On Day 17 of Cybersecurity awareness month, gain insights into the importance of resetting MFA and discover a PowerShell script that makes the process easier. Stay tuned for more blogs in the M365 Cybersecurity blog series.
Microsoft recommends enabling MFA for all users to safeguard against potential breaches. To enhance security, administrators often migrate from per-user MFA to CA policy and implement stronger authentication methods.
However, there are times when MFA can create challenges, requiring administrators to reset it to restore access and ensure security.
When to Reset MFA for Microsoft 365 Users?
Resetting MFA methods is crucial in the following situations:
- When a user loses their MFA device: If a user loses their MFA device, they can’t access their Microsoft 365 account. In such situations, MFA reset is essential to reconfigure their authentication methods and regain account access.
- When removing less secure authentication methods: Administrators may identify certain authentication methods as insecure or outdated (SMS, Voice call, etc.). In such cases, removing less secure authentication methods via reset is necessary to enhance security.
- When an attacker registers an MFA method on a compromised account: If an attacker compromises an account and registers their own MFA method, it’s crucial to reset MFA to eliminate unauthorized access and restore control to the legitimate user.
How to Reset MFA for Microsoft 365 Users
You can choose any of the following methods based on your needs:
1. Reset MFA for Microsoft 365 Users Using Entra Admin Center
You can follow the below steps to reset MFA methods through Entra admin center.
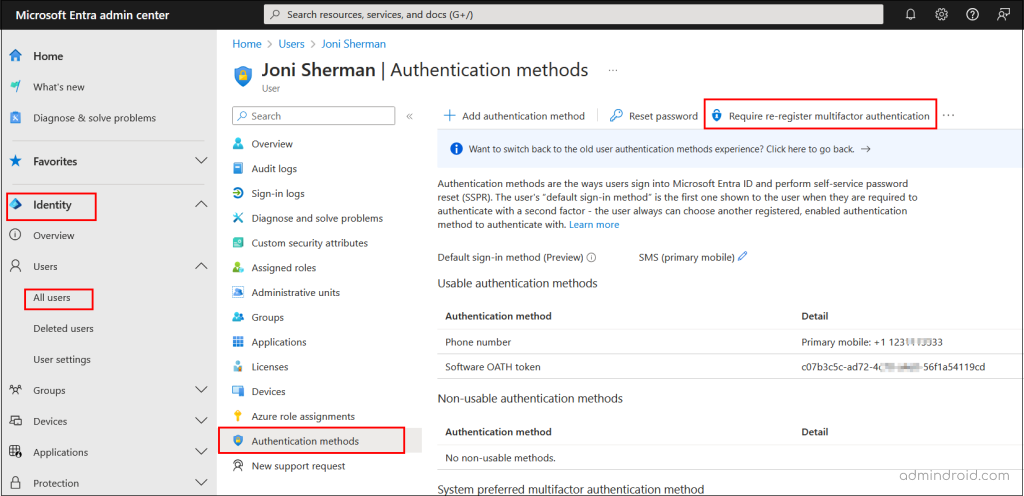
- Sign-in to Microsoft Entra admin center
- Navigate to ‘All Users’: Go to Identity > Users and select All Users.
- Select the User: Click on the required user to open their Overview page.
- Click on Authentication Methods and then click the Require re-register multi-factor authentication. This action will deactivate hardware OATH tokens and delete the following authentication methods:
- Phone numbers
- Microsoft Authenticator apps
- Software OATH tokens
How to remove a specific registered authentication method?
If you want to remove a specific registered authentication method, follow steps 1 to 3 and click Authentication Methods. Then, select the ellipsis (…) next to the authentication method listed under Usable Authentication Methods and click Delete.
This method is ideal if you need to revoke MFA authentication methods for a single user.
2. Reset MFA Using Microsoft Graph
Microsoft Graph offers a robust option for resetting MFA for Azure users. You can utilize either the Graph API or PowerShell, and here, we will focus on using Microsoft Graph PowerShell. This method is effective for both single users and bulk MFA management.
However, keep in mind that you’ll need to use different cmdlets for each authentication method. To reset MFA for multiple users and MFA methods, you’ll need to use loops to manage the process efficiently.
To simplify this task, we’ve prepared a PowerShell script that allows you to reset MFA for Microsoft 365 users in a more granular manner. Let’s dive in and explore how it works!
Reset MFA for Entra Users Using MS Graph PowerShell Script
We’ve developed an All-in-One script to reset MFA, designed to handle various real-time scenarios with ease. This script offers the flexibility to remove up to seven authentication methods, allowing you to remove either all or specific methods from all users or targeted users.
Supported authentication methods:
- FIDO2
- Microsoft Authenticator
- Phone
- Software OATH
- Temporary Access Pass
- Windows Hello for Business
User scope:
- Single user
- Bulk users (import CSV)
- All users
- Admin accounts
- Guest users
- Licensed users
- Disabled users
You can combine the user scope and authentication method to granularly reset MFA for various scenarios.
Download script: ResetMFAMethods.ps1
Here are the few major use cases to reset MFA for Microsoft 365 users:
- Reset MFA for a single user
- Reset MFA for bulk users (input CSV)
- Reset Microsoft Authenticator MFA
- Remove phone authentication from all users
- Reset MFA for guest users
- Reset MFA for admin accounts
- Reset MFA for licensed users
- Reset MFA for disabled users
- Remove a specific authentication method from all users
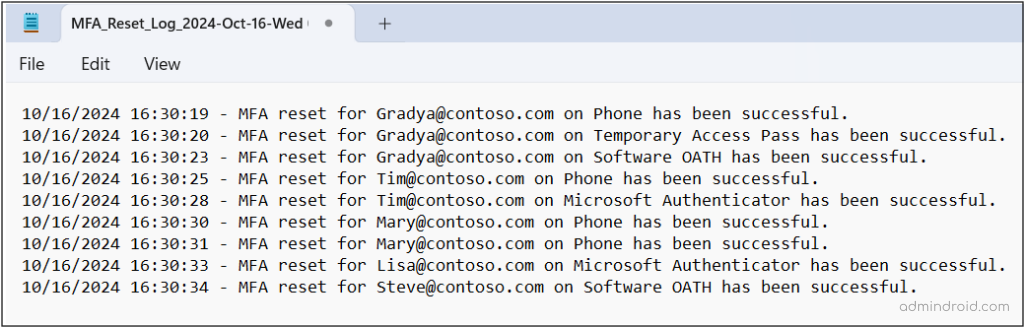
Note: After the script execution, a detailed log file will be exported, providing information on which MFA methods were removed from each user.
1. Reset Multi-Factor Authentication for a Single User
When a user cannot log in to their account using their existing authentication methods, administrators can reset MFA and prompt the user to re-register their MFA to regain access.
To reset MFA for a single user, run the script as follows
|
1 |
.\ResetMFAMethods.ps1 |
You’ll be prompted to enter the user ID. Alternatively, you can pass the UPN or Object ID using the -UserId parameter:
|
1 |
.\ResetMFAMethods.ps1 –UserId john@contoso.com |
The above example resets all registered authentication methods for John account. To reset a specific method, use the -ResetMFAMethod parameter:
|
1 |
.\ResetMFAMethods.ps1 –UserId john@contoso.com -ResetMFAMethod Phone |
The above format will remove the phone number authentication from John’s account.
2. Reset Multi-factor Authentication for Multiple Users
Managing MFA for multiple users can be time-consuming. With this script, you can reset MFA for a group of users using an input CSV file. To reset Multi-factor authentication for bulk users, pass the CSV file path using -CSVFilePath param as shown below.
|
1 |
.\ResetMFAMethods.ps1 –CSVFilePath D:/usernames.csv |
The above example resets all MFA methods for the users listed in the CSV file. You can also reset a specific method by adding the -ResetMFAMethod parameter.
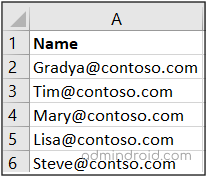
Sample input CSV:
3. Reset Microsoft Authenticator Device Details
Microsoft strongly recommends to configure MFA using Microsoft authenticator to help protect against MFA attacks. To encourage its adoption, they have also introduced the Registration campaign feature in Entra.
But what if a user loses their mobile device or accidentally resets it, losing access to the authenticator app? In these situations, resetting the Microsoft Authenticator method is crucial to ensure the user can regain access securely.
To reset the Microsoft Authenticator for a specific user, use the following command:
|
1 |
.\ResetMFAMethods.ps1 –UserId john@contoso.com -ResetMFAMethod 'Microsoft Authenticator' |
This command removes the Microsoft Authenticator app’s MFA settings, prompting John to re-enroll with a secure method.
4. Reset MFA Phone Number for All Users
Currently, passwordless authentication methods are considered safe, and users are increasingly adopting Passkeys for secure login. However, some users still depend on phone-based MFA (SMS and voice calls), which are less secure and more vulnerable to MFA attacks.
To strengthen your organization’s security, administrators should consider removing these less secure methods by resetting phone-based MFA and guiding users toward more robust alternatives.
To reset MFA phone number for all users, run the script the -AllUsers switch param.
|
1 |
.\ResetMFAMethods.ps1 –AllUsers -ResetMFAMethod Phone |
You also have the flexibility to reset phone number authentication for individual users or a group of users using a CSV file.
5. Reset MFA for Guest Users in Microsoft 365
Organizations that collaborate with external partners or vendors often grant guest users access to their resources. But what if these guests select authentication methods that don’t comply with your organization’s security policies? In such cases, you can reset MFA for Microsoft 365 guest users, ensuring they re-register with stronger authentication methods that align with your security standards.
To reset MFA methods for all guest users, execute the script with -GuestUsersOnly switch param:
|
1 |
.\ResetMFAMethods.ps1 –GuestUsersOnly -ResetMFAMethod Phone |
The above method will revoke phone authentication method from all the guest accounts.
You can also reset MFA for a specific guest account when they change phone numbers.
6. Reset MFA for Admin Accounts
Admin accounts possess elevated privileges, making them prime targets for cyberattacks. To mitigate these risks, it’s essential to enforce strong MFA authentication methods. Even when a default authentication method or system-preferred MFA is configured, admins can opt for alternative authentication methods. Therefore, it’s prudent to remove weaker authentication methods from admin accounts. To reset MFA for Microsoft 365 admins, run the script with -AdminsOnly switch param.
For example, to remove a third-party authenticator from all admin accounts, run the script as follows:
|
1 |
.\ResetMFAMethods.ps1 –AdminsOnly –ResetMFAMethod 'Software OATH' |
If you wish to reset all MFA methods for admin accounts, prompting them to re-register for MFA, use the following command:
|
1 |
.\ResetMFAMethods.ps1 –AdminsOnly |
7. Reset MFA Methods For Licensed Users in Entra
As part of Microsoft 365 offboarding best practices, it’s crucial to remove licenses from users who are no longer with the organization. When resetting MFA, you can exclude these unlicensed users to maintain a secure environment.
To reset MFA for licensed users only, run the script with -LicensedUsersOnly switch param:
|
1 |
\ResetMFAMethods.ps1 -LicensedUsersOnly |
The above example will reset the MFA for all licensed users, requiring them to re-enroll in MFA the next time they log in.
8. Reset MFA for Disabled Users
Disabled users, typically ex-employees, may still have their MFA settings linked to their accounts. To unlink their phone numbers and device details from the MFA, you can reset their MFA settings. To reset MFA for all the disabled users, execute the script using -DisabledUsersOnly switch param:
|
1 |
.\ResetMFAMethods.ps1 –DisabledUsersonly |
The above example will reset MFA and MFA registration details from all the disabled users.
9. Remove a Specific MFA Authentication Method from All Users
This use case is particularly useful when you need to eliminate a specific authentication method (e.g., SMS or software tokens) organization wide. By enforcing stronger authentication options, you can ensure a unified security approach and reduce vulnerabilities associated with weaker methods. To reset MFA method for all Microsoft 365 users, run the script with -AllUsers switch param
- To reset the Email authentication method, execute the script as follows.
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod Email |
- To reset Microsoft Authenticator MFA method, execute the script as shown below:
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod 'Microsoft Authenticator' |
- Temporary Access Pass (TAP) is a time-limited pass designed to simplify user onboarding. Once it expires, TAP remains listed under non-usable authentication methods. To reset Temporary Access Pass from all users, execute the script as follows:
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod 'Temporary Access Pass' |
Note: To use TAP, you need to enable temporary access pass in Entra. TAP is more useful during M365 user onboarding.
- To reset Windows Hello for Business, run the script as shown below:
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod ‘Windows Hello for Business' |
- To reset Software OAuth authentication (3rd-party authenticator) method, run the script using the below format:
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod 'Software OATH' |
- To reset FIDO2 or PassKeys authentication method, run the script as follows:
|
1 |
.\ResetMFAMethods.ps1 –AllUsers –ResetMFAMethod FIDO2 |
If you prefer not to run the script for all users, you can specify a UserID or a CSVFilePath instead of using the AllUsers parameter.
Note: Ensure you revoke MFA sessions to clear users’ remembered MFA sessions, which will require them to perform MFA the next time they log in.
You can also run the script using Certificate-based Authentication by registering app in Entra ID.
|
1 |
.\ResetMFAMethods.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> |
You can create a self-signed certificate or CA certificate based on your requirement.
In conclusion, regularly monitoring the authentication methods registered by M365 users is essential for safeguarding sensitive information and aligning with best security practices. We hope this blog has provided you with valuable insights to efficiently reset MFA, enhancing your organization’s security posture and productivity.