Modern identity attacks in Microsoft 365 no longer rely on guessing credentials but instead on tricking users into granting access. Threat actors now exploit human behavior through methods such as MFA fatigue attacks, malicious OAuth consent phishing, and more. Just a single inattentive tap on an MFA prompt can compromise the entire Microsoft 365 environment, including emails, Teams chats, SharePoint sites, and even admin access. These identity-based attacks highlight the urgent need for stronger user awareness and robust security controls.
Traditional security measures like strong passwords and MFA, while important, are no longer sufficient on their own. Defending against evolving identity attacks requires understanding and adapting to the new tactics that threat actors use to exploit human behavior. In this blog, we’ll explore the modern identity attacks targeting Microsoft 365 and discuss strategies to strengthen your identity protection.
Why are Microsoft 365 Identities a Prime Target for Attackers?
Microsoft 365 user accounts hold a wealth of data and access. Whether it’s a frontline worker with OneDrive access or an administrator with global permissions, every identity can become a doorway. Since cloud sign-ins are used daily, attackers know that tricking users or bypassing sign-in protections can give them direct access to the enterprise.
Unlike malware or brute-force attacks, identity attacks are designed to quietly follow normal user activity. Once a user’s identity is compromised, attackers can move through the Microsoft 365 environment using valid tokens or permissions, often without triggering standard alerts. It’s a discreet tactic that works across nearly all organizations, making it essential to defend identity attacks in Microsoft 365.
Microsoft 365 Identity Compromise Techniques
Identity attacks in Microsoft 365 are often divided into the following two stages.
Understanding these stages is essential for building a layered and proactive strategy to defend identity attacks in Microsoft 365.
1. Defending Pre-Compromise Identity Attacks
Pre-compromise attacks refer to the methods used by attackers to gain initial access to Entra identities. These typically involve:
- Crafting sophisticated phishing emails or fake login pages to capture credentials.
- Exploiting weak authentication methods, relying only on password and SMS text messages.
- Manipulating authentication flows to bypass multi-factor authentication (MFA).
Mitigating this stage involves strengthening authentication mechanisms and educate users to recognize attacks & social engineering attempts. Here, we’re going to explore some important pre-compromise attack techniques such as,
- Adversary-in-the-Middle (AiTM) attack
- Device code flow phishing
- OAuth consent phishing
- Microsoft Teams phishing
- QR code phishing
Adversary-in-the-Middle (AiTM) Phishing Attacks
With MFA adoption rising, attackers now use Adversary-in-the-Middle (AiTM) phishing. It’s type of man-in-the-middle technique that targets the entire authentication session, not just user credentials.
Some attackers use reverse proxy tools like Evilginx to capture session cookies. Alternatively, some adversaries use synchronous relay attacks via fake Microsoft login pages that steal login data and MFA codes. Groups like Storm‑0485 and Storm‑1295 have actively used such techniques against Microsoft 365 users.
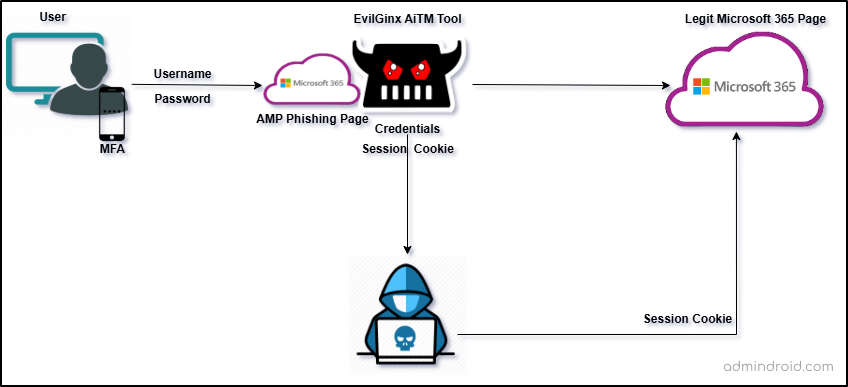
Mitigation Strategies for AiTM phishing in Microsoft 365:
- Adopt phishing-resistant MFA authentication methods like FIDO2 security keys or certificate-based authentication.
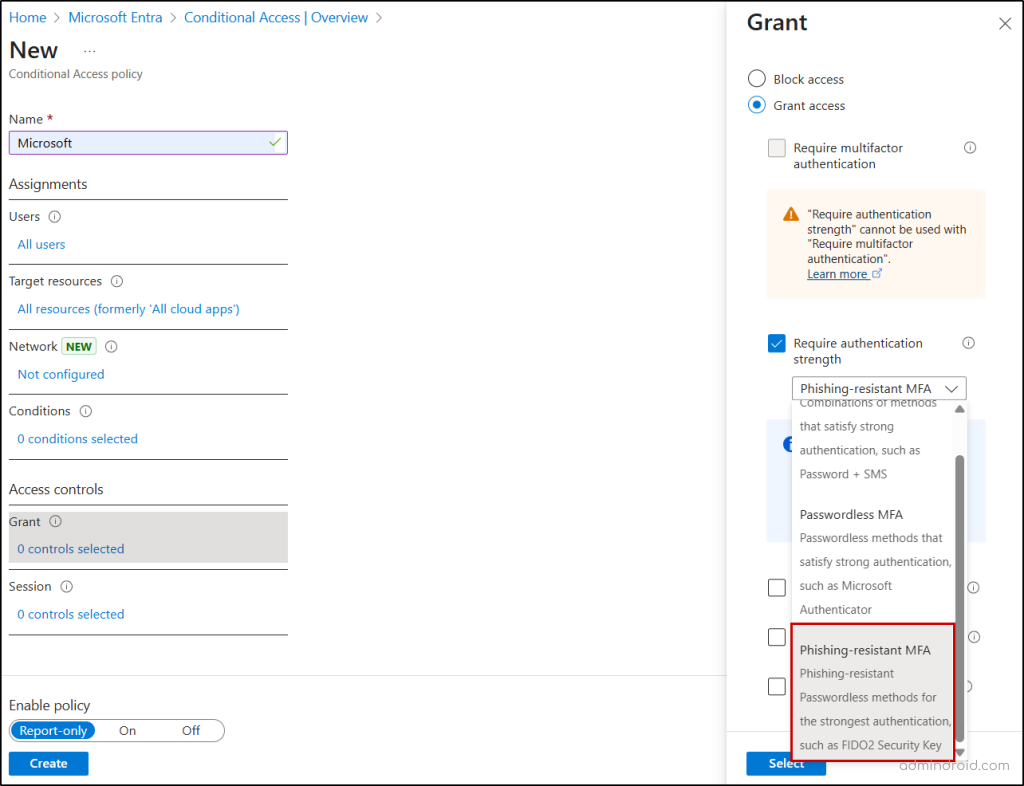
- Block sign-ins from unmanaged devices and locations using Conditional Access policies.
- Enable token binding to prevent stolen session tokens from being reused on different devices.
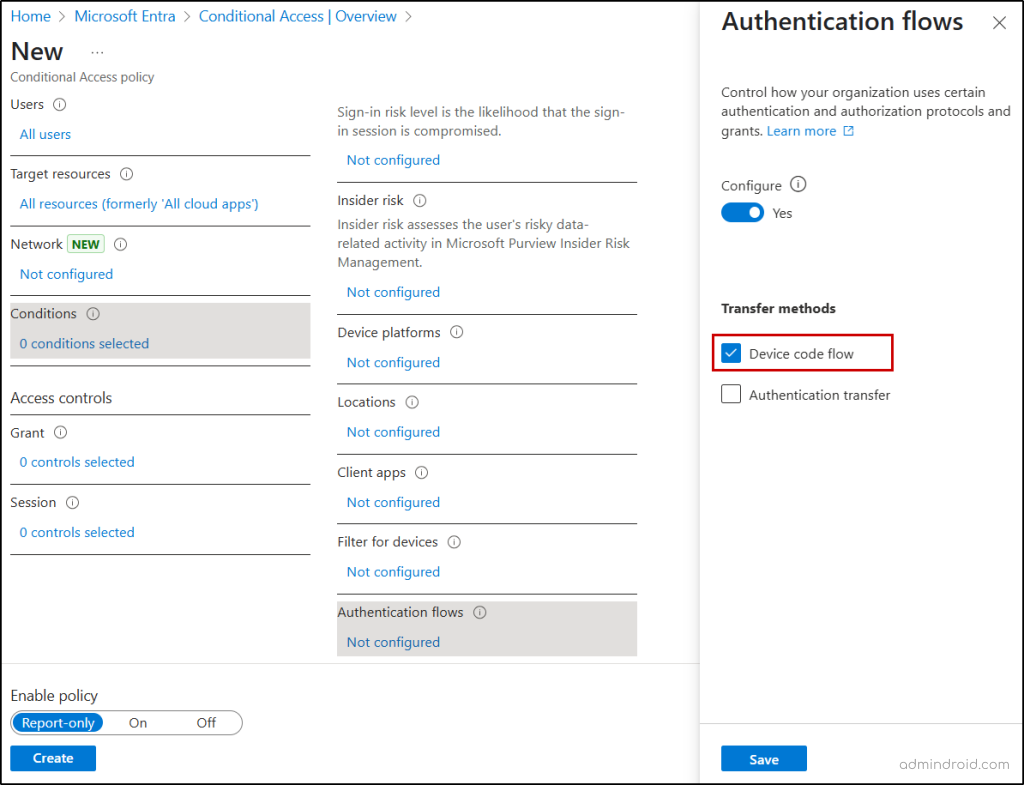
Microsoft Entra Device Code Phishing
In this method, attackers abuse Microsoft’s device code flow by tricking users into visiting the legitimate device login page and entering code tied to a malicious app.
By entering the code, the user unknowingly authorizes the attacker’s app, which then receives a valid session. Phishing campaigns like Storm-2372 and Storm-1249 performed these phishing via platforms like WhatsApp, Teams, or email by impersonating trusted contacts.
Secure Microsoft 365 Against Device Code Phishing:
- Restrict the device code flow with Conditional Access policy for external apps and enforce admin approval for app-based sign-ins.
- Use Microsoft Entra device limit restriction to reduce the attack surface and prevent malicious actors from exploiting open enrollment paths in device code phishing attacks.
OAuth Consent Phishing in Microsoft Entra
While other attacks trick users to steal credentials to gain account access, OAuth consent phishing deceive users to authorize malicious applications in their Microsoft 365. The threat actor sends emails containing consent link for a malicious third-party application.
Once the user granted consent and authorizes the app, the adversary can access Microsoft 365 data indefinitely without requiring passwords or MFA. Some attackers have even used the ‘Cancel’ button to redirect users to spoofed login pages, compounding credential theft.
Recently, attackers have advanced this tactic with techniques like the ConsentFix attack. Instead of requesting app consent, ConsentFix manipulates users into completing a legitimate OAuth flow and exposing the authorization code. The attacker redeems the code for valid tokens, hijacking the authenticated session without stealing credentials.
Protect Organization from Consent Phishing Attacks:
- Update user consent settings to allow user consent for apps from verified publishers.
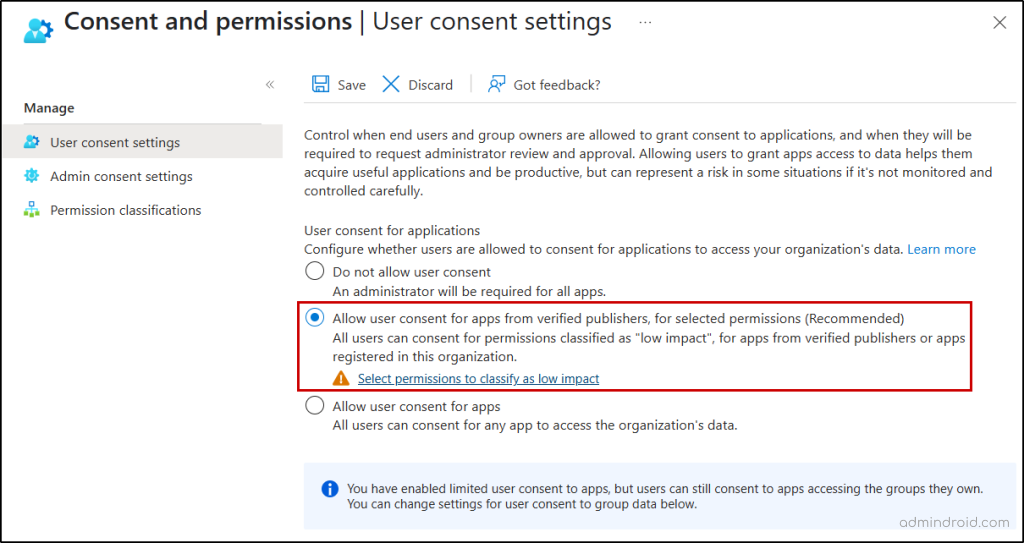
- Create an OAuth policy in Microsoft Defender for cloud apps to notify when a user consents to risky applications.
Microsoft Teams Phishing
Threat actors are increasingly exploiting Microsoft Teams to bypass email defenses. By sending phishing messages from compromised or rogue tenants, they directly contact users to steal their credentials.
Strengthen Teams Against Identity Attacks:
- Disable anonymous users from joining Teams meetings to prevent attackers from gathering information about your organization.
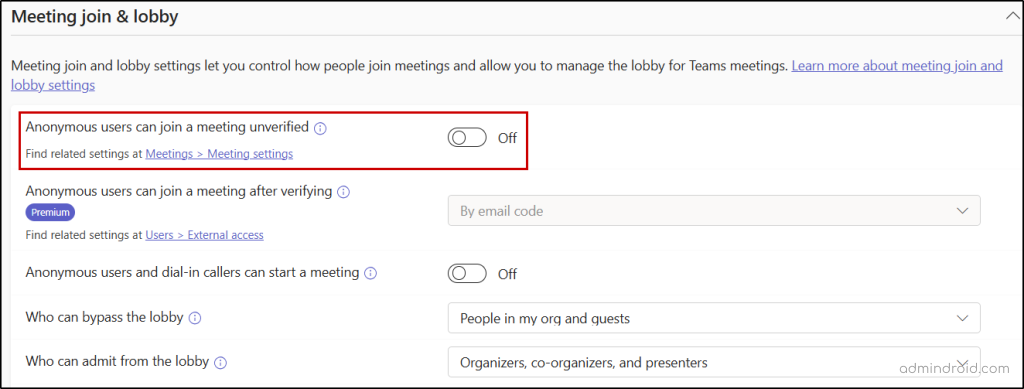
- Restrict Teams meeting chat access for anonymous users to avoid delivering phishing links and malware files to internal users.
- Enable sensitivity labels for Microsoft Teams to encrypt files shared during conversation.
QR Code Phishing in Microsoft 365
QR code phishing (quishing) emerged post COVID-19 as a sophisticated social engineering tactic. Attackers use PDF attachments with fake QR codes that lead users to spoofed Microsoft 365 login pages.
Especially, major attack groups like Storm-0249 used QR codes in tax scam emails to install dangerous malware on users’ computers. Star Blizzard took a different approach by first sending broken QR codes to get people to respond, then following up with real WhatsApp QR codes to hijack their accounts.
Combat Emerging QR Code Phishing:
- Ensure users scan QR codes for authentication only when they are shared by trusted sources like admins or managers. This prevents user credential theft through fake login prompts.
- Protect your organizations against QR code phishing by quarantining high-confidence phishing messages using Microsoft Defender.
2. Countering Post-Compromise Persistence Identity Attacks
Once attackers gain access to Microsoft 365 accounts through any of the identity attacks, they immediately work to establish long-term access. Rather than repeating the original attack again, they launch follow-on attacks to escalate privileges and deploy multiple persistence techniques to maintain access.
Attackers typically use these common persistence methods to secure their foothold:
- Vulnerable OAuth Apps: Delegating broad permissions for unprotected applications that continue working non-interactively.
Solution: Configure application instance lock in Microsoft Entra ID to lock certain sensitive properties of an application that couldn’t be modified by anyone in the organization.
- Inbox Rules Manipulation: Creating new email forwarding rules or modifying existing rules to send sensitive data to external accounts.
Solution: Monitor all inbox rules in Exchange Online to find any rules forwarding data to external accounts.
- Abuse Automation: Exploiting Power Automate flows or Azure automation to run scripts unattended for data exfiltration.
Solution: Regularly review all Power Automate workflows and Azure automation to detect unauthorized sources added for data transfers.
- Privileged Role Misuse: Assigning roles like Application Administrator to escalate privilege and gain access to sensitive apps like emergency access apps.
Solution: Use Privileged Identity Management (PIM) to enforce just-in-time role assignments and avoid unintended privilege escalations. - MFA Registration Attacks: Once attackers gain access to an account, they often attempt to bypass MFA by registering their own methods. If weak MFA options are available, they can easily hijack the account and lock out legitimate users.
Solution: Use Conditional Access policies to restrict MFA registrations for suspicious or risky users. This ensures that even if an attacker compromises an account, they cannot add or register unauthorized MFA methods.
Threat actors also leverage compromised accounts for internal phishing campaigns, which are highly effective because they originate from trusted sources and use authentic company language.
Common Best Practices to Defend Against Identity Attacks in Microsoft 365
Here are some common best practices to defend against evolving identity attacks in Microsoft 365.
- Require all users to complete MFA to increase difficulty of account compromise attempts.
- Monitor priority accounts by tagging them in Microsoft 365 to apply enhanced protections and detect identity threats faster.
- Control access to Azure resources by defining custom security attributes to required Microsoft Entra ID users.
- Use the leaked credentials report in Microsoft Entra ID to quickly identify compromised accounts.
- Once you’ve identified a compromised account, take immediate action to remediate compromised account and assess the impact.
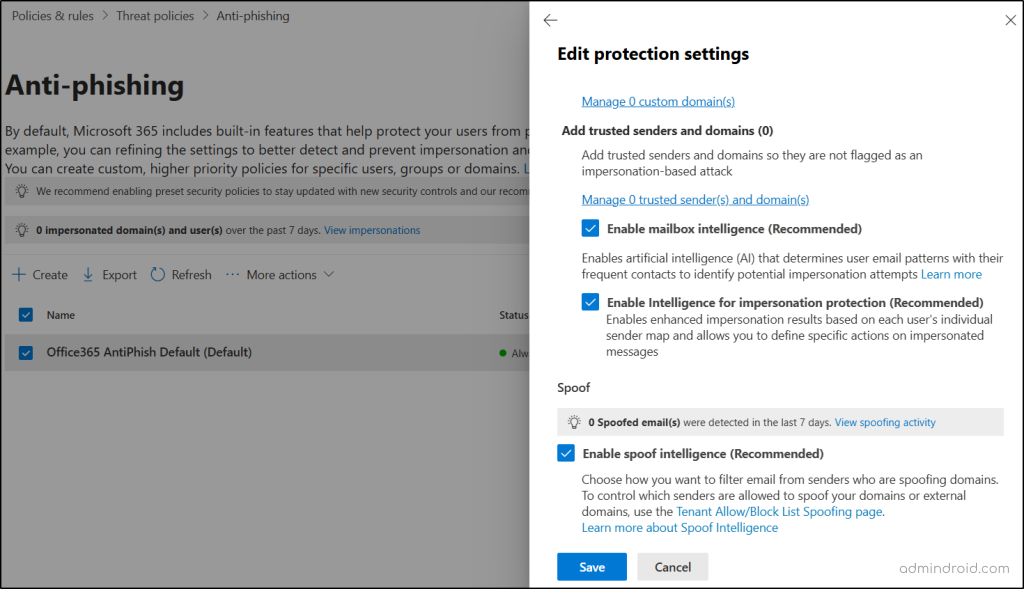
- Secure your email environment against phishing by configuring SPF, DKIM, and DMARC to block attackers from impersonating your domain in credential-harvesting attacks.
- Enable Zero-hour Auto Purge (ZAP) in Exchange Online to automatically delete phishing and malware-laden emails from inboxes before users interact with them.
- Use risk-based Conditional Access policies to evaluate sign-ins using factors like IP address, device status, and location.
- Leverage the Microsoft Entra ID Protection dashboard to monitor risky sign-ins and detect identity attacks in Microsoft 365.
We hope this blog helps you understand and defend against evolving identity attacks in Microsoft 365. Stay vigilant and keep your defenses strong! Have any questions? Share them with us in the comments section!






