On Day 1 of Cybersecurity Awareness Month, we’re kicking off with the risks of using Office IPs as trusted locations in Conditional Access. Stay tuned for more blogs in the Cybersecurity blog series.
Cybersecurity Awareness Month has begun, and so has our 31-day security series! 🎉 This time, we’re going bigger – not just Microsoft 365, but also AI, Active Directory, hybrid setups, and broader security practices will take the stage.
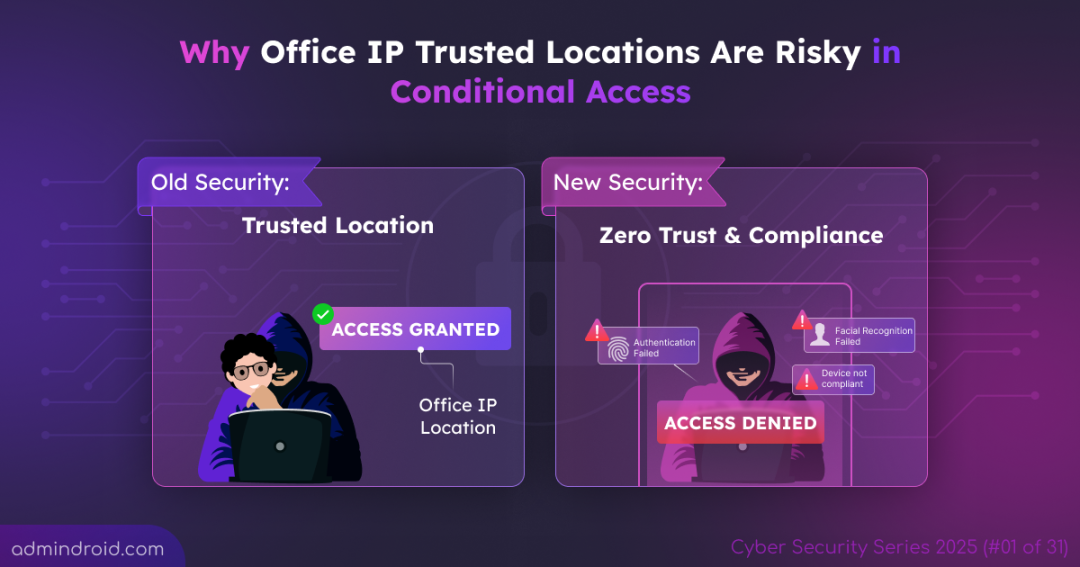
Day 1 begins with one of the most overlooked yet dangerous missteps in Conditional Access – Setting your Office’s IP address as a “Trusted Location.” Sounds convenient? Sure. Safe? Absolutely not. Every choice you make in Microsoft 365 either strengthens your defenses or creates a gap that attackers can exploit.
Many admins configure the trusted IPs feature in Conditional Access to skip MFA for anyone logging in from the office network. While convenient, trusted IP bypass can backfire. Today’s blog unpacks the hidden danger behind this practice and how to fix it with smarter controls.
The Right Way to Think About Security
Location ≠ Trust 💯
What is a Trusted Location in Microsoft Entra ID?
A trusted location is a security concept where certain physical locations (like your office) or network environments are designated as “safe” and given relaxed security requirements.
You can generally add your office IP as a named location by navigating to Microsoft Entra admin center –> Conditional Access -> Manage -> Named locations -> IP ranges location and then mark it as trusted.
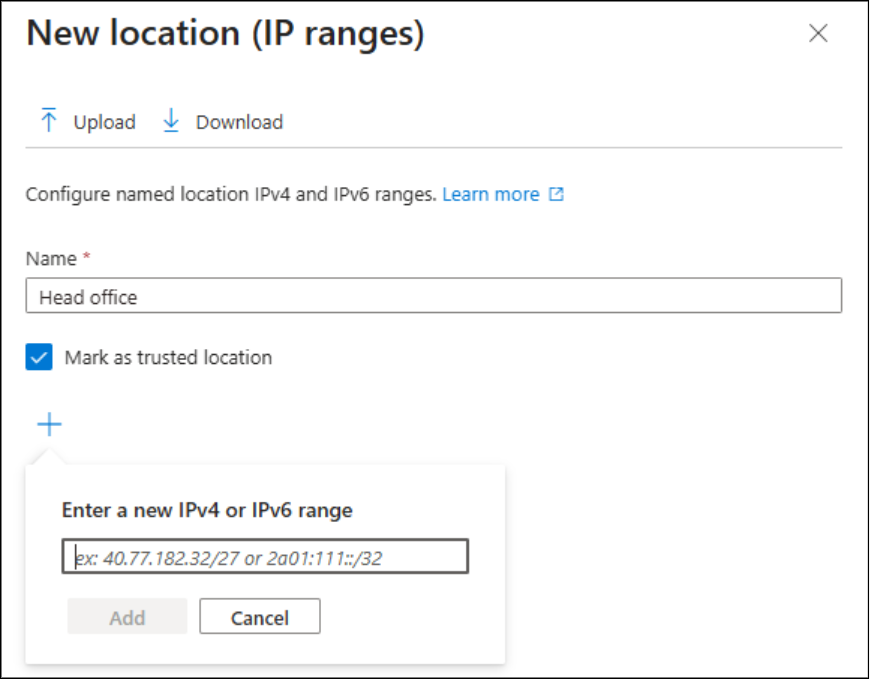
Afterward, create a policy named “Bypass MFA for Trusted Office IPs” and include all trusted networks in the Network configuration.
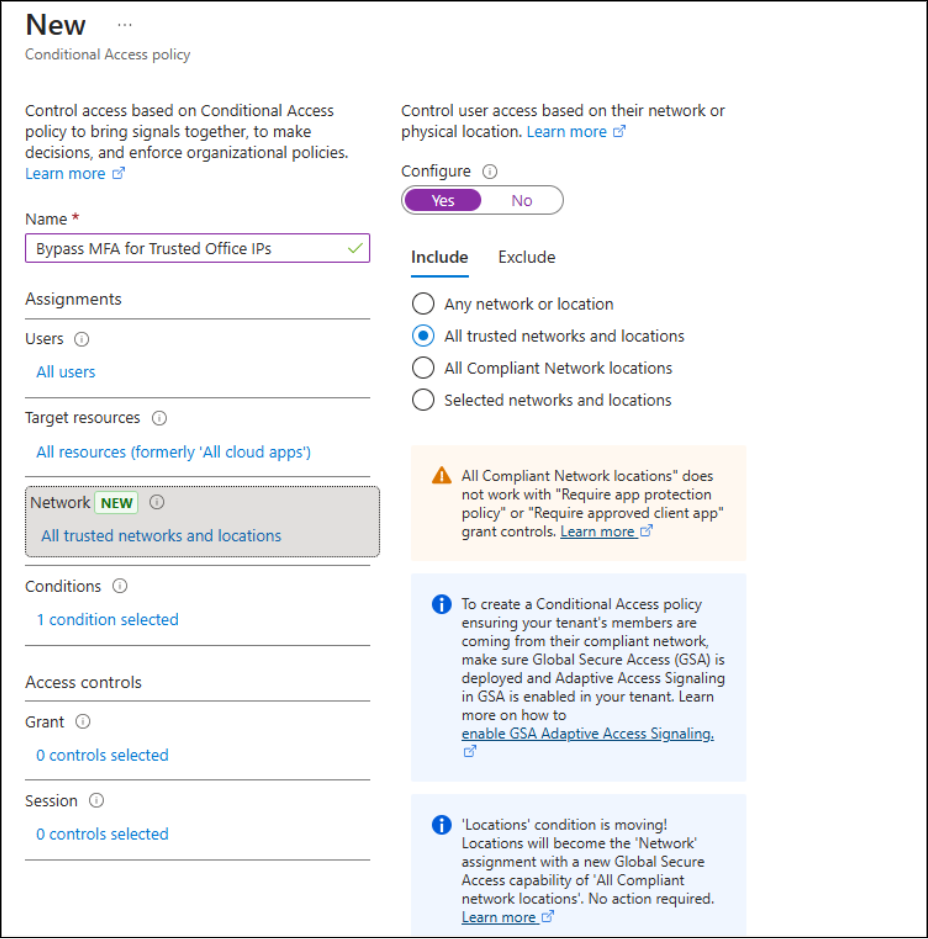
It seems convenient… until you realize the risk. Once the CA policy is active, all users connecting from those trusted IPs automatically skip multifactor authentication. On the surface, it looks like smooth access for employees, but behind the scenes, security loopholes emerge.
The Risks of Using Office IP as Trusted Locations in Conditional Access
Using the location condition in Conditional Access for access control creates risks such as:
- Inherited Trust: If an attacker gains access to your office network, they inherit the same “trusted” status, allowing them to sign in without additional verification.
- Weakened Entra ID Risk Detection: Microsoft Entra ID Protection lowers a sign-in’s risk score when it comes from a trusted location. An attacker using that IP might appear low-risk and avoid triggering suspicious-sign-in alerts.
- Phishing Attacks: If these IPs are shared with untrusted networks or exist on a compromised system, attackers could exploit this and make phishing attacks easier to succeed.
- Network Sharing: Public IP addresses are often shared by multiple devices. This means an IP-based policy could accidentally grant access to unintended users or devices, even if the policy was meant only for your internal network.
- Limited Scope with VPNs and Remote Access: If your organization uses Remote Desktop, Virtual Private Networks, or other tools that route traffic through a single location, the IP-based policy can be bypassed. All traffic may appear to come from the trusted office IP, even if it originates elsewhere.
- Public Wi-Fi Risks: Users connecting via public Wi-Fi may appear as coming from the trusted network if the connection is routed through your office IP, creating a false sense of security.
- Insider Threats: Employees or contractors with access to your office network can exploit MFA Trusted IPs to access sensitive resources without additional verification.
- Zero Trust Misalignment: By trusting the network instead of verifying the device or user, you’re essentially trusting the location, not the identity, which goes against modern zero-trust principles.
At this point, convenience comes at a cost. Users may access resources easily, but your organization’s security posture is now exposed.
What Organizations Should Do Instead: Zero Trust + Device Compliance
Instead of relying on trusted IPs, organizations should adopt Zero Trust principles. Here’s how you can put that into practice:
1. Stop Bypassing MFA for Office Networks
Assuming office IPs are inherently safe exposes your organization to potential attacks. To strengthen security, focus on the following actions:
- Require MFA for all users, everywhere, with no exceptions.
- Use modern methods like the Microsoft Authenticator app to make MFA seamless.
- Implement phishing-resistant MFA to protect accounts from advanced credential attacks.
2. Set Up Device Compliance Policies
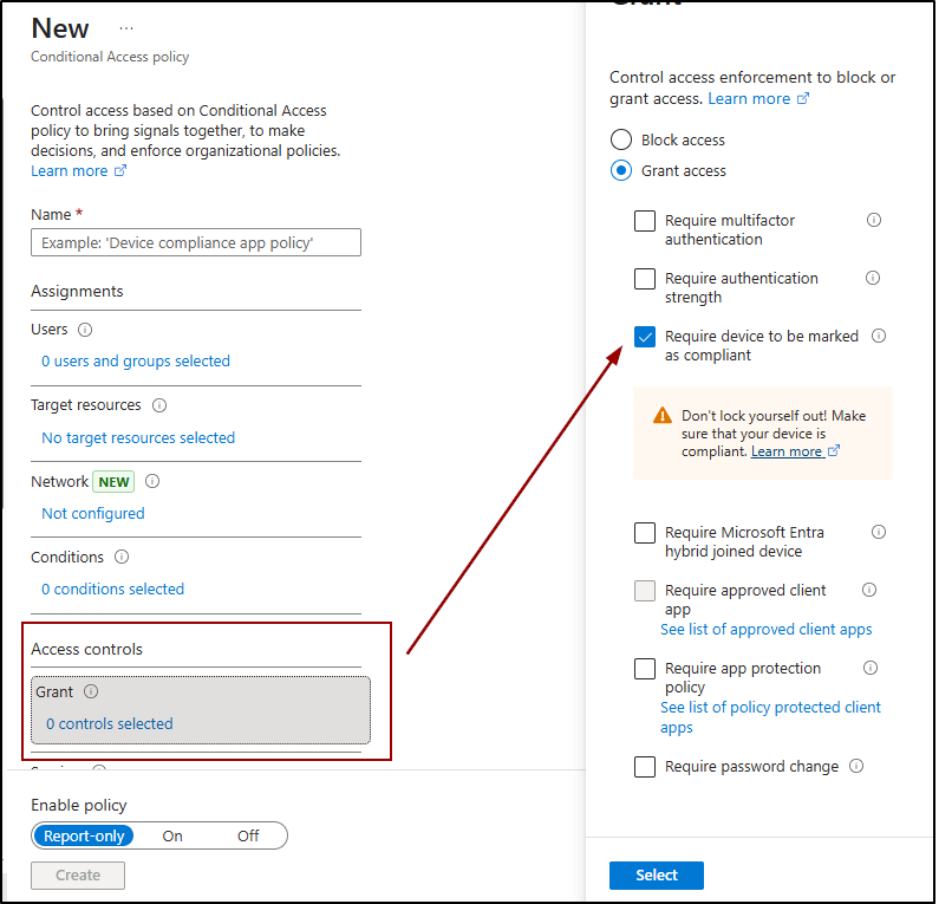
After you create device compliance policies in Microsoft Intune and define requirements such as encryption, OS version, and security settings, Intune evaluates each registered device against these rules. It then reports the device’s compliance status back to Entra ID.
You can then tie this compliance status directly into Conditional Access policies. For example, when creating a CA policy, simply enable the access control “Require device to be marked as compliant”. Once the policy is active, access is granted only to devices that meet your organization’s compliance standards.
You can also strengthen security by exploring other device-based Conditional Access policies that extend protection beyond basic compliance checks.
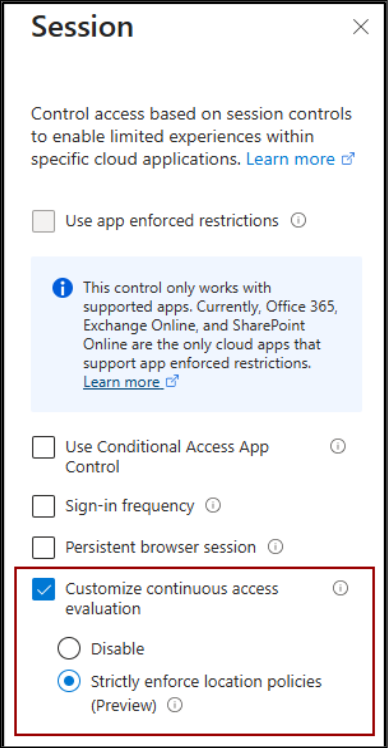
3. Continuous Access Evaluation for Real-Time Access Control
IP-based trusted locations rely on static network boundaries, which can be risky. Continuous Access Evaluation (CAE) provides a dynamic, real-time alternative. CAE lets Entra ID and client apps revoke access tokens immediately when a user’s risk changes, their location shifts, or their account is disabled. This means access is blocked instantly, without waiting for token expiration. This makes it a strong Zero Trust control instead of relying on trusted networks.
You can manage this setting when you create Conditional Access policies under Session controls, where CAE works alongside options like sign-in frequency to enforce real-time access.
4. Create Risk-Based Conditional Access Policies
IP restrictions can’t keep up with modern attack patterns. That’s why risk-based Conditional Access policies in Entra ID are a smarter approach. These policies use signals like impossible travel, unfamiliar locations, or anonymizer usage to detect risky sign-ins in real time. If a login looks suspicious, access can be blocked instantly or additional verification can be required — regardless of where the login originates.
5. Block Access from Unmanaged Devices
Unmanaged devices are often the easiest entry point for attackers to access corporate data. To reduce this risk, organizations should restrict access to Microsoft 365 apps from devices that aren’t managed or compliant. Conditional Access policies allow you to block access to all apps or selectively limit access to sensitive resources like SharePoint Online and OneDrive.
6. Enable Passwordless Authentication
Passwordless authentication reduces reliance on passwords by using modern methods like Windows Hello and FIDO2 security keys. This approach, combined with careful Conditional Access policies, can also reduce reliance on IP-based trusted locations.
So, if you’ve marked your office IPs as trusted in Conditional Access and used them to skip MFA, it’s time to rethink.
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
– Stephane Nappo
Start your cybersecurity journey this month by removing office IPs from MFA exclusions and embracing a Zero Trust approach. It might add a few more MFA prompts, but it closes one of the most dangerous gaps attackers love to exploit.
Hope this blog has provided insight into the hidden risks of using trusted office IPs in Conditional Access. Thanks for reading! We’re just getting started, stay tuned for more blogs packed with practical tips and strategies to help you stay ahead of threats.