By default, all users can join devices to Microsoft Entra ID. This poses significant risks, such as unauthorized access from private computers. Therefore, managing these device settings is crucial to safeguarding sensitive data and maintaining network security. That’s why Microsoft Entra ID provides a central place to manage device identities and monitor related event information. By configuring these settings, admins can control how devices are registered and joined with Microsoft Entra ID, mitigating the risks associated with unmanaged devices. This blog will delve into how admins can manage device identity settings in Entra ID.
Who can Manage Device Identity Settings in Entra?
To manage device settings in Azure AD, you must be assigned the following roles:
- Cloud Device administrator
- Intune administrator
- Windows 365 administrator
How to Manage Device Identity Settings in Entra ID?
To manage device identity settings in Entra ID, admins can follow these steps:
- Sign in to the Microsoft Entra admin center.
- Navigate to Devices –> All devices under the Identity tab.
- Click on Device settings under Manage.
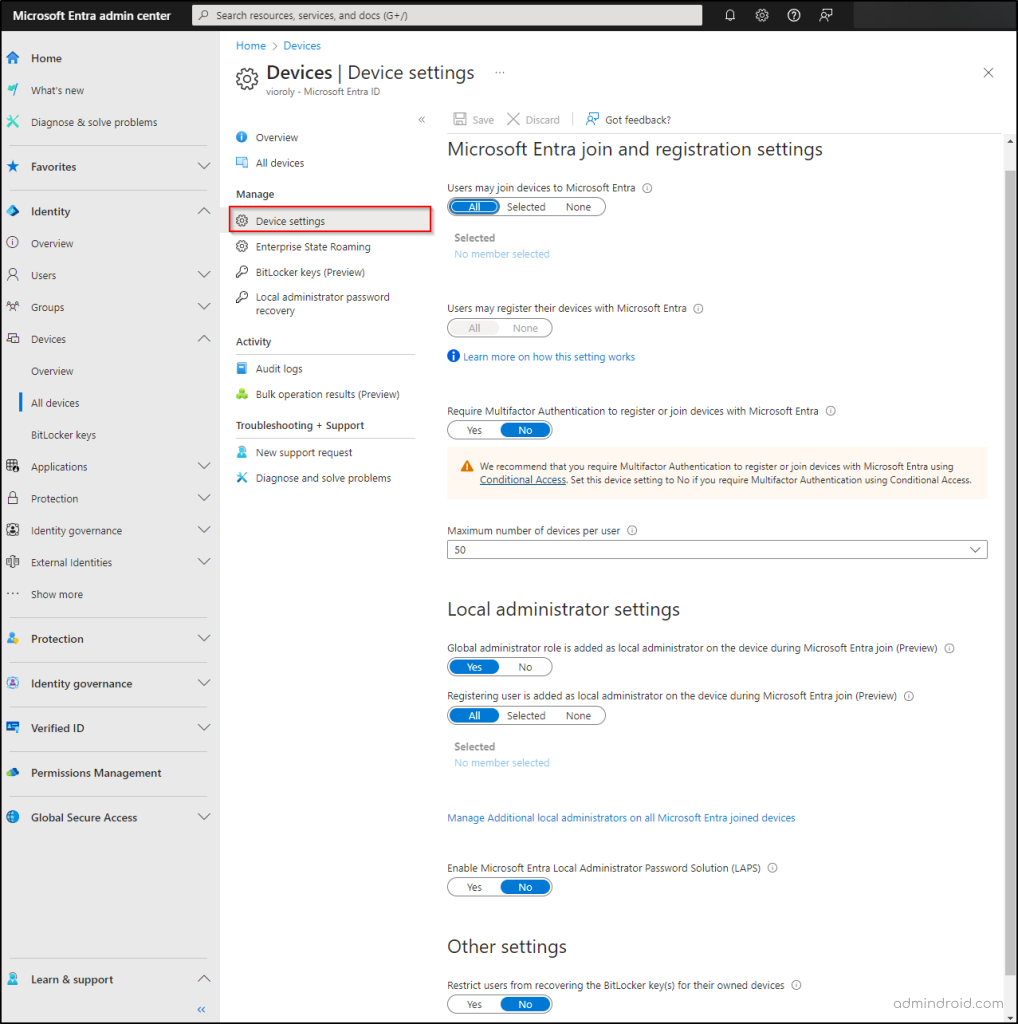
Manage Microsoft Entra ID Device Settings
Under device settings in Microsoft Entra ID, admins can manage the following configurations:
- How to allow users to join and register devices in Microsoft Entra?
- Require MFA for device configuration in Entra ID
- Microsoft Entra device limit restriction
1. How to Allow Users to Join and Register Devices in Microsoft Entra?
Users may join devices to Microsoft Entra ID: By default, all users can join devices to Microsoft Entra. This can end up as a security risk as it allows unauthorized devices to potentially access the organization’s resources. With this setting, admins can restrict this permission to specific users or groups, thereby blocking unmanaged device access.
Users may register their devices with Microsoft Entra ID: To allow users to register personal Windows 10+ devices, iOS, Android, and macOS devices, you need to configure the Microsoft Entra registration setting. If you select None, devices aren’t allowed to register with Microsoft Entra ID.
Note – Device registration setting applies only to Microsoft Entra join on Windows 10 or later, not hybrid joined devices, Azure VMs, or Windows Autopilot self-deployment mode. Enrollment with Microsoft Intune or mobile device management automatically selects “ALL” and disables “NONE”.
2. Require MFA for Device Registration in Entra ID
Require multifactor authentication to register or join devices with Microsoft Entra ID: By default, enrolling devices in Microsoft Entra ID doesn’t require multi-factor authentication beyond a user’s password. This poses a security risk because a compromised password alone could grant access to a device and potentially sensitive data. To enhance security, admins can require MFA during device registration.
This enforces MFA during device enrollment, requiring users to provide a second verification factor beyond their password. MFA authentication methods could be an authentication app, a security key, or a verification code sent to their phone.
MFA registration applies to most of the Entra joined and registered devices (with some exceptions). It doesn’t affect hybrid joined devices, Entra joined VMs in Azure, or Entra joined devices using Windows Autopilot self-deployment mode. Apart from MFA, admins can also create device-based Conditional Access policies to ensure only authorized devices can access sensitive data.
Important Note – If you require Multifactor Authentication using Conditional Access, set the device setting “Require MFA to register or join devices with Azure AD” to No. This ensures Conditional Access policies control MFA enforcement during device registration.
3. Microsoft Entra Device Limit Restriction
Maximum number of devices per user: Admins can define the maximum number of Microsoft Entra joined or registered devices a user can have. Users exceeding this limit cannot add more devices unless existing ones are removed. The default limit is 50, expandable to 100. You can also choose “Unlimited” to remove the limit (subject to existing quotas).
Note – This setting applies to Microsoft Entra joined and registered devices. This isn’t applicable to Microsoft Entra hybrid joined devices or devices enrolled through:
- Android Enterprise dedicated device
- Windows automatic enrollment with bulk device enrollment
- Windows automatic enrollment with group policy
Manage Local Administrator Settings on MS Entra Joined Devices
The way your organization manages local administrators on devices joined to Microsoft Entra plays a critical role in your overall device security posture. Local administrators have extensive privileges on a device registered in the organization. An attacker gaining local admin access can cause serious damage, installing malware, stealing data, or disrupting operations. By carefully managing local admins, admins can significantly reduce the attack surface in Microsoft 365.
Let’s explore the settings administrators can manage for local administrators in MS Entra.
- Add global administrator as local administrator
- Register user as local administrator
- Manage additional local administrators
- Enable Windows LAPS in Microsoft Entra ID
- Restrict BitLocker recovery key access
1. Add Global Administrator as Local Administrator
Global administrator role is added as local administrator on the device during Microsoft Entra join (Preview): This preview feature allows administrators to determine whether the global administrator role is automatically added as a local administrator on a device when it joins Microsoft Entra.
Enabling this feature can simplify device management and ensure that global administrators have the necessary permissions to perform administrative tasks on the device. However, it also introduces the risk of elevated privileges being misused, which could lead to security vulnerabilities. By default, this feature is not enabled.
2. Register User as Local Administrator
Registering user is added as local administrator on the device during Microsoft Entra join (Preview): This setting controls whether the user who registers the device is automatically added as a local administrator on the device when it joins Azure AD. You can choose to give this specific capability for all the users, selected users, or no users. This setting applies only once during the actual registration of the device as Microsoft Entra join.
Note – Generally, choosing “No” can enhance security by limiting the number of users with administrative privileges right from the device registration stage. This approach reduces the potential attack surface and ensures that administrative access is carefully controlled and granted only when necessary. It’s important to consider specific organizational needs and user roles when deciding to implement this feature.
3. Manage Additional Local Administrators
Manage Additional local administrators on Microsoft Entra joined devices: To manage a Windows device, you must be a member of the local administrators group. Here, admins can choose which users can be local admins on a device. These users are added to the Device Administrator role within Microsoft Entra ID. This capability allows designated users to perform administrative tasks locally on their own devices, enhancing their ability to manage and customize their work environment as needed.
4. Enable Windows LAPS in Microsoft Entra ID
Enable Microsoft Entra Local Administrator Password Solution (LAPS) (Preview):
Local Administrator Password Solution (LAPS) is a Microsoft tool that enhances security by automatically generating unique, strong passwords for local administrator accounts, storing them securely in Active Directory.
The cloud version of LAPS enables storing and rotation of local admin passwords for both Microsoft Entra and Microsoft Entra hybrid join devices. So, enabling this setting is recommended.
5. Restrict BitLocker Recovery Key Access
Restricting users from recovering the BitLocker key(s) for their owned devices:
BitLocker keys are encryption keys used by Microsoft BitLocker Drive Encryption, a feature available in Windows operating systems. These keys are used to encrypt and decrypt data on disk volumes to protect them from unauthorized access.
This setting empowers admins to restrict self-service access to BitLocker keys for device owners, ensuring only authorized admins can recover them. By default, users without the “BitLocker read” permission cannot view or copy their BitLocker keys for their own devices. This setting requires Privileged Role Administrator permissions to update.
In conclusion, managing device identities through the Microsoft Entra admin center offers a centralized and secure approach for organizations of all sizes. By leveraging these settings, organizations can achieve a more secure and manageable device environment. Additionally, implement device-related Microsoft Secure Score recommendations to further enhance device security and improve your Microsoft Secure Score for devices.






