Azure AD Graph API has been a fundamental tool for developers working with Azure Active Directory services and authentication. However, as of February 1, 2025, these APIs will no longer be available unless extended access is explicitly configured. With full retirement scheduled for June 30, 2025, Microsoft Graph API migration is now more essential than ever to ensure your applications remain functional and future-proof. Take the smart step forward by exploring how to migrate your apps and service principals from Azure AD Graph API to Microsoft Graph API for better integration.
Why is Azure AD Graph Retiring?
Azure Active Directory Graph is retiring to simplify API offerings and focus on a unified solution that aligns with Microsoft’s evolving ecosystem. Maintaining multiple APIs, such as Azure AD Graph and Microsoft Graph, creates redundancy and inefficiencies.
Microsoft will no longer invest resources or provide maintenance-related support for Azure AD Graph APIs. By consolidating all functionality in Microsoft Graph, developers gain consistent development experience, streamlined updates, and more effective feature rollouts. This shift enhances and supports a single, modern API framework designed to meet both current and future organizational needs.
Timeline of Azure AD Graph API Retirement
- June 30, 2023: Azure AD Graph officially enters its retirement phase after a three-year advance notice.
- August 31, 2024: Any new applications created after this date must continue using Azure AD Graph by enabling extended access. Existing applications will remain unaffected and continue to function as usual.
- February 1, 2025: Both existing and new applications must be enabled for extended access to continue functioning with Azure AD Graph. Applications that fail to extend access will stop working.
- June 30, 2025: Initially announced retirement date. However, Microsoft has extended limited support for apps configured with extended access.
- Late July 2025: Expect one to two planned temporary outages as Microsoft prepares for final retirement of Azure AD Graph API.
- Early September 2025: Azure AD Graph API will be completely retired. From this date, access will end entirely, and applications still dependent on it will no longer function.
Why Migrate to Microsoft Graph API Now?
Migrating to Microsoft Graph is essential to prevent disruptions caused by the deprecation of Azure AD Graph API. It ensures your apps and service principals maintain uninterrupted functionality while unlocking advanced features.
Microsoft Graph provides a unified endpoint to seamlessly access Microsoft Entra and Microsoft 365 services. It offers enhanced security and reliability compared to Azure AD Graph, while providing the same core functionality plus additional features. The new APIs expand capabilities in areas like identity protection, privileged access, workflow management, and cross-tenant permissions.
With Microsoft Graph client libraries, organizations benefit from built-in support for retry handling, secure redirects, and seamless authentication. They also provide payload compression, a capability not available with Azure AD Graph. This transition ensures continued performance and unlocks these enhanced functionalities.
How to Identify Azure AD Graph Dependent Apps?
To make our lives easy, Microsoft provides the following methods to identify applications and service principals still using Azure AD Graph API.
- Review Microsoft Entra recommendations
- Use the App registrations menu in the Microsoft Entra
- Analyze network proxy logs for Azure AD endpoints
Review Microsoft Entra Recommendations
1. Log in to the Microsoft Entra admin center and navigate to Recommendations tab under Identity → Overview.
2. If you have any apps or service principals that use the Azure AD Graph APIs, you’ll find the following two recommendations.
- Migrate Service Principals from the retiring Azure AD Graph APIs to Microsoft Graph
This recommendation lists impacted applications created within your tenant. If an app uses Azure AD Graph APIs and accesses the tenant via service principal login (e.g., Azure PowerShell or CLI), it will be shown in this recommendation. You’ll need to either configure the app for extended access or update it to stop using Azure AD Graph APIs. - Migrate Applications from the retiring Azure AD Graph APIs to Microsoft Graph
This highlights impacted service principals, which are multi-tenant apps provided by Microsoft and third-party software vendors. All apps registered in your tenant, including those from independent, external, and third-party vendors, are subject to Azure AD Graph deprecation.
By default, Microsoft provided apps have been extended until June, but they must be updated by June 2025. If a vendor-provided app appears in the recommendations, contact the vendor to request an update.
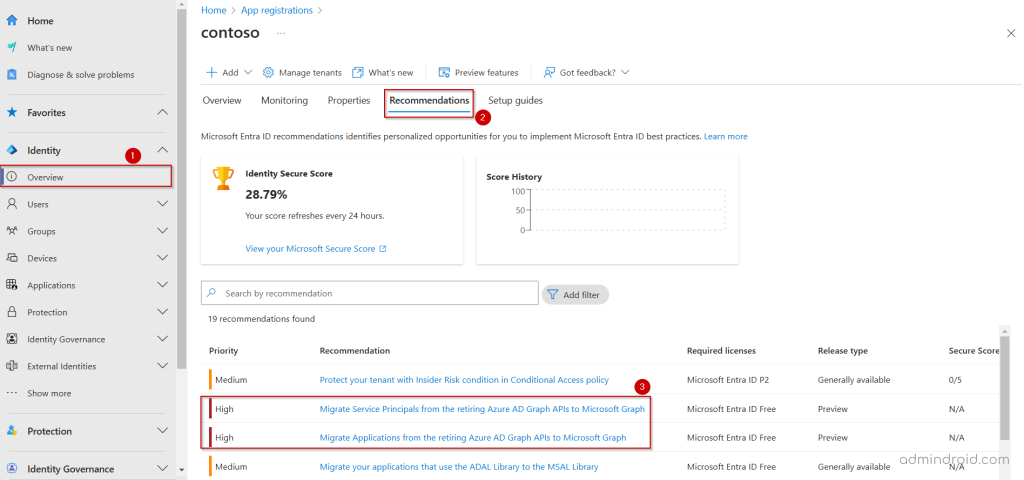
3. Click the recommendation to view the affected apps and service principals. These two retirement recommendations will summarize Azure AD Graph API usage by applications in your tenant over the last 30 days.
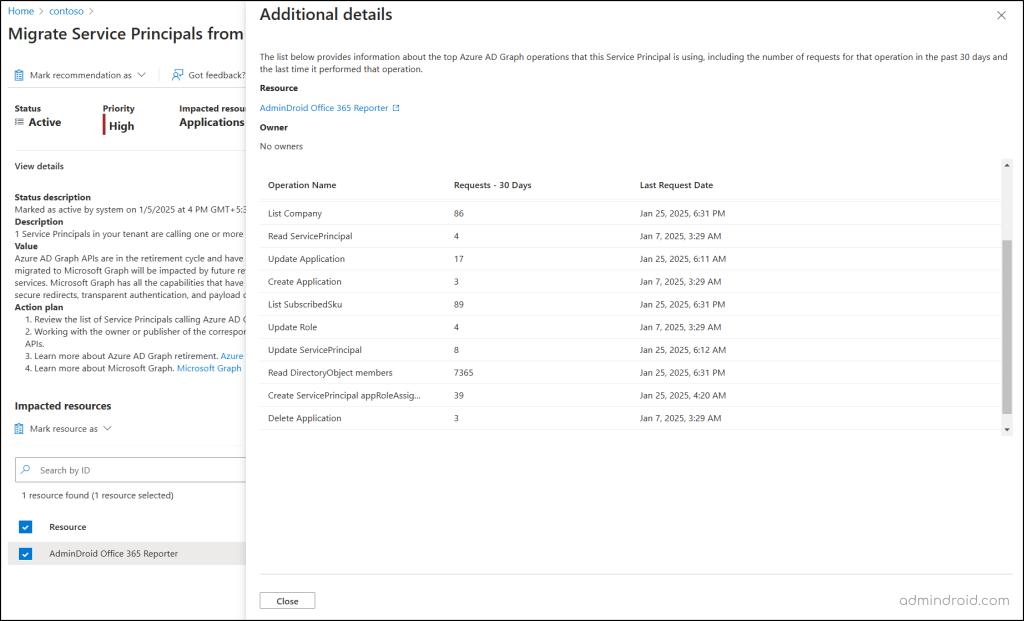
4. To view key insights into an Azure AD app’s activities, select More Details on listed app. This will show you operation name (e.g., List Application, Create User, Delete Group), the number of requests made in the last 30 days, and the date of the last request.
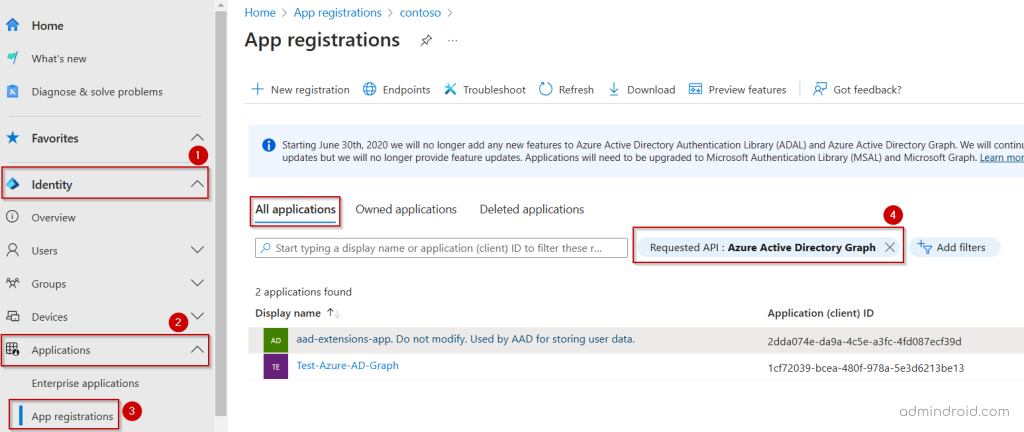
Use the App Registrations in the Microsoft Entra Admin Center
- In the Microsoft Entra admin center, navigate to Identity >> Applications >> App registrations >> All applications tab.
- Then, click the Add filters, choose the Requested API, and hit Apply. In the Requested API pop-up, select the Microsoft APIs.
- Under the Please select an API drop down, select Azure Active Directory Graph and click Apply.
Analyze Network Proxy Logs for Azure AD Endpoints
Inspect your network server traffic logs to identify apps using Windows Azure AD Graph APIs. Use a filter proxy to spot communication with the https://graph.windows.net/ Azure AD Graph endpoints.
Now, you’ve identified all applications relying on Azure AD Graph, the next step is to focus on extending their functionality and planning their seamless transition to Microsoft Graph.
How to Extend Azure AD Graph Access?
Microsoft offers a temporary option to extend access for applications that still depend on Azure AD Graph API. This temporary solution provides organizations with additional time to adapt and migrate their applications to Microsoft Graph API.
Applications created after August 31, 2024, will encounter the 403 Unauthorized error when accessing Azure AD Graph APIs unless explicitly configured for this extended access. Similarly, apps created before this date must enable extended access by February 1, 2025. However, extended access ends on early September 2025, after which all requests to Azure AD Graph APIs will be denied.
To enable extended Azure AD Graph access for an application in your tenant, run the following cmdlet.
|
1 2 3 4 5 6 7 8 9 |
Import-Module Microsoft.Graph.Beta.Applications $params = @{ authenticationBehaviors = @{ blockAzureADGraphAccess = $false } } Update-MgBetaApplication -ApplicationId <ObjectID> -BodyParameter $params #Replace <ObjectID> with the object ID of your app that you want to allow extended access period |
The Azure AD Graph access extension is a short-term solution to ensure business continuity for critical applications still awaiting Microsoft Graph API migration. However, this should not be seen as a replacement for migration since support for Azure AD Graph will eventually end.
How to Migrate Apps from Azure AD Graph to Microsoft Graph?
Microsoft provides a checklist for Microsoft Graph API migration from Azure AD Graph API, which recommends the following steps to facilitate a smooth transition.
- Understand API changes: Identify key differences between Azure AD Graph and Microsoft Graph APIs, such as request syntax, resource names, properties, methods, permissions, directory extensions, and batching.
- Assess affected resources: In Microsoft Entra Recommendations, review affected resources to find applications and service principals that utilize the Azure AD Graph API.
- Update the resources: Replace Azure AD Graph API endpoints with Microsoft Graph equivalents. Update the version, resource name, and permissions as needed to align with your application’s requirements. Migrate apps from AD FS to Entra ID as part of this transition to ensure seamless identity management.
- Adapt to changes: Modify your application to address differences in data structures, property names, and response formats. For .NET applications, update client libraries to the latest versions to ensure compatibility.
- Test and deploy: Perform comprehensive testing of features, such as directory extensions and batching, in a controlled environment before deploying to production. This helps identify and address potential issues early.
- Migrate gradually and monitor: Begin migration with non-critical systems and gradually transition core applications. Use logging to monitor performance, detect issues, and validate token acquisition. Then, confirm authentication workflows during migration.
Benefits of Migrating to Microsoft Graph
Beyond simply replacing Azure AD Graph, Microsoft Graph revolutionizes how organizations interact with Microsoft’s ecosystem. This Azure AD Graph app migration presents an opportunity to implement more robust API permissions and access enhanced functionality for your applications.
- It seamlessly connects Microsoft Entra ID with services like Microsoft 365, Dynamics 365, and Windows to enable a unified experience beyond identity management.
- With Microsoft Graph, operational tasks like managing Microsoft 365 groups, restoring deleted users, and restricting external user invitations are streamlined for seamless efficiency.
- For developers, it offers extensive support through its broad SDKs, advanced OData query capabilities, and streamlined integration workflows that simplify innovation.
- Its security features deliver advanced identity protection, privileged identity management, and proactive monitoring of risky users.
- Governance tools such as access reviews and terms-of-use agreements help organizations maintain control over their environments.
- It empowers you to assign licenses automatically through group-based licensing and makes large-scale license management more efficient.
The retirement of Azure AD Graph marks a pivotal moment to adopt Microsoft Graph. It’s more than just a migration—it’s a step toward a better and more secure API. Starting early will help you ensure a smooth transition and avoid disruptions. Hope this blog post has provided valuable insights into the Microsoft Graph API migration. Share your thoughts and experiences about this migration in the comments below.






