Why are we sounding the alarm on this today? Because in many organizations, there are still users walking around without any MFA methods. Yes, you read that right! No second layer of protection at all. 😬 That’s like using bubble wrap as body armor. 🫧🛡️
But hold up, you can fix this! The solution is simple: ensure all users can complete multifactor authentication in Microsoft 365. Let’s walk through how to get your users registered with MFA and how it directly boosts yours Microsoft 365 secure score.
Why It’s Important to Implement Multifactor Authentication in Microsoft 365?
Enabling multifactor authentication (MFA) is an essential step, but it’s only effective when MFA is made mandatory for all users. Partial adoption to MFA leaves your organization’s security posture weak, and lets user accounts expose to phishing, brute-force attacks, and more.
Applying MFA to all users, instead of just specific groups, eliminates security blind spots by ensuring every account is protected from unauthorized access. For instance, requiring MFA to access admin centers with stronger authentication methods ensures only authorized users can make changes. At the same time, enforcing MFA for all users strengthens your overall security posture and prevents weak points in your defenses.
Identify Users Without MFA Registration in Microsoft 365
Before taking steps to enforce multifactor authentication (MFA), it’s crucial to understand your organization’s current readiness. We need details such as how many users have already registered for MFA, which methods they’re using, how many are still unprotected, and so on.
Since the data from Entra ID’s recommendation ‘Ensuring all users can complete multifactor authentication’ is inaccurate and confusing, it’s better to directly check the authentication methods registered by users.
- Sign in to the Microsoft Entra admin center.
- Navigate to Identity → Protection → Authentication methods → User registration details.
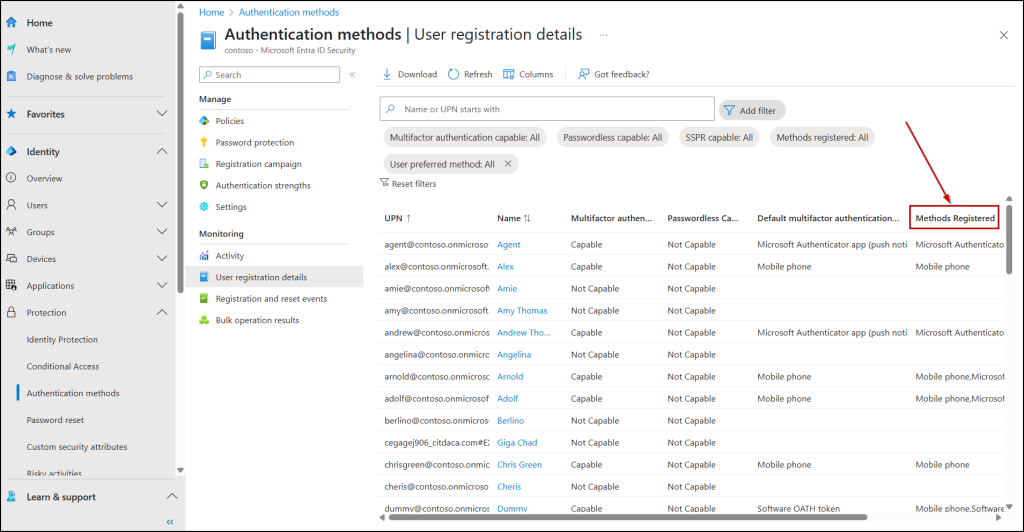
Here, focus on the ‘Methods Registered’ column, which is the key indicator that the user is not registered for MFA. If the column mentioned with any authentication method, it means the user has completed their MFA registration with the specified methods. Else, the user has not completed their MFA registration.
You can also check the Per-user MFA status in the Entra admin center by navigating to Identity → Users → All users, clicking the ellipses (···) in the toolbar, and selecting Per-user MFA. Alternatively, you can use the MS Graph PowerShell to check the MFA status of the users.
Enforce All Users to Complete Multifactor Authentication in Microsoft 365
Now that you’ve identified users who haven’t completed MFA registration in Microsoft 365, it’s time to take action and ensure they complete the MFA registration. To move forward, you can enforce MFA for users using any one of the following methods based on your organization’s needs and licensing.
- Use Security Defaults for a quick and easy MFA rollout
- Enforce MFA with Conditional Access Policies for greater flexibility
Enforce Multifactor Authentication for All Users Through Entra ID Security Defaults
Security Defaults offer a quick way to enable MFA across your entire organization with minimal setup. Once enabled, all users and the new upcoming users must register for MFA using the Microsoft Authenticator app within 14 days. If they don’t complete the registration, they’ll be unable to sign in after the 14-day period without completing the MFA setup. This is ideal for smaller organizations or those using the Entra ID free tier who want a simple way to boost security without complex configurations.
However, remember that this setting applies uniformly to all users—exceptions can’t be made. Additionally, legacy authentication protocols like IMAP and POP are automatically blocked, reducing exposure to common attack vectors.
To enable security defaults, follow the steps below:
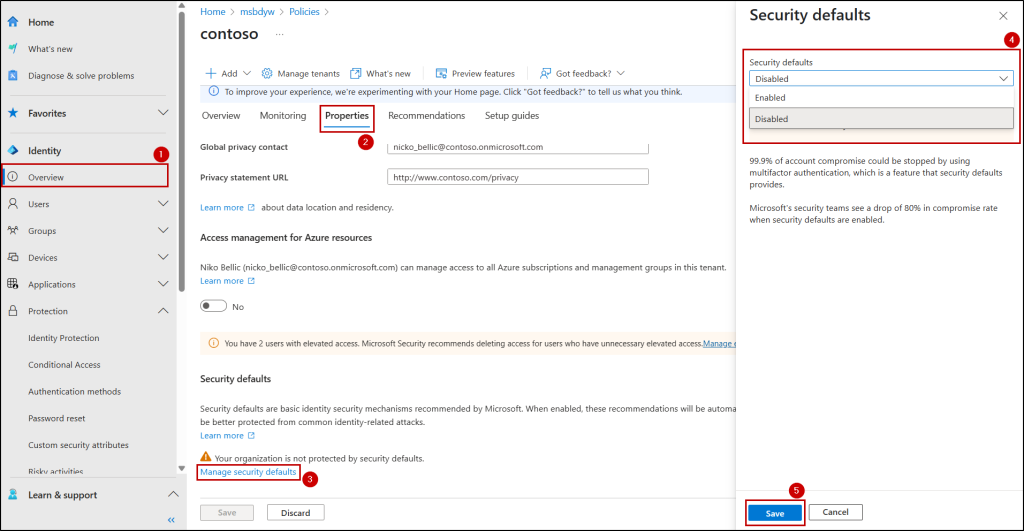
- In the Entra admin center, select Manage security defaults under Overview → Properties.
- In the flyout pane, select Enabled from the ‘Security defaults’ dropdown and click Save.
Require Multifactor Authentication for All Users using Conditional Access in Microsoft 365
Conditional Access in Microsoft 365 offers flexible MFA enforcement based on specific sign-in conditions. For instance, you can prompt for MFA when a user with a global administrator role attempts to access resources. Conditional Access is available with Microsoft 365 Business Premium, E3, E5, and Azure AD Premium P1/P2 licenses. It’s ideal for organizations that need to enforce MFA based on specific conditions, such as for admin roles or certain applications.
To configure conditional access policy, you can use the following steps:
- Navigate to Policies under Identity → Protection → Conditional Access.
- Select New policy and give it a meaningful name.
- Under ‘Assignments’, select Users.
- Under Include, select All users.
- Under Exclude, select Users and groups and choose your organization’s break-glass accounts.
- In Target resources, select All resources (formerly ‘All cloud apps’).
- Under ‘Access controls’, select Grant.
- Select Require authentication strength, then select the desired built-in MFA method from the dropdown and click Select.
Note: You can choose Require multifactor authentication under Grant to allow users to register and use any MFA method. Selecting Require authentication strength enforces only the specific method you’ve selected from the dropdown.
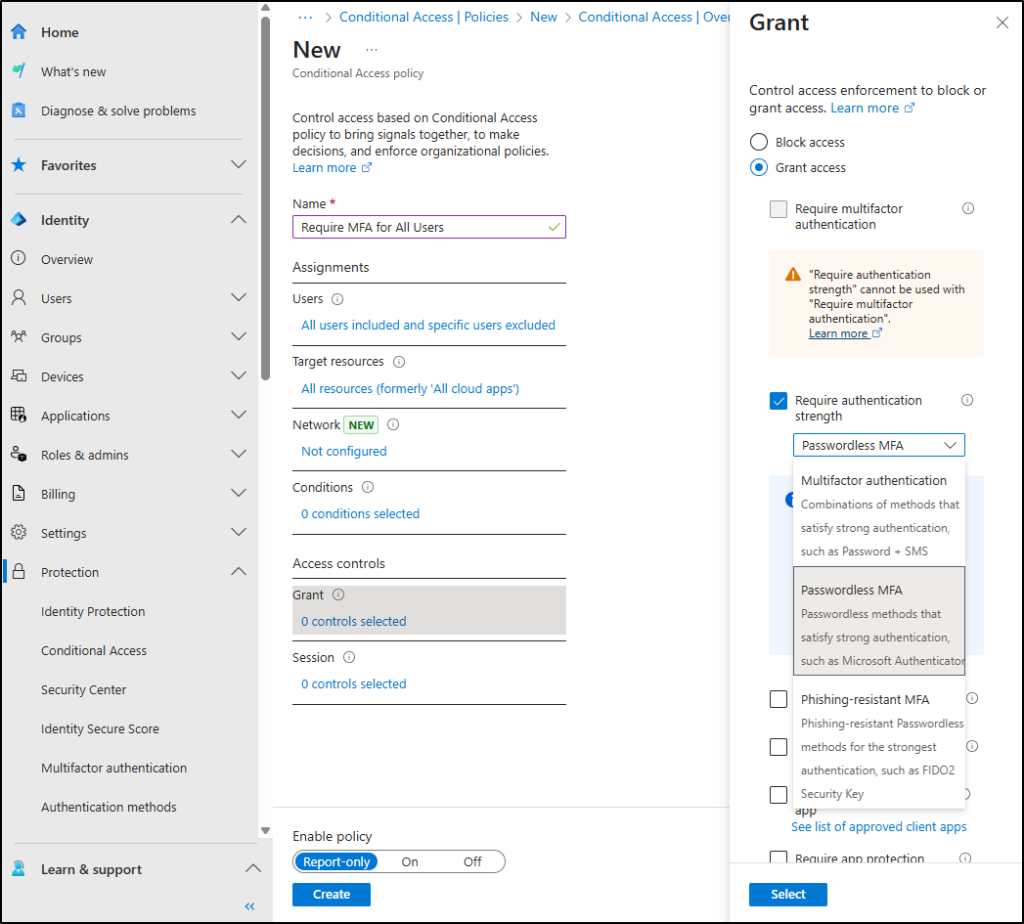
- Next, set the Enable policy toggle to Report-only mode and click Create.
Finally, evaluate the policy settings in report-only mode to observe its impact without enforcement. Once everything is fine, switch the Enable policy toggle to On.
You can also use the CA policy impact Entra workbook for a detailed analysis of how users and applications are affected.
Next Steps to Strengthen MFA Strategy in Microsoft 365
Enforcing MFA is just the beginning. To fully secure your Microsoft 365 environment and align with evolving best practices, it’s crucial to optimize how users authenticate with MFA.
- Boost MFA Adoption with Registration Campaign: Use registration campaign in Entra ID to nudge users to set up the Microsoft Authenticator app, strengthen identity protection with strong authentication methods.
- Simplify MFA Management: For a more granular approach by specifying different types of MFA for different apps, Microsoft recommends switching from per-user MFA to Conditional Access MFA.
- Prevent MFA Fatigue Attacks: Enable MFA number matching and geographical location setting to reduce MFA fatigue attacks resulting from authenticator app use.
- Enforce Adaptive MFA: Use risk-based Conditional Access policies to intelligently enforce MFA only when sign-in risks are detected, keeping security strong while minimizing user disruptions.
- Shield from Targeted Attacks: Enhance user sign-in security with phishing-resistant MFA methods like FIDO2 and certificate-based authentication.
- Protect External Identities: Configure authentication strength for external users to ensure they meet the same MFA security standards as internal users.
- Reset MFA After Account Compromise: Always reset multifactor authentication if user accounts compromised to remove existing methods and ensure only legitimate users regain access.
We hope this blog has provided you with valuable insights into ensuring all users complete MFA in Microsoft 365. Enforcing MFA across your organization, strengthens account security and builds a more resilient defense against unauthorized access. In fact, MFA can block 99.9% of account compromise attacks in your Microsoft 365 environment. Have any questions or want to share your experience with MFA enforcement? Feel free to drop them in the comments below!






