On Day 22 of Cybersecurity Awareness Month, learn how comparing Active Directory and Microsoft 365 security features can help you strengthen access management, enforce security policies, and protect your organization’s critical resources. Stay tuned for upcoming blogs in the Cybersecurity blog series.
In most modern organizations, hybrid environments have become the norm. While many still depend on traditional on-premises servers managed by Active Directory (AD), they also increasingly use cloud services like Microsoft 365, secured by Microsoft Entra ID. This dual reality often leads to confusion and critically, security gaps. This blog helps you explore Active Directory vs Microsoft 365 security features by breaking down their essential native capabilities, enabling you to build a cohesive, modern security strategy.
Understanding Active Directory and Microsoft Entra ID
Before comparing features, it’s important to get a complete understanding of Active Directory and Microsoft Entra, as their architecture directly influences their security capabilities.
Active Directory Domain Services (ADDS): It is the on-premises directory service that has supported enterprise IT for decades. It is a domain-focused, boundary-based security system designed to manage and secure access to resources within the corporate network, such as file servers, printers, domain-joined computers, and legacy applications.
Microsoft Entra ID: It is the cloud-native Identity and Access Management (IAM) platform behind Microsoft 365, is fundamentally identity-focused and built for modern, remote-first work environments. It allows organizations to manage and secure user access to resources from anywhere and on any device, including services like Exchange Online, SharePoint, Teams, and a wide range of third-party SaaS applications.
Comparing Features of Active Directory and Microsoft Entra ID
The two platforms have fundamentally different architectures, which leads to distinct features. While AD focuses on on-premises domain security, Microsoft Entra ID provides cloud-scale protection based on a Zero Trust model. Although both offer numerous capabilities, the following highlights some of the most important key features and how they differ.
- Identity lifecycle management
- External identity provisioning
- Credential management
- Identity protection for high-privileged accounts
- Threat detection
- Entitlement management and groups
- Authentication strength
- Access control policies
- Privilege access management
- Device management
1. Identity Lifecycle Management
This feature covers the automated process of provisioning, maintaining, and de-provisioning user accounts across the environment.
In Active Directory: User provisioning is a manual, script-driven, or third-party process. New accounts are created manually in the Active Directory Users and Computers snap-in (ADUC), via PowerShell scripts, or using Microsoft Identity Manager (MIM). A standout feature of Active Directory is its native account expiry date. This built-in control lets admins automatically deactivate accounts at a set date and time, ideal for managing temporary user accounts.
In Microsoft Entra ID: Identity lifecycle management is native, and automation driven. Entra ID offers HR-driven provisioning to automatically create, update, and de-provision user accounts based on employee status changes in systems like Workday or SuccessFactors. It also uses lifecycle workflows to automate tasks like sending temporary passwords or assigning access packages based on a user’s joiner, mover, or leaver status, greatly enhancing security and efficiency.
2. External Identity Provisioning
This feature addresses how organizations manage access for users outside their corporate boundaries.
In Active Directory: Provisioning external identities involves creating a guest account within the corporate forest or establishing an AD Federation Services (AD FS) trust. While this allows external users to access corporate resources, they are typically managed using the same policies as internal users. Admins can utilize account expiration dates to automatically deactivate external accounts after a predefined period, reducing the risk of stale accounts.
In Microsoft Entra ID: External identity provisioning is native, secure, and policy-driven via Microsoft Entra External ID (B2B/B2C). Users can authenticate using their own identity providers, eliminating the need for you to manage their credentials. Admins can use Entitlement Management to set up automated, time-limited access for guests that requires approval and expires automatically. This process is simplified through onboarding external users via an access package, ensuring secure and governed collaboration.
3. Credential Management
This covers the security and administrative features related to user passwords and other secret forms of authentication.
In Active Directory: Credential management is limited to on-premises policies. Password policies are enforced via GPOs. Self-Service Password Reset (SSPR) requires deploying Active Directory Federation Services (AD FS). Password hash protection relies on the domain controller’s hierarchy, and as a result, can be vulnerable to lateral movement attacks if a controller is compromised.
Additionally, Active Directory includes Managed Service Accounts (MSAs), which automate password management for service accounts. This removes the need for manual credential handling by enabling automatic password rotation and reduces the risk of hard-coded or stale passwords used by services and scheduled tasks.
Active Directory also offers fine-grained password policies, which allow admins precise control over password and account lockout settings for different users or groups. These policies let enforcing stronger rules for high-privileged accounts such as longer passwords, complexity requirements or password expiration cycles.
In Microsoft Entra ID: Credential management is cloud-native, enhanced, and proactive. SSPR is a native feature, reducing help desk calls. Entra ID Password Protection blocks known weak passwords and custom banned passwords before they can be set. Microsoft Entra connect also supports advanced password management features like Password Hash Sync (PHS), which protects against hybrid identity breaches by storing separate, cryptographically protected credentials in the cloud.
In addition to password-based authentication, Entra ID supports app authentication methods such as client secrets and certificate-based authentication, giving flexible options for securing non-interactive service access. Instead of relying on static credentials, Entra ID provides Managed Identities for Azure resources, the cloud equivalent of MSAs in Active Directory. Managed Identities eliminate stored passwords by issuing short-lived access tokens automatically, enabling secure, passwordless, and scalable machine-to-machine authentication without manual credential rotation.
4. Identity Protection for High-Privileged Accounts
This feature focuses on protecting high-privilege or sensitive accounts from compromise and limiting the impact of attacks within the environment.
In Active Directory:
Windows Server leverages several features to protect privileged accounts:
- Protected Users group: Prevents credential theft by enforcing stronger authentication protocols and limiting exposure to legacy authentication.
- Account Lockout Policies: Automatically lock accounts after repeated failed login attempts.
- Authentication Policies and Silos: Restrict where and how high-privilege accounts can authenticate, reducing the risk of compromise.
- Read-Only Domain Controllers (RODCs): Provide a secure, read-only copy of AD for remote locations, limiting exposure of sensitive credentials.
- Tiered Administrative Model: Segregates administrative accounts into tiers (Tier 0, 1, 2) to minimize risk if a privileged account is compromised.
- Secure Administrative Hosts (SAHs): Dedicated workstations for performing sensitive administrative tasks, preventing malware or credential theft on regular endpoints.
- Logon Hours: Restrict when users are allowed to sign in, reducing the risk of off-hour unauthorized access.
- Logon To / Workstation Restrictions: Limit which computers a user can log on to, minimizing the potential attack surface for compromised accounts.
In Microsoft Entra ID:
Identity Protection continuously monitors accounts for risky sign-ins, leaked credentials, and atypical behaviours. Admins can configure risk-based Conditional Access policies, require MFA, and enforce risk-based remediation to protect high-value accounts. Integration with Privileged Identity Management (PIM) ensures just-in-time access and time-bound assignments for administrative roles, further reducing exposure.
Additional security features include:
- Security Defaults: Provides baseline protection for all users, including mandatory MFA for admin accounts and blocking legacy authentication.
- Entra ID Smart Lockout: Protects accounts from brute-force attacks by intelligently locking out suspicious login attempts.
- Privileged Access Workstations (PAWs) for Cloud Admins: Ensures that sensitive admin tasks are performed on secure, hardened endpoints to reduce compromise risk.
- Entitlement Management: Automates access reviews and lifecycle management for privileged accounts, ensuring no stale or excessive privileges remain.
5. Threat Detection
This feature focuses on identifying suspicious activities, attacks, and anomalous behaviours targeting user accounts and the environment in real-time.
In Active Directory: Threat detection in Active Directory relies heavily on local Event Logs. It provides detailed records of authentication attempts, account changes, and other critical activities. These logs are essential for monitoring, auditing, and investigating suspicious behaviours.
For detecting advanced attacks such as Golden Ticket, DC Sync, or lateral movement, admins can use Event Logs, but they must manually map the events. Microsoft Defender for Identity (MDI) enhances AD threat detection by analysing authentication and network traffic from both on-premises AD and cloud identities. It enables real-time identification, investigation, and alerting for sophisticated threats across a hybrid environment.
In Microsoft Entra ID: Threat detection is proactive and intelligence-driven. It leverages Microsoft’s Global Threat Intelligence to detect risks like atypical travel, leaked credentials, and password spray attacks. It continuously evaluates sign-ins and account activity, providing alerts for potential compromise. Admins can mitigate detected risks by configuring risk-based Conditional Access policies, such as enforcing MFA or blocking access, to ensure a quick response to threats. Integration with Microsoft Defender XDR allows organizations to correlate cloud and on-premises activity, providing a unified view of threats across the hybrid environment.
6. Entitlement Management and Groups
This feature defines how access rights are requested, granted, reviewed, and revoked using group membership and role assignments.
In Active Directory: Active Directory provides fine-grained control through Security Groups. It allow admins to define access at the organizational unit (OU) or resource level. Its nested group structure enables complex hierarchies that can precisely mirror business or departmental roles. Although access assignments are largely manual, this design gives organizations direct visibility and administrative authority over every group and membership. Features like Group Policy Objects (GPOs) and Access Control Lists (ACLs) extend this control beyond identity. It influences system configuration and security policies across the network. However, because it relies on static groups, maintaining the Principle of Least Privilege requires periodic review often through manual audits or third-party tools.
In Microsoft Entra ID: Entitlement Management provides self-service access packages. Users can request access, which triggers an automated approval workflow. Critically, it enables access reviews and time-based access expiration, ensuring that access is always granted for a necessary period and automatically removed later. Dynamic groups automatically manage their membership based on user attributes, dramatically reducing administrative overhead and access sprawl.
Group SOA Conversion allows legacy AD security groups to shift authority to the cloud. This enables the groups to leverage the same governance capabilities such as access requests, approval workflows, and time-bound access even for on-premises resources.
7. Authentication Strength
The primary difference here is the fundamental shift from relying solely on a single factor – a password to mandating multiple factors or adopting passwordless authentication.
In Active Directory: Active Directory offer robust authentication through well-established protocols like Kerberos and ADLP, backed by customizable password policies (length, complexity, expiration, and history). It also allows users to log on with smart cards and supports certificate-based authentication, which organizations often require in highly regulated or air-gapped environments.
In Microsoft Entra ID: It integrates Multi-Factor Authentication (MFA) and passwordless sign-in options (Windows Hello for Business, FIDO2 keys, Authenticator app) as native capabilities. These features align with Zero Trust principles, continuously verifying identity and device health. This approach significantly reduces risks from password spray, phishing, and credential theft, especially in hybrid and remote access scenarios.
8. Access Management Policies
This highlights the shift from a network-centric security model to a user and context-centric model.
In Active Directory: Group Policy Objects (GPOs) are built-in to Active Directory. It offers very deep, granular control over practically every aspect of devices. Through GPOs, admins can configure password policies, firewall rules, registry settings, software deployment, drive mappings, scripts, application restrictions, security templates, and much more. This level of control is applied automatically when domain-joined devices contact a domain controller, which is especially powerful in tightly controlled on-premises environments. Because GPOs are native, organizations need no additional licenses to enforce device configuration settings on domain-joined machines.
In Microsoft Entra ID: By itself, Entra ID does not provide device configuration policies like GPOs. Instead, admins handle access enforcement via Conditional Access, which evaluates context dynamically, including user, location, device health, and other factors. In Microsoft Entra ID environments, administrators typically handle this through a device management solution like Microsoft Intune (Endpoint Manager). Intune applies configuration profiles, compliance policies, and CSP settings to manage devices.
9. Privilege Management
A major security best practice is minimizing “standing” administrative access, and the two platforms handle this differently.
In Active Directory: Admins typically assign administrative permissions through built-in groups such as Domain Admins, Enterprise Admins, and Schema Admins. These groups offer full or delegated control within the domain and are central to on-premises management. Secure deployments closely monitor and protect these groups because their membership grants “standing” privileges.
Optional features like Privileged Access Management (PAM), allow organizations to implement time-based group memberships. This approach supports a “Just-In-Time” model, and therefore, providing temporary administrative access, helping maintain operational control without compromising security.
In Microsoft Entra ID: Microsoft Entra ID uses role-based access control (RBAC) and Privileged Identity Management (PIM) to manage elevated access in cloud environments. Admin roles remain assigned, but the role is inactive until they explicitly request permissions. Activation can include MFA verification, approval workflows, and time-based expiration, ensuring accountability and reducing unnecessary standing privileges. All activations are logged and auditable, enabling organizations to track when and why elevated permissions were used.
10. Device Management
Securing the device a user is coming from is critical, especially outside the corporate network.
In Active Directory: Devices that are domain-joined to AD are centrally managed using Group Policy Objects (GPOs) and Security Templates, allowing administrators to enforce a wide range of settings. This only works for internal Windows machines and doesn’t support modern mobile devices or Macs without third-party tools. It supports Network Access Protection (NAP) and Network Policy Server (NPS) integrations, which can assess device health before granting network access. For organizations that operate primarily on-premises, this offers a stable and deeply integrated management model that aligns closely with Windows infrastructure.
In Microsoft Entra ID: Entra ID provides device management through integration with Microsoft Intune. Intune evaluates a device’s compliance state such as encryption status, OS version, and threat protection and shares that information with Conditional Access. Consequently, Entra ID can allow, block, or restrict access to cloud applications and data. This model supports Windows, macOS, iOS, and Android devices, providing unified visibility and control in hybrid and remote work scenarios.
Key Differences Between On-Premises Active Directory and Azure Active Directory
| Feature | Active Directory (AD) | Microsoft Entra ID |
| Authentication Protocols | It facilitates SSO within Windows environments, allowing users to access multiple applications after a single authentication. This is achieved through Kerberos and NTLM protocols. | It provides cloud-based SSO, enabling users to access thousands of SaaS applications using their credentials. This is achieved through protocols like SAML, OAuth, and OpenID Connect. |
| Directory Access | Uses LDAP (Lightweight Directory Access Protocol) for querying and modifications. | Uses REST-based API (Microsoft Graph) and PowerShell for querying and modifications. |
| Multi-Factor Authentication (MFA) | Not natively supported. Requires third-party solutions or integration with AD FS. | Supports per-user MFA, security defaults, and Conditional Access policies for risk-based enforcement. |
| Conditional Access | Not available. | Rules that grant or deny access to resources based on conditions such as user, location, device, and risk level. |
| Access Management | Utilizes Role-Based Access Control (RBAC) and Organizational Units (OUs) for managing access to resources within a domain. | Employs Microsoft Entra ID for identity and access management, supporting Conditional Access policies and integration with various applications. |
| Domain Services | Supports DNS, DHCP, NPS, Wi-Fi, and VPN for on-prem users. | No traditional network services, focuses on cloud identity management. |
| External Collaboration | External collaboration is possible via dedicated accounts; careful configuration minimizes exposure and ensures access is limited to necessary resources. | B2B collaboration allows external users to use their own credentials safely, with explicit permissions and auditing to maintain security. |
| Access Control for Privileged Users | Implement Secure Administrative Hosts. | Supports granular access control via PIM. |
| Infrastructure Role Ownership | AD uses FSMO roles to designate specific domain controllers for authoritative actions. This prevents conflicting changes, ensures replication integrity, and limits potential abuse. | Not applicable, no FSMO infrastructure roles. |
| Administrative Role Ownership | Uses built-in groups and delegated permissions for admin tasks. | RBAC assigns users to specific admin roles for delegated access. |
| Self-Service Password Reset | Limited, requires manual setup (e.g., AD FS), or relies on third-party tools (Premium license not required). | Built-in feature with Multi-Factor Authentication (MFA) support and optional password write-back (requires licensing). |
Benefits of On-Premises Active Directory
- Full control over identity infrastructure: Organizations retain complete control over their identity infrastructure; consequently, they can implement customized security policies and access controls tailored to specific needs
- Offline authentication capabilities: Users can authenticate and access resources even without an internet connection, ensuring business continuity during network disruptions.
- Customizable group policies: It utilizes Group Policy Objects (GPOs) to enforce detailed security settings and configurations across the network; additionally, this offers granular control over user and computer settings.
- Traditional security protocols: Supports traditional security protocols like Kerberos and LDAP, providing robust authentication mechanisms within the local network.
Advantages of Microsoft Entra ID
- Enhanced security features: Provides advanced security capabilities such as Multi-Factor Authentication (MFA), Conditional Access policies, and Identity Protection to safeguard against unauthorized access.
- Seamless integration with SaaS applications: It facilitates Single Sign-On (SSO) and moreover, automated provisioning for a wide range of Software-as-a-Service (SaaS) applications, streamlining user access across platforms.
- Log in from anywhere: Users can securely sign in from any device, anywhere in the world, to access cloud services like Microsoft 365.
- Simplified identity governance: Enables automated access requests, assignments, and reviews, enhancing compliance and reducing administrative overhead through integrated identity governance tools.
Best Practices for Managing Hybrid Identity Environment
- Centralize and simplify user identity: Synchronize your on-premises AD with Entra ID using the Microsoft Entra Connect tool. It uses PHS to ensure that users only need one password for both local resources and cloud apps like Microsoft 365.
- Protect high-value accounts: Do not synchronize highly privileged on-premises accounts like Enterprise Admins, Domain Admins to Microsoft Entra ID; instead, keep them strictly on-premises to limit the attack surface.
- Protect your sync server: Strictly limit who can log in; additionally, apply the toughest security measures, such as a dedicated, isolated machine and mandatory MFA for its administrators.
- Just-Enough-Administration (JEA): Grant administrative access only when needed, for a limited time, and with required approval and justification. This significantly shrinks the window of opportunity for attackers to use compromised privileged accounts.
- Emergency access accounts: Define and secure “break glass accounts” that are excluded from Conditional Access policies and PIM. These are for disaster recovery scenarios when normal administrative paths are unavailable.
- Block legacy authentication: Completely disable legacy authentication protocols like POP3, IMAP, older versions of NTLM as they cannot enforce MFA and are common targets for credential stuffing attacks.
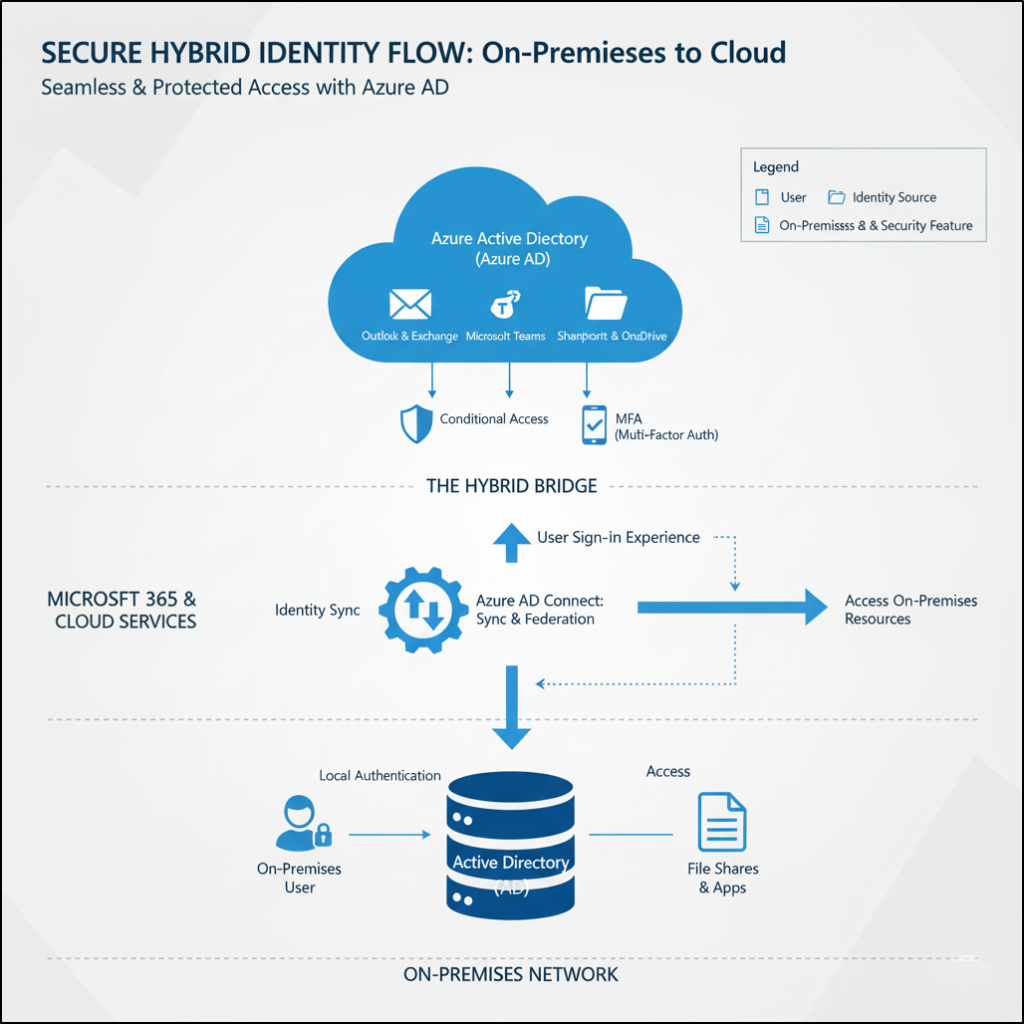
Managing a hybrid Active Directory and Microsoft 365 environment requires careful planning, consistent security policies, and proper access management to ensure both on-premises and cloud resources are protected. I hope this blog has clarified the key differences of Active Directory vs Microsoft 365 security features and best practices for a seamless hybrid identity setup. If you have any queries or need further guidance, feel free to leave a comment below.






