In today’s digital world, the importance of application security in Microsoft 365 cannot be overstated, especially as administrators struggle with protecting sensitive data. To effectively safeguard against unique challenges and vulnerabilities, security practices must extend beyond general measures. From the initial setup of application permissions to the management of access controls, each layer of application security plays a vital role in preventing data breaches. It is therefore crucial to implement security strategies specifically tailored to protect not only Microsoft 365 apps but also custom and third-party applications. Thus, it ensures the integrity of your organization’s data.
Let’s explore the basic security measures that must be implemented to secure Microsoft 365 applications effectively.
Basic Security Measures for Microsoft 365 Applications
While the conversation on security focuses on Entra security and email protection, application security in Microsoft 365 often goes unspoken. Yet, it is crucial to implement robust application security guidelines not just to protect sensitive data, but also to improve overall security. Here are some basic measures that every organization could follow to secure their applications and data.
Manage Applications in Microsoft Entra ID
- Security guidelines for app registrations
- Configure application instance lock in Microsoft Entra ID
- Manage user consent to applications in Microsoft 365
- Set Conditional Access for applications in Microsoft 365
- Configure app protection policy using Intune admin center
- Create access reviews for applications
- Verify unprotected applications in Microsoft 365
Manage Apps in Microsoft Teams
- Disable third-party app installations in Microsoft Teams
- Restrict custom app uploads in Microsoft Teams
- Restrict a specific team from accessing apps in Microsoft Teams
- Control user access to Teams apps using app centric management
Manage Applications in Microsoft Entra ID
Applications in Microsoft Entra ID need to be monitored, as app registrations to consent grants, access reviews, conditional access, etc., are configured here. So, best practices and basic security measures need to be taken at every step to maintain security and ensure data protection. Let’s take a look at the security measures below.
1. Security Guidelines for App Registrations
Users who have proper permission can register their applications in Microsoft Entra ID for various purposes. Usually, admins create applications for use and register the app in Azure AD for org-wide usage. Let’s see what measures could be considered as the best practices for application registration.
Configure Access Tokens for App Registrations
When configuring authentication flows for access tokens, consider using an Auth code flow instead of an implicit flow. It is less secure as it lacks client authentication and is no longer recommended as best practice. However, you can configure implicit flow only if the application demands it. Also, if the application is not actively in use, you can consider turning off implicit flow for better security.
You can set the Access tokens (used for implicit flows) option under the Authentication tab in Microsoft Entra admin center.
Use Certificates and Secrets for App Authentication
Microsoft highly recommends using certificate credentials instead of passwords (aka, secrets). Therefore, block the creation of client secrets in applications and enforce certificate-based authentication wherever possible.
Also, if possible, try to use x509 certificates as the only credential type for getting tokens for apps. You can retrieve Entra app registrations with expiring clients and certificates to find out their expiry date and ensure smooth authentication.
Assign Ownership to Azure Application
Usually, while creating an application, no owners will be assigned to it. Yet, it is essential to configure ownership for Microsoft 365 apps to manage all aspects of an application. Ownership should be given only to a minimum set of users. Also, admins should regularly monitor the application ownership details once every few months to ensure that the users are still available in the organization and still own an application.
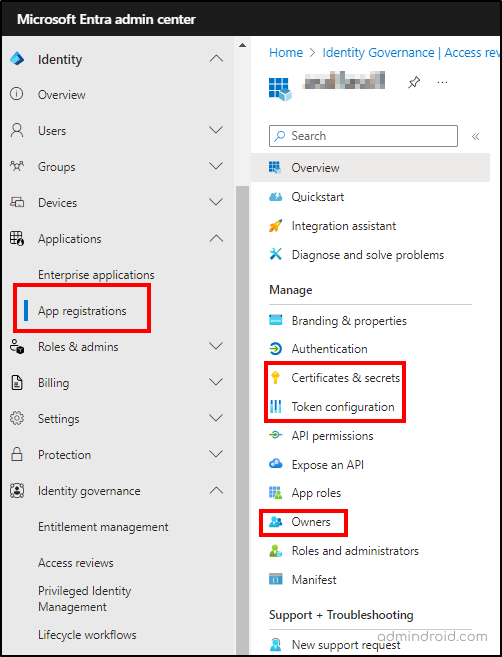
2. Configure Appliction Instance Lock in Microsoft Entra ID
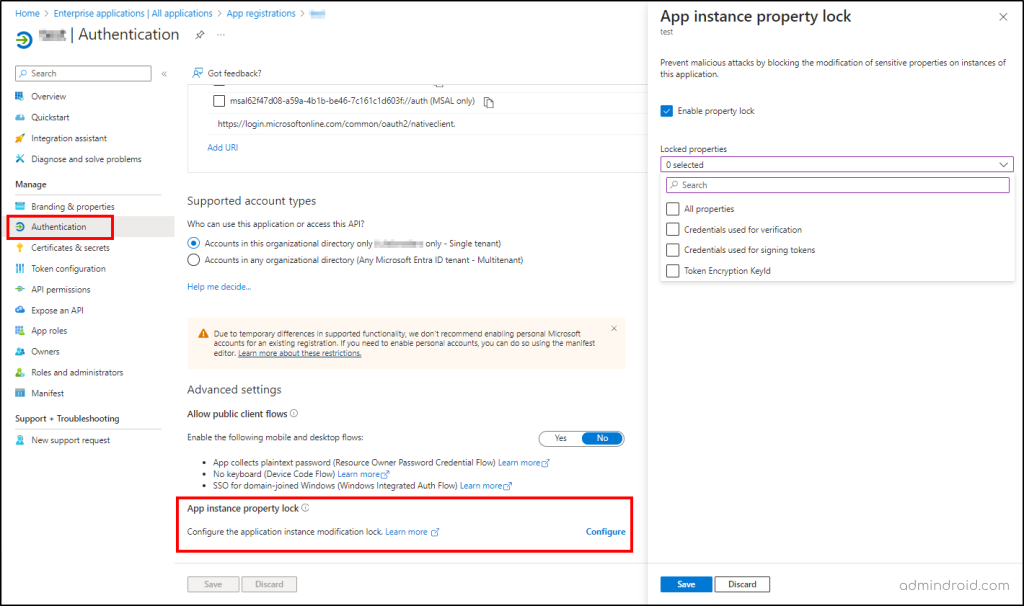
For multi-tenant supporting apps, app developers can lock certain sensitive properties of an application that couldn’t be modified by anyone in the organization. This setting will be enabled by default for new application creation. However, for existing applications, admins need to manually check and enable it. To enable the app instance property lock, follow the steps below.
- Navigate to Entra admin center –> Applications –>App registrations.
- Click on the specific app and select Authentication tab on the left.
- Under Advanced settings, locate the App instance property lock and click Configure.
- Check the ‘Enable property lock’ checkbox and select the required properties. Click Save.
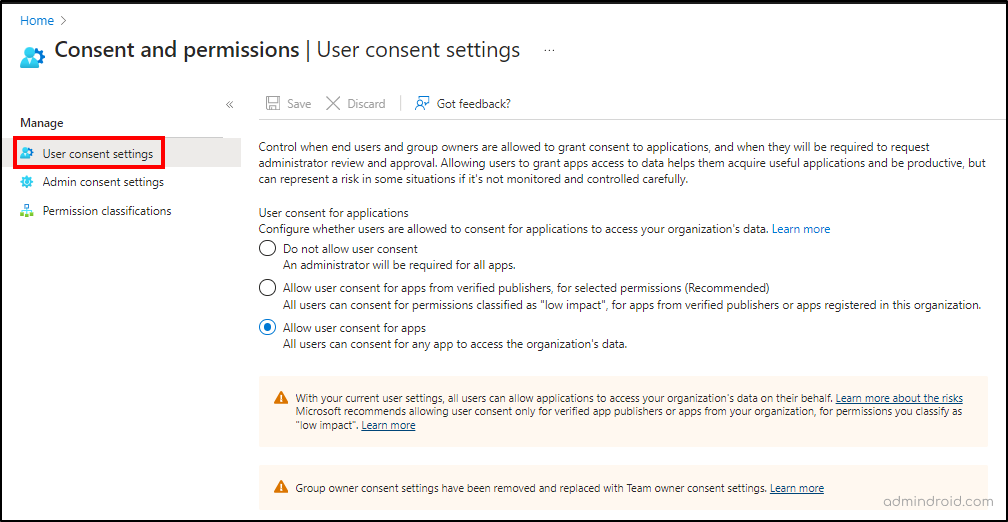
3. Manage User Consent to Applications in Microsoft 365
The User consent settings determine whether the end users and group owners can grant consent to applications to access the organization’s data. It is recommended for admins to allow user consent to apps from verified publishers alone.
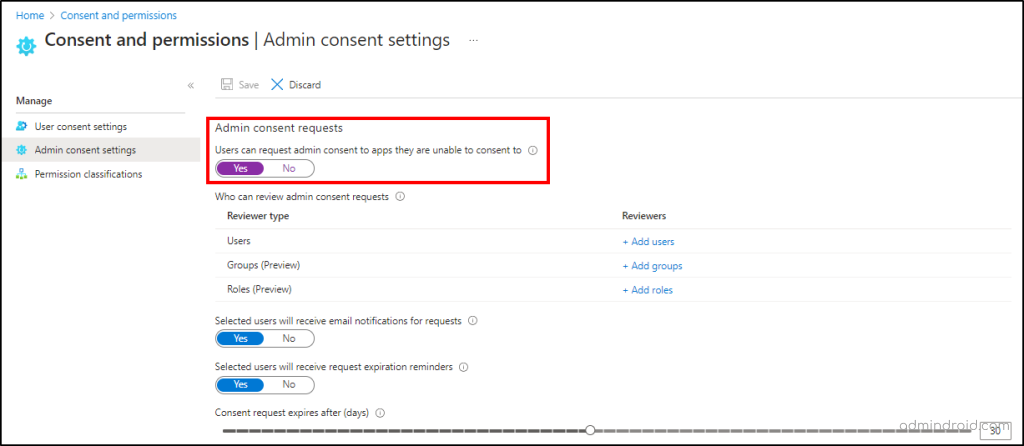
Some organizations might want to implement more strict controls and don’t want users to grant consent to apps. In such cases, admins must grant app consent in the organization. Admins can allow specific users, groups, or role members to review the requests, and they grant consent to apps.
Both admin consent and user consent to apps are configured by navigating to Entra admin center –> Applications –> Enterprise applications –> Consent and permissions.
4. Set Conditional Access for Applications in Microsoft 365
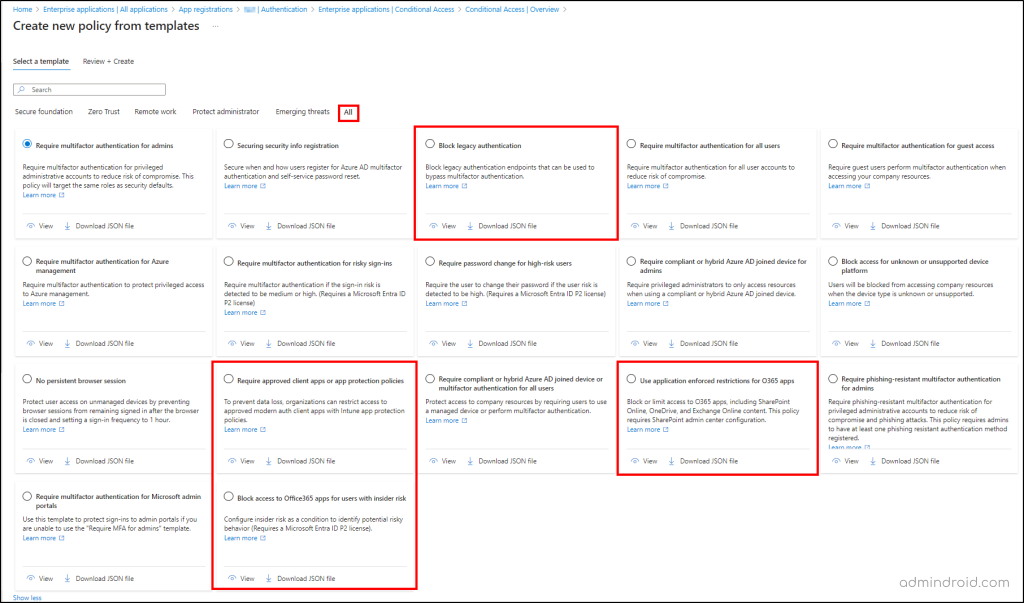
Conditional access is crucial in securing Microsoft 365 applications as it ensures that only authorized users can access sensitive app data. By configuring MFA and setting strong access controls, CA policies help prevent unauthorized access. Also, Microsoft reduced the admin’s workload by providing ready-to-deploy Conditional Access policy templates to streamline security setup. These templates can be accessed by navigating to Entra admin center –> Applications –> Enterprise applications —> Conditional access –> Create policy from templates. Let’s see what templates can be deployed for securing Microsoft 365 apps.
Note: While deploying the CA policy templates, always deploy in the report-only mode. After verifying that it works fine, you can enable the policy. Also, don’t forget to exclude emergency access applications and break glass accounts in the policy configuration.
Use Application Enforced Restrictions for Office 365 Apps
As users are using personal devices to access apps which might not be controlled or managed properly, this could lead to potential data loss. This application-enforced restriction helps to block or limit unmanaged devices from accessing SharePoint, OneDrive, and Exchange content in Microsoft 365. Thus, it helps to prevent unwanted data breaches in the organization. This template can be reviewed and deployed from the Entra admin center.
Block Access to Office 365 Apps for Users with Insider Risks
Users who are involved in risky behaviors should be monitored and blocked from accessing apps & resources. Otherwise, attackers can easily steal the sensitive data. So, users assigned with specific insider risk levels from Adaptive Protection in Microsoft Purview should be blocked from accessing Office 365 apps and resources to protect data. Admins can easily enable insider risk in the CA policy by deploying this template.
Require Approved Client App or App Protection Policy
For enhanced protection and to prevent data loss, organizations can require an approved client app to access selected cloud apps. As the approved client app grant in CA policy is going to retire soon, it is recommended to migrate to the application protection policy.
If you configure this setting in CA policy, an Intune app protection policy will be present on the client app before access is available to the specified applications.
Thus, it avoids unauthorized access and provides better security. This CA policy can be reviewed and deployed from the template in the Microsoft Entra admin center.
Note: Verify the list of client apps supporting this setting before creating or deploying these templates.
Block Legacy Authentication in Microsoft 365
Usage of legacy authentication methods can bypass CA policies and could lead to potential data loss or account compromise. Also, it is considered less secure and should be blocked in every organization for better security. Deploy this CA policy template in the organization and enhance your security by blocking legacy protocols.
5. Configure App Protection Policy Using Intune Admin Center
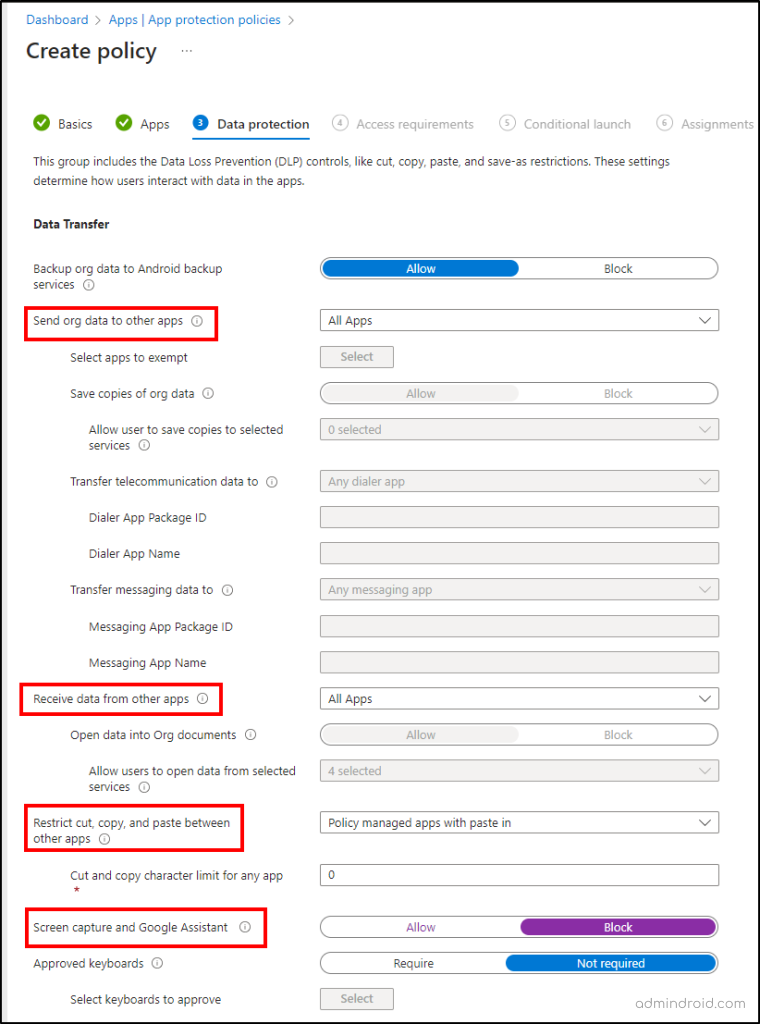
To create an app protection policy in the Intune admin center, you must first enable ‘Require app protection’ in a Conditional Access (CA) policy. Also, in Intune admin center, you can have more granular access-related settings that could be helpful in securing access to applications. Thus, creating an app protection policy would be helpful when you want to specify the access controls based on your requirements. You can create an app protection policy by navigating to Intune admin center –> Apps –> App protection policies. Here’s what you can control using the App protection policy.
- Applications sending/receiving organization data – Controls the ability of apps to share or receive data from other apps.
- Restrict cut, copy, and paste between other apps – Controls the cut, copy, and paste feature between mobile apps to prevent data sharing.
- Block screen capture and Google Assistant – Prevents users from taking screenshots on applications. It supports Android devices only.
6. Create Access Review for Applications
Access reviews in Microsoft Entra ID feature is used to periodically verify the access permissions of users on specified applications, teams, or groups. It helps to check the accesses and remove unwanted access given to the resources for enhanced security. This can be created by navigating to Entra admin center –> Identity governance –> Access reviews.
Admins can create access reviews for below cases:
- Identify and remove user access to applications who have no recent sign-in activity.
- Detect and remove users who are no longer part of the organization.
- To periodically monitor the ownership of crucial applications and ensure they are active.
7. Verify Unprotected Applications in Microsoft Entra ID
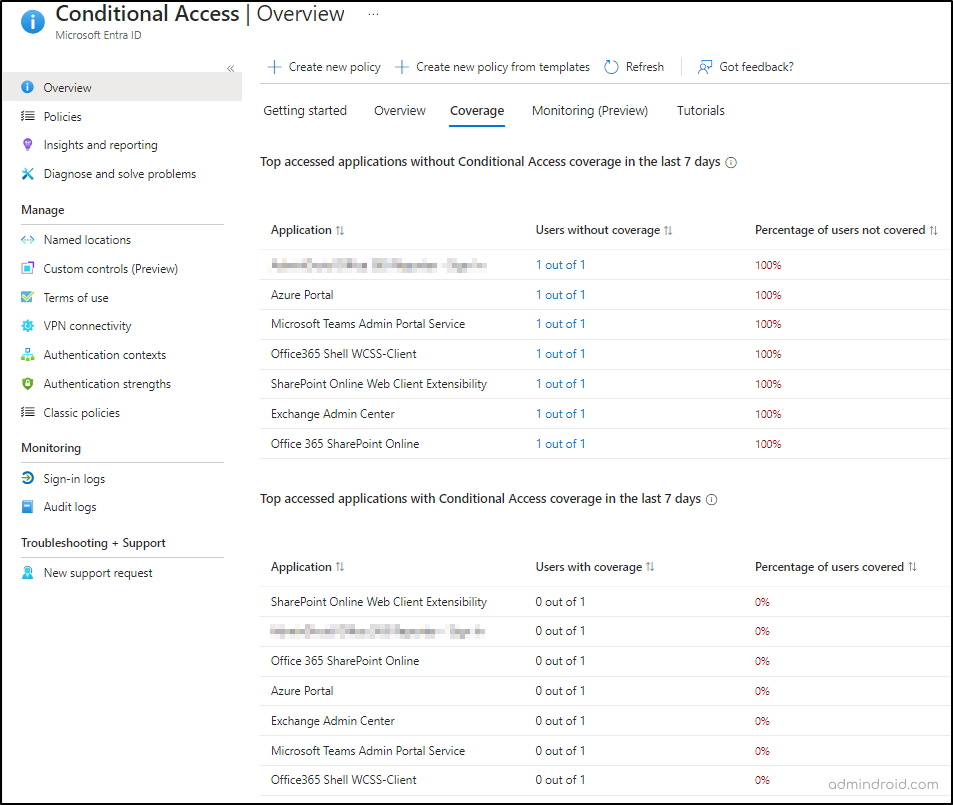
Unprotected applications in MS Entra are apps that don’t have any Conditional Access policies configured. Identifying such unprotected apps and configuring the required CA policy could prevent data loss and unauthorized access to those apps. So, to find the apps without Conditional Access, Microsoft has made it easier by just listing them in the Conditional Access overview page in the Entra admin center.
Manage Apps in Microsoft Teams
In Microsoft Teams, default and custom apps can be used by users for tasks or other purposes. Admins need to control the application usage for specific teams & users and control the custom or third-party apps usage. Because some third-party or custom applications might not align with the organization’s security guidelines. Also, specific teams or users might not be involved in projects or tasks that require third-party or custom app access. Thus, managing and controlling app usage is essential in Microsoft Teams.
8. Disable Third-party App Installations in Microsoft Teams
Admins can control whether users in their organization can install and use the default available apps, third-party apps, and custom apps in Microsoft Teams. Third-party apps installation is enabled by default. Therefore, it is suggested for Teams admin to disable this setting unless the organization requirements involve third-party usage. Since not all apps maintain proper security measures, it could lead to significant data breaches in the organization. Managing Teams apps can be done by navigating to Teams admin center Teams apps–> Manage apps –> Actions –> Org-wide settings.
Note: If your organization use third-party apps, ensure you follow these secure score recommendations to secure third-party apps.
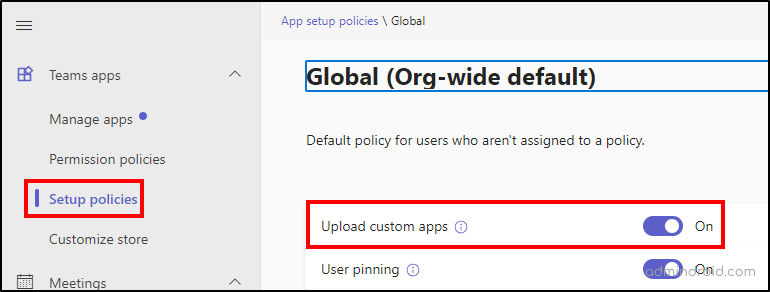
9. Restrict Custom App Uploads in Microsoft Teams
Users in the organization can create and upload custom apps for org-wide use. If the application security is not properly handled, it could compromise the data. In such scenarios, admins can disable the custom app upload option in the Microsoft Teams Admin Center–> Teams apps–>Setup policies –> click on the org-wide policy.
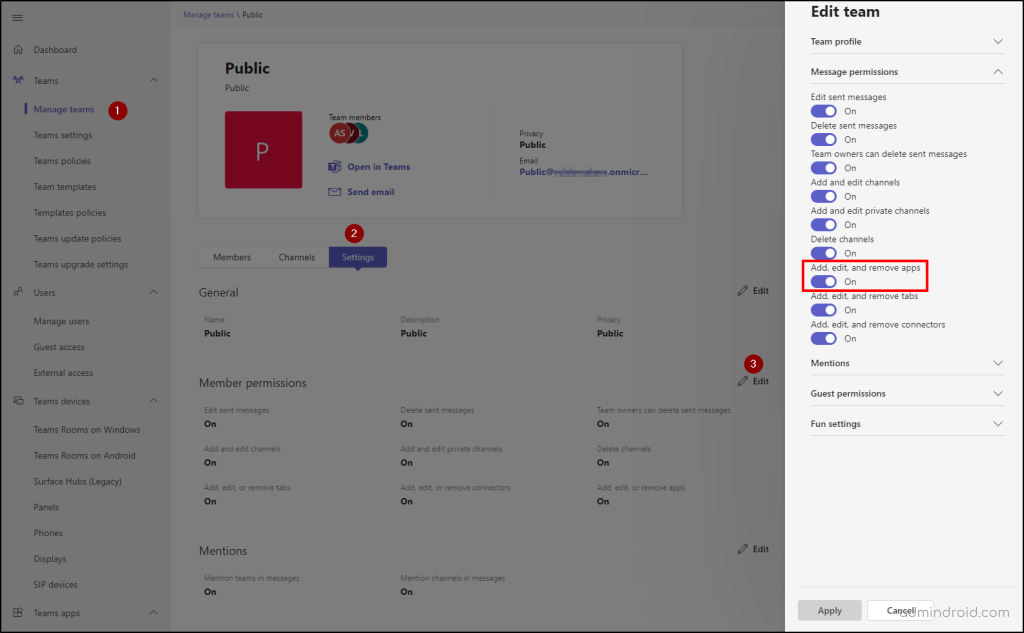
10. Restrict a Specific Team from Accessing Apps in Microsoft Teams
Admins might want to allow users to access apps, but not for most confidential teams due to security & privacy concerns. In such rare cases, admins might restrict a specific team from installing or using apps by navigating to Teams admin center –> Teams–>Manage Teams –> click on the specific team –> Settings tab.
11. Control User Access to Teams Apps Using App Centric Management
Admins often grant broad access to apps, allowing all users to access a wide range of applications, regardless of necessity. However, not every app is required by all users. Admins can control who can access a specific app in Teams using App centric management. Follow the steps below to control user access to a specific app.
- Navigate to Teams admin center –> Teams apps –> Manage apps.
- Select the desired app, click on the Assignments tab, and select Assign.
- Choose the required option from the ‘Manage who can install this app’ dropdown. You can have the below options.
- Everyone in the organization.
- Specific users or groups
- No one.
- Click Apply.
Monitor Application Usage in Microsoft 365
Configuring the right security settings alone is not enough to secure applications. Monitoring those settings and tracking the usage of applications is equally important as well. Microsoft 365 application usage insights help verify how users are using the applications, apps that are most used and least used, sign-in details, and more. Microsoft 365 application usage insights help verify how users are using the applications, apps that are most used and least used, sign-in details, and more. Monitoring app usage might be useful in making better decisions to improve productivity and security. Azure AD application activity & usage insights are available in both the Microsoft Entra admin center and Microsoft 365 admin center. Get a glimpse of what you get from those portals below.
- Microsoft Entra application sign-in activity
- Service principal sign-in activity
- Application credential activity
- Microsoft 365 app usage, activations, active users, etc.
- Microsoft Teams app usage and user activity
By monitoring the app usage insights, you can remove unused applications from the organization to protect your data.
I hope this blog gives you basic security guidelines to secure your applications in the Microsoft 365 environment. Let us know what more measures you use to safeguard M365 apps and overall Microsoft 365 security through the comment section. Happy securing!






