“MFA for all users“- This is the mantra every Microsoft 365 admin should keep in mind nowadays! 💯With more brute force attacks happening, it’s scary how easily hackers can sneak into Microsoft 365 accounts. But you can stop it, making it twice as hard for cyber criminals to get in by configuring MFA in Microsoft 365. 😎
While you may have already set up MFA in Microsoft 365, it’s crucial not to overlook any users or critical applications. Every layer of security matters! But how can you ensure that all users and apps are protected?
Don’t worry! Admins can easily identify users with no MFA & apps without MFA requirements and more with the Entra workbook feature. Let’s see that in detail below.
What are Workbooks in Entra ID?
The Entra workbook is your gateway to an interactive, personalized dashboard showcasing Entra ID sign-in and audit logs. With a workbook, you can experience the convenience of accessing eye-catching charts and insightful reports, all consolidated into a single, user-friendly view.
Within this powerful feature, you’ll find a variety of pre-built workbook templates designed to streamline your analysis, including:
- Authentication Prompt Analysis Workbook
- Sign-in Failure Analysis Workbook
- Conditional Access Gap Analyzer Workbook
- Risk-based Access Policies Workbook
- Conditional Access Insights and Reporting Workbook
- Cross-tenant Access Activity Workbook, and more.
Among all, the one workbook that stands out as particularly invaluable for finding MFA weaknesses is the “Multifactor authentication gap workbook”. Let’s dive into it.
What is Multifactor Authentication Gaps Workbook in Microsoft 365?
The multifactor authentication gaps workbook in Entra ID helps you identify weaknesses in your MFA implementation within the organization. By analyzing data and providing insights, it shines a light on areas where your MFA implementation may fall short, helping you address any issues.
How does this workbook help you?
✅Identify sign-in gaps – It helps you pinpoint user sign-ins that aren’t protected by MFA requirements. By using Conditional Access logs from log analytics, the workbook helps you easily catch missed users and applications from MFA requirements.
✅ Drilled-down insights: It’s not just a broad overview. This workbook dives deep, giving you specific sections where you can spot sign-ins lacking MFA protection by applications, locations, and more. So, nothing slips through the cracks!
✅ Get specific details precisely: No need to sift through endless data; this workbook offers filters to tailor the information to your needs. Whether you want to focus on certain users or applications or even filter by trusted locations and device states, everything is possible!
How to Use Multifactor Authentication Gaps Workbook?
Unlike the other pre-built workbooks, the MFA gaps workbook is not currently shown on the “Workbook” page. You should import the workbook from the GitHub repository. Let’s see how to import the multifactor authentication gaps workbook now.
- Log in to the Microsoft Entra admin center.
- Navigate to the Monitoring & health section and select the “Workbooks” option.
- Now, click “+ New” and select the “Advanced Editor </>” button from the top of the page. A JSON editor opens once you click the above section.
- Now, open a new tab and navigate to the Microsoft Entra Github repository using this link.
- Now, select the “Application-Insights-Workbooks” link that appears at the top.
- Then, select the “Workbooks folder > Azure Active Directory > MultiFactor AuthenticationGaps ” folders. Now, open the .workbook file.
- Copy the JSON file from the Github repository.
- Now, return to the advanced editor and paste the copied JSON file by erasing the existing one.
- Click the “Apply” button, and the insights will be populated.
- Select the “Save as” button and provide the necessary details like Title, Subscription, and Resource Group.
- Finally, select the “Apply” button. The insights will automatically get populated within a few minutes.
Let’s explore the insightful sections of the multifactor authentication gaps workbook.
1. Summary of User Sign-ins in Microsoft 365
This section provides a clear overview of user sign-ins in Microsoft 365, highlighting the count of users protected/not protected by second-factor authentication (MFA). Here’s a breakdown of what each tile signifies:
- All Sign-ins: This indicates the total number of sign-ins recorded in Microsoft 365 during the selected period.
- Protected by MFA: This represents the count of sign-ins that successfully passed through MFA requirements.
- Non-protected by MFA: Here, you’ll find the total number of user sign-ins that did not undergo MFA.
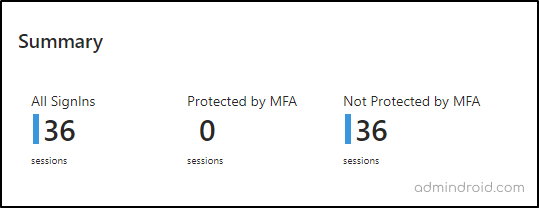
By comparing these metrics, you can gain valuable insights into the overall security posture of your Microsoft 365 organization. You can also have various filters like time range, users, trusted locations, apps, and more to narrow down your insights. Once applied, these filters will be applied through all the sections of the workbook. But you can tweak the workbook to add section-based filters in workbooks.
2. Sign-ins Not Protected by MFA Classified by Applications
This section is the breakdown of user signs that are not protected by MFA classified by applications. Here are the detailed insights.
✅Number of Users Without MFA Classified by Application:
This section will give you all the applications and respective sign-in counts that lack MFA. From this, you can easily identify the apps frequently accessed by users as well as users/apps not protected by MFA.
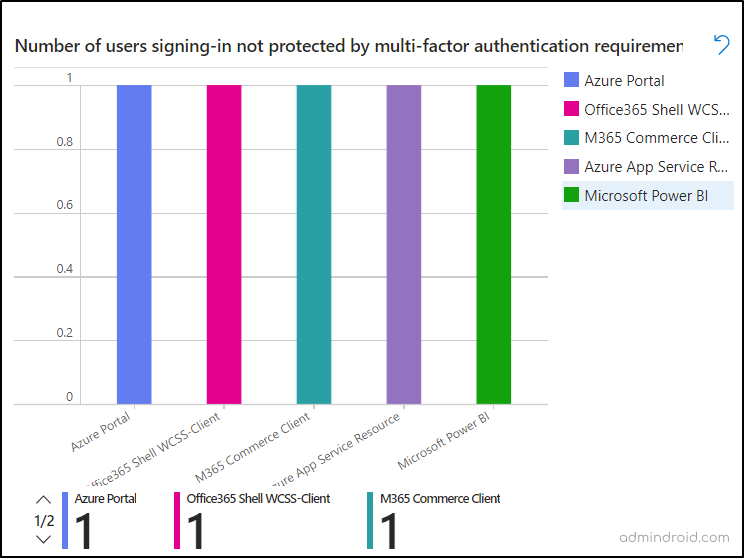
After analyzing the report, all you need is to configure a Conditional Access policy including all apps and users requiring MFA.
The adjacent section is same as the above, but it will give the users sign-ins to apps with no MFA insights in percentage for quick understanding.
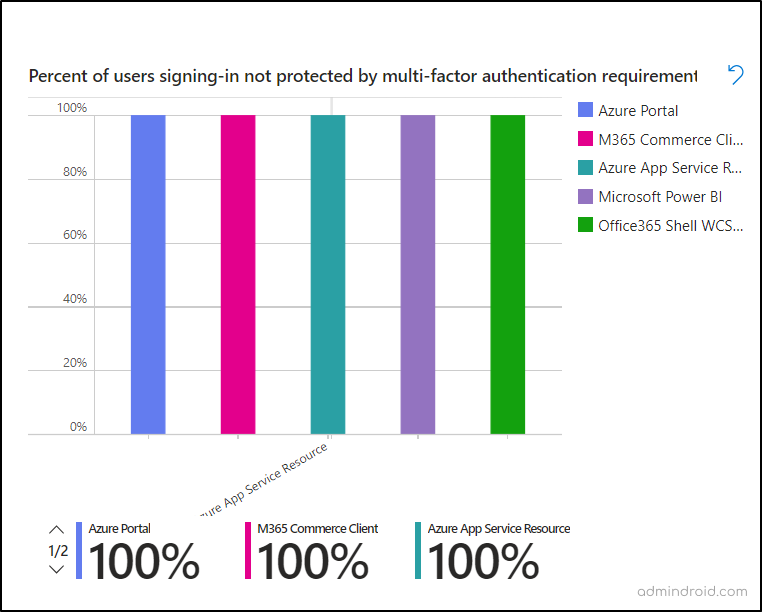
✅ Find Users and Applications Without MFA in Microsoft 365:
This section provides insight into applications and the users signing in to the apps without any (MFA) restrictions. By displaying this data, admins can easily identify users who are accessing critical applications without MFA protection. This visibility enables swift action to rectify MFA gaps by including these users in a Conditional Access policy that mandates MFA authentication.
3. Identify Users Without MFA in Microsoft 365
The above section will give insights on accounts without MFA based on the applications. In this section, you will clearly understand the users without MFA alone.
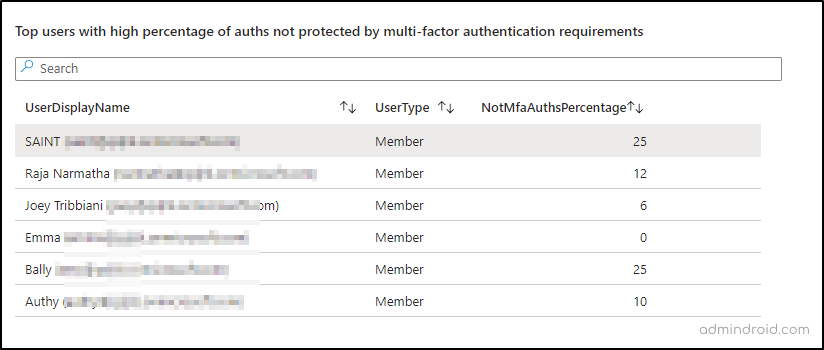
✅Report on Users with No MFA: This section highlights the top 10,000 users who have attempted sign-ins without MFA protection. Alongside their display names, you’ll see the number of sign-in attempts in Microsoft 365 with no MFA requirements. This will help you monitor risky sign-in users in Microsoft 365. Added to that, you can also get to know the users who don’t have MFA enabled in Entra ID.
✅ Top 10 users with a high percentage of authentications not protected by MFA: Here, you can get a report of the top 10 users who often log in without using MFA. This information empowers administrators to create a targeted Conditional Access policy to require MFA for these users. You can also disable MFA for specific Azure AD users found in the list if they are expected one.
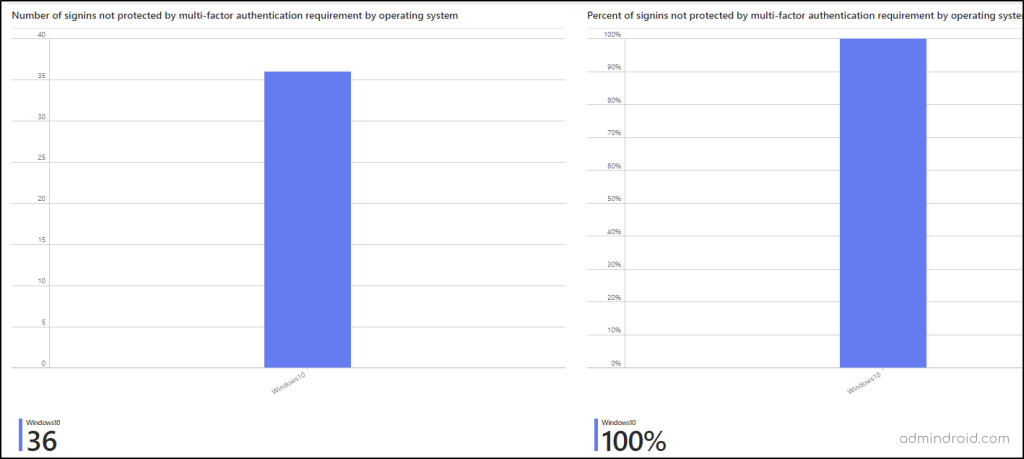
4. Sign-ins Not Protected by MFA by Operating System and Location
This section presents data on sign-ins without MFA protection, segmented by the operating system used.
- By identifying the top operating systems through which users sign in without MFA, administrators can tailor Conditional Access policies to mandate MFA for users accessing via specific operating systems. Also, it helps you identify sign-ins from older OS that are not compatible with MFA.
- The adjacent section offers the same insights but in percentage format, facilitating easy comprehension.
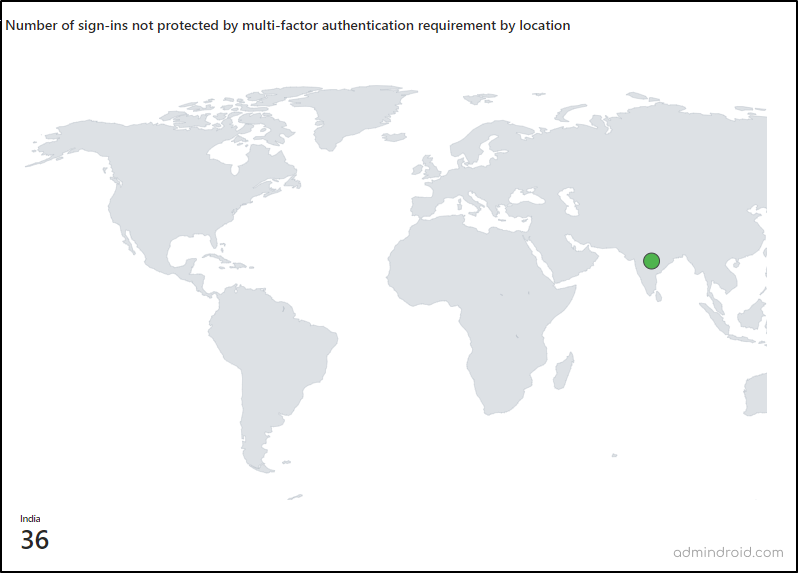
- In the next section, you can classify the sign-ins with no MFA requirement by location. So, you can easily include named locations in the Conditional Access policy and require MFA for users from such locations.
Edit or Create a New Workbook in Entra ID
If you are not satisfied with the insights given by this built-in workbook or need specific details alone from the workbook, don’t worry! You have the flexibility to customize /edit the Entra workbook as needed.
In addition, you can create a new Entra workbook with the MFA insights you need easily. To achieve it, Microsoft offers five main components: text, parameter, query, group, and links. You can use this to add explanatory texts, navigation links (jump links), group similar insights for better viewing, and more to make a personalized workbook.
To help you do it, I have used the Query component to get a sign-in count of specific applications without any MFA requirements.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
SigninLogs | where ResultType == 0 // Filter to sign-ins that are successful. No interrupts | where AADTenantId == ResourceTenantId // Filter out cross tenant resource access. | where array_length(ConditionalAccessPolicies) != 0 //bootstrap | where '*' in ({Users}) or UserDisplayName in ({Users}) | where ("{FilterDQ}" == "Yes" and ResourceIdentity !in ("00000002-0000-0000-c000-000000000000", "00000003-0000-0000-c000-000000000000")) or ("{FilterDQ}" != "Yes") | where AppDisplayName == "Azure Portal" | where '*' in ({DeviceState}) or case(DeviceDetail["trustType"] == "", "Unmanaged", DeviceDetail["trustType"]) in ({DeviceState}) | where ("{FilterLegacy}" == "Only Legacy Authentications" and (ClientAppUsed != "Browser" and ClientAppUsed != "Mobile Apps and Desktop clients")) or ("{FilterLegacy}" != "Only Legacy Authentications") | where ("{TrustedLocation}" == "Only Trusted Locations" and NetworkLocationDetails contains "trustedNamedLocation") or ("{TrustedLocation}" != "Only Trusted Locations") | extend UserDisplayName = strcat(UserDisplayName, " (", UserPrincipalName, ")") | project UserDisplayName, UserType, AppDisplayName, AuthenticationRequirement | where AuthenticationRequirement == "singleFactorAuthentication" | summarize NotMfaCount=count() by AppDisplayName, UserDisplayName, UserType | order by NotMfaCount desc |
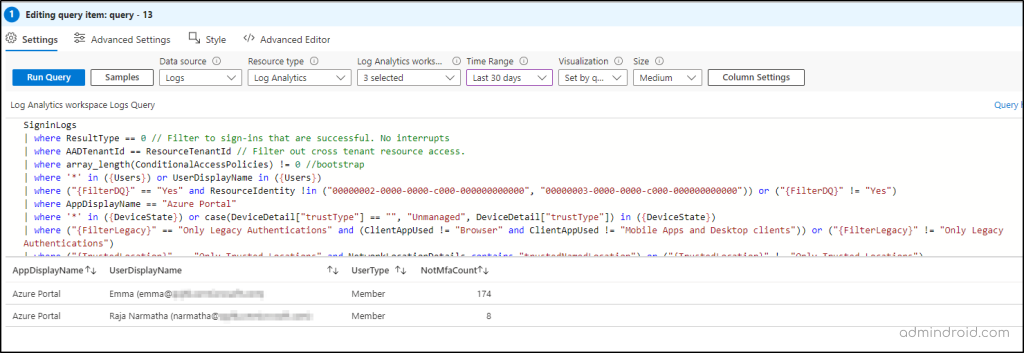
Like above, you can also create your Kusto query and get desired MFA insights like list of Office 365 accounts without MFA and more.
No More MFA Loophole in Microsoft 365!
A single crack in MFA can lead to a huge security risk in Microsoft 365! So, without any delay, jump to this workbook in your organization and spot missed users and apps from the MFA safety net! After spotting, get the MFA status report using PowerShell and check if MFA is enabled/disabled for those users. If MFA is disabled for Azure AD users, make sure to set it up! Once done, proceed to include them in CA policies and make sure all Azure users are required MFA.
I hope you have gained a clear view of the MFA gap workbook. Furthermore, feel free to contact us in the comment section for more assistance needed.






