On Day 25 of the cybersecurity awareness month, learn how to find and eliminate inactive users using access reviews in Microsoft Entra ID. Stay tuned for more blogs in the M365 Cybersecurity blog series.
In large organizations, managing user accounts can be a challenging task. When employees leave an organization, their user accounts are not promptly deleted. As a result, these accounts remain in the system, even though they are not actively being used by the former employees. These inactive accounts can pose security risks and consume resources, such as licenses, which is why it’s important to identify and address them. By doing so, admins can simultaneously free up licenses and save money for their organization. But, how to identify inactive users in Microsoft 365 environment?
Despite various other options available, Microsoft Entra ID Governance access reviews emerged as the most efficient way to manage inactive accounts. With this feature, organizations can identify accounts that have not been actively used to sign into Entra ID for up to 720 days.
The greatest threat to an organization is not its competition but its own inactivity.
– Steve Maraboli
In this blog, we will explore how to find and manage inactive user accounts in Microsoft Entra using access reviews! Let’s begin with the basics.
What are Inactive User Accounts in Microsoft 365?
Inactive user accounts are those no longer actively used to access an organization’s resources. The key identifier is a lack of recent sign-in activity, typically within 90-180 days. Inactive user accounts can persist for various reasons, including former employees, service accounts, and external users. Therefore, it’s crucial to periodically identify and remove inactive accounts in M365.
What are the Risks of Inactive Accounts?
Inactive accounts pose several security risks:
- Password Vulnerability: The passwords or credentials of inactive accounts may still be compromised if they are well-known.
- Lack of Multifactor Authentication: Inactive accounts are less likely to have MFA enabled, making them more vulnerable to unauthorized access.
- Bypassing Security Controls: Due to their inactivity, these accounts may go unnoticed even by advanced security controls that are in place.
Find Inactive Users Using Access Reviews in Microsoft Entra
Before going further, learning how to create access reviews in Microsoft Entra and its license requirements is mandatory! Once you have met the requirements, follow the steps below to set up an access review for inactive accounts.
- Select the Teams/Groups to Review in Microsoft Entra
- Configure the Review Stage, Reviewers, & Recurrances
- Set up additional settings in access reviews
- Create an Access Review to Find Inactive Users
Select the Teams/Groups to Review in Microsoft Entra
This section includes the steps involved in configuring access review parameters in the Microsoft Entra admin center.
- Sign into your Microsoft Entra account using the Identity Governance administrator credentials.
Navigate to Identity Governance –> Access reviews. - Click New access review.
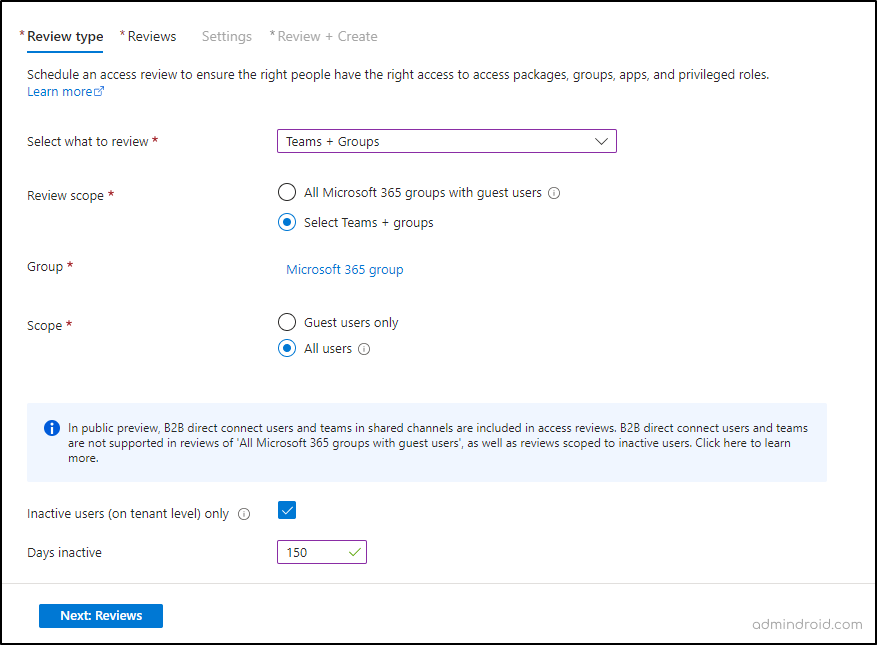
- In the “Select what to review” box, choose Teams + Groups.
- For the review scope, choose Select Teams + Groups.
- Under the section labeled + Select group(s), pick the group you want to include in the review from the provided list.
- Choose the scope for the review, which can be either Guest users only or All users.
- Select Inactive users (on tenant level) only and specify the number of days an account has been inactive (you can set this to a maximum of 720 days).
- Then, click Next: Reviews.
Note – If you encounter difficulties configuring the settings for inactive users, it indicates that the capabilities have transitioned to read-only mode. To regain access to these features, you will need to acquire a new Microsoft Entra ID Governance license.
Configure the Review Stage, Reviewers, & Recurrences in Identity Governance
In this section, you can specify the review stages and reviewers involved in access reviews.
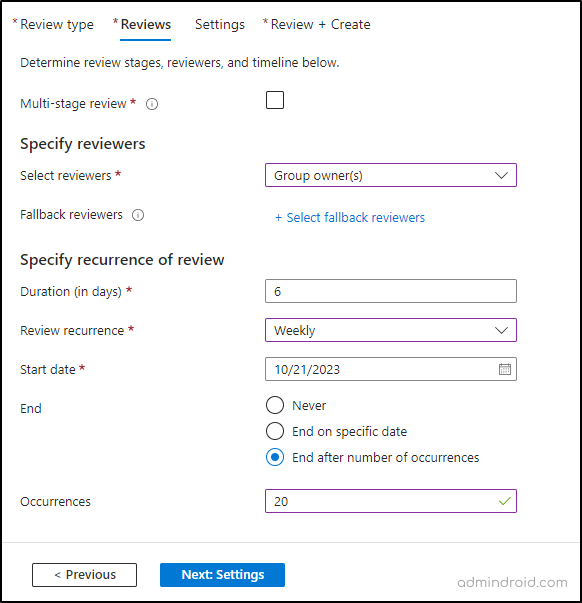
- You can choose either a single-stage or multi-stage review. Here, I am going with a single-stage review.
- In the “Specify reviewers” section, select one or more people to review. Reviewer options include group owners, selected users or groups, users reviewing their access, and managers of users.
- Now, you can specify a fallback reviewer for cases where there is no assigned manager or group owner.
- Following the reviewers, specify the review’s duration, start date, and end date.
- Click on Next: Settings.
Set Up Additional Settings in Access Reviews
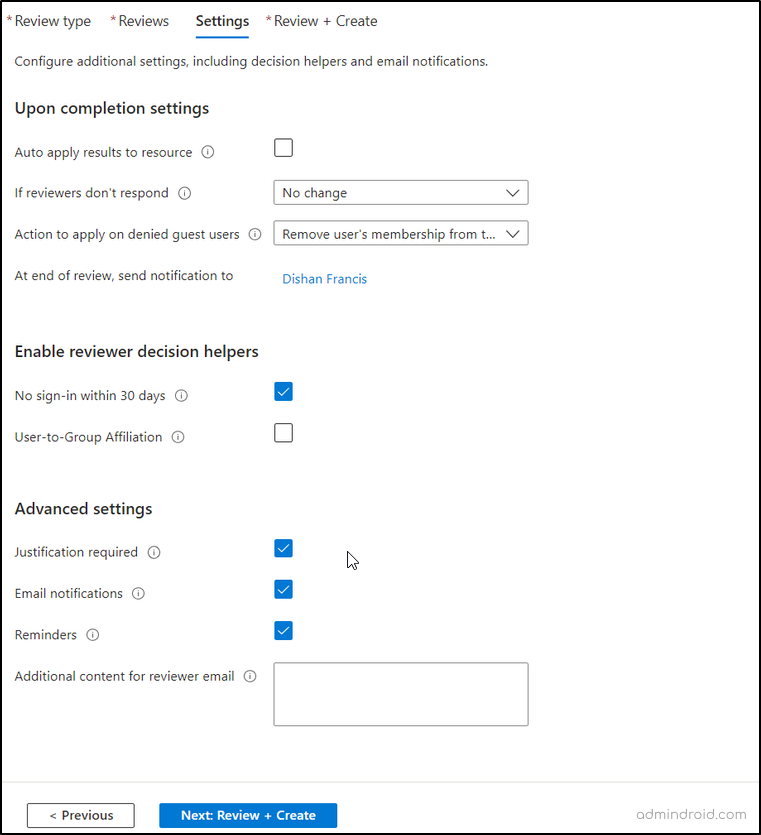
Here, you can specify the actions to be taken upon completing the review.
- You have the option to auto-apply the results or leave them for manual review.
- You can also utilize the ‘No sign-in within 30 days’ data for decision-making.
- After configuring these settings, click Next: Review + Create.
Create a Access Review to Identify Inactive Users
This is the final step of the process.
- On the last page, give the review task a name and a description.
- Then click Create to finalize the setup.
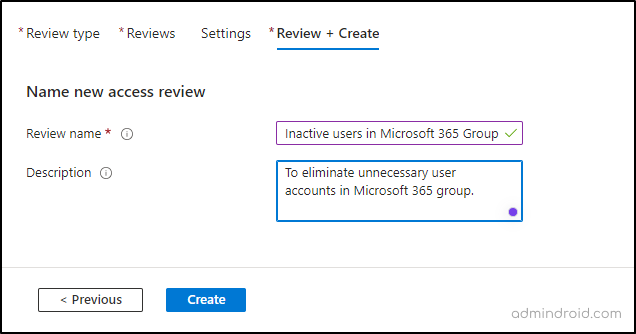
These steps should help you set up an access review in Entra’s Identity Governance system more effectively.
Examine the Access Review Result
The next step after conducting an access review is to thoroughly examine the results. After the review is complete, assigned reviewers will receive an email notification, making them aware of pending results.
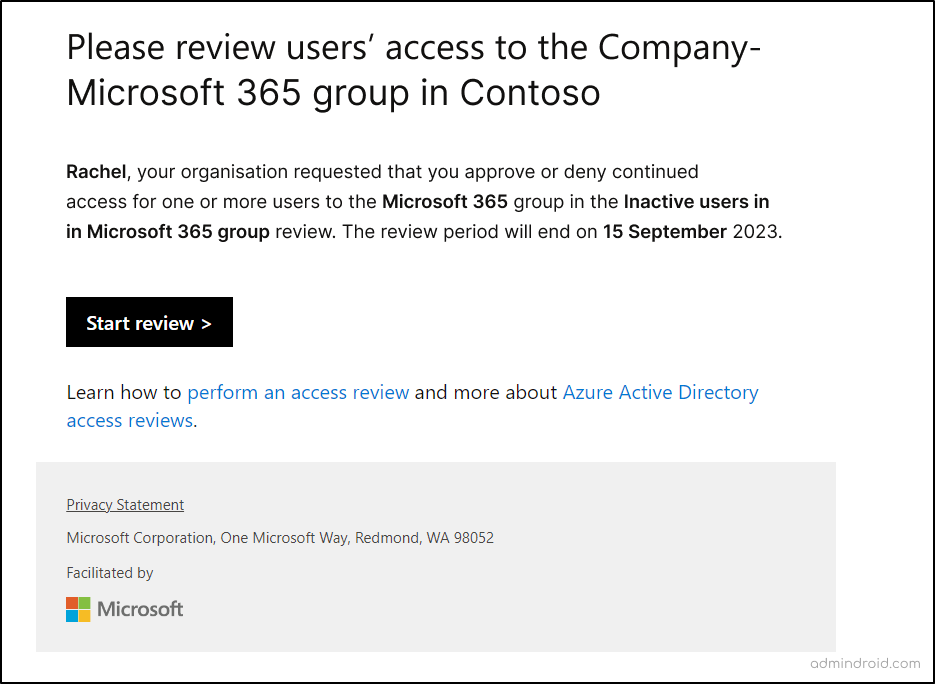
Once the results are available, reviewers can dive deeper into the specifics. Microsoft Entra ID Governance simplifies this by providing a clear interface that displays detailed information about the users and recommended actions. This transparency empowers your team to make informed decisions.
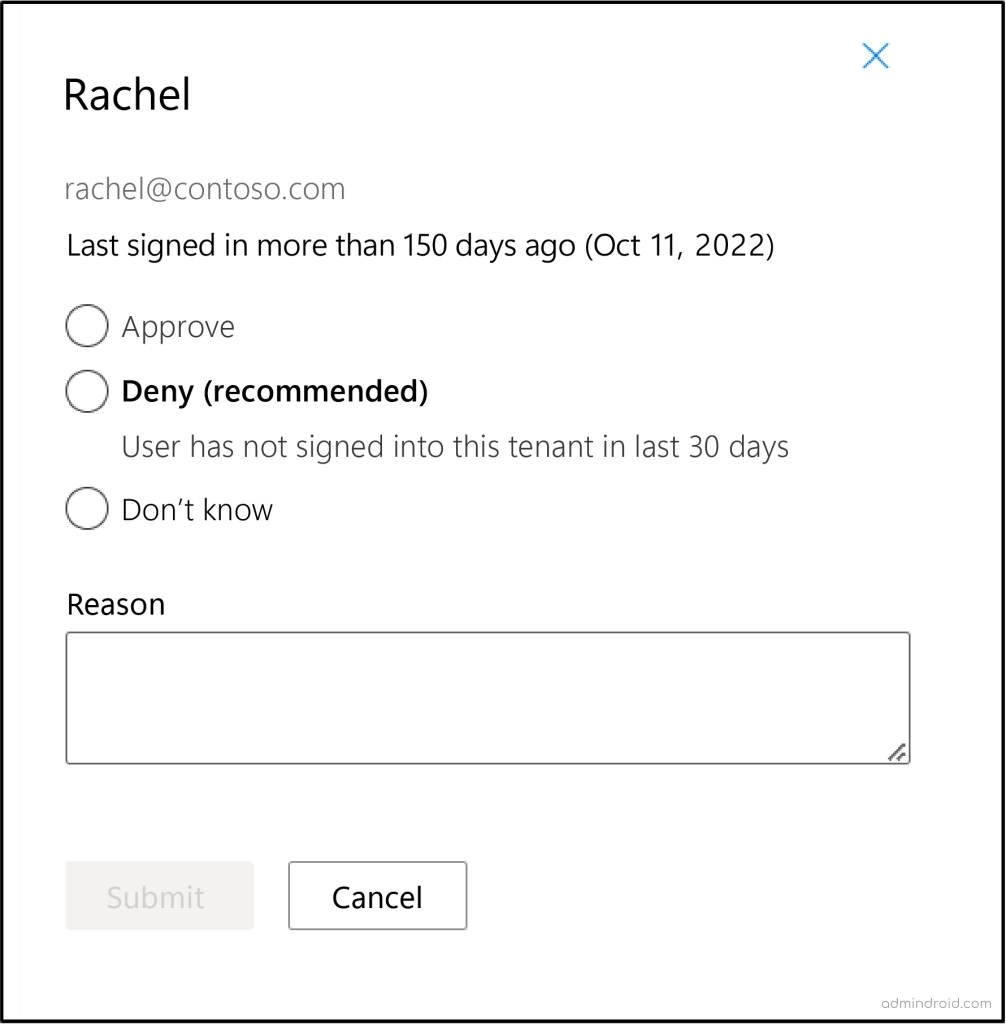
Review and Remove Inactive Users Based on Access Reviews
Based on the findings, reviewers have the option to approve or deny access to the identified accounts. This is a critical step in ensuring the security of your organization’s data. By using the information at their disposal, reviewers can confidently make these decisions.
Final Thoughts
In the ever-evolving landscape of cybersecurity, staying vigilant and proactive is essential. By regularly conducting access reviews and addressing inactive accounts, you not only enhance your organization’s security but also save valuable resources. We hope this blog has equipped you with the knowledge and tools needed to take control of inactive users and protect your organization’s data.