In today’s rapidly evolving digital landscape, cybersecurity remains a paramount concern for organizations striving to protect their sensitive data and secure their systems. As organizations face an increasing number of email threats, Microsoft Defender Portal emerges as a comprehensive solution by offering quarantine management features. 📧
Discover how the Microsoft Defender Portal allows organizations to take control of their quarantine experience and protect against emerging cyber risks as we uncover the latest advancements. Let’s explore the exciting updates that Microsoft has in store for us! 🚀
Latest Quarantine Management Features:
- Microsoft Defender for Office 365 allows submission of up to 100 Emails
- Enhanced Handling of Full Quarantine Storage and Zero Hour Auto Purge
- New Hard Experience in Quarantine Messages
- Hourly Options for Quarantine Notifications
- Addition of ‘Admin Action – File Type Block’ in Quarantine Reason Filters
- Messages quarantined based on file type will now be rejected with an NDR
- Quarantine Admin Role is a Must for Quarantine Operations
- Columns and Filters preference Saved for re-use in Quarantine Folders
- Quarantine Notifications Enabled for Preset Security Policies
- Migration of Quarantine Notification Frequencies
1. Microsoft Defender for Office 365 Allows Submission of Up to 100 Emails
Microsoft Defender for Office 365 is introducing a new feature that will make your email analysis process much easier. Soon, you will be able to submit up to 100 emails at once for analysis from quarantine, threat explorer, and User reported page to Microsoft. Since you can conveniently submit 100 emails at once, this change will save you time and effort for manual submissions at a greater rate. 📈
Note – This feature is applicable to the tenants using Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2, or the Microsoft 365 Defender plan.
📢 Rollout – The rollout of this update will begin in early May 2023 and will be completed by early June 2023.
2. Enhanced Handling of Full Quarantine Storage and Zero Hour Auto Purge
In situations where a user’s quarantine storage reaches its maximum capacity, any new incoming messages directed to that mailbox will be throttled, and an NDR (Non-Delivery Report) will be generated for those messages. However, when it comes to Zero Hour Auto Purge, malicious items that do not fit in the quarantine will be placed in the junk mail folder instead. This ensures that potential threats are still isolated, even if they are in a different location.
Note – In the event of a false positive during the Zero Hour Auto Purge, where messages are wrongly identified as malicious and moved to the junk mail folder, users have the option to easily restore these messages back to their original location.
📢 Rollout – This update will be rolled out starting in mid-June 2023 and will be complete by mid-November 2023.
3. New Hard Delete Experience in Quarantine Messages
Before, when users deleted messages from quarantine, the deleted messages could still be retrieved within 30 days. To help users manage storage more effectively, a new hard delete feature is going to be released. With the hard delete, once messages are deleted, they cannot be recovered. End users can delete quarantine messages only if their admins have granted them access through the quarantine policy. This restriction ensures that only authorized messages can be deleted from quarantine.
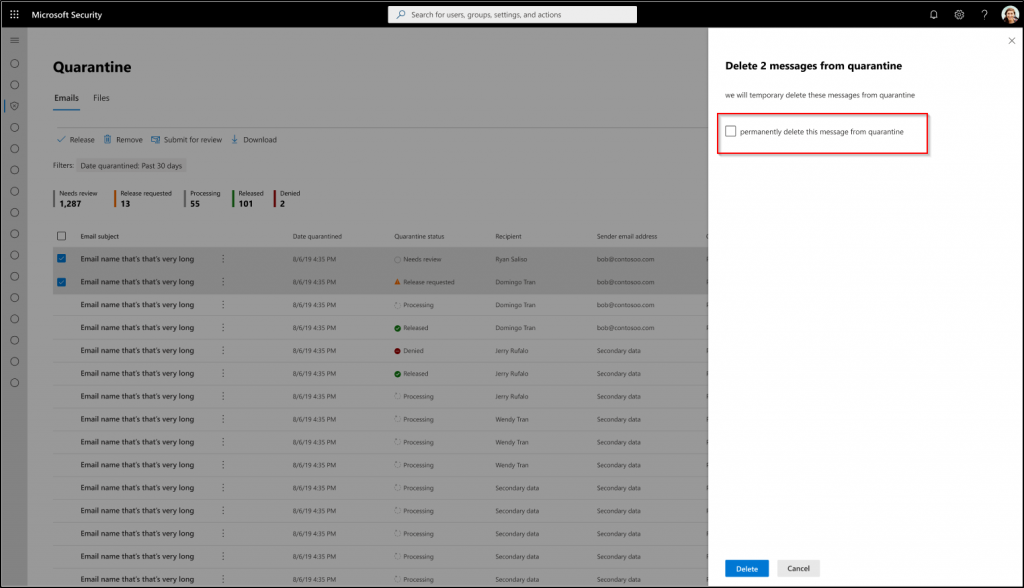
📢 Rollout – The rollout will begin in June and be complete by mid-November.
4. Hourly Options for Quarantine Notifications
To ensure users receive timely updates about quarantined items, a new option for end user quarantine notifications is coming soon. With this feature, users will be notified more frequently whenever new items arrive in their quarantine folder.

📢 Rollout – This enhancement will be rolled out gradually between late November 2022 and late June 2023.
5. Addition of ‘Admin Action – File Type Block’ in Quarantine Reason Filters
The Quarantine page includes a comprehensive list of all quarantined email messages, including those classified as malicious, spam, or subject to other admin actions. This led to confusion. In the anti-malware policy, there is an option to quarantine messages that have malicious attachments, such as malware or phishing files. Additionally, the policy allows the configuration of common attachment filters to quarantine messages with specific file extensions.
So, a new filter called ‘Admin Action – File Type Block’ to the Quarantine reason filter is going to be introduced. By applying this filter, admins/SecOps can easily identify and review email messages that were specifically quarantined by the common attachment filter due to their file type.
You can notice this change while using the Get-QuarantineMessage cmdlet. Specifically, the QuarantineTypes parameter will now include the AdminActionFileTypeBlock option.
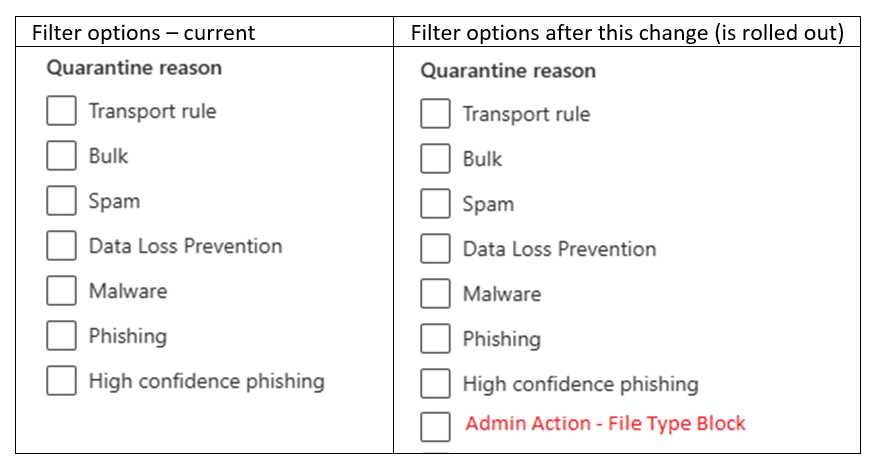
📢 Rollout – This rollout will begin in early June 2023 and expected to be completed by late-August 2023.
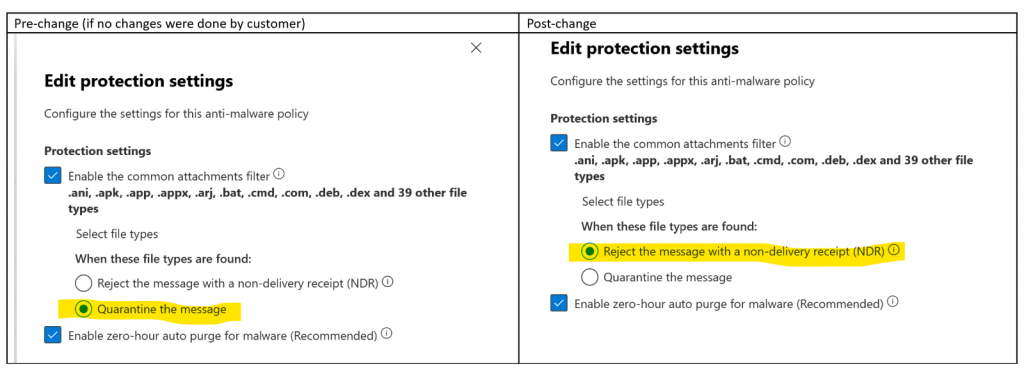
6. Messages quarantined based on file type will now be rejected with an NDR
In the future, any message that was quarantined because of the matching file type will be rejected by an NDR. Under the Anti-malware policy, the default policy had ‘Quarantine the message’ selected. However, it has been now updated to the ‘Reject the message with NDR’ option. This change allows senders to receive faster notifications and quickly resend important emails that may have been quarantined due to blocked file types.
7. Quarantine Admin Role is a Must for Quarantine Operations
Previously, Exchange Admins had the ability to perform various quarantine operations on behalf of users in their organization, such as releasing, deleting, downloading, and previewing quarantined messages. To further strengthen security measures and improve control, Exchange administrators will now be required to be assigned the Quarantine Administrator role in order to perform quarantine operations effectively.
📢 Rollout – This rollout will begin in early to late May 2023.
8. Columns and Filters preference Saved for re-use in Quarantine Folders
Soon, admins and end users will notice that the Customized Columns and Filters in Quarantine folders will persist even when they leave the interface and revisit it later. Previously, these settings would reset upon returning to the Quarantine folder.
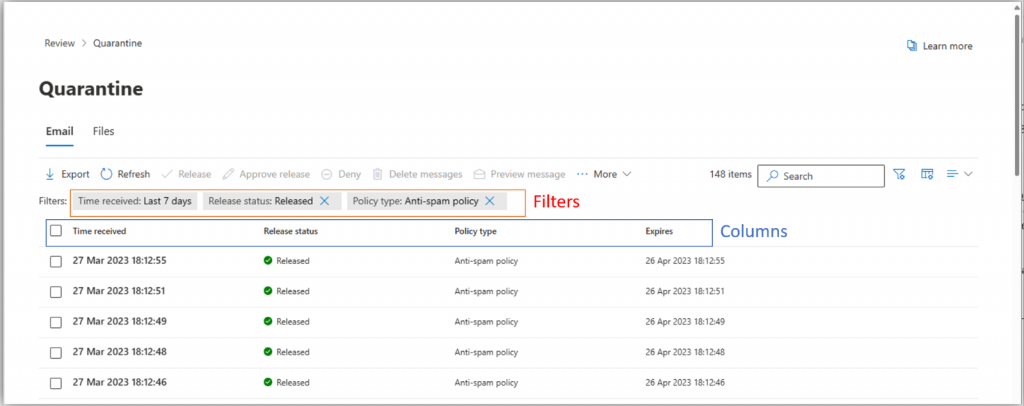
📢 Rollout – Rollout completed in late April 2023.
9. Quarantine Notifications Enabled for Preset Security Policies
Microsoft updated the quarantine notification policy in the Standard and Strict preset security policies. With the DefaultFullAccessWithNotificationPolicy, users will now receive quarantine notifications for emails that have been quarantined due to the corresponding threat policy.
If your organization has enabled preset security policies, these policies will be automatically updated to include the quarantine notification policies (DefaultFullAccessWithNotificationPolicy) as listed in the provided table for the standard and strict protection profiles.
Note – It is important to note that if the delivery location for the quarantined emails is set to the Junk folder, the assigned Quarantine policy will be ineffective. In other words, users will still receive notifications, but the emails will be delivered to the Junk folder instead of the designated quarantine location.
| Policy | Quarantine Policy | Standard | Strict |
| Anti-Spam | SpamQuarantineTag | DefaultFullAccessPolicy | DefaultFullAccessWithNotificationPolicy |
| Anti-Spam | HighConfidenceSpamQuarantineTag | DefaultFullAccessWithNotificationPolicy | DefaultFullAccessWithNotificationPolicy |
| Anti-Spam | PhishQuarantineTag | DefaultFullAccessWithNotificationPolicy | DefaultFullAccessWithNotificationPolicy |
| Anti-Spam | HighConfidencePhishQuarantineTag | AdminOnlyAccessPolicy | AdminOnlyAccessPolicy |
| Anti-Spam | BulkQuarantineTag | DefaultFullAccessPolicy | DefaultFullAccessPolicy |
| Anti-Phish | TargetedUserQuarantineTag | DefaultFullAccessWithNotificationPolicy | DefaultFullAccessWithNotificationPolicy |
| Anti-Phish | TargetedDomainQuarantineTag | DefaultFullAccessWithNotificationPolicy | DefaultFullAccessWithNotificationPolicy |
| Anti-Phish | MailboxIntelligenceQuarantineTag | DefaultFullAccessPolicy | DefaultFullAccessPolicy |
| Anti-malware | QuarantineTag | AdminOnlyAccessPolicy | AdminOnlyAccessPolicy |
| Safe Attachments | QuarantineTag | AdminOnlyAccessPolicy | AdminOnlyAccessPolicy |
📢 Rollout – Rollout was completed by Mid-April 2023.
10. Migration of Quarantine Notification Frequencies
Microsoft is updating the available frequency intervals for user quarantine notifications. Currently, admins can choose from intervals ranging from 1 day to 15 days, with 3 days being the default.
With the upcoming change, the new frequency intervals will be as follows:
- Within 4 hours
- Daily (new default)
- Weekly
To ensure a smooth transition, Microsoft will automatically migrate customers who currently have notification frequencies between 1 day and 7 days to the “Daily” interval. For customers with notification frequencies exceeding 7 days, the migration will be to the “Weekly” interval.
📢 Rollout – Rollout was completed in Last Feb 2023
| Features | Message Center ID | Road Map ID |
| 1. Microsoft Defender for Office 365 allows submission of up to 100 Emails | MC535260 | 115509 |
| 2. Enhanced Handling of Full Quarantine Storage and Zero Hour Auto Purge | MC383875 | 93302 |
| 3. New Hard Experience in Quarantine Messages | MC383875 | 93302 |
| 4. Hourly Options for Quarantine Notifications | MC383901 | 93304 |
| 5. Addition of ‘Admin Action – File Type Block’ in Quarantine Reason Filters | MC528356 | 117520 |
| 6. Messages quarantined based on file type will now be rejected with an NDR | MC544793 | |
| 7. Quarantine Admin Role is a Must for Quarantine Operations | MC447339 | |
| 8. Columns and Filters preference Saved for re-use in Quarantine Folders | MC542832 | |
| 9. Quarantine Notifications Enabled for Preset Security Policies | MC505088 | |
| 10. Migration of Quarantine Notification Frequencies | MC468486 | 93304 |
Exciting Quarantine Management Features That Are Made Generally Available
Find the existing features in Microsoft Defender for Office 365 that enhance the quarantine experience below.
- New quarantine policy to configure custom user request release permissions.
- Custom organization branding in quarantine notification.
- Admins/SecOps can choose to allow or prevent users from submitting messages to Microsoft for analysis.
- Streamlined release of bulk quarantine emails.
- Enhanced Quarantined Message Preview for Added Security against Threats.
- Shared mailbox delegates can triage quarantine folder items.
- Enhanced Priority Account Visibility in Quarantine Experience.
- Default End User Spam Notifications in User’s Mailbox Language Setting.
- Added partial string-matching functionality to the search function.
- Asynchronous approach of 1000 message bulk operation support in quarantine.
- Password protected download of quarantines messages.
I hope this blog has provided you with valuable insights into the latest updates in quarantine management within Microsoft Defender for Office 365. If you have further queries, please reach out to us through the comment section.






