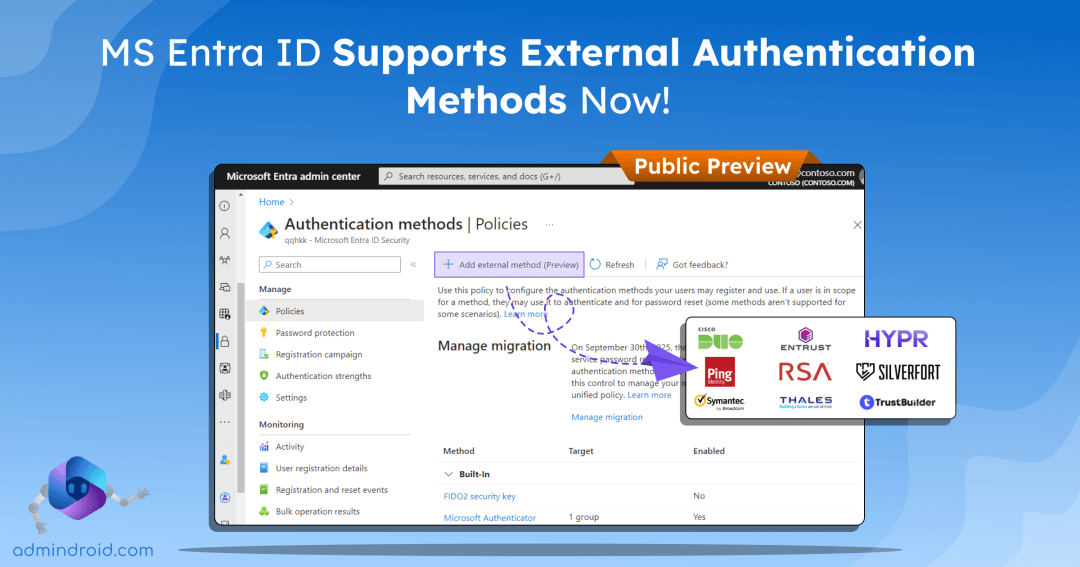
Entra ID is an identity provider that allows you to manage access to your resources and applications while protecting user identities. Users’ additional authentication like MFA is typically performed through various methods including passwords, SMS, phone calls, or an authenticator app. As Microsoft mandates MFA for accessing portals like Entra, Intune, and Azure, implementing strong authentication methods, such as phishing-resistant MFA, becomes crucial. Microsoft is now introducing external authentication methods in public preview, which enables the integration of third-party MFA solutions for user sign-ins.
A recent study by Microsoft revealed that MFA prevents 99.2% of account compromises, highlighting its importance in securing user accounts. With external authentication methods (EAM), users can seamlessly integrate their preferred MFA solutions directly with Entra ID. This provides greater flexibility and choice while ensuring secure user identities.
What are External Authentication Methods in Microsoft Entra?
An external authentication method in Microsoft Entra ID allows users to select an external provider to fulfill multifactor authentication (MFA) requirements during their sign-in. This means you are not restricted to using only Entra’s native authentication methods; you can also opt for third-party authentication solutions that better align with your organization’s needs. Unlike federation, where user identities are managed externally, EAMs maintain user identities within Microsoft Entra ID.
Previously, custom controls were used to achieve similar outcomes. However, custom controls can’t be used with Microsoft Entra ID Protection’s automation, which requires Microsoft Entra multifactor authentication. These new external authentication methods replace custom controls and offer several added advantages:
- They adhere to a standards-based open model, allowing any authentication provider to build an integration by following the integration documentation.
- They are managed in the same way as Entra authentication methods.
External authentication methods in Entra ID can be used to satisfy MFA requirements for different situations including,
- Migration from Active Directory Federation Services (ADFS) to Entra ID
- Conditional Access MFA requirement
- Identity Protection risk-based policies
- Privileged Identity Management role activation
- Microsoft Intune device registration
- Applications requiring MFA
Note: EAMs and custom controls can work in parallel. Microsoft recommends creating two Conditional Access policies: one for the custom control and one for MFA.
License Requirement for Entra ID External Authentication Methods
To utilize external authentication methods, at least a Microsoft Entra ID P1 license is required.
What are the Supported Identity Providers for EAM?
The following Independent Software Vendors (ISVs) build integration with Microsoft Entra ID & Microsoft is yet to add more to the list.
- Cisco Duo
- Entrust Identity
- HYPR Authenticate
- Ping Identity
- RSA
- Silverfort advanced MFA
- Symantec VIP
- Thales STA
- TrustBuilder MFA
Create an External Authentication Method in Microsoft Entra
To create an EAM, you need the following information from your external authentication provider:
- Application ID: This is a unique ID assigned to your application by your authentication provider. It’s used to integrate your application with their services. You typically need admin consent to use this ID within your organization.
- Client ID: This ID is used to identify your application specifically when it requests authentication from Microsoft Entra ID.
- Discovery URL: This is the discovery endpoint where your application can discover information about the authentication provider’s capabilities and settings, like OpenID Connect (OIDC) details.
UPDATE DEC 2025: External Authentication Methods Registration Enforcement
Previously, users could optionally register an External Authentication Method (EAM) in Microsoft Entra ID during the Public Preview. Microsoft has now updated the Public Preview to enforce registration for EAM, ensuring that all users have a registered method. This change is part of preparations for General Availability planned for the end of March 2026.
Key changes:
| User Type | Status Before Dec 8, 2025 | Status Before Dec 8, 2025 |
| Existing users | Registration optional | Pre-registered by Microsoft (no action needed) |
| New users | Registration optional | Must complete in-line registration during first sign-in (joining after Dec 2, 2026) |
| Admins | Optional user registration | Can register users on their behalf if needed |
Configure an EAM Using Entra Admin Center
To integrate third-party multifactor authentication solutions with Entra ID, follow the below steps.
Step 1: Sign in to the Microsoft Entra admin center at least as a Privileged Role Administrator.
Step 2: Select Authentication methods under ‘Protection’.
Step 3: Click on Add external method (Preview).
Step 4: Fill in the provider details in the Method Properties section. For example,
Name: Adatum
Client ID: 06a011bd-ec92-4404-80fb-db6d5ada8ee2
Discovery Endpoint: https://adatum.com/.well-known/openid-configuration
App ID: 2f3d5a67-7441-4f1e-aa92-e77ca6b5a5ca
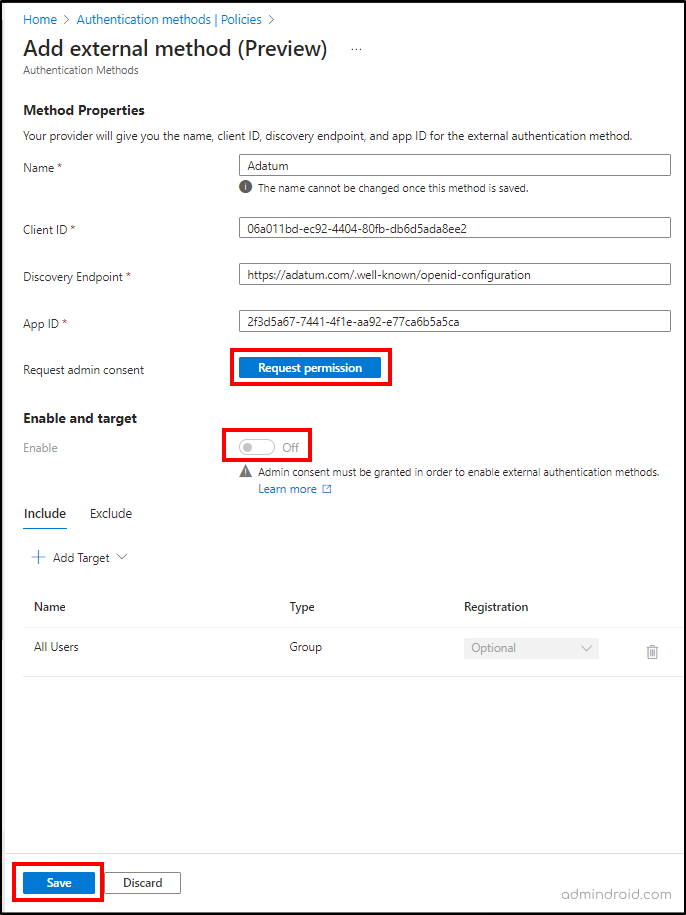
Note: The display name (e.g., Adatum) is shown to users while selecting MFA methods and must be unique. It cannot be changed once it is created.
Step 5: The next step is to grant admin consent for the provider’s application. For that, click on the ‘Request permission’ button.
Step 6: Then, sign in with a privileged role admin/ global admin account and grant the provider’s application with the necessary permissions. If you don’t have the required role, you can only save the method but not enable it.
Step 7: Click ‘Accept’ to grant admin consent to the application. The page will refresh, confirming that admin consent has been granted.
Step 8: Once admin consent is granted and permissions are approved for the application, you can enable the method.
Step 9: Under the Include -> Add Target section in the ‘Add external method’ page, you can add the desired groups. Once added, all users in the groups can choose this method to fulfill their MFA. If permissions are revoked or the application is deleted, signing in using this method will fail.
Manage External Authentication Methods Using Microsoft Entra Admin Center
To manage your EAMs in the Microsoft Entra admin center, go to Authentication methods -> Policies under ‘Protection’. From there, select the specific method name to open its configuration options. Choose which users are included and excluded from using this method.
If you wish to restrict access to the EAM, you have two options:
- Toggle Enable to Off and save the method configuration.
- Alternatively, click Delete to completely remove the method from the policy.
You can also manage the Authentication methods policy by using Microsoft Graph. For this, you need the Policy.ReadWrite.AuthenticationMethod permission.
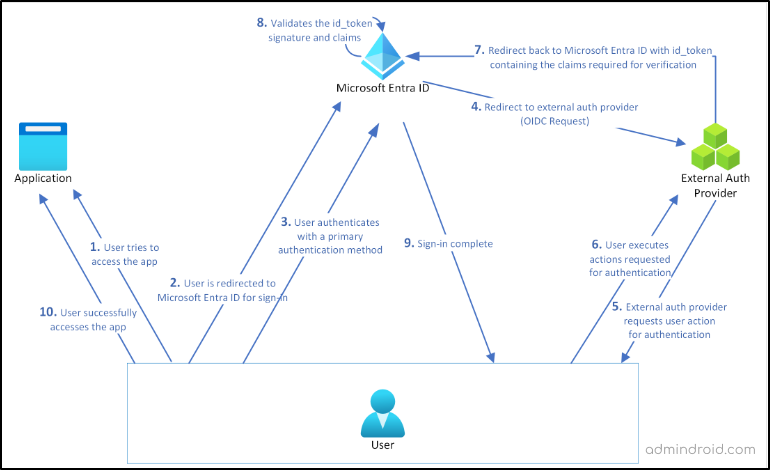
EAM Sign-in Flow in Microsoft Entra
After integrating external MFA with Entra ID, the sign-in process proceeds as follows:
- User Sign-In:
- User signs in with a first factor (e.g., password).
- Microsoft Entra ID determines if MFA is required.
- MFA Requirement:
- If MFA is required, the user can choose the EAM to complete second factor authentication.
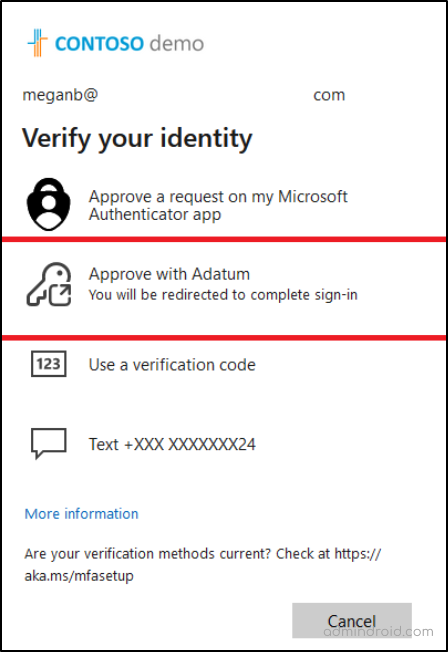
Note: Currently, system-preferred MFA is not supported for EAM. When system-preferred MFA is enabled, users will see their other sign-in options in the default order. They can choose a different method and then select the EAM.
- Redirection to EAM:
- Microsoft Entra ID redirects the user’s browser to the EAM URL.
- The URL is discovered from the discovery URL provided by the admin.
- The application provides a token with user and tenant information.
- Token Validation:
- The external provider validates the token from Microsoft Entra ID.
- Optionally, the external provider may call Microsoft Graph to fetch additional user information.
- User Authentication:
- The external provider requests user action for authentication.
- Once the user executes the requested action, the external provider redirects back to Entra ID with id token required for verification.
- Final Validation:
- Microsoft Entra ID validates the token’s signature and claims.
- If validation is successful, the MFA requirement is met and the sign-in will be completed.
Closing Lines
We hope this blog provides you with the necessary details to begin using Entra ID EAM. Implementing MFA is essential to avoid account compromises. With the addition of external MFA, you can significantly enhance Entra ID security. Thanks for reading. Feel free to reach out through the comment section for any further questions.