After the Entra Suite Camp, Microsoft kicked off a three-part webinar series focused specifically on why and how to unify identity and network access for stronger security. This is a Practitioner series hosted by Merill Fernando, Product Manager at Microsoft, known for his insightful weekly Entra newsletter.

If you’re an identity or network admin, this webinar series is for you! Even if you missed the first webinar, I’ve summarized what was covered in the foundation session.
The IDC Whitepaper That Set the Stage!
The webinar referenced an IDC whitepaper titled “A Guide to Unified Identity and Network Strategy”, authored by Chris and Emmanuel from IDC. The research dives into the challenges organizations face with hybrid workforces, cloud collaboration, and 3rd party access, and why unifying identity and network controls has become critical.
We all know hybrid and remote work is now the norm, not an emergency plan. IDC reports that 73% of organizations manage hybrid or remote workforces that rely heavily on cloud collaboration and 3rd party access, yet over 60% admit their current access controls can’t keep up!
In other words, many are trying to govern today’s dynamic access patterns with a security model built for the last decade. 💯
The whitepaper includes plenty of real-time feedback and survey insights from organizations, highlighting both the tools they’ve adopted and the gaps they still face.
You can read the complete IDC report here.
The one amusing thing was AI risks now top the list, surpassing even malware and ransomware threats! This isn’t hype, AI is evolving so fast that it’s now displacing ransomware from the Top 3 threats.
Whereas AI even presents a dilemma, and I loved how Kaitlin phrased it: AI introduces new risks that must be secured, but also provides opportunities to improve security.
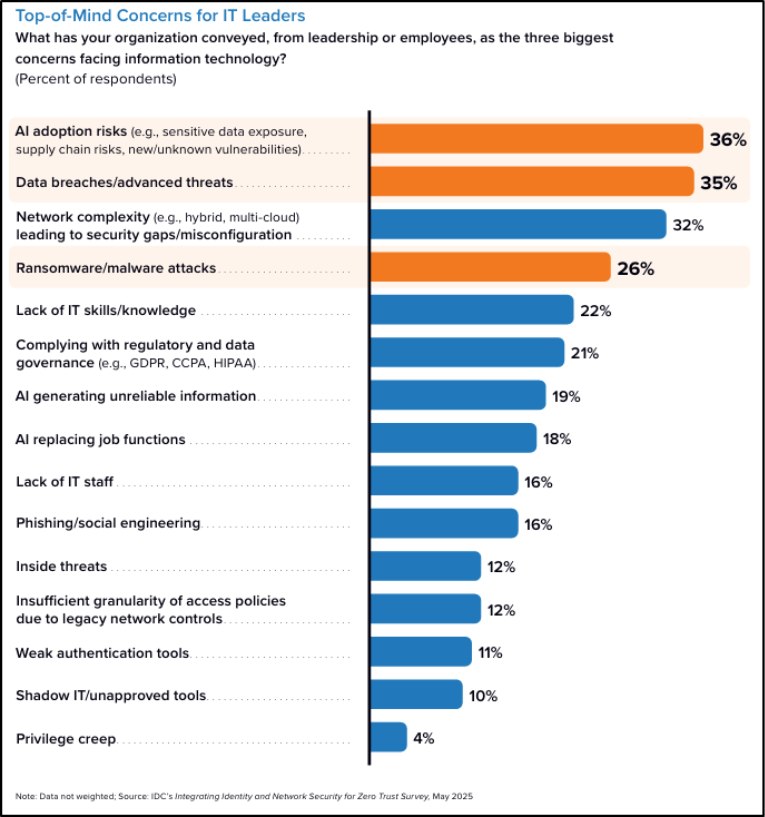
She pointed out that the focus is now expanding from human users to non-human identities, creating an urgent need for stronger controls. So, the clear solution that should be embraced by practitioners to board members is to integrate and unify signals across users, devices, networks, apps, and the internet. Doing so reduces blind spots, avoids duplicate spending, and improves the employee experience.
While discussing this, Chris highlighted a striking statistic: despite widespread awareness, many organizations are still behind! Most continue to rely on legacy firewalls and VPNs, and although 90% use MFA, SSO, and password managers, roughly 60% haven’t adopted advanced tools such as SWG, ZTNA, PAM, or RBA.
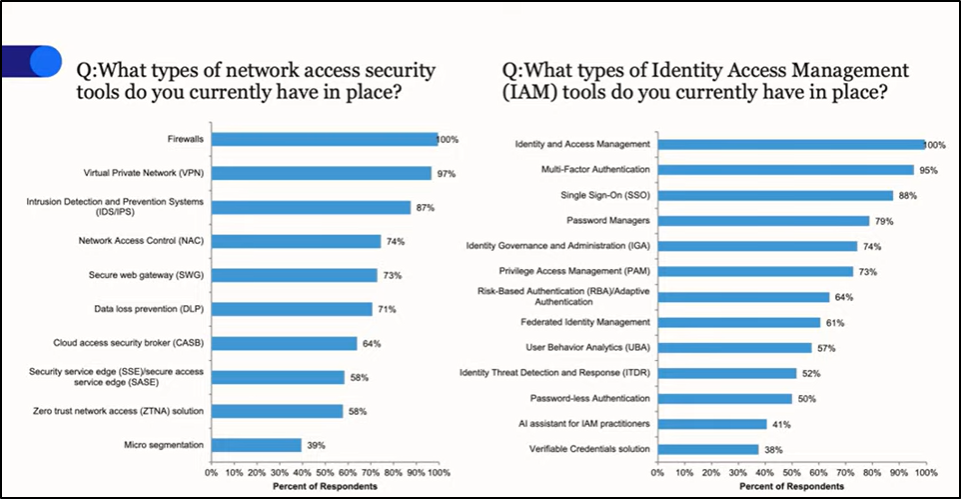
This reason justifies enough and tells us to focus on integration!
Chris emphasized that integration is both a security imperative and a strategic investment. To truly implement Zero Trust, identity and network access cannot operate in silos. Unification doesn’t mean replacing everything; it means orchestrating existing tools under a single decision-making framework for stronger security, better visibility, and more efficient operations.
Problems with Integration:
A major challenge with integration is that identity and network teams often work in silos. While leadership may see them as aligned, true collaboration is still lacking. Tools like Microsoft Entra Suite require expertise from both teams to successfully unify identity and network controls.
So, the key takeaway suggested by Merill is don’t overlook collaboration; it’s just as important as the technology itself when building an integrated security strategy.
Q&A Highlights from the Webinar
After the discussion on the IDC whitepaper and key stats, I really enjoyed the Q&A segment! 💯 Merill posed several insightful questions that made the webinar engaging and kept everyone focused. Below is a summary of the questions, along with the key points and takeaways from the answers.
Question 1: What are the first steps organizations are taking to unify identity and network access?
Unsurprisingly, traditional IAM, traditional network, or Endpoint security are everyone’s starting territory still. Anyhow, many teams are layering in more advanced, cross-functional tools like SOAR (Security Orchestration, Automation, and Response), SIEM (Security Information and Event Management), NAC (Network Access Control), and DLP (Data Loss Prevention). The market trends back this up:
- SOAR is projected to grow by 18%
- XDR (Extended Detection and Response) by 15% in the next year
It’s clear that organizations are no longer treating identity and network as separate silos; they’re building a single, adaptive defense model around both.
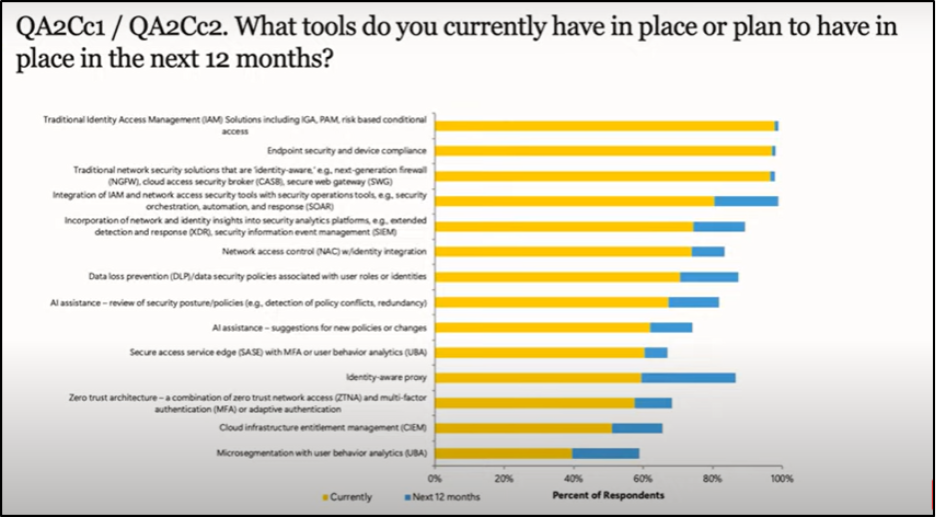
Kaitlin highlighted that another significant trend is the adoption of Zero Trust access frameworks, such as Microsoft Entra Suite.

Many organizations are finding that Entra Suite makes access simpler and more secure by:
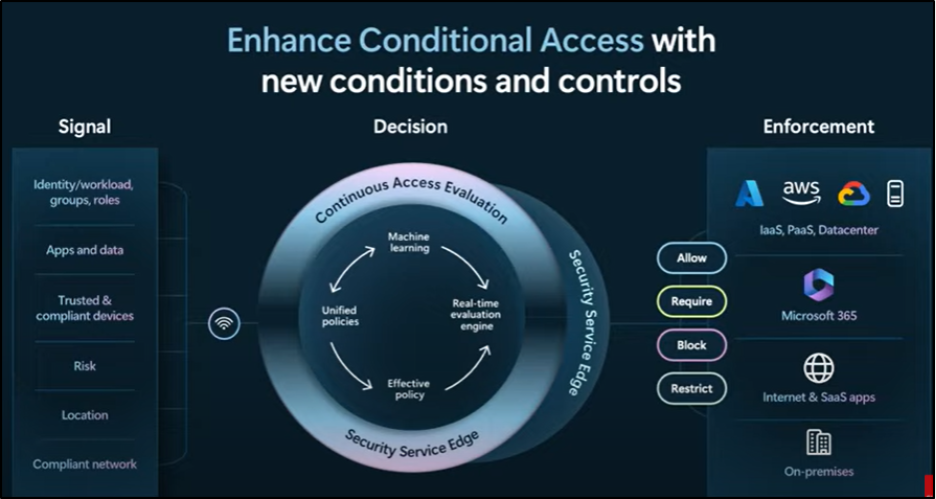
- Extending Conditional Access across all users, devices, apps, and networks to minimize the attack surface while keeping experiences seamless.
- Managing user lifecycle, entitlements, and access rights in one unified platform.
- Enabling secure collaboration with partners, vendors, and customers.
- Using risk-based adaptive access to automatically respond to risky sign-ins or compromised accounts.
This unified approach reduces the attack surface and ensures that every access request is verified, no matter where it comes from, on-premises, in the cloud, or from AI-driven apps.
Finally, Merill wrapped up the question by noting that many organizations are rethinking their network trust model. Rather than relying on broad, legacy VPN access, they’re moving toward app-level trust with default segmentation.
Question 2: What role does Identity Governance play in a unified identity and network access strategy?
How can organizations modernize access reviews and policy management to keep pace with SaaS growth and AI-driven access?
Chris emphasized that Identity Governance is the central decision layer in any unified identity and network access strategy. It connects access controls with real-time threat intelligence, user context, and device posture, ensuring that every access decision is informed and secure. As organizations face rapid SaaS adoption and AI-driven access patterns, governance must evolve from static, reactive compliance checks to a dynamic, proactive engine that keeps pace with change.
To modernize governance, organizations are taking several key steps:
- First, automate access reviews using risk-based and AI-driven insights, so decisions are faster and smarter.
- Replace static rules with dynamic, context-aware entitlements that adapt to user behavior and risk levels.
- Implement policy-as-code frameworks to scale consistent enforcement across complex environments with minimal manual effort.
- Integrate telemetry and monitoring to detect anomalies early and accelerate response.
- Leverage lifecycle workflows, just-in-time (JIT) access, and segmentation to ensure access is granted only when necessary and revoked automatically when it’s not.
The ultimate goal should be to transform identity governance from a reactive, compliance-only function into a strategic driver of risk reduction, operational resilience, and secure productivity.
Don’t worry if this feels too technical — the next webinar will break it all down! You’ll learn about Microsoft Entra Suite, including setting up device Conditional Access, identifying devices, and other essential prep steps to pilot unified identity and network access. Expect plenty of hands-on tips and expert insights to make the process practical and easier to follow.
Question 3: What additional visibility do organizations gain by consolidating identity and network tools?
Kaitlin explained that by unifying identity and network controls, organizations gain a single policy engine that offers complete visibility across users, devices, and network conditions. This consolidated view
- Simplifies troubleshooting
- Reduces policy drift and
- Speeds up response times because identity, device posture, and network context are automatically correlated.
- It also allows organizations to enforce consistent least-privilege access across all applications, whether they’re cloud-based, on-premises, or public internet apps.
To start, organizations can co-author converged policies, begin with high-value applications, and use audit mode to fine-tune rules before full enforcement. Defining break-glass accounts ensures critical access is never accidentally blocked.
Question 4: What practical steps can organizations take to move from legacy controls to a unified policy claim?
How should network architects and engineers approach unification?
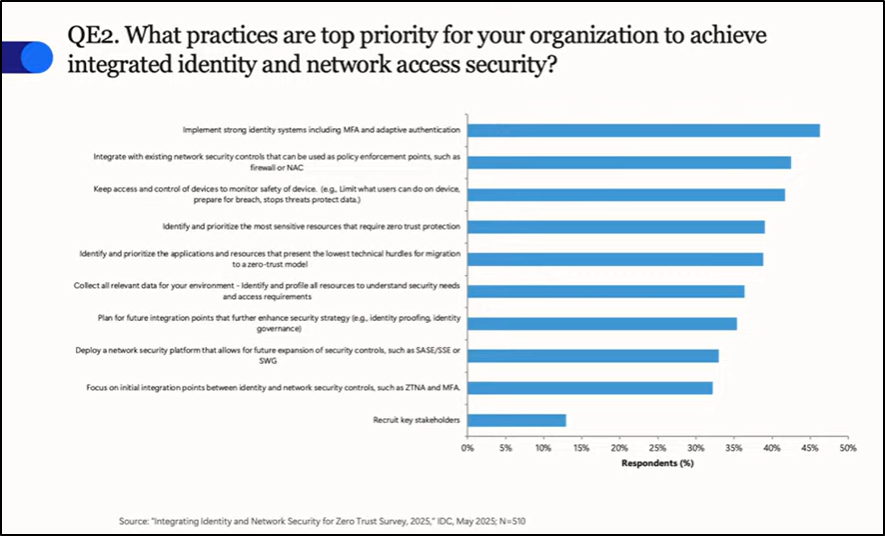
Chris explained that from a security and engineering perspective, modern unification begins with a few key practices that most organizations are prioritizing:
- Implementing strong identity systems with multi-factor authentication and adaptive MFA.
- Integrating identity and network controls to establish consistent policy enforcement points.
- Strengthening device controls to support secure access decisions.
He also noted that while adoption of Zero Trust has been slower historically, its principles are strong, and wider implementation is expected soon.
Despite these efforts, many organizations still face challenges:
- 33% of organizations as top access security concerns.
- 20% struggle with governance gaps
- 17% report inconsistent enforcement.
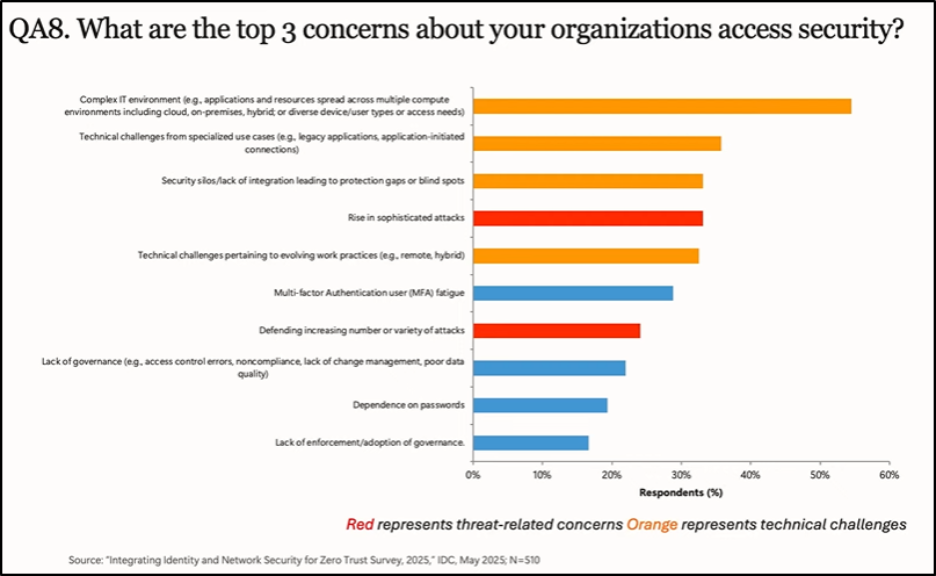
These gaps highlight why a thoughtful, phased approach is essential! The practical way to get started, as suggested in the webinar, is to treat integration as a step-by-step process rather than a big-bang change. For example:
- Run your existing VPN alongside a Zero Trust Network Access (ZTNA) solution so both can coexist. You can take it slowly by replacing VPNs with Microsoft Entra Private Access further.
- Migrate applications gradually, one at a time, using Conditional Access routing with rollback options to fine-tune policies.
This phased approach ensures continuity, reduces risk, and gives teams time to validate policies before fully retiring legacy controls.
Question 5: What do you see as the top benefits of unification?
Speakers highlighted several key benefits organizations gain from unifying identity and network controls. On the security side, the most significant improvement is improved detection and response, cited by 43% of organizations.
Other security benefits include secure remote access and faster incident response.
But unification isn’t just about security; it also delivers business and operational advantages. Organizations reported:
- Reduced overall costs (26%), as integrated systems streamline processes and reduce redundant tools.
- Better user experience (25%), with consistent authentication flows and fewer access issues.
- Lower IT workload, especially related to breach management and help desk support.
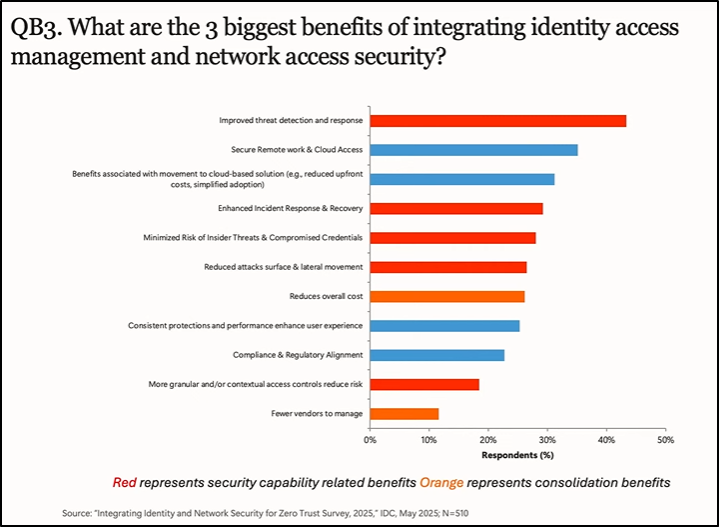
From the end-user perspective, speakers noted benefits like:
- Higher satisfaction
- Improved productivity
- Consistent authentication flows
- Fewer help desk tickets
- Support works faster because it has integrated signals and dashboards.
When implemented correctly, unification is a win-win. I personally loved the phrase by Kaitlin:
Better for the practitioner, better for the end user!
Question 6: How can organizations get started on their journey to unify identity and network access?
For organizations looking to unify identity and network access, speakers emphasized that the journey is more about people and processes than just tools! A few practical starting points include:
- Define the jobs to be done clearly, even if it means going back to basics to understand your current gaps and priorities.
- Bring all teams along, security, IT, network, and business stakeholders, to ensure collaboration and alignment. Integration works best when everyone is on the same page.
- Track results and iterate. Check if the changes you’re making are delivering the expected outcomes and adjust where needed.
- Leverage resources and workshops. Free trials, Entra Suite workshops, and Zero Trust workshops can help accelerate progress, derisk initiatives, and provide actionable guidance.
- Align with Zero Trust principles early. Doing so addresses multiple security and business needs simultaneously and creates a strong foundation for policy enforcement.
- Make the business case. Most importantly, track KPIs, highlight security and operational benefits, and use momentum to secure budget and stakeholder support.
Chris highlighted that unifying identity and network systems brings both business and security benefits. He emphasized that collaboration isn’t just about tools, it’s about people. Feedback from organizations shows that teams with integrated systems report higher satisfaction and smoother collaboration, whereas teams without integration often feel only somewhat satisfied or dissatisfied.
I hope this gives a clear and practical summary of what was discussed in the first webinar, the insights, the stats, and the approaches around unifying identity and network access. ✌️Check out the summaries of the two webinar discussions below, we’ve captured the key takeaways, insights, and highlights from each session.






