Join us for Day 8 of the Microsoft 365 Cybersecurity blog series! Discover how to lock down devices and level up your Secure Score. Let’s take your security to the next level together!
“A secure device is the first line of defense in today’s interconnected world.” – Gene Spafford
Devices are often the entry point for attacks, making device security a crucial focus. As we all know, Microsoft Secure Score isn’t just about boosting a number—it’s about implementing critical security measures. That’s why this time we’re highlighting secure score recommendations specifically designed to enhance device security. By addressing these recommendations, you can protect sensitive data, close security gaps, and strengthen your IT environment.
In this blog, we’ve handpicked key recommendations to enhance device security, reduce risks, and drive your Microsoft Secure Score higher. Let’s dive in and fortify your devices for a safer future!
Microsoft Secure Score Recommendations for Device Security
The device-based Secure Score recommendations can be grouped into three categories, as outlined below.
1. Generic Devices Security – 12 Points
| Recommendation | Secure Score Points | Attacks Prevented |
| Ensure that devices connecting have AV and a local firewall enabled | 3 | Account breach |
| Block OneDrive for Business sync from unmanaged devices | 3 | Data exfiltration |
| Ensure devices lock after a period of inactivity to prevent unauthorized access | 3 | Account compromise, identity theft, and unauthorized system access. |
| Ensure that users cannot connect from devices that are jail broken or rooted | 3 | Account or data breaches |
2. Mobile Devices Security – 9 Points
| Recommendation | Secure Score Points | Attacks Prevented |
| Ensure mobile device management policies are set to require advanced security configurations | 3 | Account breaches |
| Ensure mobile device management policies are required for email profiles – iOS/iPadOS only | 3 | Potential breaches of accounts and data. |
| Ensure mobile devices are set to wipe on multiple sign-in failures to prevent brute force compromise | 3 | Brute force attacks, Account breach |
3. Password-based Device Security – 18 Points
| Recommendation | Secure Score Points | Attacks Prevented |
| Ensure mobile devices require the use of a password | 3 | Sensitive data theft, account credential compromise, and malware installation. |
| Ensure that mobile devices are set to never expire passwords | 3 | Account breach |
| Ensure that mobile device password reuse is prohibited | 3 | Account breach |
| Ensure that mobile devices require a minimum password length to prevent brute force attacks | 3 | Brute force attacks, Account breach |
| Ensure that mobile devices require complex passwords (Simple Passwords = Blocked) | 3 | Account breach |
| Ensure that mobile devices require complex passwords (Type = Alphanumeric) | 3 | Account breach |
Where to Find These Device Secure Score Recommendations?
- You can quickly access and act on these recommendations within Microsoft 365 Defender. Simply follow this path:
Microsoft Defender → Exposure Management → Secure Score → Recommended actions. - Then, type “Device” in the search bar to display all device-related recommendations.
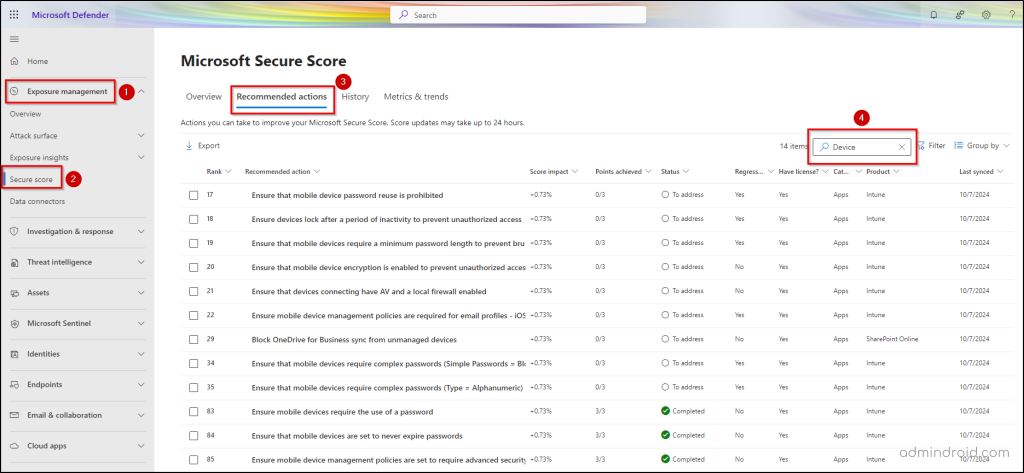
Without further delay, let’s dive into the detailed device recommendations. 🚀
4 Key Microsoft Secure Score Recommendations for Stronger Device Security
Microsoft 365 offers key recommendations to ensure that all devices connecting to your network are secure, preventing unauthorized access and data breaches.
1. Ensure that Devices Connecting Have AV and a Local Firewall Enabled
📍 Risk: Without antivirus and a local firewall, devices are highly vulnerable to common internet threats, making it easier for attackers to exploit weaknesses. This can lead to compromised accounts, data breaches, and unauthorized access, putting the organization at serious risk. Ensuring these protections are in place helps prevent such security gaps.
✅ Solution: Create a compliance policy in the Microsoft Intune admin center to ensure that all connecting devices have antivirus software and a local firewall enabled.
How to Create a Device Compliance Policy in Microsoft 365?
To create a device compliance policy in Microsoft Intune, follow the steps below.
Microsoft Intune admin center → Devices → Manage devices → Compliance → Create policy.
- Select the appropriate machine platform and profile type. Next, click Create.
- In the Basics tab, enter a suitable name and description for the policy. Click Next.
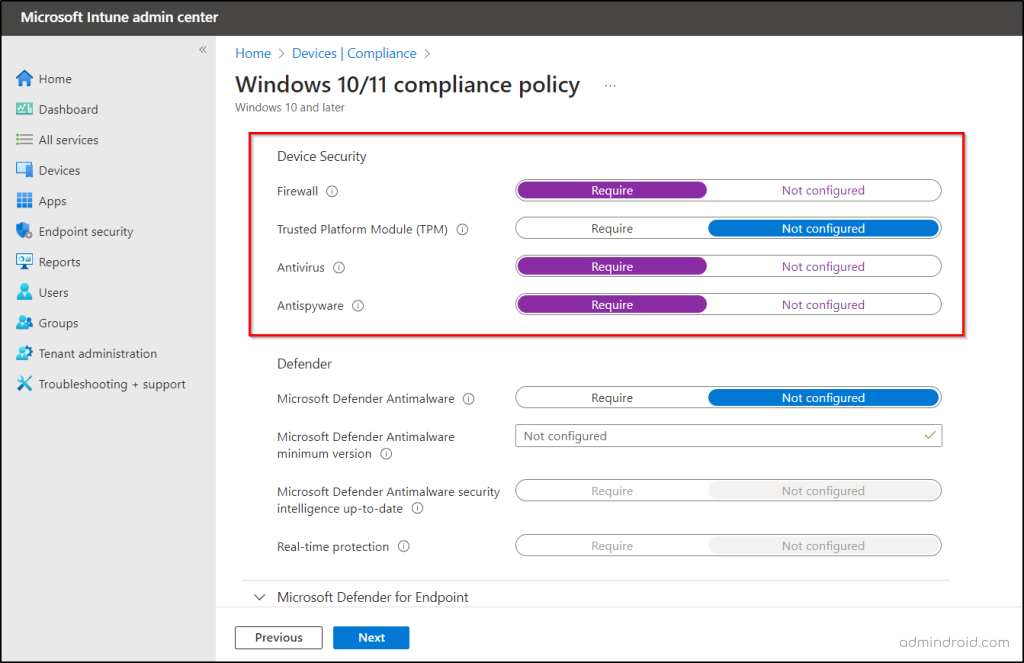
- In the Compliance settings tab, under System Security, navigate to the Device Security section.
- Set Firewall, Antivirus, and Antispyware to “Require” (Note: Some configurations may be hidden based on the platform).
- Configure any additional settings as needed, then click ‘Create.’
2. Block OneDrive for Business Sync from Unmanaged Devices
📍 Risk: Microsoft OneDrive for Business enables users to access their files from anywhere by signing into their cloud accounts. However, users can sync their folders or entire OneDrive account to local devices once OneDrive is installed, regardless of whether the device is Azure Domain Joined or Active Directory Domain Joined. This poses a security risk, as unmanaged devices may not comply with security policies, increasing the likelihood of accidental or intentional data leaks.
✅ Solution: To prevent data exposure, allow syncing only on computers joined to specific domains, ensuring only secure devices access organizational data. This applies to hybrid Active Directory setups.
For Microsoft Entra ID-joined devices, use Conditional Access policies to manage access. Device-based Conditional Access policies ensure that only compliant and secure devices are allowed to access organizational resources, further tightening security controls.
3. Ensure Devices Lock After a Period of Inactivity to Prevent Unauthorized Access
📍 Risk: Requiring devices to lock after inactivity is crucial. An unlocked phone in a public space can be stolen, giving attackers access to Microsoft 365 accounts and sensitive data.
✅ Solution: To lock the screen after a period of inactivity, create a device management policy in the Microsoft Intune admin center by following the steps below.
How to Auto-lock Microsoft Devices After a Period of Inactivity?
- Open the Device configuration policy page and select Create → New Policy.
- Choose the appropriate machine under Platform and Profile type as Templates. Then, choose Device restrictions and click Create.
- In the Basics tab, enter a suitable name and description for the policy. Click Next.
- In the Configuration settings tab, open the Password drop-down.
- Enable the Password setting by toggling it to Require to configure the options below.
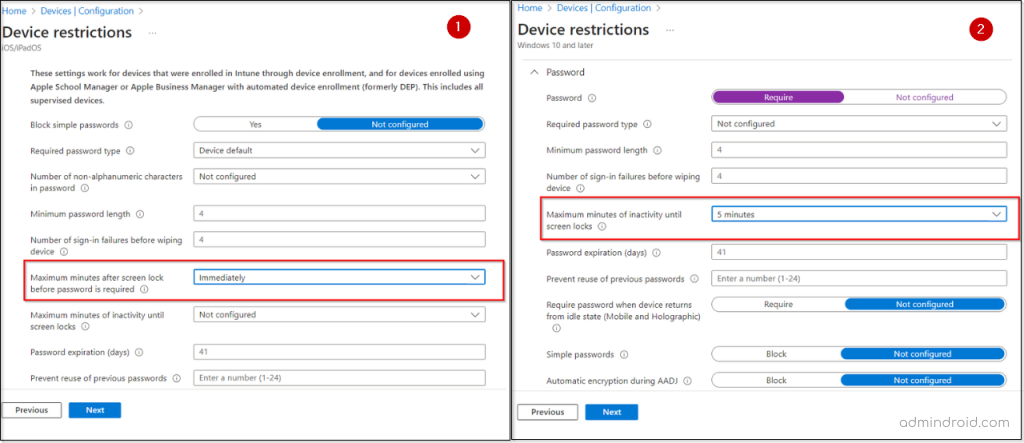
- In the Password section, ensure the following settings:
- For iOS/Mac devices, set the Maximum minutes after screen lock before password is required to Immediately.
- For All other devices, set the Maximum minutes of inactivity until screen lock to 5 minutes.
- Click Next, configure any additional settings, and then create the policy to implement the device profile.
4. Ensure that Users Cannot Connect from Devices that are Jail Broken or Rooted
📍 Risk: Jailbroken or rooted devices are those that have been modified to bypass manufacturer security controls, making them highly vulnerable to threats. With security protections disabled, these devices can easily run malicious software, compromising accounts and sensitive data.
✅ Solution: Blocking jailbroken or rooted devices helps prevent your organization from facing serious breaches and unauthorized access.
How to Block Jailbroken or Rooted Devices in Microsoft Intune?
Microsoft Intune admin center → Devices → Manage devices → Compliance → Create policy.
- Configure the Platform and Profile type according to your preference.
- In the Basics tab, enter a suitable name and description. Click Next.
- Under Compliance Settings → Device Health, set Jailbroken (iOS) or Rooted (Android) devices to Block.
- Configure any additional settings, then create the policy.
Boost Mobile Device Security with Microsoft Secure Score Insights
Microsoft 365 focuses on strong mobile device management (MDM) to protect sensitive information, making sure mobile devices meet security standards.
5. Ensure Mobile Device Management Policies are Set to Require Advanced Security Configurations
📍 Risk: Managing mobile devices in your Microsoft 365 organization is crucial for maintaining security. Without enforcing advanced security configurations, like requiring patches or blocking rooted devices, users could connect from vulnerable devices. For instance, imagine an employee using an outdated, unpatched device. This opens the door to basic exploits, potentially leading to data breaches and account compromises. Ensuring devices are up-to-date and secure helps protect against these risks.
✅ Solution: To ensure compliance and secure mobile devices, create mobile device management profiles in Microsoft Intune. At minimum, set up one configuration policy. For better coverage, Microsoft recommends separate policies for iOS and Android, allowing tailored security for each platform.
6. Ensure Mobile Device Management Policies are Required for Email Profiles – iOS/iPadOS only
📍 Risk: If you don’t enforce mobile device management to manage email profiles, especially on iOS/iPadOS devices, users can configure email accounts without security controls. This increases the risk of account breaches and data loss, as these unmanaged accounts lack the necessary protections.
✅ Solution: Microsoft recommends configuring a dedicated mobile device management policy for email profiles. This is especially important for iOS/iPadOS devices to ensure proper security controls.
Configure Mobile Device Management Policy for Email Profiles
Microsoft Intune admin center → Devices → Manage devices → Compliance.
For each policy applied to “iOS/iPadOS”:
- Select the policy by clicking on its name and choose the Properties tab.
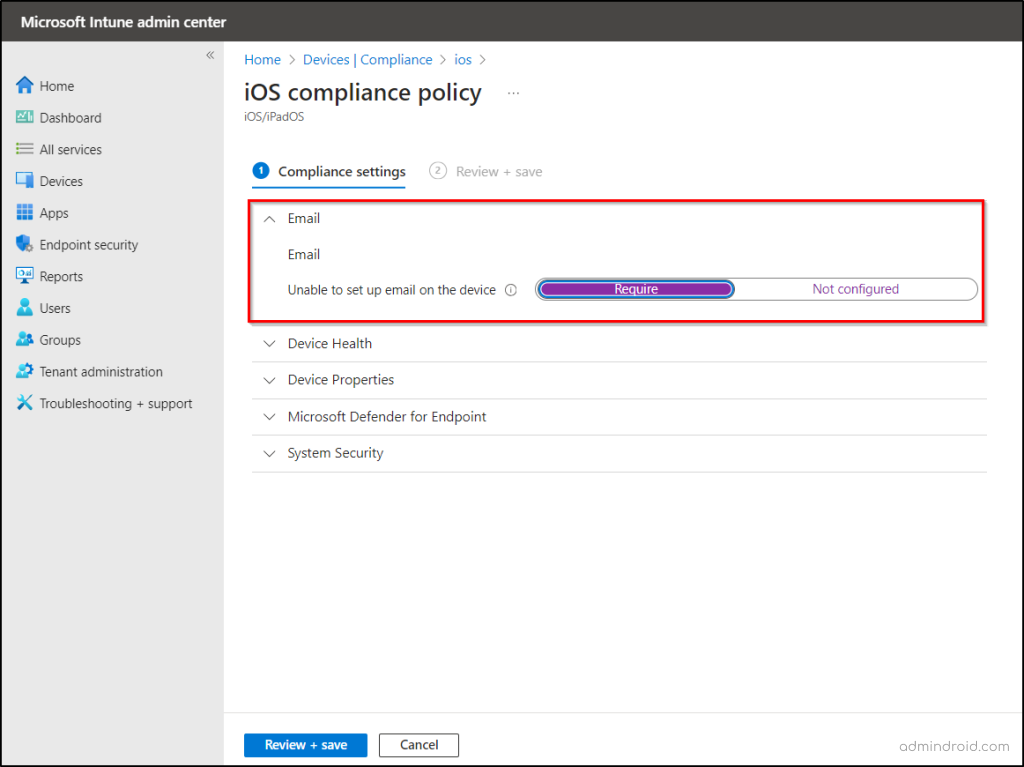
- Click Edit next to Compliance settings.
- In the Email section, it’s important to have “Unable to set up email on the device” set to “Require” to ensure secure email access.
- Finally, click Review + Save to apply the configuration.
7. Ensure Mobile Devices are Set to Wipe on Multiple Sign-in Failures
📍 Risk: Leaving mobile devices unprotected against multiple sign-in failures makes them vulnerable to physical attacks. If a device is lost or stolen, an attacker could attempt multiple sign-ins to gain access. Without a wipe feature, they could steal credentials, data, or install malware, putting your entire network at risk.
✅ Solution: Enforcing a wipe after failed sign-ins ensures data security, even in these situations.
How to Set Mobile Devices to Wipe on Multiple Sign-in Failures?
- Open the Device configuration policy page and select Create → New Policy.
- Under Platform, choose the appropriate machine. For Profile type, select Templates.
- Choose Device restrictions and click Create.
- In the Basics tab, enter a suitable name and description for the policy, then click Next.
- In the Configuration settings tab, expand the Password section.
- In the Password settings, ensure that Number of sign-in failures before wiping device is set to 10. (Ensure the Password setting is toggled to Require in order to configure this option.)
- Click Next and configure the remaining settings as per your preference. Finally, select Create to finalize the policy.
Lock Down Device Passwords with 6 Microsoft Secure Score Actions
📍 Risk: Securing accounts is important, but ensuring strong device password configurations is just as vital. Weak, reused, or simple passwords leave devices vulnerable to unauthorized access, brute force attacks, and data breaches. Without proper protection, device passwords can become an easy target for attackers, putting sensitive data at risk.
✅ Solution: To strengthen Microsoft 365 password protection and minimize device vulnerabilities, MS recommends the following password configurations in Intune:
- Ensure mobile devices require the use of a password.
- Ensure that mobile devices are set to never expire passwords.
- Ensure that mobile device password reuse is prohibited.
- Ensure that mobile devices require a minimum password length to prevent brute force attacks.
- Ensure that mobile devices require complex passwords (Simple Passwords = Blocked).
- Ensure that mobile devices require complex passwords (Type = Alphanumeric).
How to Create a Microsoft Intune Password Policy?
In Endpoint Manager, you can create a dedicated Intune password policy to apply these device restrictions efficiently, streamlining security management. Follow these steps to create a password policy in Microsoft Intune:
Microsoft Intune admin center → Devices → Manage devices → Configurations → Create → New policy.
- Choose the appropriate Platform, then under Profile type, select Templates >> Device restrictions and click Create.
- In the Basics tab, provide a suitable name and description for your policy, then click Next.
- On the Configuration settings tab, select the Password drop-down. Configure the following values for the respective Intune password settings, and then create the policy.
| Setting | Value |
| Password | Require |
| Password expiration (days) | Set the possible highest value. |
| Prevent reuse of previous passwords | 5 |
| Minimum password length | 6 |
| Simple passwords | Block |
| Required password type | Alphanumeric |
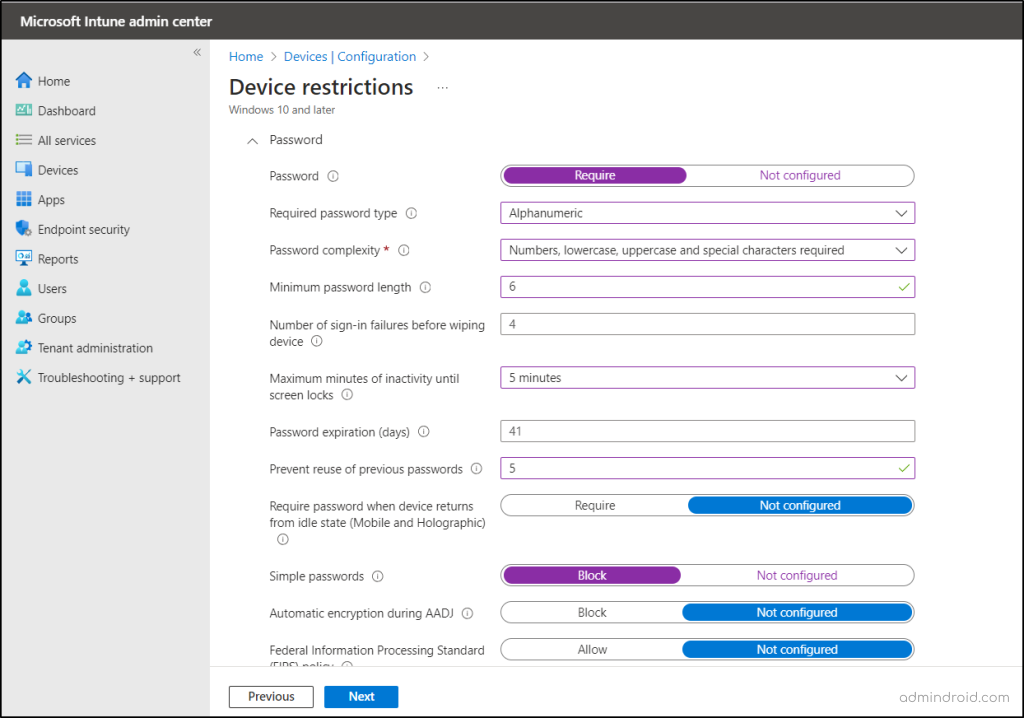
Points to Note:
- The profile type may be selected by default or adjusted based on your device configuration.
- Keep in mind that device configuration and compliance setting names may vary slightly depending on your choices. Ensure your configurations align with the intended purpose of the policy without causing interruptions.
While these recommendations enhance security, it’s important to see how they impact your Microsoft Secure Score. Tracking each configuration change can be difficult, and you may want a consolidated view of your Secure Score, especially for devices. That’s where Microsoft Defender Vulnerability Management dashboard comes in—a dedicated space to monitor and manage your Secure Score for devices.
Microsoft Secure Score for Devices
This device secure score reflects the security posture of your organization’s operating systems, applications, networks, accounts, and security controls. The goal is to address security configuration issues to improve your Microsoft Secure Score for devices. Simply select the bars in the dashboard to access detailed security recommendations and take action.
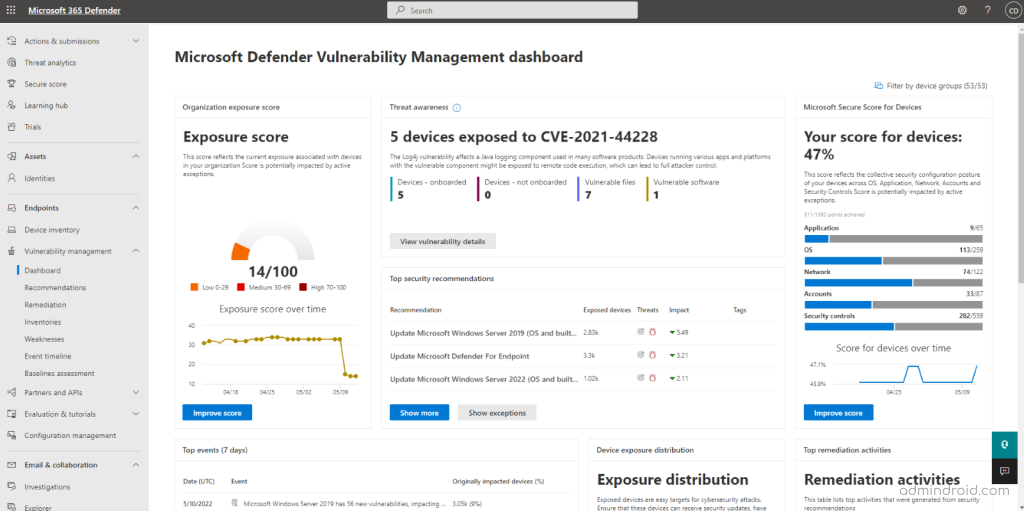
In addition to the Microsoft Secure Score for Devices, this dashboard also highlights several key components crucial to ensuring device protection.
- Exposure Score in Microsoft 365 Defender– View your organization’s device exposure to threats. The score is evaluated based on device vulnerabilities, the likelihood of breaches, and alerts detected on your devices. Lowering this exposure score requires remediating security issues from the recommendations.
- Device Exposure Distribution – See the number of exposed devices based on their risk level. Click a section in the chart for details like device name, risk level, OS, and health status.
- Expiring Certificates – Monitor certificates that have expired or are set to expire within the next 30, 60, or 90 days.
- Top Security Recommendations – View prioritized recommendations based on your organization’s risk. Explore exceptions and take action on recommendations that require urgent attention.
- Top Vulnerable Software – Get a ranked list of vulnerable software installed on your devices. Select an item for more details or view the complete software inventory.
- Top Remediation Activities – Track remediation actions generated from security recommendations. Review details or manage exceptions to keep security framework up to date.
- Top Exposed Devices – See a list of exposed devices and their exposure level. From the device list, you can manage actions like running antivirus scans, initiating investigations, or isolating devices.
These insights help Microsoft 365 admins proactively address vulnerabilities, reduce exposure, and strengthen device security across the organization.
We hope this blog has effectively highlighted the essential device-related Secure Score recommendations and simplified the process of configuring them. If you have any questions or need further clarification, feel free to leave a comment below. Stay proactive in securing your devices, and improve your Microsoft Secure Score for devices!






