mailbox activities, mailbox permission changes, and more. Ensure Exchange Online mailbox activities auditing through the below-mentioned reports to secure sensitive mailbox contents.
- Audit email deletions in Outlook: Purging Exchange Online emails will delete them permanently (hard delete). What if important emails are purged? Therefore, you must audit email deletions in Microsoft 365 to identify the emails that are deleted, soft deleted, or permanently deleted.
- Audit mailbox permission changes: Delegated access can let the Microsoft 365 users to read, manage, and send emails from other’s mailboxes. To ensure a secure environment, mailbox permission changes must be audited.
- Exchange Online mail flow reports: Audit Exchange Online activity for mail flow configuration and transport rules to find the reasons behind email delivery failures.
- Non-owner mailbox access: Through Exchange Online mailbox delegation, non-owners can access the mailbox. To secure unauthorized access, non-owner activities are monitored.
Get Power BI Audit Logs:
The insight into the organization’s data can be obtained from Microsoft Power BI reports. So, the reports in Power BI must be safeguarded, and access to these reports must be tracked. Export Power BI audit logs on these mentioned activities to monitor and secure your M365 data.
- Track user activities in Power BI: Since essential organizational data is available through Power BI, it is essential to monitor user activities in Power BI dashboards and reports.
- Audit Reports downloads in Power BI: Downloading is a common activity, but there is no need for everyone to download Power BI audit reports. Therefore, it is essential to monitor the users who download them.
- Get audits from all workspaces in Power BI service: Retrieving audit logs from all workspaces provides a centralized way to monitor report usage metrics across the entire Power BI environment. By accessing these audits, admins can analyze report usage patterns and monitor user activities to prevent data leaks.
How Long Are Audit Logs Retained in Microsoft 365?
The Microsoft 365 Purview (Standard) customers can retrieve audit logs for up to 180 days (previously 90 days). To access data beyond this period, a higher license, such as E5, A5, or G5, is required, but it may incur additional costs! Microsoft Purview Audit Premium license customers can retain audit logs for up to 10 years.
But here’s the interesting part: Now with basic plans, admins can access additional audit events that were previously exclusive to the premium subscription. This includes 30+ new activities such as mail items accessed, MS Teams messages read, new chats created in MS Teams, and more.
Is it possible to get an audit log older than 180 days without an E5 license? Yes. You can search audit logs using PowerShell to retrieve the audit data for up to one year.
|
1 |
Search-UnifiedAuditLog -Startdate <mm\dd\yyyy> -Enddate <mm\dd\yyyy> |
With ‘Search-UnifiedAuditLog’, you can retrieve the audit data for up to one year for all license types. There is no official announcement regarding this long-term audit log capability. However, most tenants have the ability to retrieve audit data for 365 days.
Note: The “HighCompleteness” parameter (currently in Preview – MC736435) can be used with cmdlet to get more comprehensive search results, but it may require a significantly longer time to process.
Master Office 365 Tracking & Monitoring with AdminDroid!
While Office 365 audit logs offer some insights, they come with limitations that may leave you wanting more.
One notable limitation of depending on audit logs is their 90-day range, but AdminDroid Microsoft 365 auditing tool breaks free from this constraint!
However, with AdminDroid, you can overcome these limitations and gain a deeper understanding of your organization’s activities in a heartbeat! Moreover, AdminDroid offers a unified view of the audit information, making it easier to track and monitor activities across multiple Microsoft services.
It provides comprehensive visibility with its 360-degree view and dedicated dashboards. You can effortlessly monitor auditing and reporting for Microsoft 365 solutions including Azure AD, Exchange Online, SharePoint Online, OneDrive, and Microsoft Teams using AdminDroid.
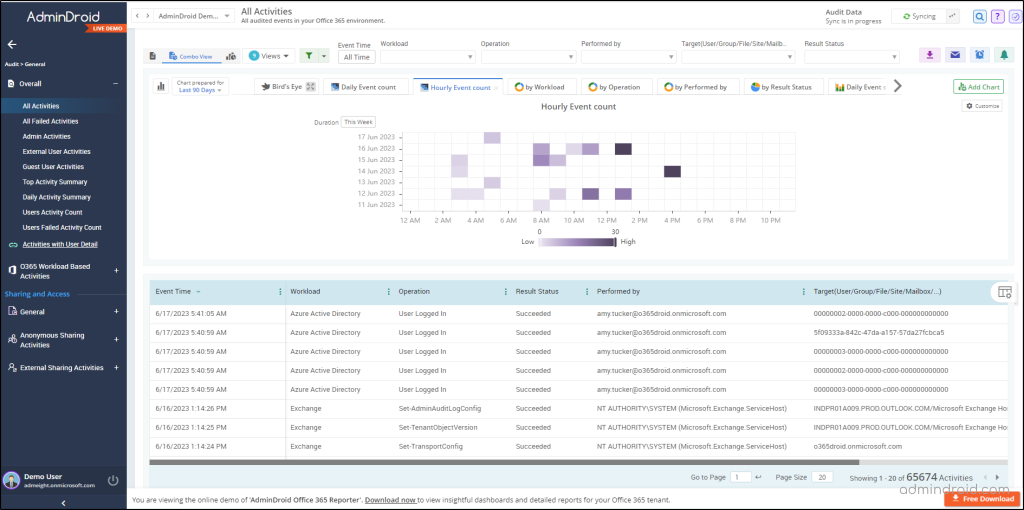
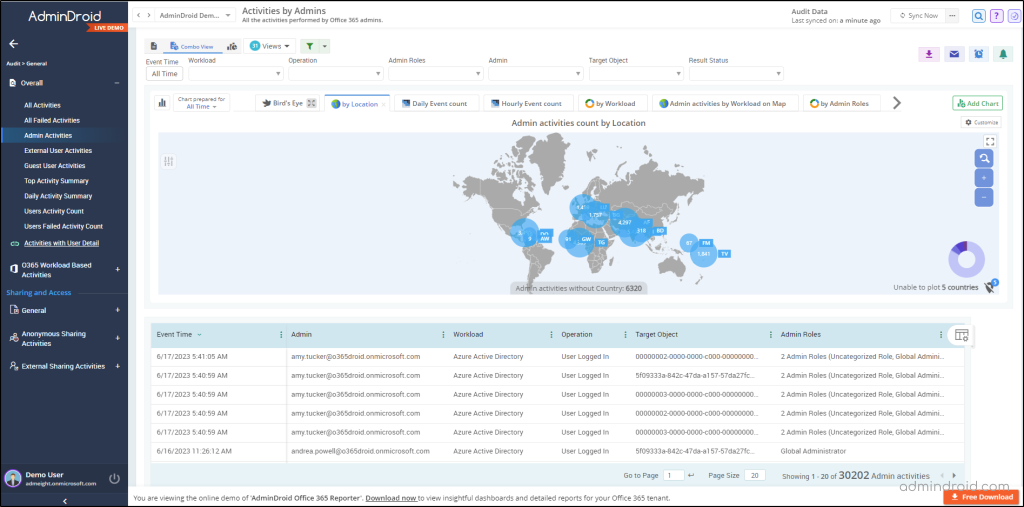
AdminDroid goes beyond the basic audit logs and offers visually appealing charts, graphs, and detailed insights on various Microsoft 365 services. Whether it’s the management of Azure AD, Exchange Online, Microsoft Teams, SharePoint Online, OneDrive for Business, Microsoft Yammer, or other real-time updates on your Microsoft 365 environment, AdminDroid Microsoft 365 auditing tool has got you covered! 💯
With AdminDroid, you can effortlessly track essential activities, including,
- Microsoft 365 User logins auditing
- Exchange Mailbox permissions
- SharePoint Online usage reporting
- Microsoft OneDrive auditing
- Teams’ management reports
Moreover, AdminDroid empowers you to pinpoint issues through thorough report auditing and promptly address any unexpected events that may occur.
Don’t settle for limited native logs! Download AdminDroid today and unlock a world of comprehensive reports, efficient management, and enhanced security for your organization. Plus, take advantage of the free 15-day premium license to experience the full capabilities of AdminDroid.
Wrapping Up!
It is better to notice the issue before it gets out of hand. So, monitor your tenant activities at regular intervals using a unified audit log. Hope we have fulfilled your requirements regarding the unified audit logs. If you have any further queries, feel free to reach us through social media. We would be glad to assist you!






