MFA is a must, there is no doubt about it! 💯But what matters in MFA is its frequency. Like how everything beyond a certain limit is dangerous, over-MFA prompting can also affect users’ productivity. 😑 Even this unexpected over prompting might be the game of the attackers phishing via MFA.
So, as an admin, it’s essential to monitor the frequency of authentication/MFA prompts, noticing any unusual patterns and investigating them further when needed. 💯 But how can you effectively tackle this task?
Well, Microsoft got your back with their Entra workbook, “Authentication prompts analysis”! This handy tool helps you analyze why users are getting bombarded with prompts and lets you troubleshoot excessive MFA prompts. Let’s first see the reason behind the frequent prompts and continue with how Entra workbooks will help for further investigation.
Reasons for Excessive Authentication Prompts in Microsoft 365
Here are the reasons why users might be prompted for second-factor authentication frequently:
- If the idle session timeout in Microsoft 365 is set too low, users will need to authenticate more often.
- Users may also be prompted for reauthentication if their sign-in frequency is set to “every time” in Conditional Access policies.
- Users might encounter frequent MFA prompts when logging in from different devices that fall under device-based Conditional Access policies.
- Cybercriminals may use MFA fatigue attacks and try to gain access to Microsoft 365 resources, leading to frequent MFA prompts for users.
- Sometimes, users are prompted for MFA every time they log in to different workload due to misconfigurations.
- When the “Remember MFA on trusted device” setting is configured too low, users may face increased prompts for reauthentication. Customizing the “Don’t ask MFA again” option is important in such cases while ensuring security.
In simple, the frequent auth prompts may be due to stringent MFA policies, misconfigured applications, and most importantly there might be a cyber-attack attempt happening! So, admins need to figure it out and differentiate whether the MFA request is legitimate or unexpected. This can be done easily with Entra workbooks. Let’s get into the main topic now.
What are Microsoft Entra Workbooks?
Microsoft Entra workbooks are used to create a personalized interactive dashboard of Entra ID logs. These workbooks facilitate the creation of visually engaging reports and charts derived, providing a comprehensive overview of essential Entra data.
Microsoft offers pre-built workbook templates like sign-in failure analysis workbook, Conditional Access gap analyzer, Conditional Access insights and reporting workbook, sign-in analysis workbook and MFA gaps workbook, to facilitate the easy analysis of Entra logs. One such template that helps to overcome the problems we discussed earlier is the “Authentication prompt analysis workbook” to analyze the MFA prompts. Let’s dive into its details now.
Authentication Prompts Analysis Workbook in Entra
The authentication prompt analysis workbook serves as a comprehensive workbook for identifying and analyzing various types of authentication prompts that’s happening within your Microsoft 365 environment. These prompts are categorized based on different pivots, including users, applications, operating systems, processes, and more.
When Can We Use the Authentication Prompts Analysis Workbook?
- Swiftly analyze users with many prompts: This workbook will help us analyze cases where users are prompted for Multi-Factor Authentication (MFA) more frequently than usual. It will also assist in quickly evaluating user feedback regarding frequent MFA occurrences.
- Interpret specific auth details: Admins can readily interpret specific details of authentication prompts, such as checking MFA prompts by specific authentication methods, the count of multi-factor authentication prompts per user, or MFA prompts triggered by specific Entra ID policies. This granular analysis helps you fine-tune the necessary MFA policies and allows you to take swift actions.
- Prompts on high-profile users: For high-profile users like CEOs and COOs, monitoring MFA prompts is needed to ensure their accounts are protected with stronger MFA, without any misconfigurations. With this workbook, you can analyze the frequency of the prompts of such high profiles easily.
- Identify legacy auth methods: The workbook extends its utility by offering insights into legacy TLS and other authentication processes. This feature allows administrators to monitor the usage of outdated protocols and flag any security risks associated with their continued use.
Let’s see how to use authentication prompts analysis workbook. Before that, make sure you have satisfied all the prerequisites to use Microsoft Entra workbooks.
How to Use Authentication Prompts Analysis Workbook?
To view and access the authentication prompts analysis workbook, follow the steps below.
- Log in to Microsoft Entra admin center.
- Navigate to the Monitoring & health section and select “Workbooks” options.
- Select the “Authentication Prompts Analysis” workbook from the Usage section.
This workbook uses major components text, query, parameter, and group, for better understanding and organization of necessary details on MFA prompts.
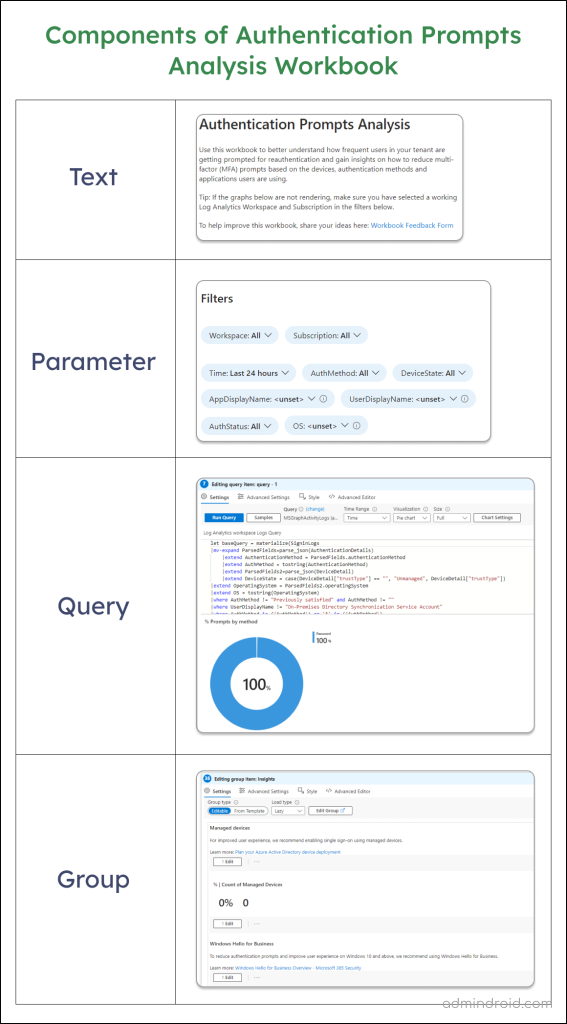
Now, let’s get to break down the key sections of the authentication analysis workbook in Entra ID.
- Check MFA Prompts Based on Authentication Methods
- Analyze Authentication Prompts Based on Devices
- Authentication Prompts Based on Users
- Authentication Prompts by Application
- Analyze Authentication Prompt Based on Process Detail
- Authentication Prompt by Entra ID Policies
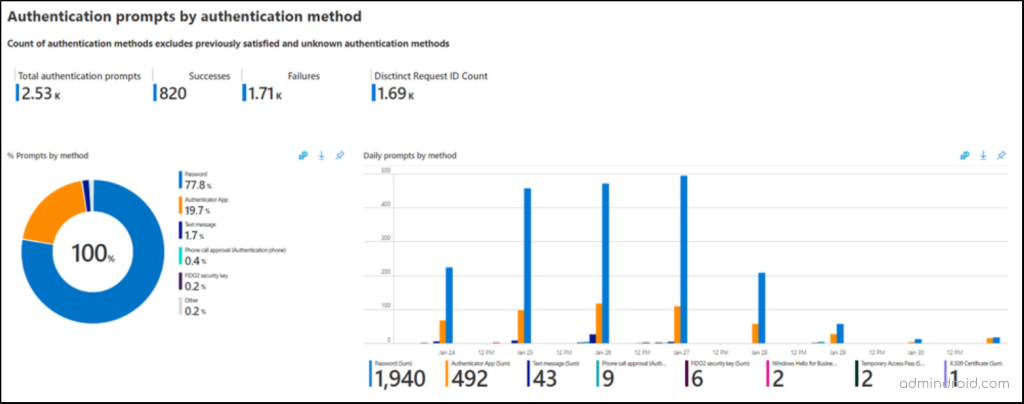
✅Check MFA Prompts Based on Authentication Methods
This section provides you a summary of authentication prompts by authentication methods, including:
- Total authentication prompts across different MFA methods.
- Count of successful authentication prompts.
- Count of failed authentication prompts.
- Count of unique attempts by authentication method (Distinct request ID count).
Also, this section provides insights into the count of authentication prompts based on different authentication methods such as,
- Passwords
- SMS
- Authenticator app
- FIDO2 security key, etc.
It helps you identify which MFA methods are causing users to be prompted frequently. If you need to analyze prompts by authentication methods within specific time ranges, you can utilize the default “Time” filter provided. However, keep in mind that if you specify the time range using this filter, it will apply to all sections of the workbook.
- For a more granular approach, you can customize the workbook in Entra ID by creating specific time range filters for each section. This allows you to tailor the analysis to focus on particular time frames relevant to individual sections.
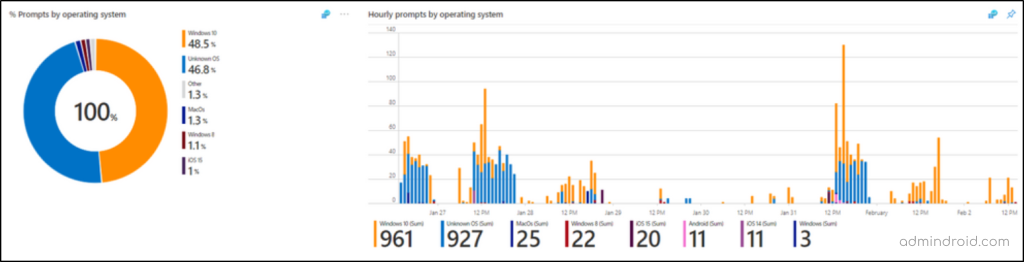
✅ Analyze Authentication Prompts Based on Devices
This section is categorized into two:
- Authentication prompt by operating system – In this sub-section, you can view the hourly MFA prompts based on operating system (OS), such as Windows, macOS, or mobile operating systems like iOS or Android. It helps to determine if the authentication prompts are being caused by devices that have older or outdated operating systems installed. Therefore, once you identify users with devices running older operating systems, it is advisable to upgrade them to newer versions.
- Authentication prompt by device state – This sub-section displays how prompts are distributed across various types of devices in your environment: Azure AD joined, Hybrid Azure AD joined, Azure AD registered, or unmanaged devices. The important thing is to see how many devices are unmanaged. If unmanaged devices are detected, plan ahead to take action immediately to prevent a security risk.
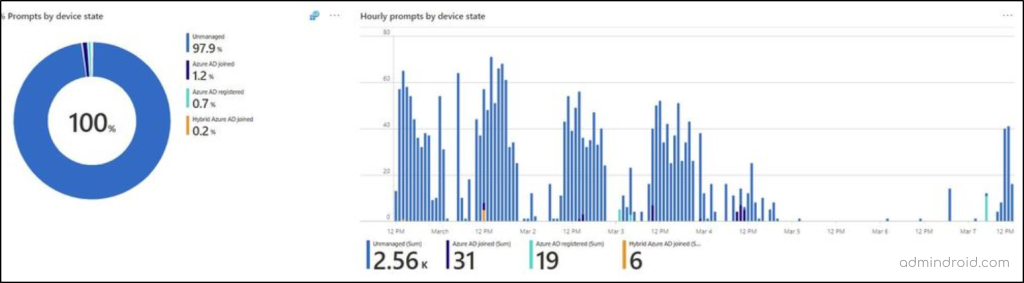
✅ Authentication Prompts Based on Users
This section focuses on individual Microsoft 365 users and their authentication prompt count. Admins can see how frequently a particular user encounters prompts, which aids in troubleshooting high-profile user issues.
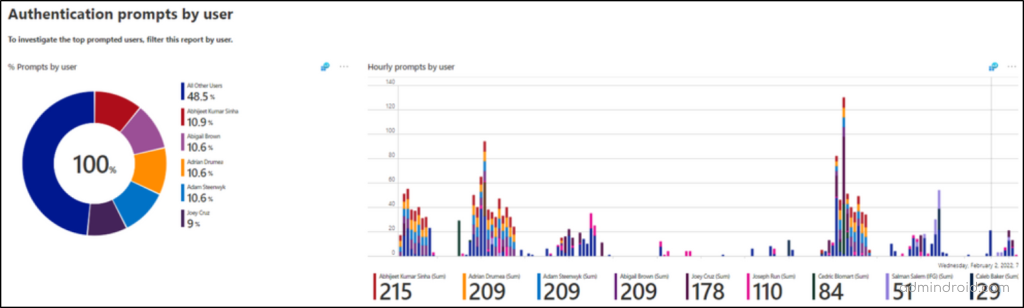
When you scroll further, you can see the two following tiles.
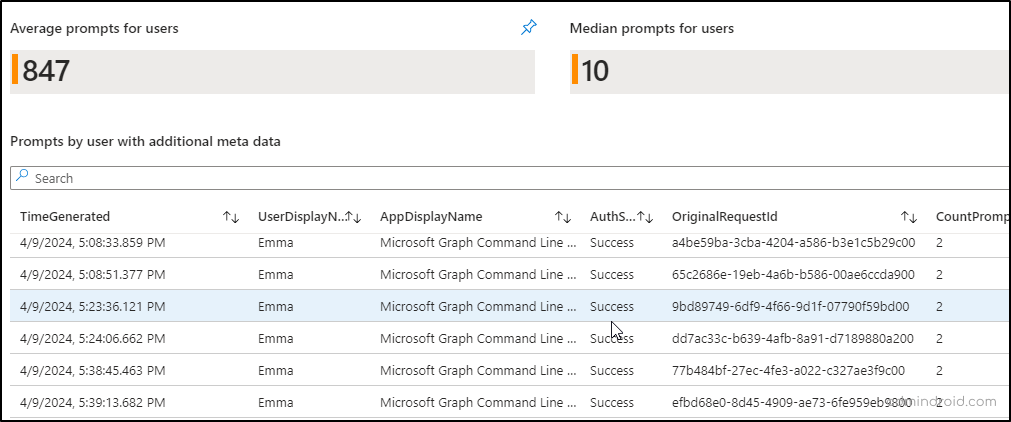
- Average prompts for users: This section provides details about the average number of MFA prompts for users. This can be helpful when investigating specific user complaints or identifying potential configuration issues with a particular user’s account.
- Median prompts for users: This section shows how many prompts a typical user encounter. It helps you see what a normal user experiences, not someone who gets prompted constantly or barely at all.
You can also get a detailed report with additional information like App Id, timings, request ID from the “ Prompts by user with additional meta data ” report.
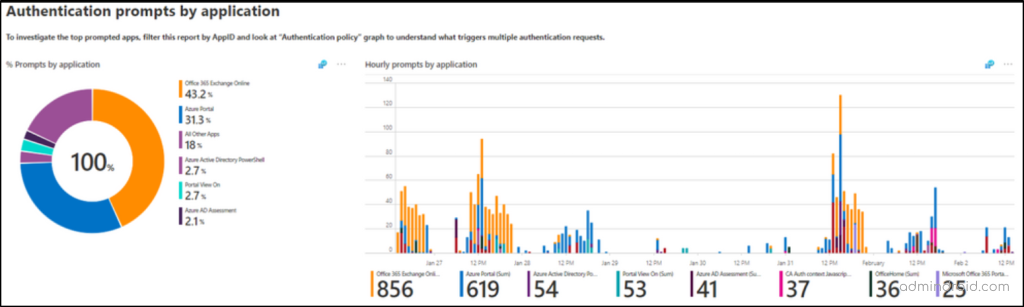
✅Authentication Prompts by Application
Misconfiguration of applications in Microsoft 365 can also lead to unexpected and continuous prompts on users. In this section, you can identify while accessing which apps like SPO, and Teams client users are prompted for authentication. So, you can take the necessary steps like reconfiguring the application. This also helps you identify if specific applications have overly strict authentication requirements.
✅ Analyze Authentication Prompt Based on Process Detail
This section provides deeper insights into the authentication process, including details like OAuth scope, authentication library type, IP addresses, and legacy TLS usage. This helps diagnose complex authentication problems.
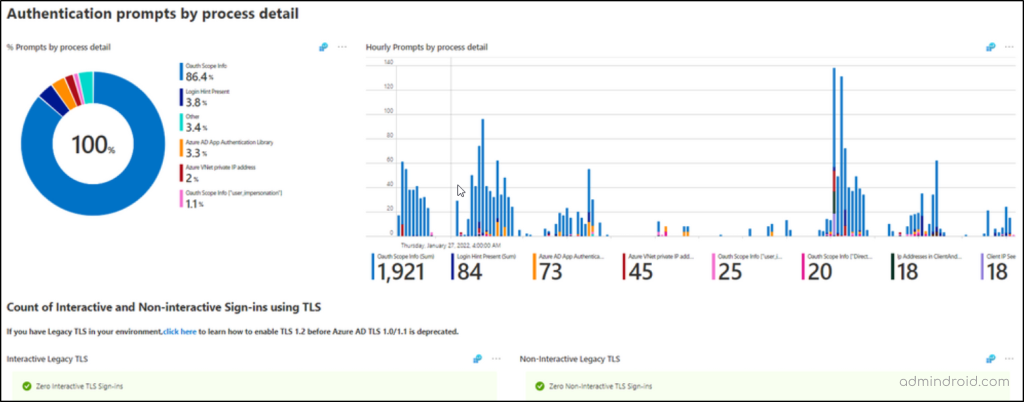
✅ Authentication Prompt by Entra ID Policies
This section helps you investigate how the MFA is enforced by Azure AD policies like Conditional Access, security defaults, per-user MFA, app requires MFA, and others. So, you can analyze and fine-tune the settings balancing both the user convenience and Microsoft 365 security.
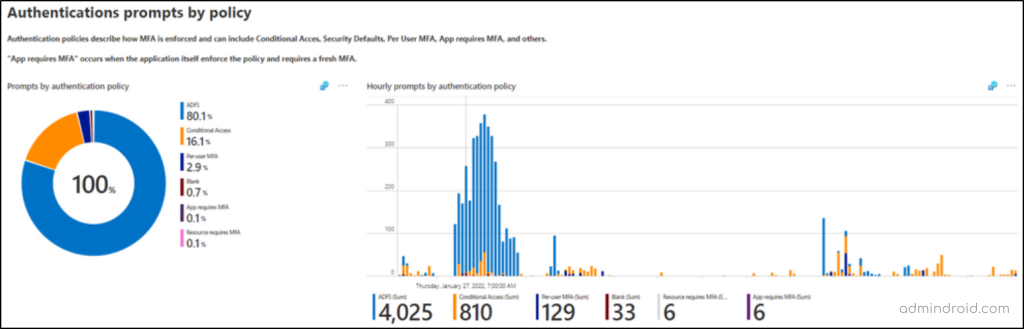
Also, at the end, you can see the recommendation section, which will give you tips like below to securely reduce extra MFA prompts with authentication prompt analysis workbook.
- Single-sign-on using managed devices.
- Recommend using Windows Hello for Business.
- Move users to Microsoft Authenticator.
- Microsoft Enterprise SSO plug-in for Apple devices.
Edit or Create a New Authentication Prompts Analysis Workbook
While this workbook provides a comprehensive overview of authentication prompts in Microsoft 365, it’s possible that it doesn’t include all the specific details you’re looking for. However, don’t fret! You have the flexibility to customize or even create a brand-new workbook to focus solely on the insights that matter most to you.
Edit Existing Authentication Prompts Analysis Workbook in Microsoft Entra ID:
You can tailor the pre-existing authentication prompt analysis template by using the “Edit” option accessible for each object within the workbook. This allows you to refine the insights and include specific details that might be crucial for your analysis.
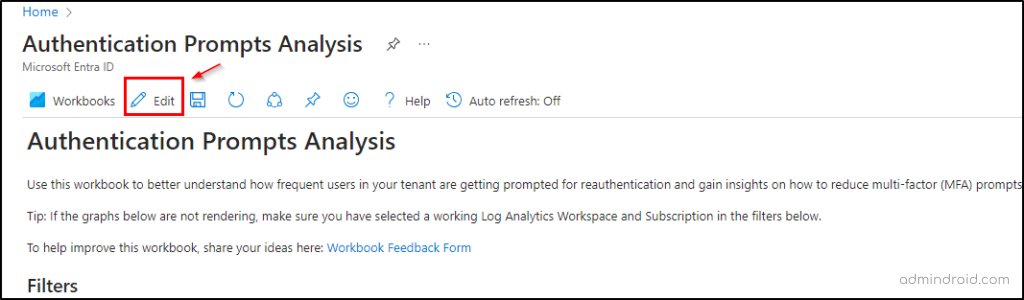
Create a New Workbook in Microsoft Entra ID:
Microsoft provides the flexibility to create a new Entra workbook, meeting your exact needs. You’ll utilize various components such as text, queries, links, and more to construct your workbook.
As an example, suppose you need to get the authentication prompt counts of specific user by specific auth method over the past 7 days. In this case, you can employ the query component and utilize the Kusto query below to get the authentication counts on specific users based on specific method.
|
1 2 3 4 5 6 7 8 9 |
SigninLogs | where TimeGenerated >= ago(7d) | where UserPrincipalName == '<UserName>' |mv-expand ParsedFields=parse_json(AuthenticationDetails) |extend AuthenticationMethod = ParsedFields.authenticationMethod |extend AuthMethod = tostring(AuthenticationMethod) | where AuthMethod == '<Authentication_Method>' | summarize Count = count() by UserPrincipalName | project UserPrincipalName, Count |
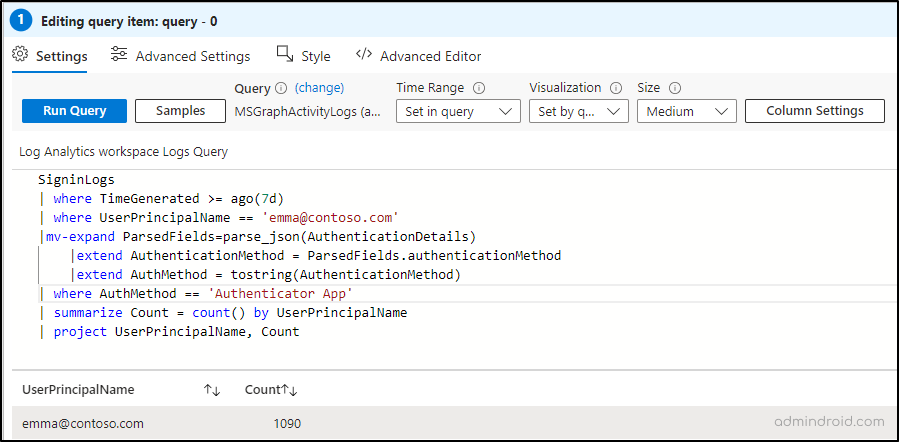
Additionally, you have the flexibility to incorporate other components to further personalize your workbook. Whether it’s adding explanatory text, including hyperlinks to related resources, or integrating visualizations to enhance understanding, all are possible!
Easily Plan Next Steps with Authentication Prompts Analysis Workbook
- Once you’ve pinpointed the sources of excessive prompts with this workbook, you can take proactive measures such as temporarily disabling respective MFA method for thorough investigation.
- If the issue stems from vulnerable authentication methods like passwords, you can configure a password policy in Azure AD to enhance Microsoft 365 security.
- Even better, you can enable a registration campaign in Entra ID to move your users to a strong MFA method “Microsoft Authenticator”.
So, hereafter swiftly and instantly handle all the over prompting cases by analyzing this workbook. I hope this blog brings you information about the needed authentication prompt analysis workbook. Stay tuned for the next workbook in the series. Furthermore, if you have queries about this workbook, contact us in the comment section.