Month of October
The month of cozy fall evenings, 🍂
The month of Halloween, 🎃
And most importantly, the month of Cybersecurity Awareness! 🛡️
After 2 successful years of helping Microsoft 365 admins with our series on:
- Essential, frequently missed Microsoft 365 configurations – 31 Settings
- Harden Microsoft 365 Security – 31 Advanced Settings
We’re back and ready with a new approach this year!
| The theme for Cybersecurity Awareness Month 2024 is going to focus on something different, a fresh perspective: Secure Scores in Microsoft 365. |
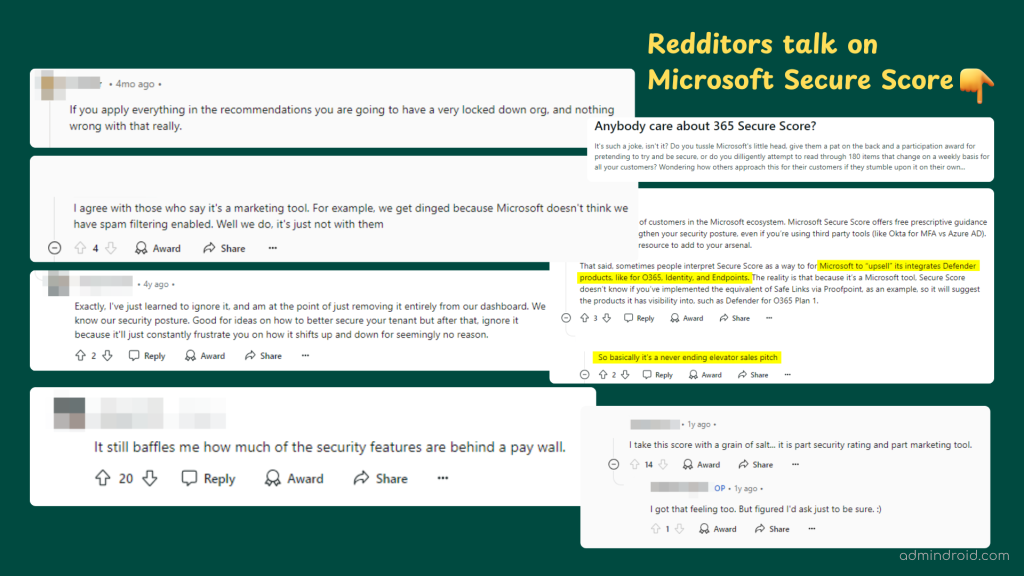
Sure, we know some sysadmins bash on the Secure Score as just a sales pitch from Microsoft—but there is more to it than meets the eye! If you have not explored its full potential yet, that is exactly what we will do.
Is Microsoft Secure Score Really a Sales Pitch?
The ‘secure score recommendations based on assessments’ sound like a great help from Microsoft, right? And they definitely are! 💯But many people online seem to buzz a lot, a few are:
- Most security features recommended are only available with higher-tier licenses and are locked behind a price barrier!
- Can you only increase your Microsoft Secure Score if you buy more advanced licenses?
- Secure Score is merely a marketing tool – a “sales pitch” to upsell Microsoft products.
- Some even argue that Secure Score is more about pushing Defender products—like Defender for Office 365, Identity, and Endpoint protection—than genuinely improving your security.
- Many believe that to boost your score, you might take actions that could even be counterproductive.
Microsoft Secure Score – A Free Security Assessment Tool:
Microsoft Secure Score is all about how you see and use it. 😌At its core, Microsoft Secure Score is a security monitoring tool, dashboard, or portal – however you want to refer to it!
It’s free, easy to use, and a great starting point for Microsoft 365 security audits. Here’s what it does:
✅Evaluate your organization’s security posture,
✅ Gives a snapshot of your overall security health,
✅ Calculate a score based on the protocols you’ve implemented,
✅ Shows you exactly how secure your organization is.
🔥It also offers ‘Actionable Recommendations’ to boost your security and score.
The recommendations update over time, so even if you’re not keeping up with the latest security practices, Secure Score can guide you on what to improve.
One more thing: A good Secure Score is often requested for Cyber Insurance, so it’s worth paying attention to! 😉
Focus on Recommendations, Not the Score:
At AdminDroid, we suggest using Secure Score wisely:
- Focus less on the score itself but more on the recommendations it suggests!
- Review the Secure Score recommendations, prioritize the ones that are most relevant to your organization, and decide if they’re worth the upgrade for your setup.
- Not every recommendation will fit your Microsoft 365 environment; always balance security with usability.
Ultimately, we say: Act on the recommendations, not the score!
| It’s just a number! Don’t feel so INSECURE about your SECURE SCORE. 💯 |
Cybersecurity Awareness Month Series – 2024
Now, let’s jump into our plan for this series! The end goal is not to chase the highest secure score but to increase security standards by selectively implementing recommendations tailored to your licenses, size, and specific needs.
We at AdminDroid have planned to take off the series into two parts:
- Part 1: We’ll categorize & compile the Microsoft suggested recommended actions in the secure score along with a step-by-step implementation guide.
- Part – 2: This is different! We will provide a thorough list of security configurations missing from the secure score recommendations.
This way, we can support everyone – from those looking to increase their Secure Score to those who just wish to strengthen their Microsoft 365 security.
After all, A security configuration a day keeps the hacker away!
Day 1: Boost Secure Score by 12 Points with 3 Easy Configurations
Enhance your organization’s security with three easy Microsoft 365 configurations. Disable external calendar sharing, block third-party app registrations, and ensure only invited users bypass the Teams meeting lobby. These quick adjustments improve your Microsoft Secure Score by 12 points, providing stronger protection without needing extra licenses.
Day 2: Top 3 Settings to Increase Secure Score by 28 Points
With numerous recommendations available, it can be tricky to focus on the most impactful ones. This blog highlights the highest-scoring configurations that boost your Microsoft Secure Score by 28 points and secure your Microsoft 365 environment.
Day 3: Top 5 Microsoft Entra ID Secure Score Recommendations to Boost Your Security
Increase your Microsoft secure score as well as improve overall security by these top 5 Entra ID recommendations, especially for Entra ID P1 and P2 users. Right from configuring sign-in risk CA policies to blocking legacy authentication, insider risk protection, and much more with detailed implementation steps. Check out and enhance your organization’s security.
Day 4: 6 SharePoint Online Recommendations to Improve Secure Score
Enhance your organization’s security with 6 actionable recommendations for SharePoint Online. These tips focus on critical settings like managing guest access, enabling Microsoft Defender, and more. By following these steps, you can improve your Microsoft Secure Score by 16 points, ensuring better protection for your data and collaboration tools.
Day 5: 6 Essential Password Settings to Improve Secure Score & Security
Did you know that 81% of cyberattacks can be blocked with simple password configurations? By implementing essential password settings, you can greatly enhance your Microsoft 365 security and improve your Secure Score. Here are the top 6 password settings every M365 organization should consider.
Day 6: How to Improve Microsoft Identity Secure Score?
Microsoft secure score provides scores across various categories, such as apps, data, and devices. Among these, the secure score focuses specifically on recommendations related to an organization’s identity, which we call “Identity secure score recommendations”. To boost your identity secure score, check out this blog where we highlight three essential and easy-to-implement recommendations.
Day 7: Strengthen Exchange Online Security with Microsoft Secure Score Recommendations
As organizations heavily rely on email for professional communications, strengthening Exchange Online security is essential. This blog outlines key steps such as enabling Customer Lockbox, mailbox auditing, modern authentication, etc., to protect sensitive data and ensure compliance. Implement these Secure Score suggestions to significantly boost your security in email communications.
Day 8: Top Ways to Maximize Microsoft Secure Score for Devices
Devices are often the first target for attacks, making their security critical. Microsoft Secure Score is more than just a number—it’s a roadmap to stronger protection. This blog highlights key device-related Secure Score recommendations, explaining their significance and how to configure them. By implementing these steps, you’ll protect sensitive data, close security gaps, and strengthen your IT environment.
Day 9: Major Microsoft Teams Configurations to Boost Secure Score by 8 Points
As Teams becomes central to collaboration, securing meetings is crucial. This blog highlights essential configurations, such as limiting external presenters, restricting anonymous users, and controlling meeting access, to enhance your organization’s secure score by 8 points. Implement these changes to safeguard your Teams environment and ensure secure communication.
Day 10: 6 Microsoft Information Protection Recommendations to Improve Secure Score
Improve your organization’s data security with six simple Microsoft Information Protection (MIP) tips that can help you gain 15 points in your Microsoft Secure Score. This blog covers important settings like turning on data loss prevention and creating sensitivity labels for your data. By following these tips, you can better protect sensitive information and reduce the risk of data breaches in your Microsoft 365 environment.
Day 11: Secure Your Third-party Applications with Microsoft Secure Score Recommendations
Enhancing your organization’s security requires securing the third-party applications as well. Identify the supported third-party apps in MS secure score and implement the given recommendations to improve your secure score and overall security.
Day 12: Boost Microsoft Secure Score with Essential Email Filtering and Spam Protection
This blog explores key email filtering and spam protection strategies in Exchange Online to strengthen cybersecurity and Microsoft secure score. It provides detailed steps for configuring anti-spam policies, quarantining threats, and utilizing Zero-hour auto purge to protect against phishing, malware, and spam attacks.
Day 13: Boost Secure Score & Manage Third-Party Apps in Microsoft Defender for Cloud Apps
Discover how to boost your organization’s Secure Score with Microsoft Defender for Cloud Apps. This blog outlines essential cloud app policies for monitoring app approvals, detecting suspicious activity, and managing cloud app trends to strengthen your security posture.
Day 14: Tune Phishing Protection to Boost Your Microsoft Secure Score
With evolving phishing threats on the rise, it’s crucial to keep your security measures up to standard. Manually catching every email threat is impossible, so here are a few Microsoft Secure Score recommendations to help fine-tune your organization’s phishing protection.
Day 15: Track Secure Score Changes in Microsoft 365
Setting up Secure Score recommendations is just the beginning—monitoring changes is what truly matters! Keep track of how your Microsoft 365 Secure Score evolves with gains, losses, regressions, and more to ensure continuous protection.
Day 16: Change Default Calendar Permissions in Microsoft Outlook
With Microsoft Outlook’s default setting allowing everyone to view each other’s availability, effective management of calendar permissions is essential. Shared calendar information, such as availability status, meeting titles, locations, and durations, can expose sensitive data. This blog gives a clear guide on changing default calendar permissions in Microsoft Outlook.
Day 17: How to Reset MFA for Microsoft 365 Users
Is your organization still relying on weak MFA methods, or have users lost access to their MFA devices? Resetting MFA is your first line of defense to ensure security and productivity! Simplify this process with our PowerShell script, which addresses over 25 real-world scenarios for effortless MFA resets.
Day 18: Strengthen Security by Configuring Idle Session Timeouts for Entra Portal
Discover how to enhance security in your organization by configuring session timeouts in the Entra portal. This guide explores the importance of session management and provides step-by-step instructions to automatically sign out users after periods of inactivity in the Entra portal. Doing so significantly reduces the risk of session hijacking and unauthorized access, thereby protecting sensitive data in Microsoft 365.
Day 19: Microsoft Security Defaults vs Conditional Access – When to use What?
The debate over how to enable MFA—Security Defaults vs. Conditional Access—has persisted for years. This blog will highlight the key distinctions between these approaches, guiding you to choose the one that best meets your organization’s security needs.
Day 20: Enable Preset Security Policies in Microsoft 365
Missing key security configurations amid constant updates and feature rollouts in Microsoft 365 can be risky, right? That’s where preset security policies in Microsoft Defender come in. These pre-configured measures let you quickly apply protections by simply selecting the users. Learn how to enable them in this blog.
Day 21: Allow External Sharing for Specific SharePoint Sites
Setting site-level external sharing in SharePoint is a wise decision, but the process can be quite cumbersome as you have to configure it for each site individually. Plus, you also need to restrict sharing for sensitive areas. Fortunately, this can be simplified with a PowerShell script that allows you to enable external sharing for one or multiple sites while also restricting it for others. Let’s dive in and see how it works!
Day 22: Remove Unused Credentials from Apps in Microsoft Entra
This blog highlights the importance of eliminating unused application credentials in Microsoft Entra. The Identity Secure Score recommendations provide insights into how stale credentials can create security vulnerabilities. We will outline the risks involved and how addressing them can reduce attack surface and improve your overall Microsoft 365 security.
Day 23: Get Entra App Registrations with Expiring Client Secrets and Certificates
Microsoft 365 applications can be used for various purposes and its usage has been increased. For admins, it’s essential to identify the expiration of application client secrets and certificates to avoid downtime. This blog helps to retrieve the expiration details and solves various use cases, providing granular reports efficiently.
Day 24: How to Disable LinkedIn Integration in Microsoft Teams & Outlook
LinkedIn integration in Microsoft 365, especially in Teams and Outlook, links your LinkedIn account to your work profile. While it lets you view colleagues’ profiles, skills, and work history, it can raise privacy concerns, increase phishing risks, and cause distractions. For better security, it’s recommended to disable LinkedIn integration in Microsoft 365.
Day 25: Shared vs. Inactive Mailboxes: The Best Choice for Managing Departed Employee Emails
Managing email data for departed employees can be tricky. Many organizations convert mailboxes into shared ones, but this poses privacy risks and ongoing email complications. Inactive mailboxes, on the other hand, offer a secure solution by preserving data indefinitely and blocking new emails. This blog explores why inactive mailboxes in Microsoft 365 are the best option for managing employee exits, outlines the risks of shared mailboxes, and emphasizes the need to rethink how you handle ex-employee mail.
Day 26: Customize Remember Multi-factor Authentication Setting in Microsoft 365
Did you know that the default bypass period for MFA in Microsoft 365 is up to 90 days after login? 😱 This long window could expose your organization to serious risks like session hijacking and unauthorized access. Learn how to adjust the ‘remember MFA’ setting to reduce the timeframe and boost your Microsoft 365 security from this blog.
Day 27: Block Uploading Specific File Types in SharePoint and OneDrive
Managing file uploads to SharePoint and OneDrive is a key to maintaining security and efficiency. Allowing all file types can introduce security risks or unwanted content. Admins can control uploads, prevent data leaks, and optimize storage by blocking specific file types. This guide explains how to block file types and keep your cloud environment secure.
Day 28: Delete Phone Authentication for Microsoft 365 Users
Phone-based MFA is a less secure method, as we all know. However, just being aware of its risks, like SIM swapping attacks, isn’t enough! Admins must proactively remove phone-based MFA from user accounts in Microsoft 365. With that in mind, an all-in-one PowerShell script is here to help you delete phone-based MFA methods based on your specific needs. Let’s dive in!
Day 29: Identify and Remove Inactive Users in Microsoft 365 using PowerShell
Microsoft 365 inactive user accounts are a loophole through which attackers might gain initial access and can further take action. Additionally, these accounts consume unnecessary licenses that can be reused to reduce costs. Let’s learn how to find and delete inactive users in Microsoft 365 in detail.
Day 30: Top 14 Best Practices to Protect Microsoft 365 Admin Accounts
Admins are the heart of Microsoft 365, ensuring everything runs smoothly. But with great responsibility comes great risk, making them prime targets for cyberattacks. This National Checklist Day, we’ve compiled an essential security checklist to help safeguard admin accounts against phishing, brute force, and other threats. Just as a checklist is vital for safety, these steps are crucial to keeping your Microsoft 365 environment secure.
Day 31: Create Auto-labeling Policy to Apply Sensitive Labels to Content Automatically
Discover how to protect your sensitive data effortlessly with auto-labeling policies in Microsoft 365. This blog details the steps to create a policy that automatically applies sensitivity labels to your content, ensuring compliance and data protection without user intervention.
We’ll update the list daily, so subscribe now to get the latest updates! 🔔
Reddit: reddit.com/r/AdminDroid/
LinkedIn: linkedin.com/company/admindroid
Twitter: twitter.com/admiindroid
Facebook: facebook.com/admindroid






